Connect and Protect Your Digital Business
Innovative apps are essential for organizations that want to be first to market, first to differentiate, and first to profit. Automation is the catalyst that helps organizations facilitate this application revolution across technology, process, and people. Unfortunately, attackers also have embraced automation, using it to attack and abuse web apps and APIs. Readily available tools, infrastructure, and compromised data make these attacks cheap to carry out and highly profitable, creating high-value attacker economics. Criminals even have their own digital fingerprint darknet store .
Skilled attackers are motivated by profit. They continually assess which targets will provide the highest return on their investments.
“Skilled attackers are motivated by profit. They continually assess which targets will provide the highest return on their investments.”
Attacks are easy to implement, and their potential value is astronomical. As digital transformation and the use of apps and APIs to facilitate online commerce continues to skyrocket, attackers will embrace automation and AI to overcome the security countermeasures that stand in their way.
Commonly used mitigations such as CAPTCHA and multi-factor authentication (MFA) are designed to deter bots, but they often frustrate customers while failing to provide the security they’re meant to deliver, in some cases even causing transaction and brand abandonment. Motivated attackers can bypass these defenses; they merely provide a false sense of security, which can create a wide range of costly problems for organizations that rely on them.
Want proof? One in three customers will leave a brand they love after just one bad experience.
“One in three customers will leave a brand they love after just one bad experience.”
Key Benefits
Unparalleled visibility
F5 powers more than half of the world’s applications across all types of environments, protects over 1 billion transactions daily from application attacks on the largest companies, and ensures the safety of more than 200 million legitimate human transactions every day.
Unwavering resilience
F5 solutions uniquely provide long-term, persistent efficacy through spoof-proof telemetry collection, highly trained AI, and best-in-class security operations.
Optimized customer experience
F5 solutions reduce or remove high-friction user authentication mechanisms, including CAPTCHA and multifactor authentication, thereby improving the customer experience.
Detecting Bots and Deterring Fraud and Abuse
Adapting to attacker economics
Automated attacks continue to evolve, enabling bad actors to adapt and bypass basic security defenses with very little investment. These attackers typically leverage readily available infrastructure, such as bots and toolkits, for pennies on the dollar.
The proliferation of architectures, cloud, and complex software supply chains has expanded the risk surface for attackers. Application vulnerabilities such as injection and cross-site scripting continue to exist, even after 20 years with established security best practices. It’s no surprise that attackers leverage bots and automation to scan for these vulnerabilities and exploit them—creating potentially disastrous outcomes, including data breach.
Increasingly, attackers are turning their attention to critical business logic that underpins organizations’ digital footprints—from customer shopping carts to the API fabrics that connect B2B commerce. Endpoints such as logon, create account, and add to cart are inundated with automated attacks, leading to account takeover, fraud, and lost customer trust. These attacks can happen both on web apps and back-end API infrastructure. Attackers perform reconnaissance and retool to identify their targets and evade detection.

A successful attack can result in several business problems with serious impacts:
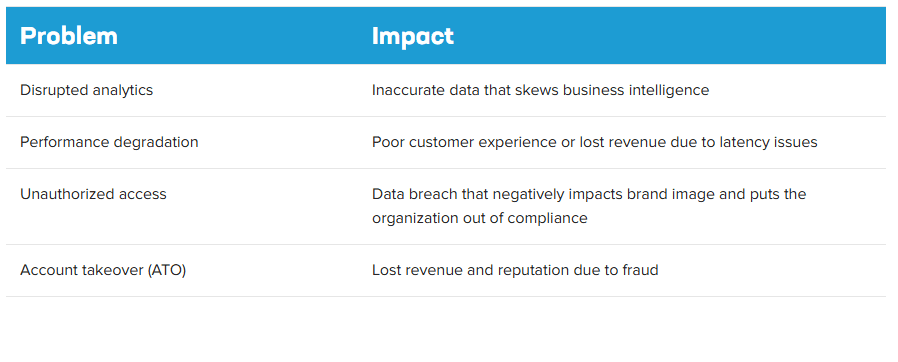
Bots are commonly used for commercial and retail fraud. Attacks vary in sophistication and often adapt to security countermeasures. For example:
- Automation that leverages bots to scan for application vulnerabilities
- Credential stuffing that uses compromised credentials and tools to commit account takeover
- Imitation attacks that employ tools that emulate human behavior to bypass anti-automation defenses
- Manual attacks that leverage human click-farms, fingerprints, or real-time phishing proxies to evade detection
Attackers invest along four vectors—often simultaneously—until they get past whatever defenses an organization may have:
- Emulating valid network traffic
- Spoofing a variety of valid devices and browsers
- Mimicking actual human behavior
- Using stolen credentials, tokens, and personally identifiable information

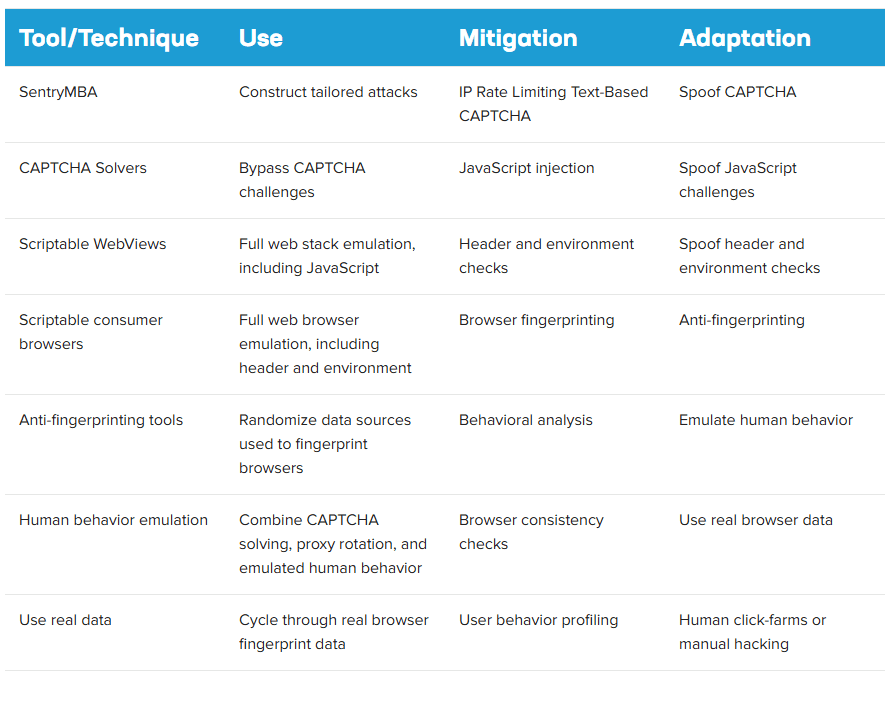
An attack may use a variety of tools to adapt to and bypass mitigation countermeasures:

Key Features
Deployment Flexibility
Insertion points through application proxies, application platforms, and content delivery networks quickly protect all critical business logic
Universal Visibility
Visibility across clouds and architectures provides machine learning models with real-world training data, rendering solutions tuned to actual threats.
Continuous Protection
Real-time threat intelligence, AI-based retrospective analysis, and continuous SOC monitoring provides resilience to thwart the most advanced cybercriminals and state actors.
Proven Efficacy
Battle-tested defenses deter credential stuffing across the Fortune 500.
Highest Impact
Accurate and adaptive security slashes bottom-line losses and improves top-line potential by deterring fraud and abuse—without inserting friction into the customer journey.
Granular Control
Flexible policies to manage aggregators and prevent attacks through third-party integrations.
Neutralize attackers by detecting bots and mitigating fraud and abuse
Your customers demand simplicity. Your applications are complex. Your attackers are motivated.
Security must adapt to attacker retooling that attempts to bypass countermeasures—regardless of the attackers’ tools, techniques, or intent—without frustrating users with login prompts, CAPTCHA, and MFA. This includes omnichannel protection for web applications, mobile applications and API interfaces, real-time threat intelligence, and retrospective analysis driven by AI.
Visibility across clouds and architectures, durable and obfuscated telemetry, coupled with a collective defense network and highly trained machine learning models provides unparalleled accuracy to detect and unwavering resilience to deter bots, automated attacks, and fraud. This allows mitigations to maintain full efficacy as attackers retool and adapt to countermeasures—stopping even the most advanced cybercriminals and state actors without frustrating your real customers.
This ability to maintain effectiveness dramatically improves key business outcomes:
- Less fraud, less friction, less effort
- Improved conversion, retention, and loyalty
- Increased top-line revenue
- Decreased bottom-line losses
- Reduced complexity
- Increased operational efficiencies
“Bots are commonly used for commercial and retail fraud.”
Bot Detection and Security to Stop Automated Attacks
Security vendors must operate under the assumption that skilled attackers already have or soon will bypass all defenses. Attacker frameworks are known to leverage trained AI models (https://community.f5.com/t5/technical-articles/how-attacks-evolve-from-bots-to-fraud-part-1/ta-p/286685) to bypass security. The only viable defense is deterrence, disrupting attacker economics by making successful attacks too costly and unfeasible.
F5 solutions connect into any application architecture and protect all critical business logic, maintaining persistent, long-standing efficacy no matter how attackers retool in their efforts to evade detection. F5 solutions also reduce or remove high-friction security controls, including CAPTCHA and MFA, thereby improving the customer experience and overall solution effectiveness.
