A friend of mine recently received an email with his password in plaintext in the subject line. The message contained a demand for $10K in Bitcoin. To ensure compliance, the attacker included plans on how they would hack and destroy the receiver. This same friend mentioned he used a password management software to manage his passwords and realized he had used the same password for over 140 different sites.
Clearly, he needed to change his password on all of them.
Obtaining a user’s credentials has always been cheap and easy. The accelerated digital expansion experienced by most organizations and employees since the beginning of the COVID-19 pandemic has only made it cheaper and easier.
In the last week of March, the top application downloaded was Zoom. Unfortunately for the 3.2M new users (and all the existing ones), bad actors immediately exploited its sudden popularity, enabling threat researchers to purchase over 500,000 Zoom usernames and passwords for less than a penny each.
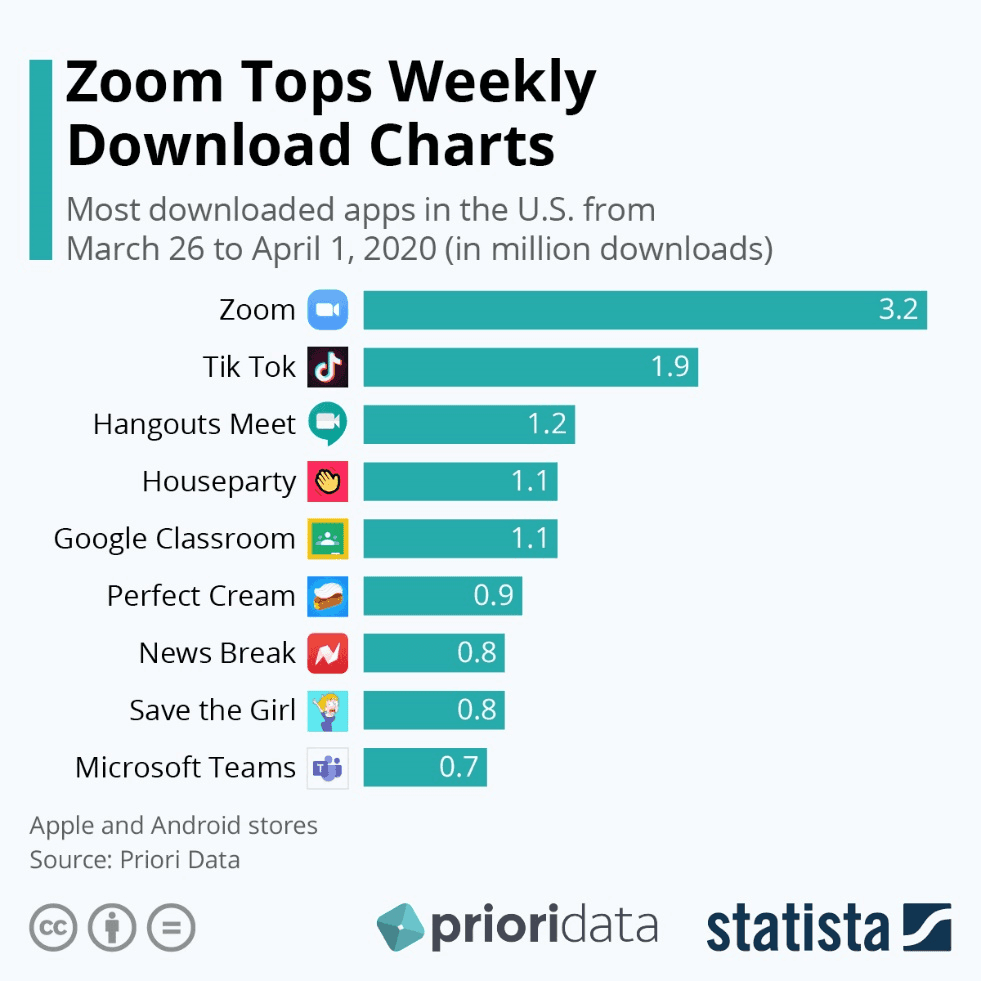
In this case, no one "hacked" Zoom. No one exploited a specific vulnerability in Zoom’s software. Attackers merely tried some of the billions of previously exposed credentials from other breaches on Zoom, and found they worked just fine.
They worked because people reuse credentials. And people reuse credentials because of the increasing number of digital activities they engage in. Every account opened with a streaming service, social media platform, or corporate application is another opportunity to reuse credentials. As early as 2015, a Dashlane analysis of data from more than 20,000 users found that the average user had 90 online accounts. In the US alone, that average was 130. In the past five years the use of digital services has only grown, and along with it, the need for credentials.
In the corporate world, the number of credentials required is just as worrisome. A LastPass survey “found that at larger companies with over 1,000 employees, the average employee was expected to have about 25 unique logins. That number shoots up to 85 at the smallest companies, far too many numbers and symbols for the average person to keep track of. Employees that do not have a password manager available to them will almost inevitably resort either to re-using passwords, or to common passwords that are easily cracked by dictionary attacks.”
Anecdotal evidence says even those who use a password manager may reuse passwords across properties.
Attackers know this. Their success at gaining access to personal and corporate accounts is due to the proliferation of password reuse and a technique known as ‘credential stuffing.’
Credential stuffing is an attack technique that uses lists of credentials to attempt access to applications and web sites. Through the wonder of automation, attackers can iterate over a list of thousands of credentials in minutes, ‘stuffing’ each one into a login screen until they find those that work.
The expansion of applications due to digital transformation exacerbates the problem by offering additional attack surfaces for bad actors to target. The pandemic has pushed organizations to offer digital capabilities, thus expanding both the pool of credentials and the possible targets for attackers.
There are established best practices that can help both businesses and consumers protect against becoming a victim of a credential stuffing attack.
- Users should pay careful attention to password management for both work and personal usage. Using simple techniques such as interspersing a common complex password string with certain characters from website name can help reduce the anxiety about forgetting credentials that leads to password reuse. As an example, password to Bank of America would be B<complex string>A and Wells Fargo would be W<complex string>F or similar variations.
- Default passwords on infrastructure—both enterprise and home—should be changed immediately. At home this means routers, modems, cameras, home automation systems, and wireless access points. In the enterprise this includes infrastructure like routers and switches or operational applications used by administrators to manage application infrastructure. (In 90s, SSH to routers using default admin settings was a common hack.)
- Use different browsers for financial, business, and recreational activities to minimize compromise by MITBs (Man in the Browser). Change your settings to clear your cache and cookies on exit and make it a habit to close out your browser every time you log out.
As the pandemic continues to reshape the way we interact with each other and organizations, the number of applications and accounts we rely on will continue to be an attractive opportunity for attackers. The reality is you cannot prevent any attack. You have no control over the actions of bad actors. But you can take steps to prevent a successful attack.
For additional background on credential stuffing, check out The Credential Crisis: It’s Really Happening from F5 Labs.
About the Author
Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.