
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Introduction
Welcome to the January 2024 installment of the Sensor Intelligence Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data. This month’s attack data is superficially similar to recent months, with several of our “favorite” CVEs showing heavy targeting, but in fact we’ve made several changes under the hood. This month we tweaked our approach to threat hunting in the data and preemptively added several high-profile vulnerabilities to our detection list, including several CVEs that both have high EPSS scores and feature on CISA’s list of Known Exploited Vulnerabilities (KEV). Newly tracked vulns include:
- CVE-2019-2725, an injection vulnerability in Oracle WebLogic Server (CVSS 9.8, EPSS 97.6%).1
- CVE-2019-1653, an info exposure vulnerability in the web interface of certain Cisco routers (CVSS 7.5, EPSS 97.6%).2
- CVE-2014-6271, also known as Shellshock, an OS command injection vulnerability in Bash (CVSS 9.8, EPSS 97.6%).3
- CVE-2020-5902, a path traversal vulnerability in the F5 BIG-IP user interface (CVSS 9.8, EPSS 97.6%).4
- CVE-2015-1635, a code injection flaw in the HTTP.sys component of certain versions of Windows and Windows Server (CVSS 10, EPSS 97.5%).5
- CVE-2019-16057, an OS command injection vulnerability in the D-Link DNS-320 NAS (CVSS 9.8, EPSS 97.5%).6
- CVE-2017-5638, an improper input validation vulnerability in Apache Struts (CVSS 10, EPSS 97.5%).7
- CVE-2017-10271, a remote code execution flaw in Oracle WebLogic server (CVSS 7.5, EPSS 97.4%).8
Note that they all have EPSS scores above 97%. Despite the fact that we deliberately focused on adding signatures for prominent, high-risk CVEs, few of them showed a lot of recent traffic in our telemetry, which once again highlights the difference between the kind of opportunistic traffic we suspect we see on passive sensors and the more targeted attacks likely to show up in the KEV. Let’s get into this month’s top avenues of attack.
January Vulnerabilities by the Numbers
Figure 1 shows January attack traffic for the top ten CVEs that we track. Note the emergence of CVE-2020-11625 at the top. This vulnerability has shown some odd patterns, having the exact identical number of requests for November and December 2023, before jumping up 250% to nearly 5700 connections in January. This is a vulnerability in few different web-enabled video security cameras from brand AvertX. In other words, this is yet another IoT vulnerability, supporting the ongoing trend of IoT scanning and exploitation in our passive sensors.
Following CVE-2020-11625, we see a number of old favorites in the top ten. In terms of our sensor data, CVE-2020-8958 is the top-targeted CVE of all time and is still sitting in second place despite dropping in popularity since a high point in Summer 2023. We also spot a few Microsoft Exchange Server vulnerabilities; flaws in Laravel Ignition, Spring Cloud Gateway, and Geoserver; and a buffer overflow in the FortiOS and FortiProxy SSL-VPNs from Fortinet.
Leaving the top ten, Table 1 shows traffic volumes for all vulnerabilities that we’re tracking, along with change from the previous month, CVSS score, and EPSS score. This month we’ve gone back to including percent change in addition to the raw change. In terms of high-traffic CVEs, the percent change is usually more instructive. In terms of low-traffic CVEs where a fluctuation of a handful of connections makes for a change of hundreds of percent, raw traffic is more useful.
| CVE Number | January Traffic | Change from December | Percent Change | CVSS v3.x | EPSS Score |
| CVE-2020-11625 | 5670 | 4050 | 250% | 5.3 | 0.1% |
| CVE-2020-8958 | 2801 | 1410 | 101% | 7.2 | 74.2% |
| CVE-2022-24847 | 2451 | -66 | -3% | 7.2 | 0.1% |
| CVE-2017-9841 | 2055 | 625 | 44% | 9.8 | 97.5% |
| CVE-2022-22947 | 1623 | -508 | -24% | 10 | 97.5% |
| CVE-2022-42475 | 1207 | -30 | -2% | 9.8 | 38.8% |
| CVE-2022-41040/CVE-2021-34473 | 1058 | -123 | -10% | 9.8 | 97.1% |
| CVE-2021-3129 | 491 | 464 | 1719% | 9.8 | 97.5% |
| CVE-2020-0618 | 417 | -106 | -20% | 8.8 | 97.4% |
| CVE-2021-28481 | 390 | 108 | 38% | 9.8 | 4.2% |
| CVE-2014-2908 | 303 | 45 | 17% | NA | 0.6% |
| Citrix XML Buffer Overflow | 303 | 45 | 17% | NA | #N/A |
| CVE-2021-40539 | 270 | 3 | 1% | 9.8 | 97.4% |
| CVE-2022-35914 | 209 | 208 | 20800% | 9.8 | 96.9% |
| CVE-2021-26086 | 180 | 121 | 205% | 5.3 | 55.0% |
| CVE-2019-18935 | 176 | -1 | -1% | 9.8 | 94.6% |
| CVE-2017-1000226 | 175 | 152 | 661% | 5.3 | 0.1% |
| CVE-2021-26855 | 172 | 34 | 25% | 9.8 | 97.5% |
| CVE-2014-6271 | 171 | 156 | 1040% | 9.8 | 97.6% |
| CVE-2020-25078 | 117 | 32 | 38% | 7.5 | 80.7% |
| CVE-2021-44228 | 113 | 9 | 9% | 10 | 97.5% |
| CVE-2019-9670 | 101 | 98 | 3267% | 9.8 | 97.2% |
| CVE-2019-1653 | 95 | 3 | 3% | 7.5 | 97.6% |
| 2018 JAWS Web Server Vuln | 64 | -72 | -53% | NA | #N/A |
| CVE-2021-26084 | 55 | -25 | -31% | 9.8 | 97.2% |
| CVE-2013-6397 | 52 | 52 | NA | NA | 52.8% |
| CVE-2017-5638 | 41 | 40 | 4000% | 10 | 97.5% |
| CVE-2018-10561 | 37 | 8 | 28% | 9.8 | 97.2% |
| CVE-2019-9082 | 33 | 8 | 32% | 8.8 | 97.5% |
| CVE-2017-10271 | 31 | 22 | 244% | 7.5 | 97.4% |
| CVE-2019-12725 | 27 | 23 | 575% | 9.8 | 96.3% |
| NETGEAR-MOZI | 25 | 6 | 32% | NA | #N/A |
| CVE-2018-9995 | 24 | 11 | 85% | 9.8 | 90.0% |
| CVE-2017-18368 | 23 | -3 | -12% | 9.8 | 97.5% |
| CVE-2018-13379 | 23 | -23 | -50% | 9.8 | 97.3% |
| CVE-2022-22965 | 21 | 10 | 91% | 9.8 | 97.4% |
| CVE-2022-1388 | 19 | -9 | -32% | 9.8 | 97.3% |
| CVE-2020-5902 | 17 | 4 | 31% | 9.8 | 97.6% |
| CVE-2014-2321 | 15 | -4 | -21% | NA | 96.4% |
| CVE-2018-20062 | 13 | 8 | 160% | 9.8 | 96.8% |
| CVE-2018-7600 | 10 | 6 | 150% | 9.8 | 97.6% |
| CVE-2022-40684 | 10 | 2 | 25% | 9.8 | 96.0% |
| CVE-2014-6287 | 8 | 7 | 700% | 9.8 | 97.3% |
| CVE-2020-17496 | 8 | 1 | 14% | 9.8 | 97.5% |
| CVE-2022-26134 | 7 | -2 | -22% | 9.8 | 97.5% |
| CVE-2020-25213 | 6 | -9 | -60% | 9.8 | 97.4% |
| CVE-2020-7961 | 6 | 4 | 200% | 9.8 | 97.4% |
| CVE-2019-16057 | 5 | 4 | 400% | 9.8 | 97.5% |
| CVE-2021-23394 | 5 | 4 | 400% | 9.8 | 1.8% |
| CVE-2019-12987 | 4 | 3 | 300% | 9.8 | 97.3% |
| CVE-2019-12988 | 4 | 3 | 300% | 9.8 | 97.3% |
| CVE-2019-2725 | 4 | 2 | 100% | 9.8 | 97.6% |
| CVE-2020-13167 | 4 | 3 | 300% | 9.8 | 97.4% |
| CVE-2020-15505 | 4 | 3 | 300% | 9.8 | 97.5% |
| CVE-2020-17506 | 4 | 2 | 100% | 9.8 | 96.1% |
| CVE-2020-25506 | 4 | 2 | 100% | 9.8 | 97.4% |
| CVE-2020-3452 | 4 | -1 | -20% | 7.5 | 97.5% |
| CVE-2020-9757 | 4 | -5 | -56% | 9.8 | 96.8% |
| CVE-2021-29203 | 4 | 2 | 100% | 9.8 | 95.5% |
| CVE-2021-33564 | 4 | 2 | 100% | 9.8 | 9.3% |
| CVE-2015-8813 | 3 | 2 | 200% | 8.2 | 0.5% |
| CVE-2017-0929 | 3 | 2 | 200% | 7.5 | 0.8% |
| CVE-2017-17731 | 3 | 2 | 200% | 9.8 | 20.2% |
| CVE-2018-1000600 | 3 | 2 | 200% | 8.8 | 95.6% |
| CVE-2018-17246 | 3 | -1 | -25% | 9.8 | 96.6% |
| CVE-2019-2767 | 3 | 2 | 200% | 7.2 | 15.0% |
| CVE-2019-8982 | 3 | 2 | 200% | 9.8 | 2.5% |
| CVE-2020-28188 | 3 | 2 | 200% | 9.8 | 97.3% |
| CVE-2021-21985 | 3 | -1 | -25% | 9.8 | 97.4% |
| CVE-2021-32172 | 3 | 2 | 200% | 9.8 | 26.3% |
| CVE-2017-11511 | 2 | 1 | 100% | 7.5 | 33.2% |
| CVE-2017-11512 | 2 | 1 | 100% | 7.5 | 97.2% |
| CVE-2020-17505 | 2 | 1 | 100% | 8.8 | 96.5% |
| CVE-2020-7796 | 2 | 1 | 100% | 9.8 | 72.5% |
| CVE-2021-20167 | 2 | 1 | 100% | 8 | 94.8% |
| CVE-2021-21315 | 2 | 1 | 100% | 7.8 | 96.9% |
| CVE-2021-33357 | 2 | 1 | 100% | 9.8 | 96.7% |
| CVE-2022-1040 | 2 | 1 | 100% | 9.8 | 97.1% |
| CVE-2021-25369 | 1 | 0 | 0% | 6.2 | 0.1% |
| CVE-2021-3577 | 1 | 0 | 0% | 8.8 | 96.7% |
| CVE-2021-41277 | 1 | -1 | -50% | 10 | 5.8% |
| CVE-2022-21587 | 1 | -18 | -95% | 9.8 | 96.3% |
| CVE-2023-25157 | 1 | -1 | -50% | 9.8 | 49.1% |
| CVE-2007-3010 | 0 | 0 | 0% | NA | 97.3% |
| CVE-2008-2052 | 0 | -3 | -100% | NA | 0.2% |
| CVE-2008-6668 | 0 | -1 | -100% | NA | 0.4% |
| CVE-2012-4940 | 0 | -1 | -100% | NA | 16.4% |
| CVE-2014-8379 | 0 | 0 | 0% | NA | 0.1% |
| CVE-2014-9753 | 0 | 0 | 0% | 9.8 | 1.1% |
| CVE-2015-1635 | 0 | 0 | 0% | NA | 97.5% |
| CVE-2015-3897 | 0 | -2 | -100% | NA | 83.2% |
| CVE-2016-4945 | 0 | 0 | 0% | 6.1 | 0.2% |
| CVE-2017-9506 | 0 | -1 | -100% | 6.1 | 0.6% |
| CVE-2018-18775 | 0 | -1 | -100% | 6.1 | 0.2% |
| CVE-2018-7700 | 0 | -3 | -100% | 8.8 | 73.2% |
| CVE-2020-0688 | 0 | 0 | 0% | 8.8 | 97.2% |
| CVE-2021-27065 | 0 | 0 | 0% | 7.8 | 97.1% |
| CVE-2021-31589 | 0 | -1 | -100% | 6.1 | 0.3% |
| CVE-2022-42889 | 0 | 0 | 0% | 9.8 | 96.7% |
| CVE-2021-22986 | 0 | 0 | 0% | 9.8 | 97.4% |
Table 1. CVE targeting volumes for January, along with change from December. Here we see that CVE-2020-11625 grew 250% last month.
Targeting Trends
As you can see from Table 1, there has been some big change in terms of targeting volume lately, so to visualize some of these changes, Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. By coincidence (we presume), our current frontrunner, CVE-2020-11625, received exactly the same number of requests in November and December, though the change in rank makes it hard to spot in this plot. We also observe the progressive decline of CVE-2020-8958 from its high last June, only to rebound in January back to second. Also prominent is the drop in traffic for CVE-2016-4945 and CVE-2017-9841, although 2017-9841 has retained some interest whereas 2016-4945 has been untargeted since August.
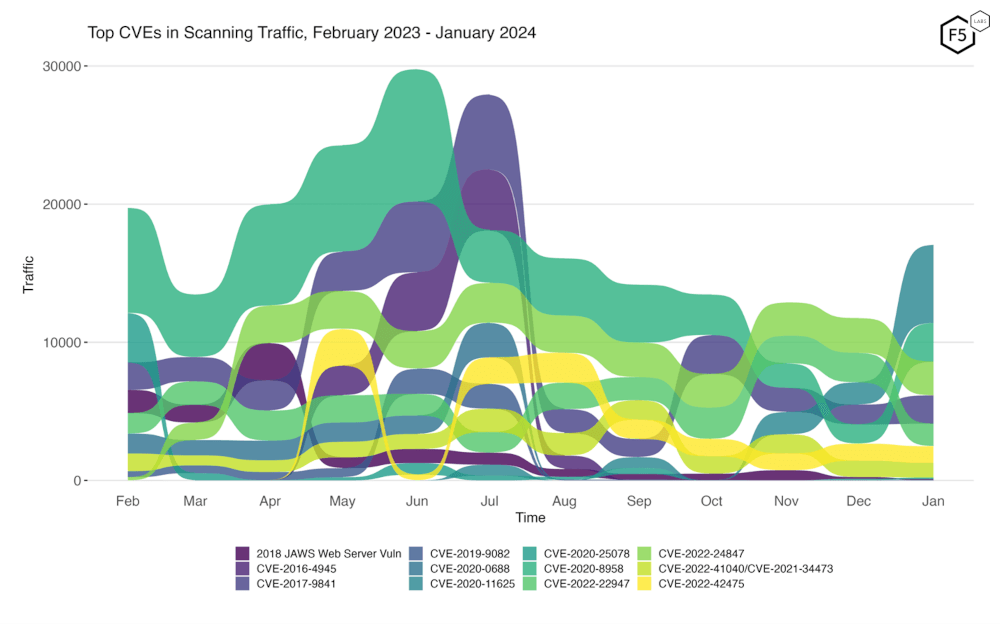
Figure 2. Evolution of vulnerability targeting in the last twelve months. Recent months have seen less dramatic change in this view than we observed in summer months.
Long Term Trends
Figure 3 shows traffic volume over the past year. If you’ve seen this series before, you’ll notice that Figure 3 looks different this time. Until now we have included plots of traffic for all of the CVEs we track, but since we track nearly 100 CVEs, this plot was getting a little congested, and many of the less popular vulns have minimal traffic anyway. What this figure shows now is traffic for the top 19 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs.
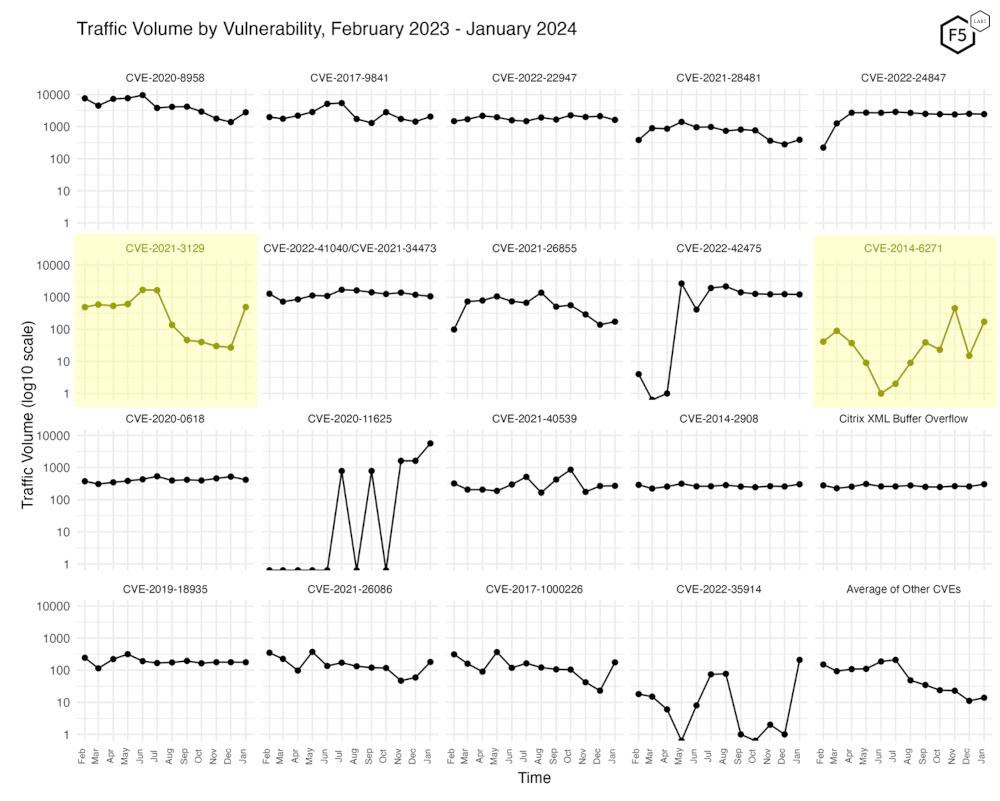
Figure 3. Traffic volume by vulnerability. This view accentuates the recent growth in CVE-2021-3129, which jumped up 1700% to the 8th most attacked CVE last month after languishing in obscurity for months.
This view is also notable since it is the first time we’re seeing any of these newly added, high-profile CVEs show up. Second row, far right is CVE-2014-6271, an OS command injection vulnerability more commonly known as Shellshock/Bashdoor. Shellshock shows more targeting variability from month to month than most CVEs (not including CVE-2020-11625, which has been all over the place). In the last year it has seen up to 450 attacks in a month, and as little as one request. Going back a little further, it received 5200 attacks in October 2022, and 3800 in August 2022, but has been all over the map before and since. As Shellshock is older than most of our tracked CVEs and is also extensively documented, we’re wondering how fruitful these relatively large-scale scans for it are in 2024. Do they know something we don’t?
Conclusions
Under the hood, this month’s installment marks a step forward in this series, as we’ve made several technical and procedural changes. We will continue adding new signatures for prominent CVEs even without evidence of heavy attention in our data, partly to look for interesting, low-lying trends and partly to continue exploring the similarities and differences between the attack traffic we observe and other sources. Documenting a low level of attacks is more useful in terms of information gain than none at all, in the sense that a value of zero and a null value have different significance. Plus, since the raw observations noted here also feed the EPSS vulnerability intelligence system, the more exhaustive we can be, the better it is for everyone.
On a more tactical note, we note once again the enduring popularity of IoT and Microsoft Exchange vulnerabilities. As IoT devices are often poorly managed and patched over time, particularly in terms of default admin credentials, these kinds of devices are useful for attackers to build out infrastructure for future attacks, including but not limited to DDoS. So patch those cameras, routers, and other IoT gear, not just for your own sake, but also for everyone else’s.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


