A Ascensão dos Bots (Perguntas e Respostas de Dan Woods Parte 2)
Desde propagar mentiras e manipular usuários de mídia social até interromper negócios globais, os bots são um tópico cada vez mais quente.
Na segunda parte da nossa sessão de perguntas e respostas com Dan Woods, chefe global de inteligência da F5, exploramos o que os bots fazem, os riscos dos quais é preciso estar ciente e como as organizações podem se adaptar às ameaças em evolução. ( Link para a primeira parte )
O que são bots e por que eles são potencialmente perigosos?
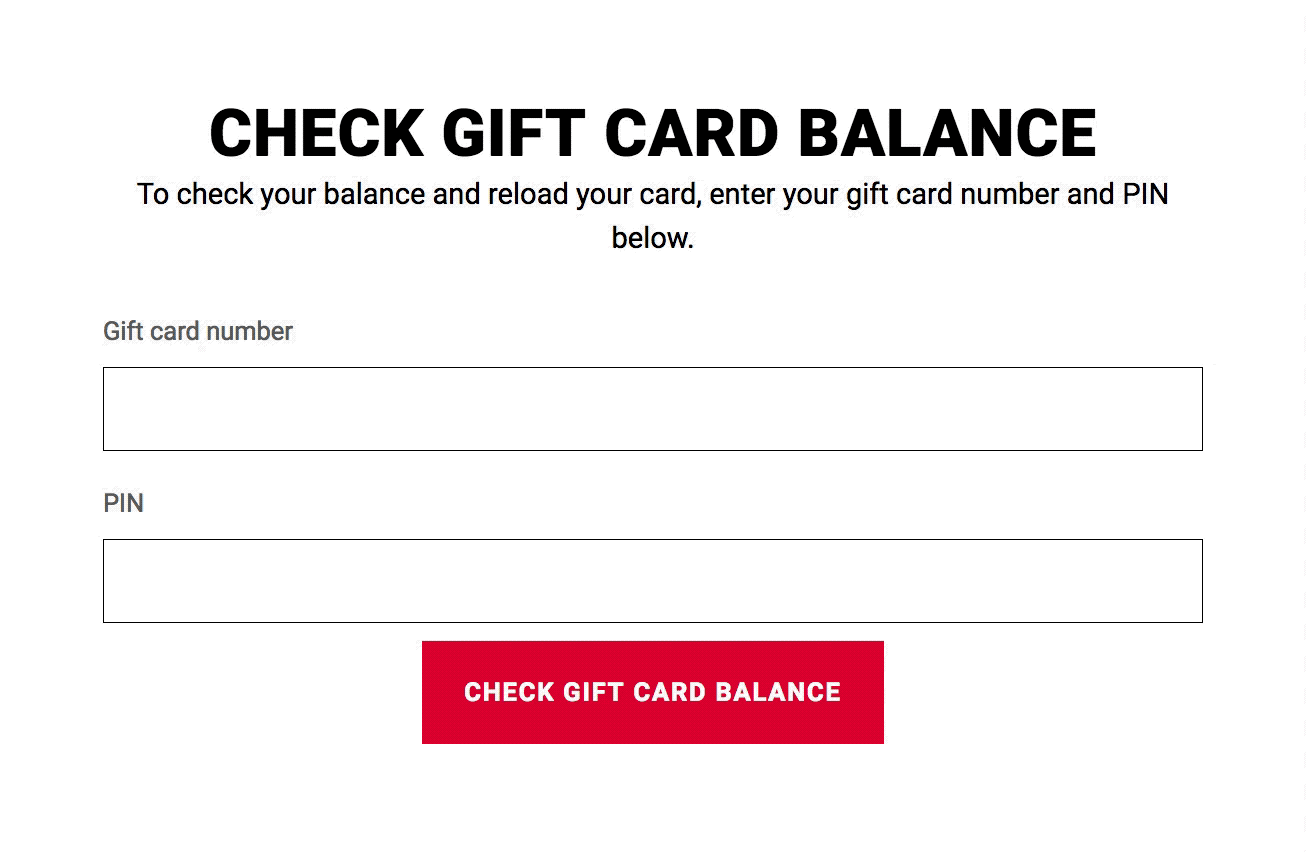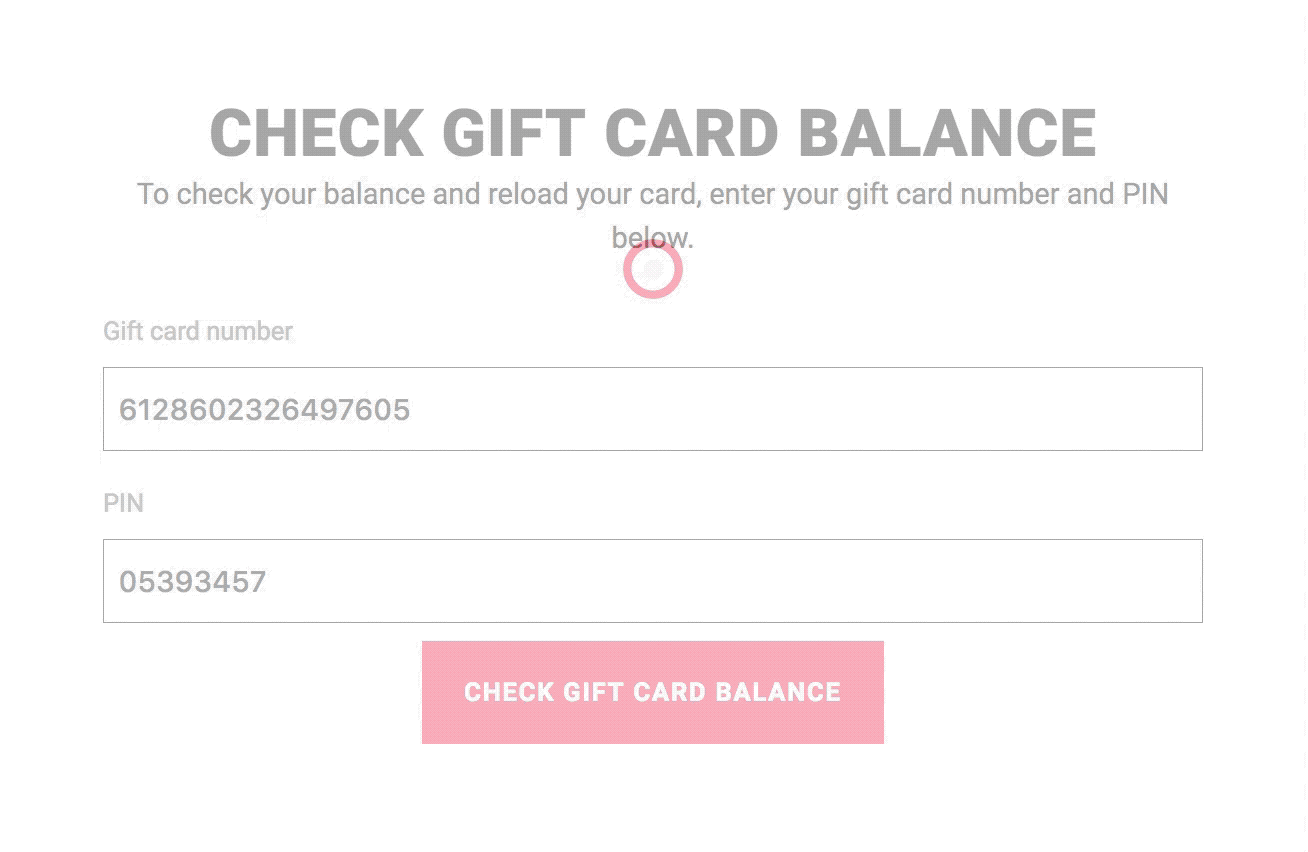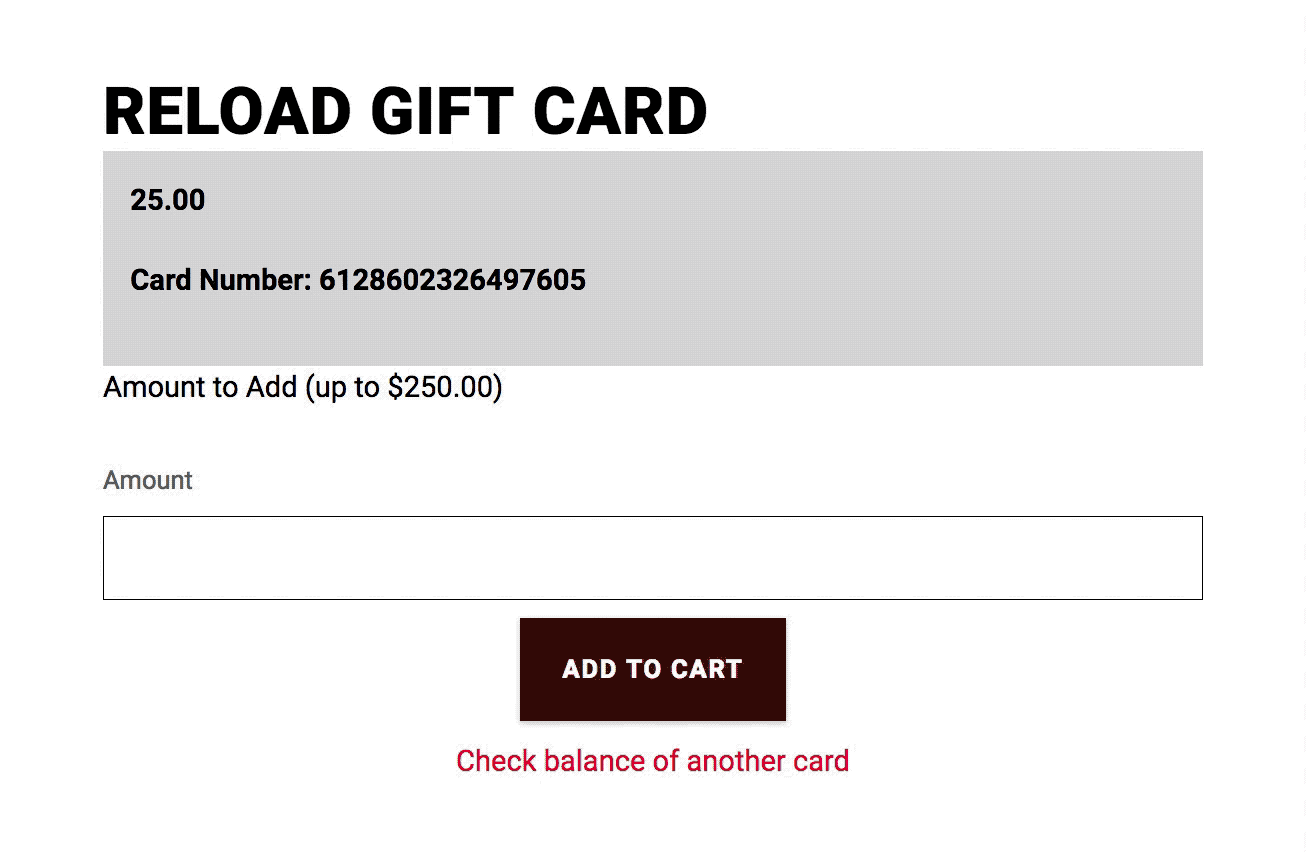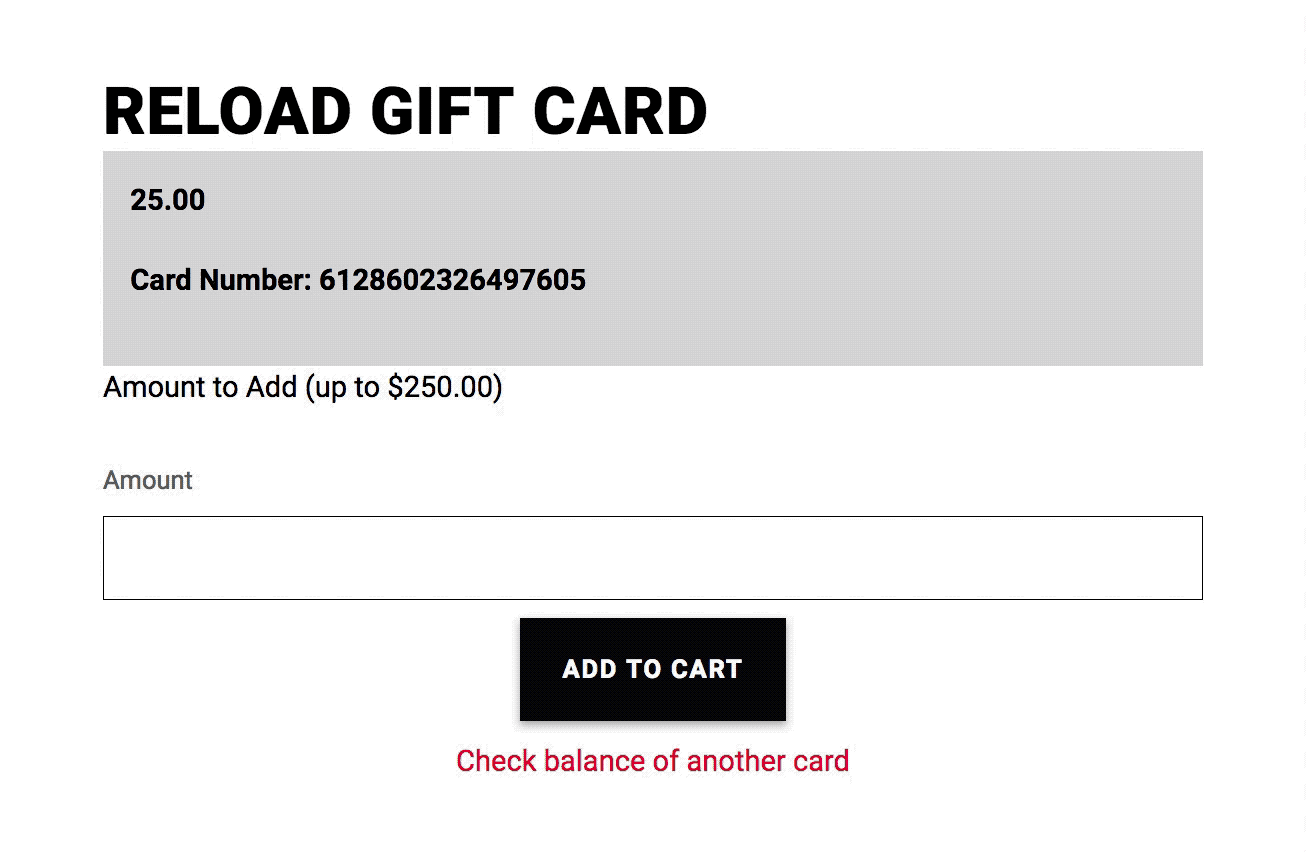
Bots são trechos de código que automatizam tarefas. Verificar o saldo de cartões-presente é um exemplo disso.
Por que alguém faria isso? Bem, tudo o que um criminoso precisa para roubar o valor armazenado em um cartão-presente é o número do cartão de 16 dígitos e o PIN. Eles poderiam usar uma versão modificada do bot acima para verificar o saldo de milhões, até bilhões, de pares de números de cartão e PIN. Quando encontram um par de número de cartão e PIN com saldo, eles podem vendê-lo a terceiros. O verdadeiro dono do cartão-presente nem perceberá que o saldo foi roubado até tentar usá-lo.
Bots também estão sendo usados para vasculhar sites de seguradoras. Se você quiser uma cotação de seguro de vida, precisará passar por um processo que pergunta sua idade, onde você mora, o que você faz para viver, etc. Concorrentes e terceiros podem usar um bot para navegar no mesmo fluxo de trabalho, cada vez fornecendo respostas diferentes. Isso permite que eles façam engenharia reversa no algoritmo de preços da seguradora.
Um dos maiores problemas é o uso de bots maliciosos para testar nomes de usuários e senhas vazados — da dark web ou de um comprometimento em alguma empresa — no aplicativo de login de outras empresas. Devido aos hábitos dos consumidores de reutilizar nomes de usuários e senhas, esses ataques geralmente afetam de 0,1% a 3% das contas tentadas. Então, quando um criminoso tenta centenas de milhões de pares de nome de usuário/senha, ele acaba comprometendo dezenas de milhões de contas.
Outros exemplos disruptivos incluem um bot comprando muitos tênis em oferta por tempo limitado ou ingressos para shows 30 segundos após o início da promoção e depois revendendo-os por preços inflacionados no mercado secundário. Ou, se uma empresa oferece algo de valor pela abertura de uma conta online, como uma xícara de café grátis, um bot pode criar milhares de contas para aproveitar milhares de xícaras de café grátis. Ou talvez uma organização criminosa precise de muitas contas online para se envolver em lavagem de dinheiro.
Todos os bots são ruins?
Nem todos os bots são ruins. Por exemplo, o Googlebot coleta e indexa bilhões de sites para possibilitar pesquisas. O Kayak e outros agentes de viagens on-line cobram tarifas aéreas e de hotéis de muitas empresas de viagens para oferecer as melhores ofertas aos seus clientes.
E quanto ao impacto dos bots nas empresas de mídia social?
Alguns anos atrás, uma empresa de mídia social contratou a F5 para entender melhor os bots que estavam ativos em seus aplicativos web e móveis. Quando implementamos nossos sinais do lado do cliente (os sinais que nos ajudam a identificar bots), determinamos que mais de 90% de todos os logins eram relacionados a bots. Com base na alta taxa de sucesso de login e nas discussões com o cliente, essas contas foram associadas a golpes de golpistas . Infelizmente, algumas empresas de mídia social não estão interessadas em saber a verdade sobre o tráfego de seus bots porque a verdade teria um impacto negativo em seu DAU e no preço/avaliação de suas ações.
Como os bots podem influenciar a opinião pública e manipular usuários de mídias sociais?
Imagine a influência que um criminoso poderia exercer se tivesse controle programático sobre milhões de contas do Twitter, TikTok, Facebook ou Instagram? Para começar, eles poderiam amplificar um volume significativo de notícias e conteúdo para influenciar a opinião pública.
Nos últimos seis a sete anos, sempre que vi um incentivo, um meio e a falta de uma contramedida significativa antes de entrar na fila, sempre observei a automação que esperava depois de entrar na fila. Não tenho dúvidas de que atores políticos e estatais estão usando plataformas de mídia social para influenciar a opinião pública e até mesmo eleições.
Todo mundo é impressionável. Alguns mais que outros. Se um comediante conta uma piada e você não ri, mas todos os outros riem, você pode começar a acreditar que a piada era realmente engraçada. É por isso que os seriados de comédia usam risadas gravadas. Quanto mais impressionável alguém for, maior a probabilidade de mudar de opinião com base na pressão dos colegas, mesmo que esses colegas sejam, na verdade, robôs.
Por que as empresas subestimam o problema dos bots?
Muitos bots aumentam as perdas devido a fraudes. Mas os danos não param por aí: dependendo do volume de bots, também pode aumentar os custos associados a CDNs ou ferramentas de fraude que cobram com base no número de transações. Além disso, eles podem impactar negativamente a latência e prejudicar a experiência do usuário para clientes legítimos. As métricas distorcidas também podem influenciar negativamente os gastos corporativos e a tomada de decisões.
A maioria das empresas quer saber a verdade. Aqueles que se envolvem com o F5 descobrem a verdade, mas aqueles que tentam detectar bots como um projeto "faça você mesmo" quase sempre subestimam o tamanho do problema por alguns motivos.
Primeiro, os bots agora estão usando centenas de milhares, ou até milhões de endereços IP. As equipes de segurança geralmente conseguem identificar as centenas ou milhares de IPs mais ruidosos. No entanto, eles perdem a longa cauda de IPs que são usados pelo bot apenas algumas vezes. Em segundo lugar, os ataques de bots geralmente aparecem gradualmente ao longo do tempo, o que os torna mais difíceis de reconhecer e não confundir com crescimento orgânico. Depois de trabalhar com a F5, as organizações geralmente acham os resultados chocantes e inacreditáveis, mas rapidamente passam a acreditar quando veem os dados.
O que as organizações devem fazer para reduzir o problema de bots em seus sites?
Duas coisas: eles devem coletar sinais do lado do cliente (do usuário, do agente do usuário, do dispositivo e da rede) e devem ter dois estágios de defesa.
Exemplos de sinais do lado do cliente incluem o tempo de pressionamento de teclas e cliques/movimentos do mouse, plugins, fontes, utilização da tela, número de núcleos, como o agente do usuário executa cálculos de ponto flutuante ou renderiza emojis e dezenas de outros.
Você não precisa de centenas ou milhares de sinais. Você só precisa de algumas dezenas de sinais de alta qualidade que são muito difíceis de falsificar. Esses sinais são normalmente coletados usando JavaScript em navegadores da web e móveis e usando um SDK, instalado junto com o aplicativo nativo. Quando os invasores são mitigados na web, eles farão a transição para atacar a API móvel. O JavaScript e o SDK também devem ser bem reforçados para tornar a engenharia reversa extremamente difícil.
Agora vamos analisar os dois estágios da defesa.
O primeiro estágio é quase em tempo real (abaixo de 10 ms) e aproveita os sinais associados a uma única transação. Se os sinais indicarem que é um bot indesejado, tome medidas de mitigação. Se os sinais indicarem que a transação é de um humano, passe-a para a origem para processamento normal. Embora esse primeiro estágio identifique quase todos os bots, ele não é capaz de acompanhar as reformulações (quando um invasor percebe que seu ataque está sendo mitigado e decide melhorar seu bot para superar a contramedida).
Retools são a razão pela qual as organizações precisam de um segundo estágio de defesa. Enquanto o primeiro é quase em tempo real, o segundo estágio é retrospectivo. É onde os modelos de IA/ML operam em transações agregadas (todas as transações que chegaram nos últimos 30 segundos, minuto, hora, dia, alguns dias, etc.). Mesmo assim, as organizações não podem depender exclusivamente de IA/ML para encontrar reequipamentos. Eles devem ter humanos revisando os alertas disparados pelos sistemas de IA/ML para eliminar falsos positivos. E certifique-se de que os modelos de IA/ML estejam aprendendo corretamente. Quando as organizações encontram tráfego de bot indesejado no segundo estágio, elas também devem ser capazes de atualizar as defesas em tempo real para mitigar o tráfego de bot recém-descoberto sem afetar o tráfego de clientes legítimos.
A F5 fornece ambos os estágios de defesa, a IA/ML e os humanos, como um serviço gerenciado. Lutar contra bots nunca deve ser um projeto "faça você mesmo".
A ameaça dos bots vai piorar?
É impossível quantificar, mas o problema dos bots certamente aumentou nos últimos seis a sete anos. Durante esse tempo, vi bots maliciosos e incômodos lançarem automação contra empresas em praticamente todos os setores. Quando penso que já vi todos os casos de uso, surge um novo. Tirar os olhos da bola nunca é uma opção!