Another month has passed, which means more sensor telemetry to analyze for attacker targeting trends. October’s data is notable primarily because we detected attackers looking for a handful of interesting vulnerabilities that were recently released or discovered, most notably CVE-2022-41040, one of the Microsoft Exchange zero day vulnerabilities that attackers began to exploit in August 2022,1 as well as CVE-2022-40684, a recent authentication bypass vulnerability on several Fortinet appliances.2
At the same time, most of the targeting traffic we observed was going after the same old standard targets, so let’s dig in and see what’s new and what’s old.
October Vulnerabilities By the Numbers
Figure 1 shows the volume of traffic targeting the top 10 vulnerabilities in October, and it’s largely the same cast of characters we’ve observed since January 2022. After a dip from its high point in July, CVE-2020-8958 grew 60% in frequency from September to October. CVE-2017-9841 continued to trend downwards in frequency, both in absolute as well as in relative terms.
CVE-2018-13379 was a newcomer to our logs last month, and despite its presence in the second spot this month, October traffic targeting it actually increased by 16% compared with September. We suspect that the increased attention on Fortinet systems in general reminded threat actors about this vulnerability.
Table 1 shows the traffic for all of the vulnerabilities that were targeted in October, along with the change in traffic from the previous month. We noted the presence of traffic targeting another interesting vulnerability without a CVE number, which we’ve dubbed “Citrix XML Buffer Overflow.”3 We also noted large changes across the board, such as CVE-2020-25078, which grew nearly ninefold in prevalence from the previous month. Dramatic changes such as this without any obvious explanation illustrate that predicting attacker attention is very difficult except for a small number of high-value indicators.4
| CVE Number | Count | Change |
| CVE-2020-8958 | 3775 | 1421 |
| CVE-2018-13379 | 3452 | 472 |
| CVE-2020-25078 | 2738 | 2433 |
| CVE-2017-9841 | 2449 | -214 |
| CVE-2022-22947 | 1953 | -257 |
| CVE-2021-28481 | 1378 | -414 |
| 2018 JAWS Web Server Vuln | 1256 | -1474 |
| CVE-2018-10561 | 952 | -392 |
| CVE-2021-3129 | 574 | -49 |
| CVE-2019-9082 | 519 | -140 |
| CVE-2017-18368 | 490 | -159 |
| CVE-2022-22965 | 353 | 349 |
| NETGEAR-MOZI | 353 | -113 |
| CVE-2020-15505 | 301 | 80 |
| CVE-2022-40684 | 296 | 296 |
| CVE-2013-6397 | 279 | 41 |
| CVE-2019-18935 | 241 | -19 |
| CVE-2019-12725 | 227 | 24 |
| Citrix XML Buffer Overflow | 197 | 3 |
| CVE-2021-40539 | 197 | -29 |
| CVE-2021-44228 | 177 | 52 |
| CVE-2021-26086 | 138 | -200 |
| CVE-2019-9670 | 114 | -54 |
| CVE-2021-41277 | 68 | -20 |
| CVE-2021-29203 | 49 | 45 |
| CVE-2021-22986 | 44 | -58 |
| CVE-2021-21315 | 44 | 41 |
| CVE-2020-3452 | 17 | 12 |
| CVE-2022-41040 | 12 | 12 |
| CVE-2020-9757 | 6 | 4 |
| CVE-2018-7600 | 4 | -6 |
| CVE-2018-1000600 | 2 | 0 |
| CVE-2022-1388 | 1 | -5 |
| CVE-2018-7700 | 1 | -1 |
| CVE-2021-33357 | 1 | -1 |
| CVE-2021-3577 | 1 | -1 |
| CVE-2022-25369 | 1 | -1 |
Table 1. CVE targeting volume for October, along with traffic change from September.
Targeting Trends
To understand how attacker targeting in October contrasted with the rest of 2022, see Figure 2. Continuing the visualization approach that we began with August data, these eleven vulnerabilities represent the top 5 for each month, visualized across the entire period. While several vulnerabilities changed volume dramatically, Figure 2 really captures the magnitude of the change in CVE-2020-25078, an IoT vulnerability which spiked in July, only to lapse back into relative obscurity in the intervening time. In contrast, another IoT vulnerability we’ve discussed recently, the 2018 JAWS web server vulnerability affecting networked surveillance cameras, dropped in prevalence almost as dramatically as 2020-25078 grew. Most of the other vulnerabilities making up the overall top 11 remained more or less consistent in terms of attacker activity.
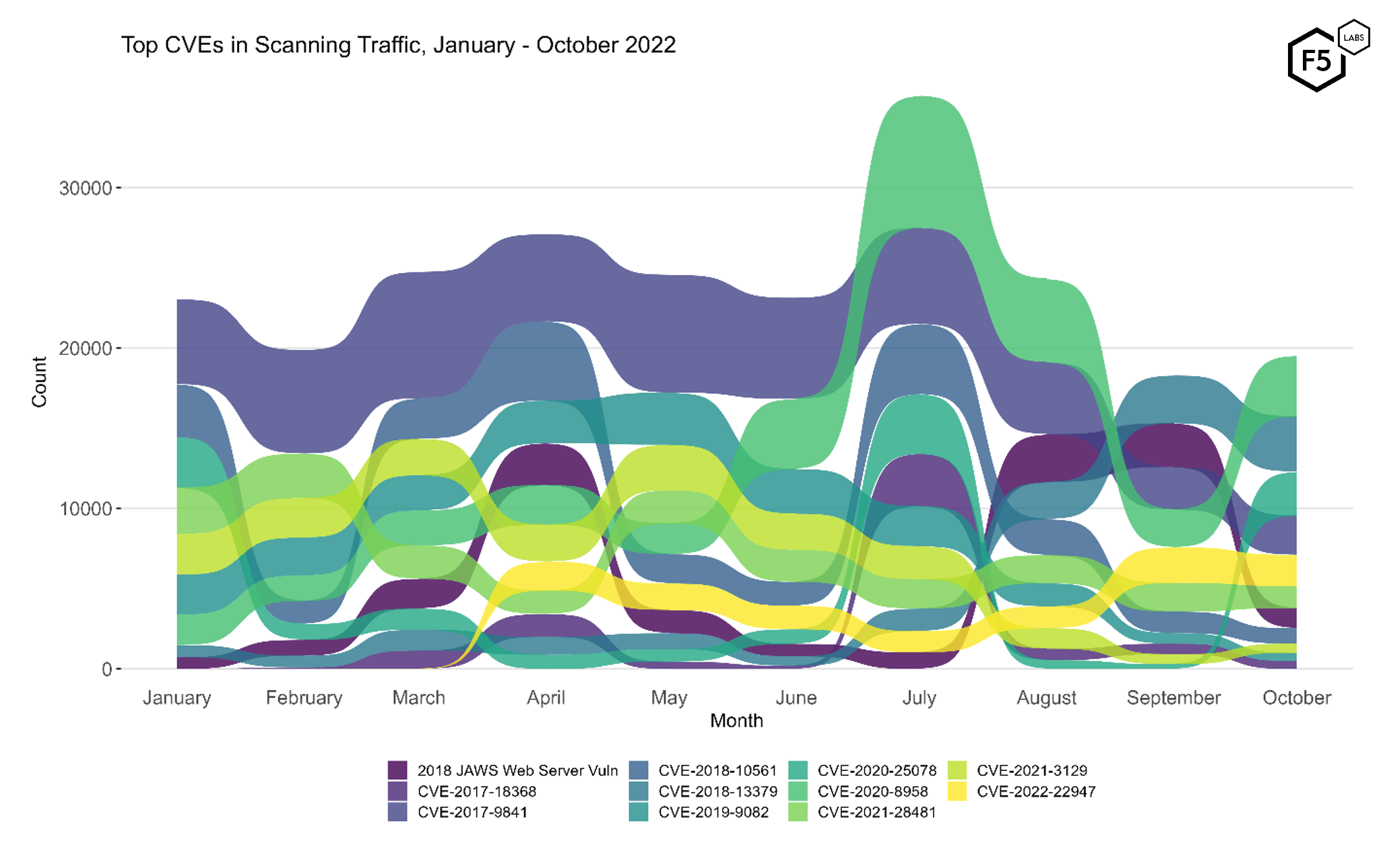
Figure 2. Evolution of vulnerability targeting, January-October 2022. The Fortinet credential disclosure vulnerability CVE-2018-13379 which was heavily targeted in September was superseded by the resurgence of CVE-2020-8958.
Identifying Rapid Growth
As we did for the September SIS, we’ve plotted the volume of traffic over time for all of the vulnerabilities we’ve been tracking. In addition to highlighting periods of dramatic change in attacker activity, this plot also shows vulnerabilities that we’ve just recently added, including the Microsoft Exchange zero day vulnerability CVE-2022-41040. Given that this was exploited in zero day attacks in mid-October, we’re relieved to see it only showing up in our logs in October and not before.
Also notable is the comparison between the two Fortinet vulnerabilities. While CVE-2018-13379 experienced roughly ten times the attention that CVE- 2022-40684 did, CVE-2022-40684 was only published on October 18. The amount of attention garnered in just the second half of October alone indicates that this is likely to continue to grow. We haven’t seen the last of this vulnerability.
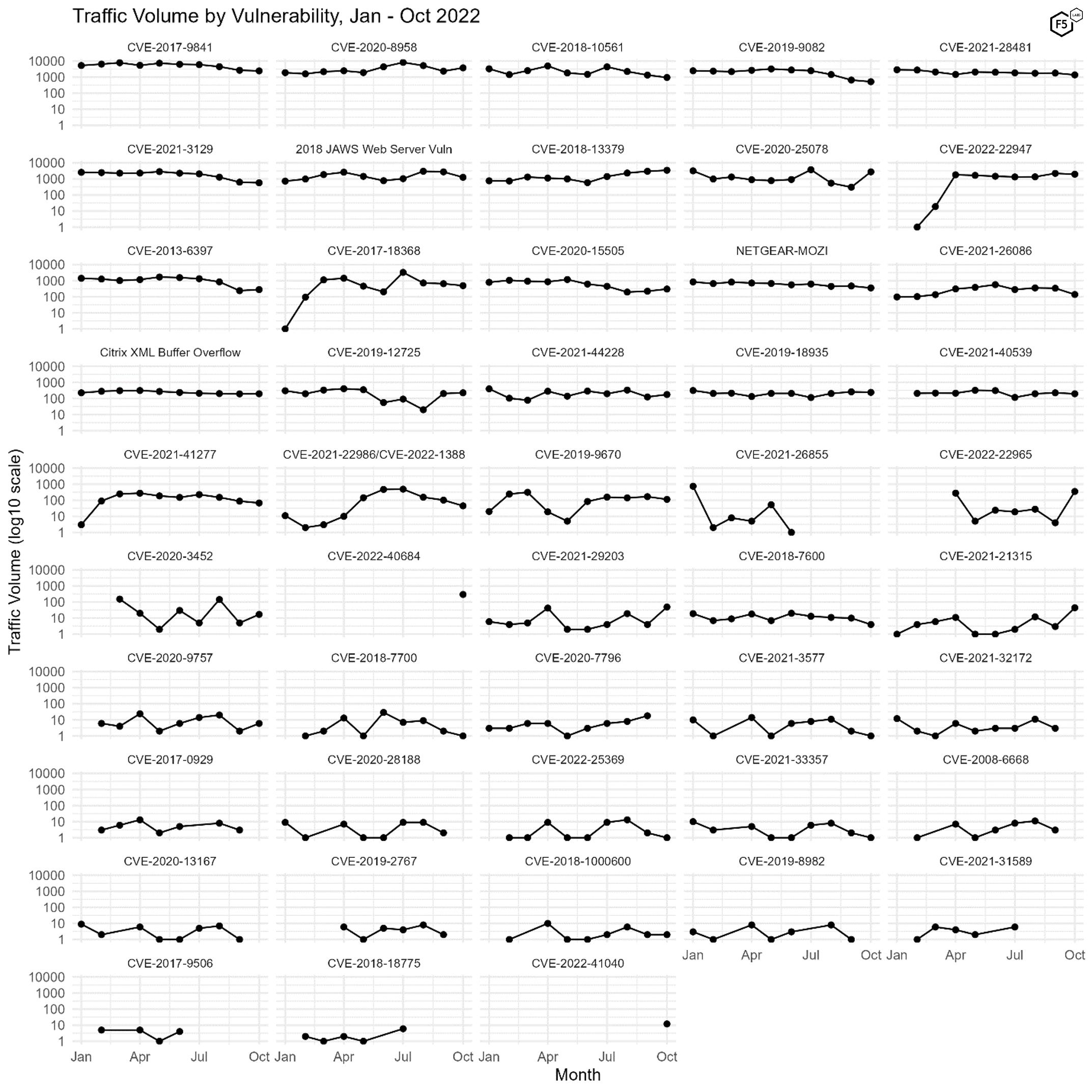
Figure 3. Plot of all 48 tracked CVEs over time. Note log10 scale on y axes.
Port Data
Most of our inquiry is focused on web traffic, but to get a sense of how traffic targeting ports 80 and 443 compares with other ports, Figure 4 shows the traffic volume and ranking for the top ten targeted ports from January to October of this year. Port 5900, which is usually used for Virtual Network Computing, has consistently been targeted more than any other port, and this remains a constant. In October, however, we did note that while the level of scanning for port 5900 remained roughly consistent from September, other ports dropped off sharply, and indeed the total number of events dropped by 25%.
The specific ports scanned remained constant, however, although the ranking changed; this is not unexpected, as we've noted in previous reports.
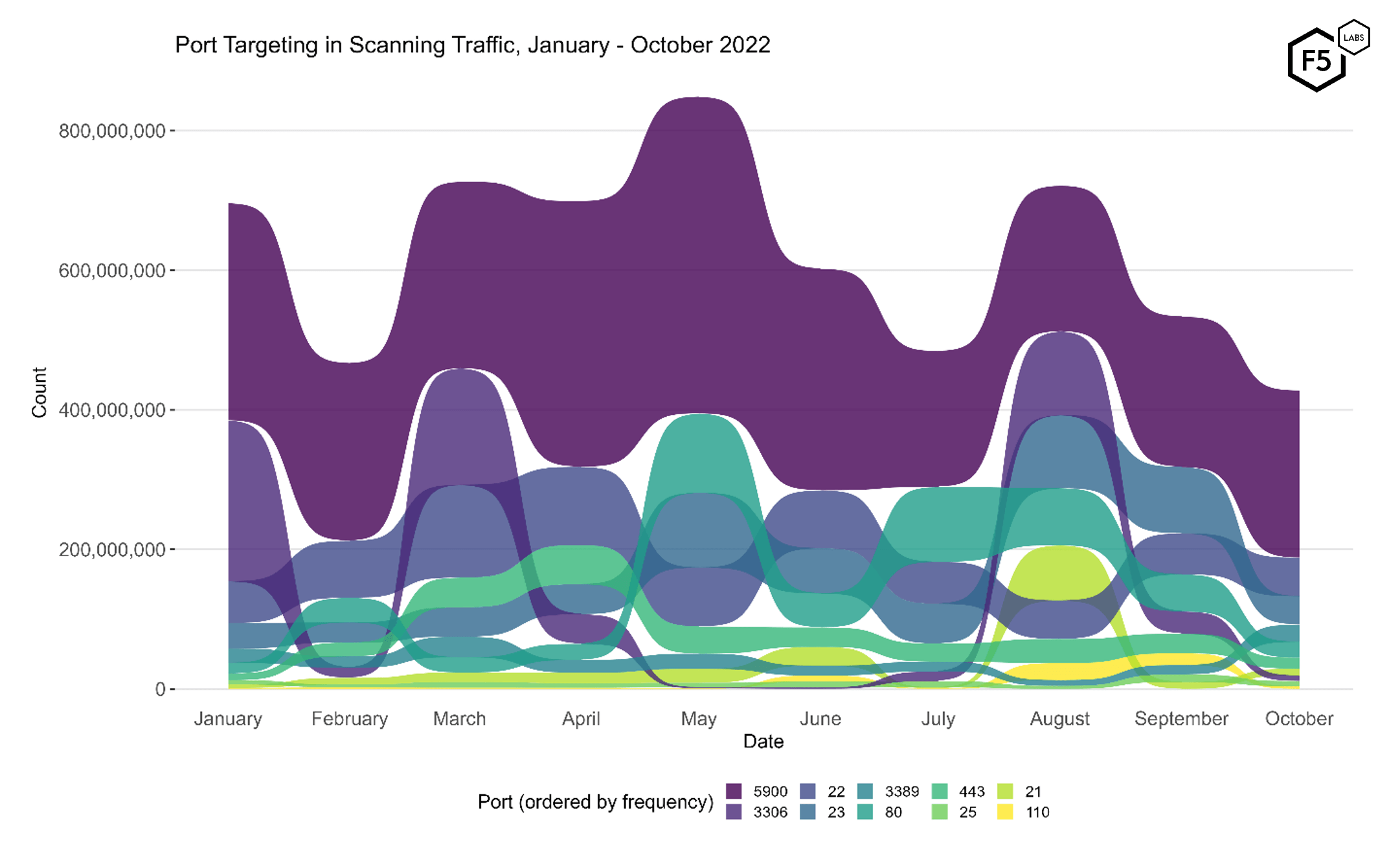
Figure 4. Port targeting in scanning traffic, January - October 2022. Port 5900 retains its crown as the top-targeted port, but other ports show significant change throughout the entire period.
| Port | % of total Connections | Typical Application |
| 5900 | 48.37% | VNC |
| 22 | 11.19% | SSH |
| 23 | 8.15% | Telnet |
| 3389 | 5.00% | RDP |
| 80 | 4.62% | HTTP |
| 443 | 3.17% | HTTPS/TLS |
| 21 | 2.00% | FTP |
| 3306 | 1.59% | Mysql/MariaDB |
| 25 | 1.49% | SMTP |
| 110 | 0.78% | POP3 |
Table 2. Traffic volume for top 10 ports in October.
Conclusions
As always, the most urgent and unequivocal recommendation from this data is to patch any vulnerabilities from this list that are extant in your systems. Even the vulnerabilities receiving only marginal interest in our logs can still be damaging.
In addition, the resurgence of several IoT vulnerabilities probably indicates that attackers are continuing to look for systems amenable to compromise for DDoS attacks. The previous two years have seen several record-breaking DDoS attacks, and DDoS is increasingly becoming part of the ransom playbook for many ransomware operators. In our estimation, organizations should take the presence of IoT targeting here as a leading indicator of DDoS risk.
Finally, the recent emergence of several zero-day or rapidly-exploited critical vulnerabilities indicates that while all of us can predict the occurrence of a paroxysmal security event, none of us can reliably predict what systems, and organizations, it will apply to. For this reason this is also a good opportunity to remind organizations to maintain up-to-date inventories, risk registers, and incident playbooks so that the preparatory work is already done when an incident occurs.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


