What Is MITRE ATT&CK®?
MITRE ATT&CK is a documented collection of information about the malicious behaviors advanced persistent threat (APT) groups have used at various stages in real-world cyberattacks. ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, includes detailed descriptions of these groups’ observed tactics (the technical objectives they’re trying to achieve), techniques (the methods they use), and procedures (specific implementations of techniques), commonly called TTPs.
Although MITRE ATT&CK is not a threat model per se (it doesn’t compare in a traditional sense to models like PASTA,1 STRIDE2 or OCTAVE3), it is often used as the foundation for organizations developing their own customized threat models. Think of it as an encyclopedic reference that describes TTPs adversaries use, provides suggestions for detection and common mitigations for specific techniques, and profiles APT groups’ known practices, characteristics, and specific attack attributions. ATT&CK also provides an extensive list of software used in attacks (both malware and commercially available and open-source code that can be used legitimately or maliciously). All information captured in ATT&CK comes from publicly available data and reports as well as from the community—threat researchers and security teams in the trenches experiencing or analyzing attacks daily.
Who Uses MITRE ATT&CK and Why
ATT&CK is a free tool that private and public sector organizations of all sizes and industries have widely adopted. Users include security defenders, penetration testers, red teams, and cyberthreat intelligence teams as well as any internal teams interested in building secure systems, applications, and services. The wealth of attack (and attacker) information it contains can help organizations determine whether they’re collecting the right data to effectively detect attacks and evaluate how well their current defenses are working.
Unlike other models written from a defender’s perspective, ATT&CK intentionally takes an attacker’s point of view to help organizations understand how adversaries approach, prepare for, and successfully execute attacks. This also makes ATT&CK an excellent resource and teaching tool for individuals interested in entering the field of cybersecurity or threat intelligence and those who simply want to understand more about attacker behavior.
Although the information captured in ATT&CK reflects known APT behaviors, it would be a mistake to assume those behaviors are the exclusive territory of APTs. As Ray Pompon, former CISO and current Director of F5 Labs warns, “What APTs are doing today, script kiddies will be doing tomorrow.” If you think your organization can’t benefit from ATT&CK because it’s not the target of APTs and will never experience APT-like attack behavior, think again. The TTPs outlined in ATT&CK happen every day in organizations of all sizes and significance. It’s not necessary to be the target of an APT to experience the same kinds of attacks or to use the ATT&CK tool to improve your defenses.
An Overview of the ATT&CK Framework
Attackers operate differently depending on their attack target. For example, they use different TTPs to compromise enterprise systems than they would to attack mobile devices or industrial control systems. MITRE provides three separate “matrices” to address these distinct environments. Together, these three matrices make up what MITRE collectively refers to as the ATT&CK framework.
The Enterprise matrix addresses platforms such as Windows, macOS, Linux, and others as well as something called “PRE,” which simply indicates actions taken pre-attack or in preparation for an attack. The Mobile matrix addresses both Android and iOS, and the ICS matrix addresses industrial control systems. Although the three matrices share some common tactics (Initial Access and Persistence, for example), the specific techniques for each tactic can vary by environment.
This article focuses primarily on the Enterprise matrix. At first glance, its sheer size and density can leave you wondering where to begin (see Figure 1).
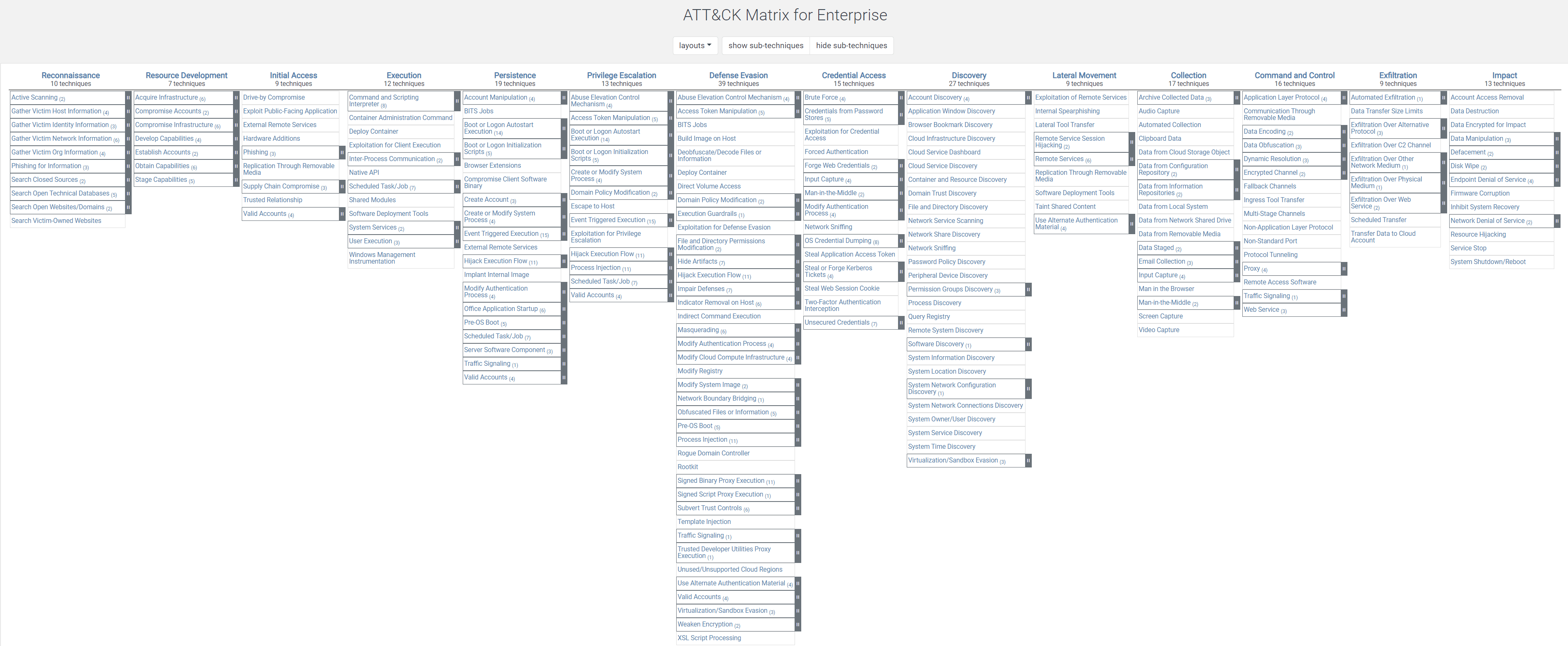
Figure 1. At first glance, the density of the Enterprise ATT&CK matrix can seem daunting.
The term matrix can also be somewhat misleading if you’re expecting rows that run the width of all columns like in a spreadsheet. Once you realize the 14 independent columns are structured more like individual organization charts (see Figure 2), the full matrix becomes far less daunting. Associated techniques and sub-techniques appear beneath each tactic.
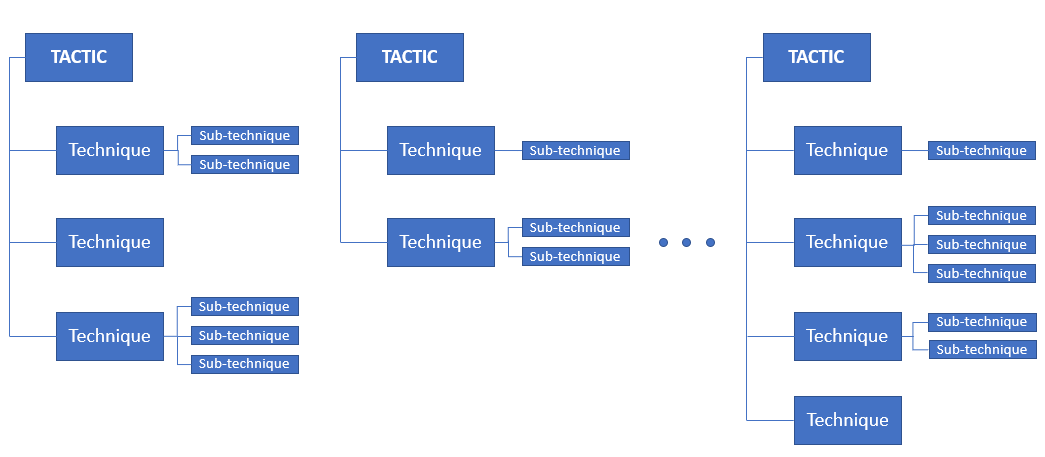
Figure 2. Columns in the ATT&CK Enterprise matrix represent distinct tactics, each with associated techniques and sub-techniques.
Key ATT&CK Terminology
Before we dig into the matrix, it’s important to understand how MITRE ATT&CK defines tactics, techniques, and procedures since these terms can have different meanings in other contexts.
- Tactics: Describes the immediate technical objectives (the “what”) attackers are trying to achieve, such as gaining Initial Access, maintaining Persistence, or establishing Command and Control. Invariably, attackers must use multiple tactics to successfully complete an attack.
- Techniques: Describes the “how”—the methods attackers use to achieve a tactic. All tactics in each matrix have multiple techniques; the Enterprise matrix breaks some techniques down further into sub-techniques. An example of this is the Phishing technique attackers use to gain Initial Access (a tactic). Phishing’s three associated sub-techniques are Spearphishing Attachment, Spearphishing Link, and Spearphishing via [a] Service.
- Procedures: Describes the specific implementations of that techniques and sub-techniques APTs have used (sometimes in clever or novel ways), or it can refer to specific malware or other tools attackers have used.
More about Tactics
The latest version (version 9) of the Enterprise ATT&CK matrix includes 14 tactics listed in a logical sequence, indicating the possible phases of an attack.4 They include:
- Reconnaissance: gathering information in preparation for an attack
- Resource Development: creating, buying, compromising, or stealing resources needed for an attack
- Initial Access: gaining access to the victim’s network or systems
- Execution: running malicious code on the compromised network or systems
- Persistence: maintaining access in that network or systems
- Privilege Escalation: attempting to gain higher-level privileges
- Defense Evasion: taking actions to avoid detection
- Credential access: attempting to steal account names and passwords
- Discovery: gathering information about the compromised environment
- Lateral Movement: moving from system to system within the compromised environment
- Collection: gathering data to support the high-level attack goal
- Command and Control: establishing control over systems in the victim’s network and/or communicating with compromised systems from outside the network
- Exfiltration: stealing the victim’s data
- Impact: damaging, destroying, or otherwise making networks, systems, and/or data unavailable to the victim
The leftmost column, Reconnaissance, reflects the fact that most attackers first perform some type of information gathering to determine which targets to pursue. The rightmost column, Impact, represents a later phase in which an attacker might, for example, destroy data or wipe disks. But not every attack uses all tactics, and not necessarily in the order presented. This is why MITRE ATT&CK is technically not considered a “cyberattack lifecycle” model, similar to Lockheed Martin’s decidedly sequential Cyber Kill Chain framework.5 Each attack has a unique set of circumstances, and the number of tactics and techniques and the order in which they’re used depends in part on an attacker’s high-level goal. The red arrows in Figure 3 illustrate how an actual attack might be mapped in ATT&CK version 9.6 Note that six of the 14 tactics—including Reconnaissance and Impact, just discussed—are not used in this scenario, and some techniques lead to the use of multiple techniques to achieve subsequent tactics.
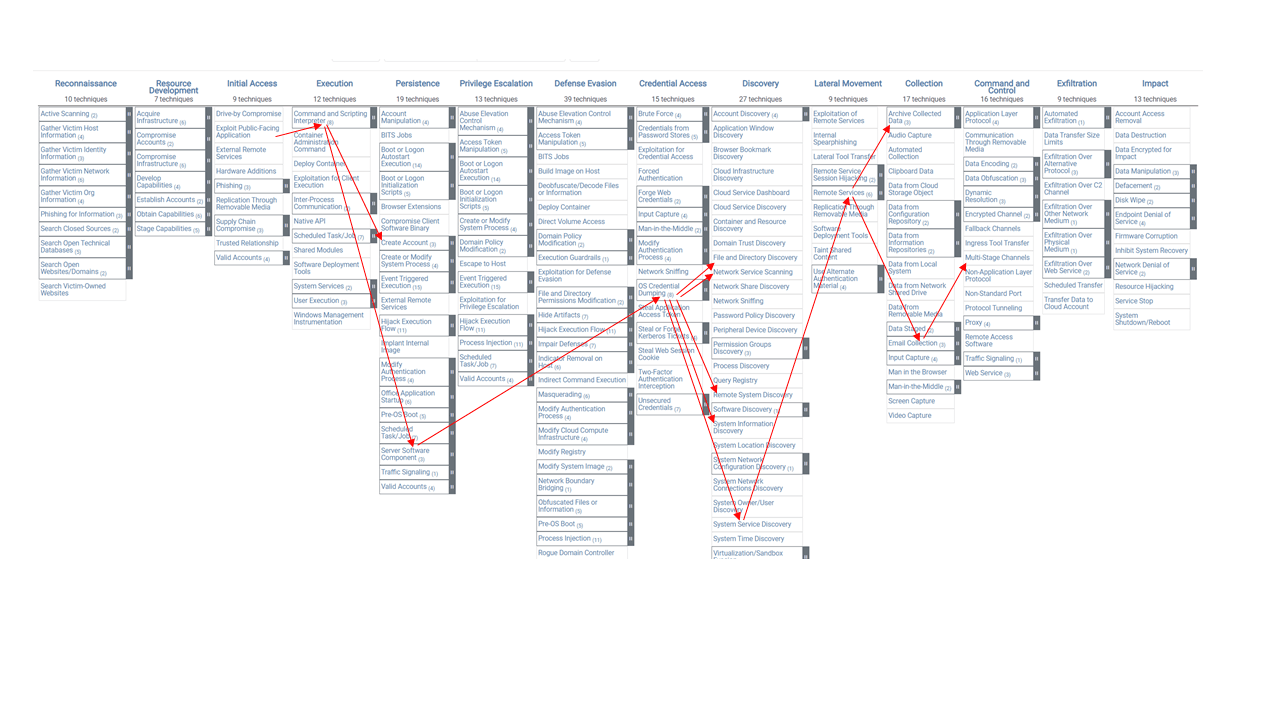
Figure 3. ATT&CK is not a sequential model; attackers choose whatever tactics and techniques enable them to accomplish their overarching goal.
What about Attackers’ Goals?
You might have noticed the ATT&CK matrices don’t address an attacker’s overarching goal, such as “get Company X to pay a ransom” (Enterprise), “brick a device” (Mobile), or “shut down a region’s electric grid” (ICS). It’s not possible to enumerate every attacker’s high-level goal, but even if it were, each goal could be achieved using many of the same tactics. Just as a burglar who wants to rob you might surveil your home, disable security cameras, pick a lock, and leave a window open to regain entry, a vandal whose goal instead is to damage and destroy your home could use any of the same tactics. Because the TTPs ATT&CK outlines can be used to achieve many different attack goals, the primary focus is understanding the TTPs attackers use and how to detect intrusions and mitigate them.
How to Use ATT&CK
The easiest way to learn about the ATT&CK matrix and see the depth of information it provides is to dive right in. Let’s start by zooming in on a partial view of the matrix introduced in Figure 1. Figure 4 shows the first three tactics in the Enterprise matrix: Reconnaissance, Resource Development, and Initial Access, with Techniques listed beneath each tactic. Entries with a gray bar on the right have sub-techniques, the number of which appears in parentheses following each technique name.
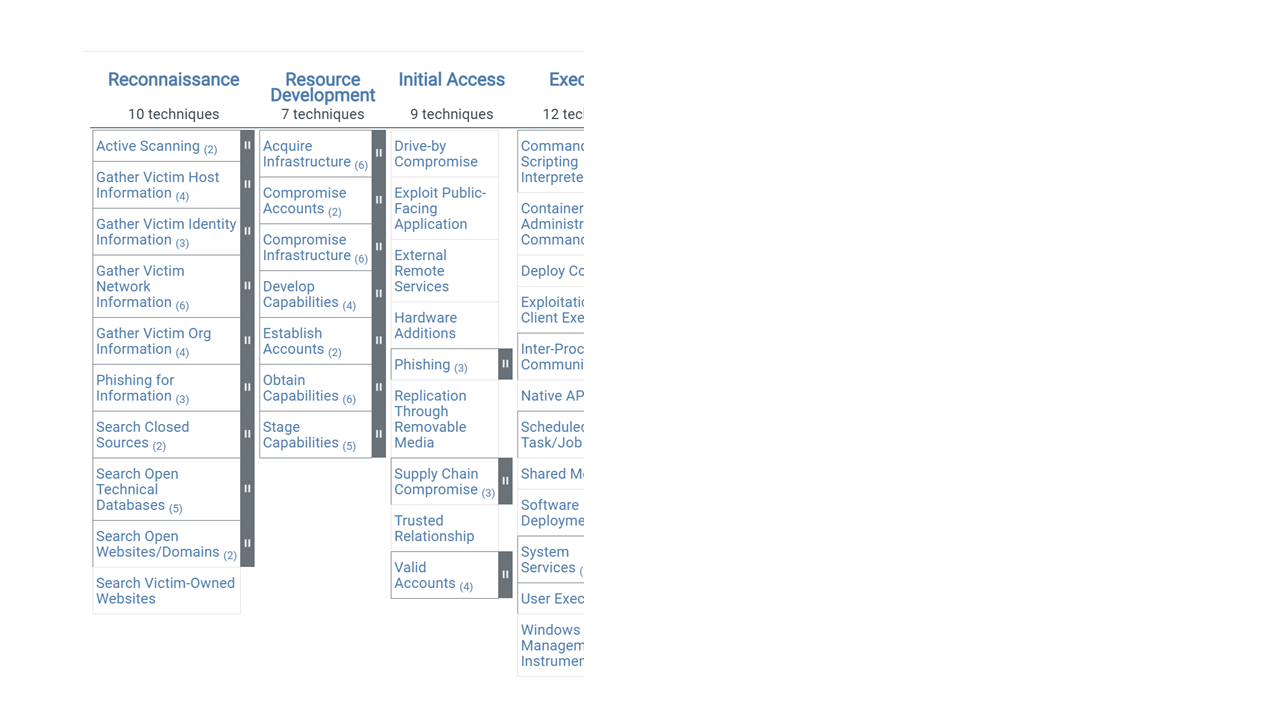
Figure 4. Techniques are listed beneath each tactic; gray bars on the right indicate sub-techniques.
Exploring Tactics Detail Pages
Clicking a tactic name displays its detail page, which includes a general description of the tactic and a list of all techniques and associated sub-techniques. Metadata to the right of the description lists the tactic ID number, date created, and date last modified. Figure 5 provides a partial view of the Initial Access detail page, showing three of the nine techniques. Each entry listed under Techniques has an ID number and a specific name (both clickable).
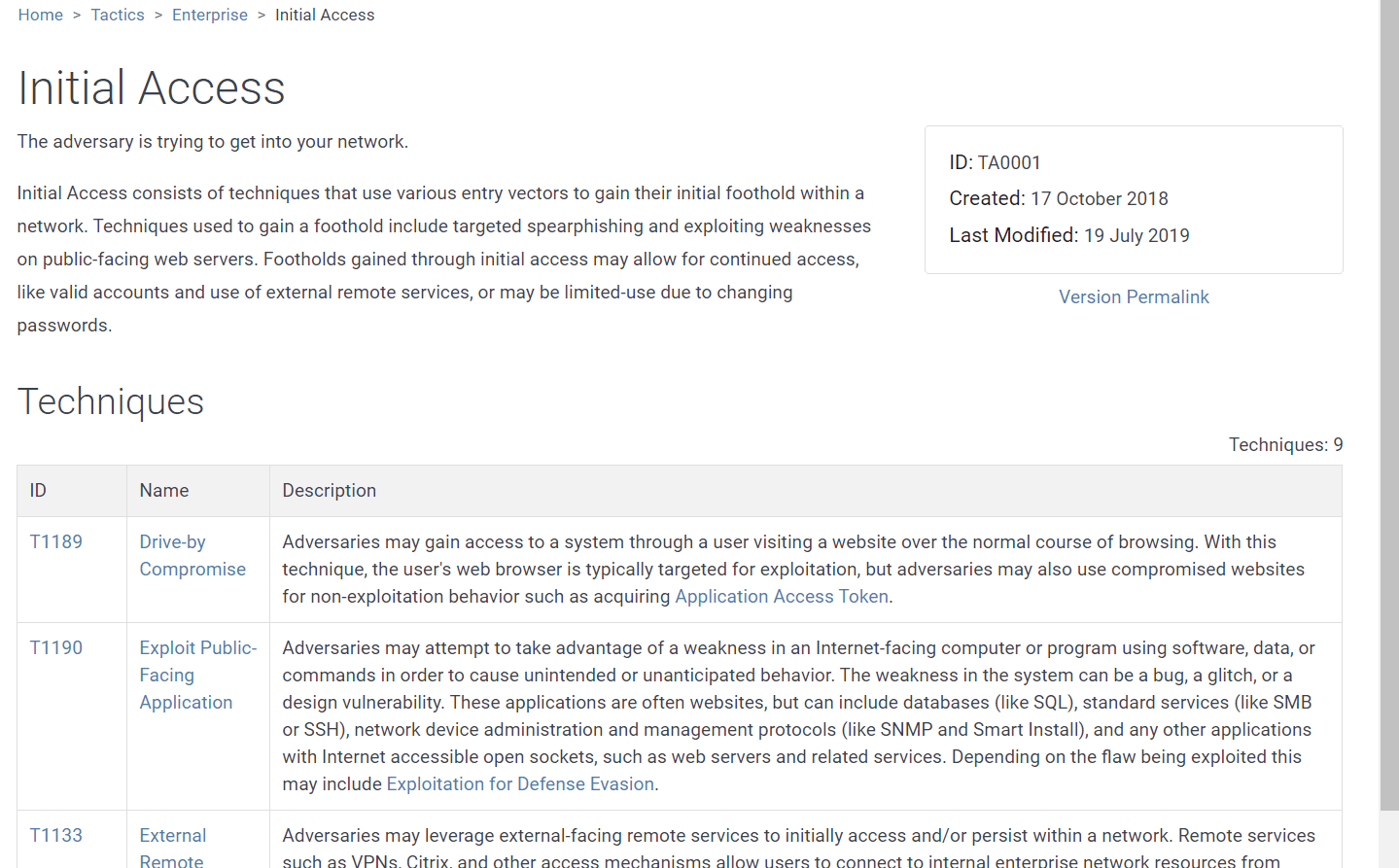
Figure 5. The detail page for the Initial Access tactic includes metadata and applicable techniques.
Exploring Technique Detail Pages
Every technique has a similar detail page. To see details of the Phishing technique (shown in Figure 6), click the Phishing entry under Initial Access on the matrix. The technique details page includes an overall description and significantly more metadata than appears on the tactics detail pages. The metadata includes the three sub-technique numbers, the tactic this technique belongs to, the platforms it applies to, the data sources you might use to detect this type of activity, and more. Beneath the description, the list of Procedure Examples details how specific APTs have used this technique, while additional sections list possible mitigations and suggestions for detecting the use of this technique in your environment.
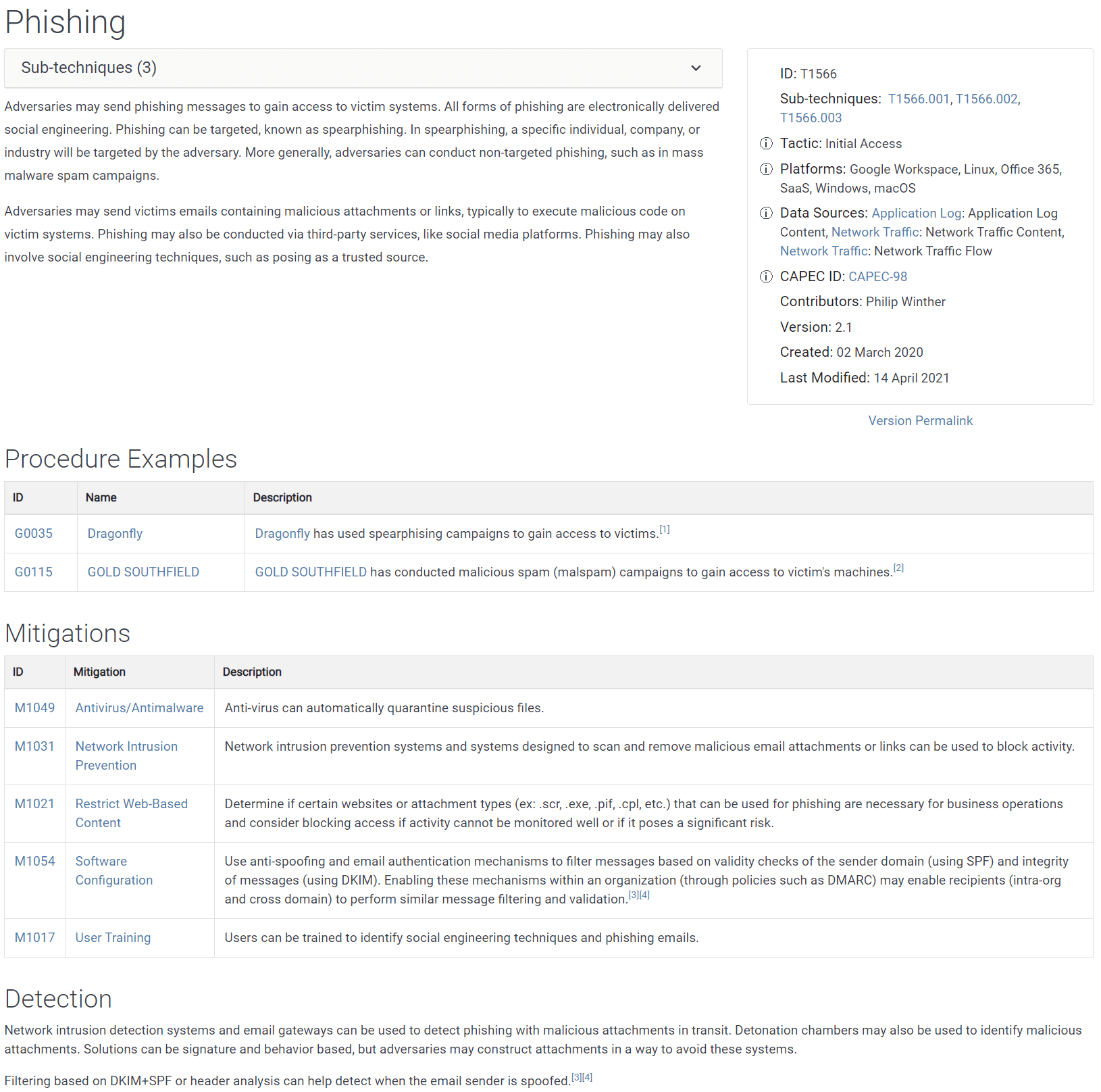
Figure 6. Detail page for the Phishing tactic under Initial Access.
Exploring Sub-Technique Detail Pages
Returning to the full matrix, clicking the gray bar to the right of any technique exposes its sub-techniques. Figure 7 shows the Phishing sub-techniques of Phishing under the Initial Access tactic.
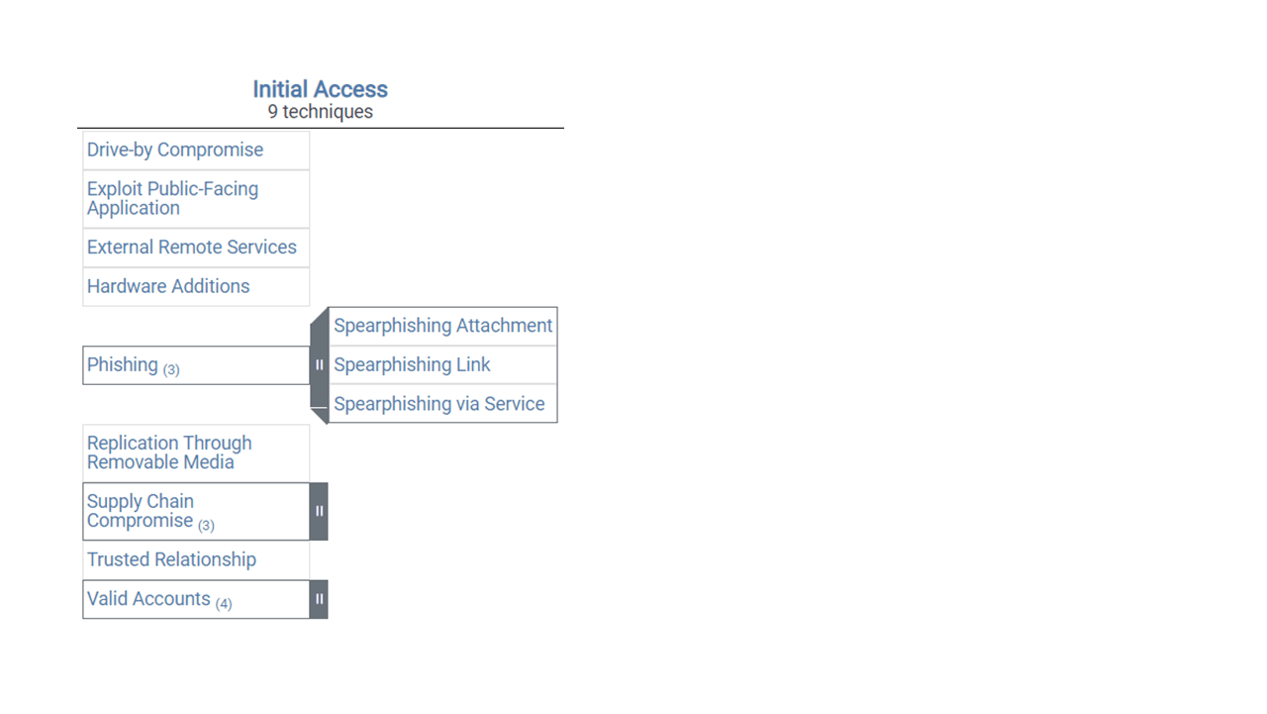
Figure 7. All tactics have multiple techniques; many in the Enterprise matrix have one or more associated sub-techniques.
To display detailed information about a sub-technique, click its name. Figure 8 shows the detail page for Phishing: Spearphishing Link. Comparing this to the detail page for Phishing (see Figure 6), while both include descriptions and similar metadata, far more procedure examples appear here—45, to be exact! Remember, procedures recount the various ways a technique or sub-technique has been implemented in actual attacks. The abundance of examples can provide insight into both routine and sometimes novel ways adversaries use techniques, tools, and malware to accomplish their objectives. The sheer number of documented instances is also an anecdotal indication of how “popular” (successful) this sub-technique is with attackers.
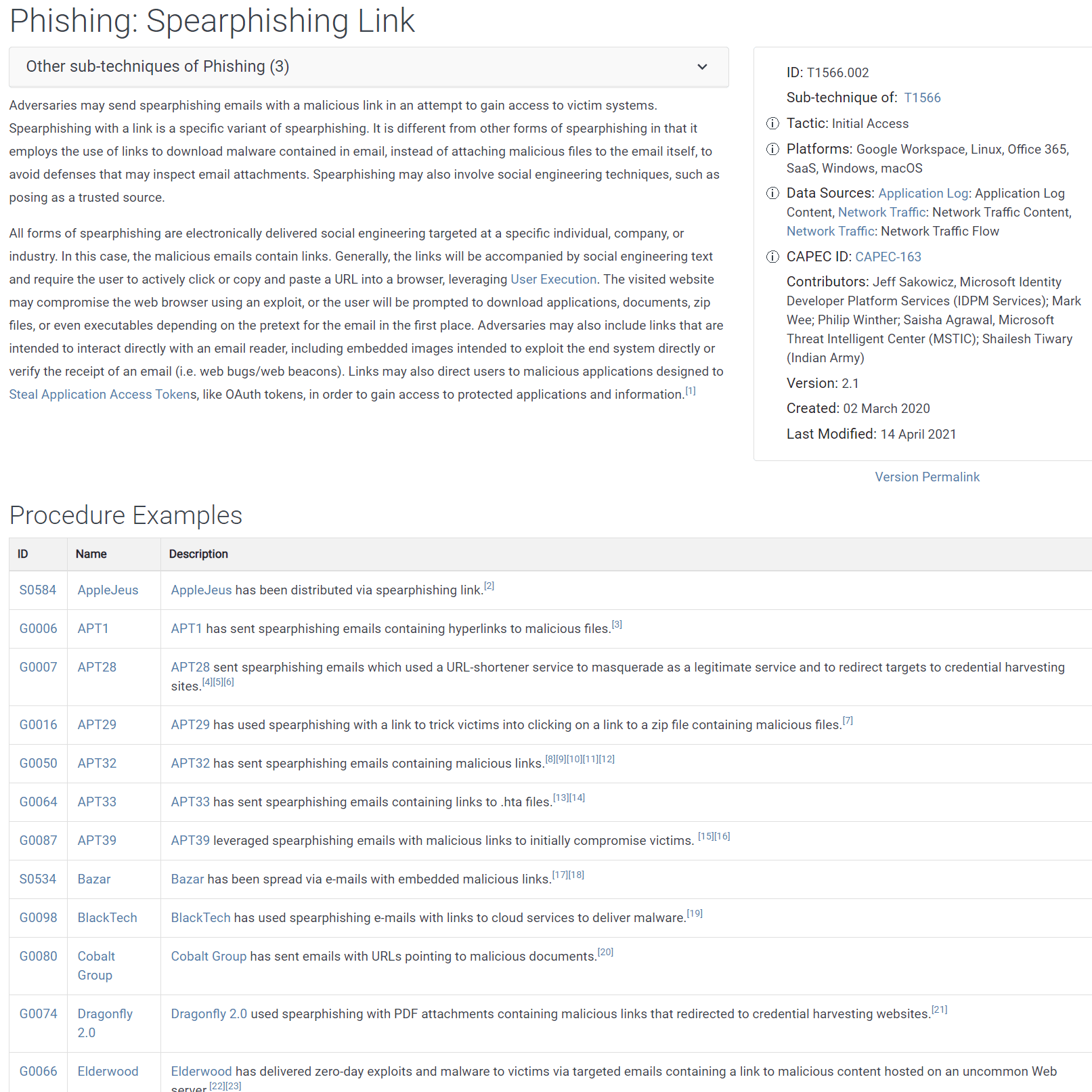
Figure 8. A partial view of the Phishing: Spearphishing Link detail page for the Initial Access tactic shows 12 of the 45 total procedures observed in the wild.
This is a good place to point out that some techniques and sub-techniques can be listed under multiple tactics. For example, Spearphishing Link also appears under the Reconnaissance tactic (see Figure 9) as a sub-technique of Phishing for Information. The description is nearly identical to the one for the Initial Access: Phishing tactic shown in Figure 8. But notice in Figure 9 the metadata lists a different ID number, “Sub-technique of” number, and tactic. The platform listed is PRE, indicating this technique takes place in a pre-attack phase. Notice, too, that the list of procedures here is significantly shorter—five entries versus 45—because these procedures occurred as part of Reconnaissance rather than during an attempt to gain Initial Access.
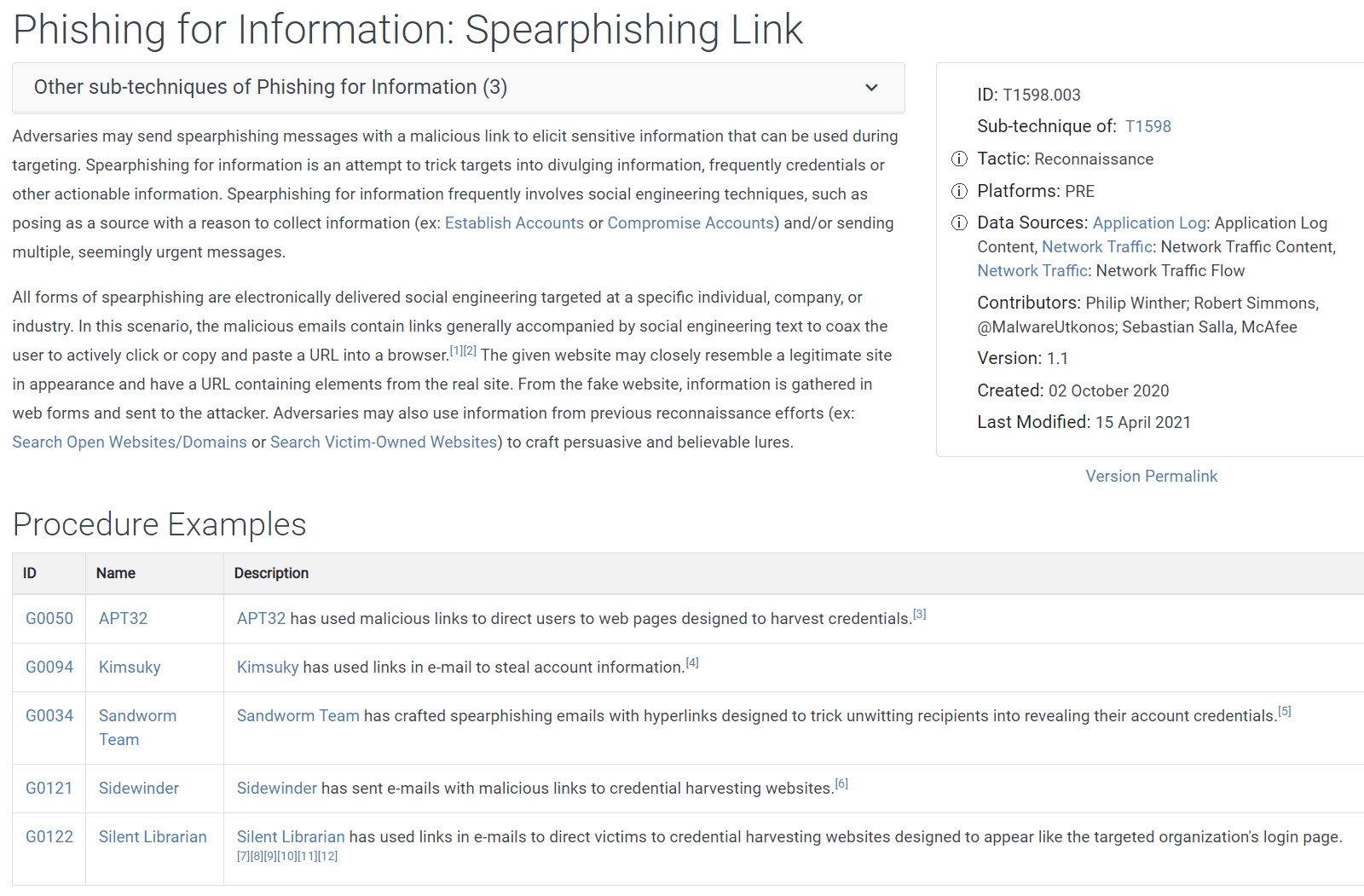
Figure 9. Spearphishing Link is also a sub-technique under the Phishing for Information technique that ladders up to the Reconnaissance tactic.
A final word about detail pages: don’t overlook the footnotes. All data in ATT&CK is meticulously documented so you can review and compare the original sources of information to your organization’s own data, research, insights, history of adversary activity, etc.
Other Ways to Access Information in MITRE ATT&CK
The navigation bar on all MITRE ATT&CK web pages includes tabs for Matrices, Tactics, Techniques, Mitigations, Groups, Software, and Resources (see Figure 10). While some of these may seem redundant with the pages we’ve already seen, they are useful for filtering the amount of data displayed and getting to the data you want quickly.

Figure 10. MITRE ATT&CK's navigation bar provides many ways to access data.
Filtering the Matrices
We mentioned earlier that the Enterprise matrix addresses Windows, macOS, Linux, “and others.” Those others include cloud-based platforms such as Office 365, Azure AD, Google Workspace, SaaS, and IaaS, as well as network and container environments. Clicking Matrices in the navigation bar and selecting Enterprise displays all of these options, allowing you to focus on one area. Figure 11 shows the nine tactics and associated techniques that apply to Office 365 (under Cloud)—a far more manageable view than the entire matrix.
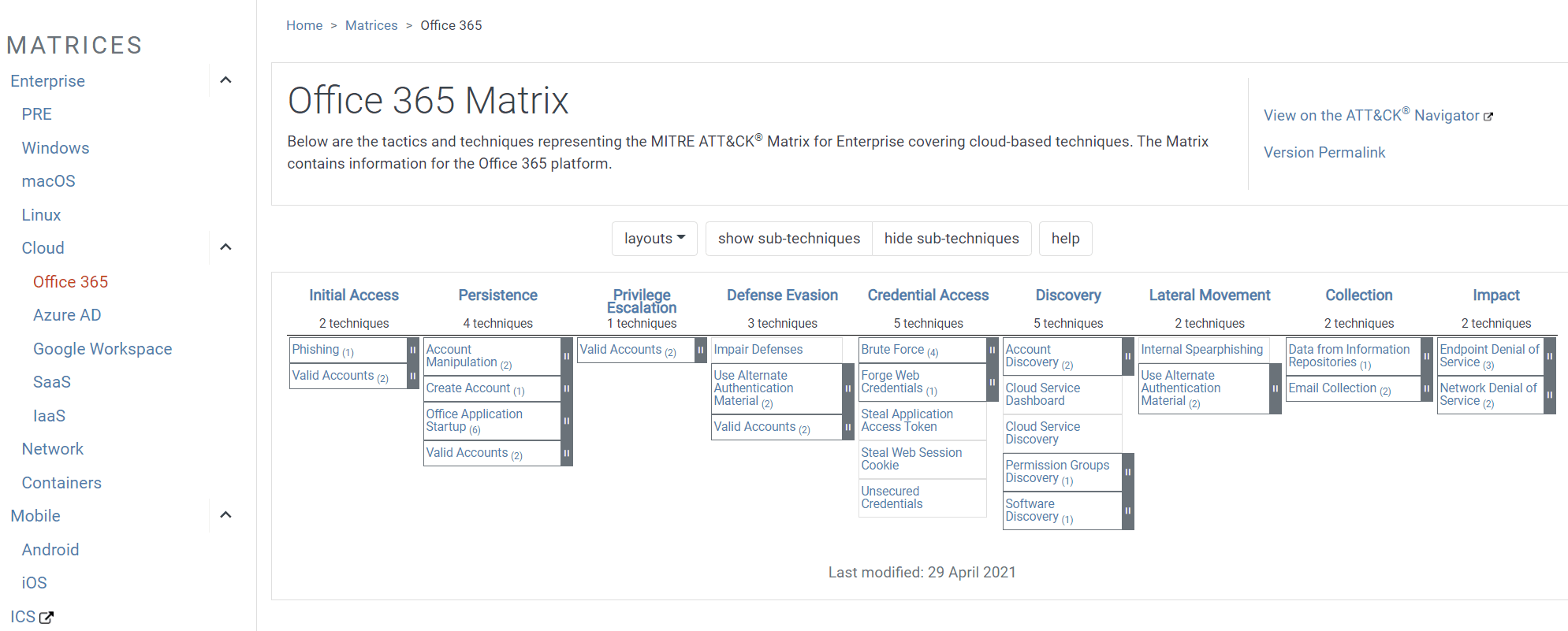
Figure 11. Filtering the Enterprise matrix for Office 365 shows only the tactics and techniques that apply to this cloud-based platform.
Zeroing In on Tactics, Techniques, and Mitigations
The Tactics, Techniques, and Mitigations tabs in the navigation bar all give you the option to display information in a concise, alphabetized list. In each case, the IDs and names for each entry are all clickable, taking you to a detail page similar to the one shown in Figure 6. What’s nice about these summary pages are the brief descriptions you can read quickly to decide if you want more detail. Figure 12 shows a partial example of the Enterprise Mitigations page; the full list includes 42 mitigations.
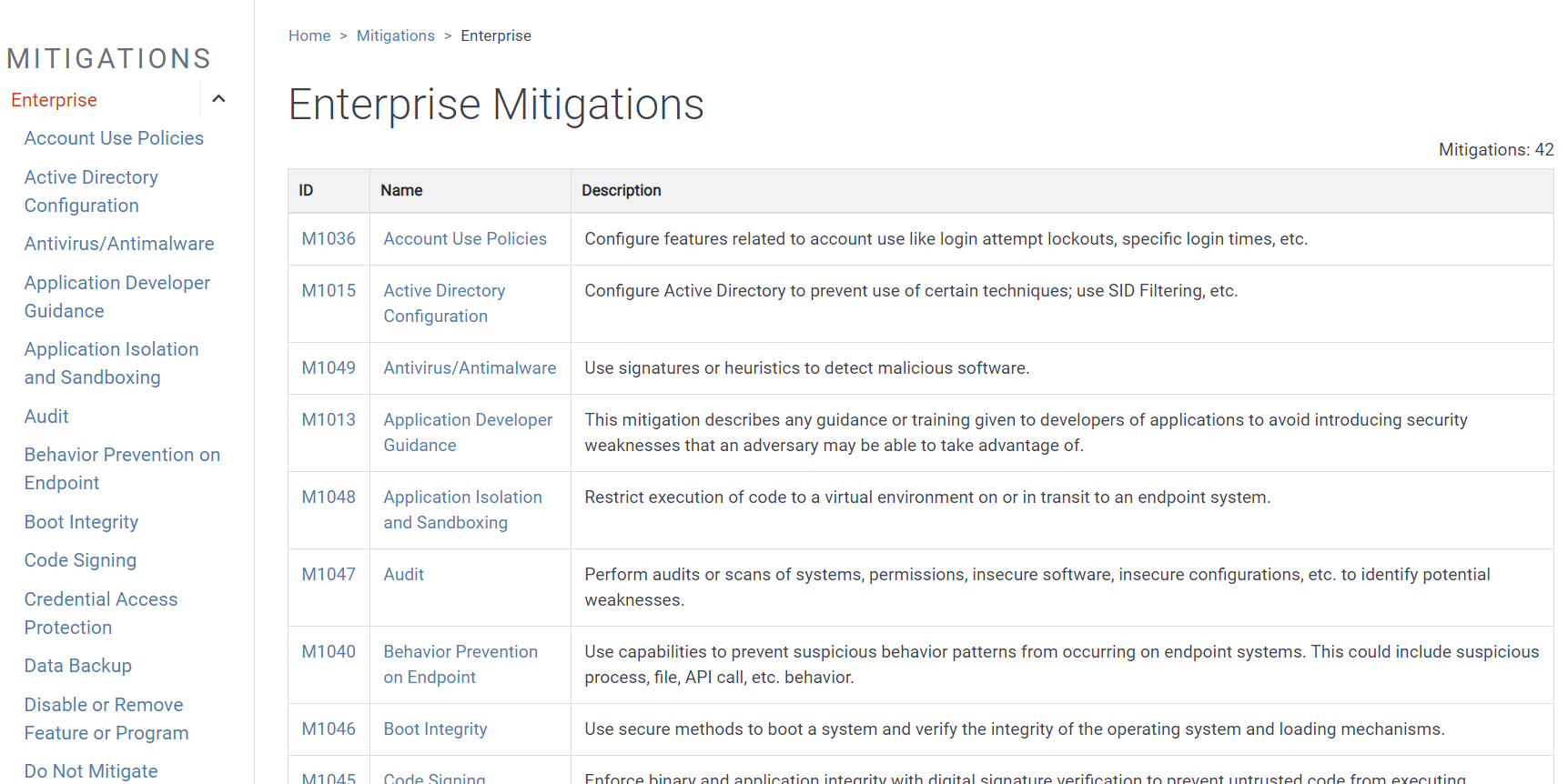
Figure 12. A quick reference list of all Enterprise Mitigations shows the ID number, name, and a brief description for each.
Clicking a Mitigation entry provides a list of techniques and sub-techniques that mitigation addresses (see Figure 13). Again, the technique IDs and names listed on Mitigation pages are clickable, taking you immediately back to a technique’s detail page.
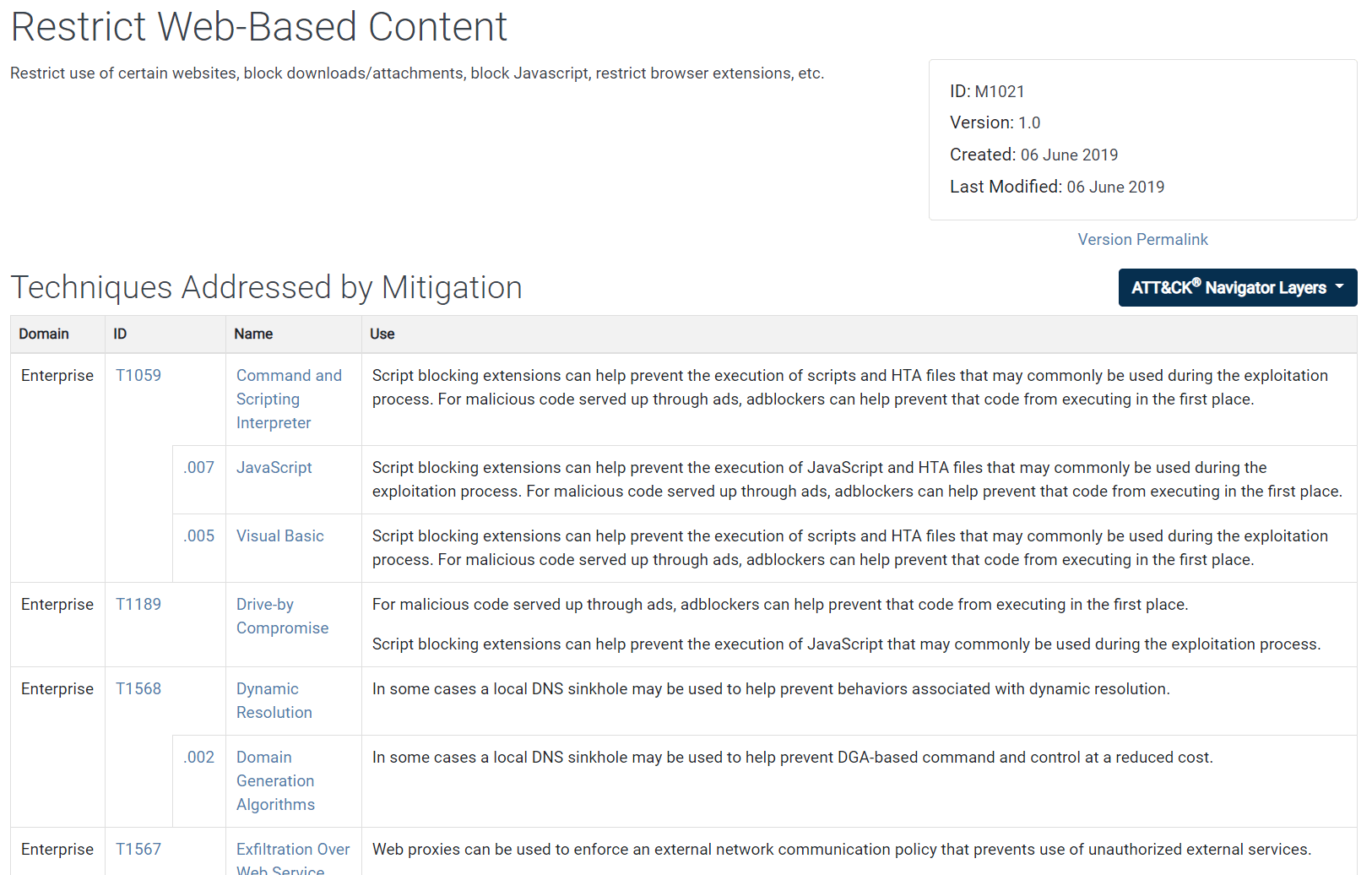
Figure 13. A Mitigation detail page lists all techniques and sub-techniques that mitigation addresses.
ATT&CK’s Easy-to-Miss Invaluable Resources
Many people who are new to MITRE ATT&CK focus so closely on the matrices, they aren’t aware of three additional invaluable resources: MITRE's knowledge base of APT groups, its extensive list of software that adversaries use, and the ATT&CK Navigator tool. Let’s look at Groups first.
Getting to Know APT Groups
ATT&CK provides one of the most useful, centralized references about threat groups you’ll find in the public domain. This resource, available by clicking Groups in the navigation bar, is helpful in understanding both known and suspected groups, along with their histories, habits, and observed malicious behaviors. In most cases, the word group refers to known and suspected APT groups. In other cases, it refers to a set of related intrusive activities or a set of tools used that cannot be attributed to a specific group. A good example of this is Blue Mockingbird, which ATT&CK refers to as both “a cluster of observed activity involving Monero cryptocurrency-mining payloads” and a set of tools.
As shown in Figure 14, each group is assigned an ID number and name, both of which can be clicked to display detail pages. Note that version 9 of ATT&CK provides information on 122 groups (you can scroll through them quickly in the left pane). And because organizations often refer to groups by different names (and attribute certain activities to different groups), the Group detail pages list other associated group names and descriptions.
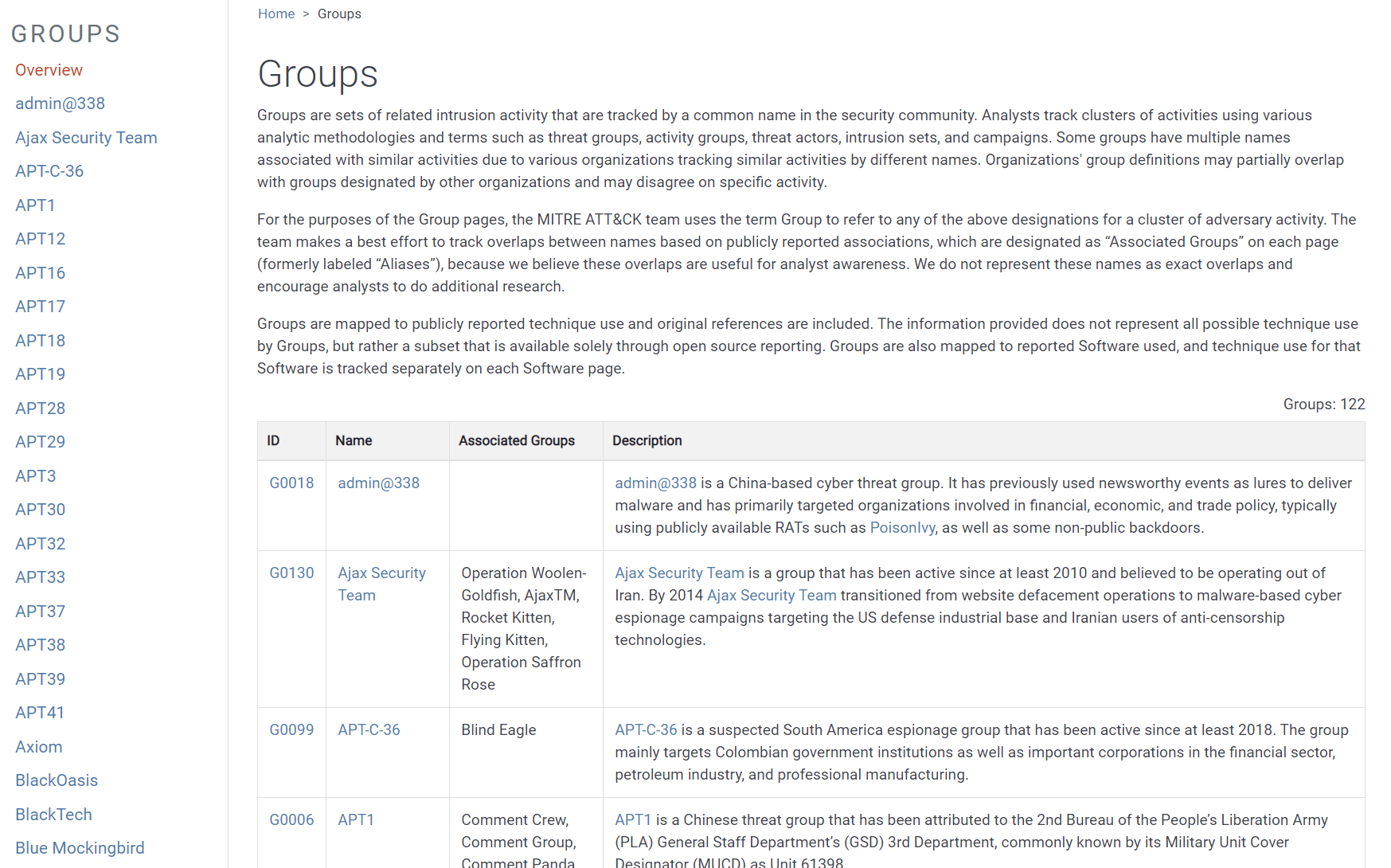
Figure 14. The Groups page lists known threat groups as well as sets of related but non-attributed intrusion activity.
Tracking the Tools Adversaries Use
The Software page in ATT&CK includes an extensive list—585 entries—of software APTs are known to use. In this context, the term software is used broadly and primarily consists of malware. But it also includes commercially available, custom, and open-source code, as well as tools and some operating system utilities (such as ifconfig in UNIX or netsh in Windows) used to aid in attacks (see Figure 15).
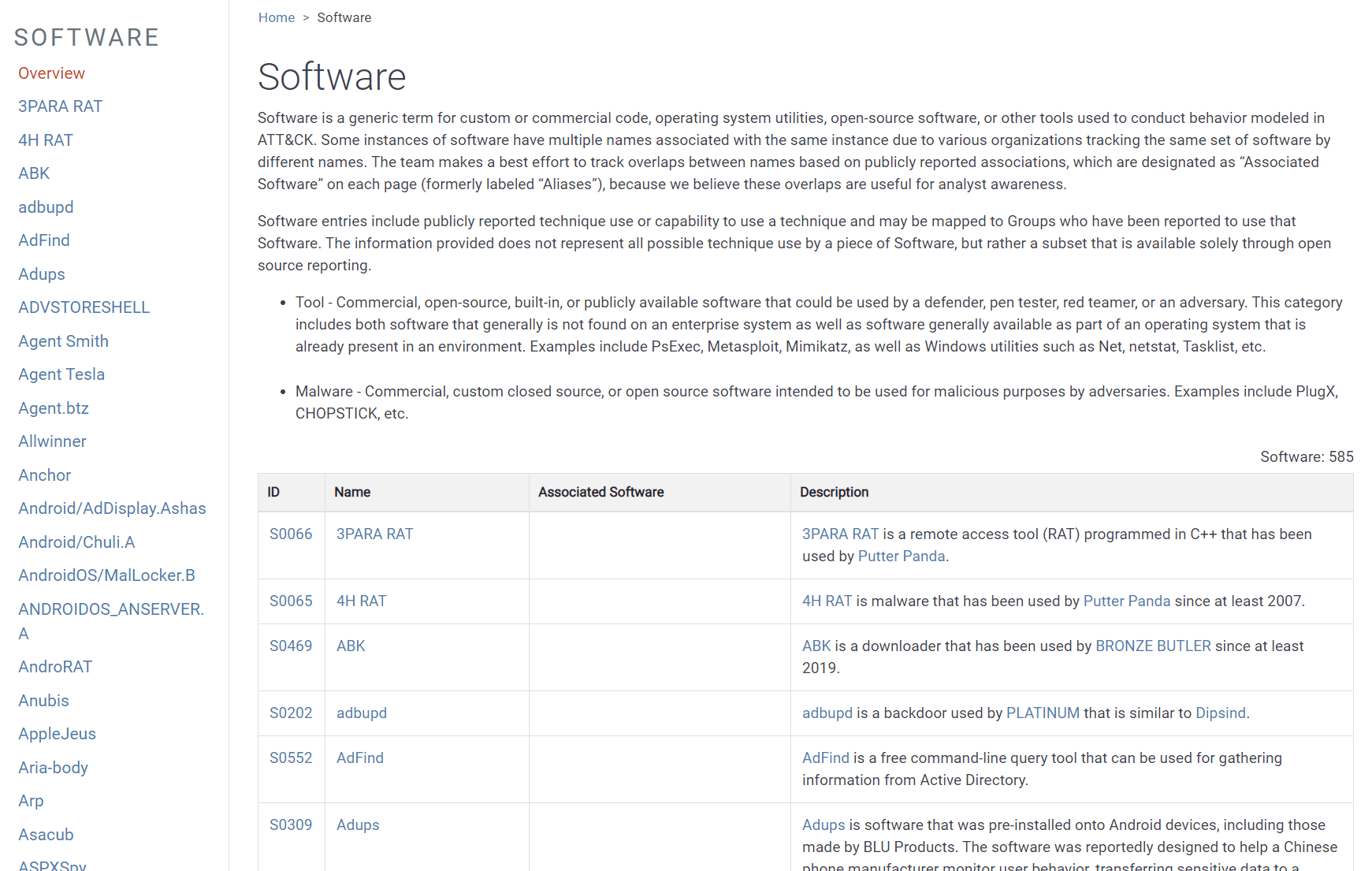
Figure 15. MITRE tracks known software (both malware and legitimate tools and utilities) used in APT attacks.
If the list of 585 entries isn’t impressive enough on its own, click any of the IDs or names to see detailed descriptions of how the software has been used, by whom, and for what purpose. Figure 16 shows a portion of the detail page for the malware loader Emotet. The full list includes a total of 24 techniques, many with additional sub-techniques. Software detail pages also list other names by which software is known under Associated Software Descriptions.
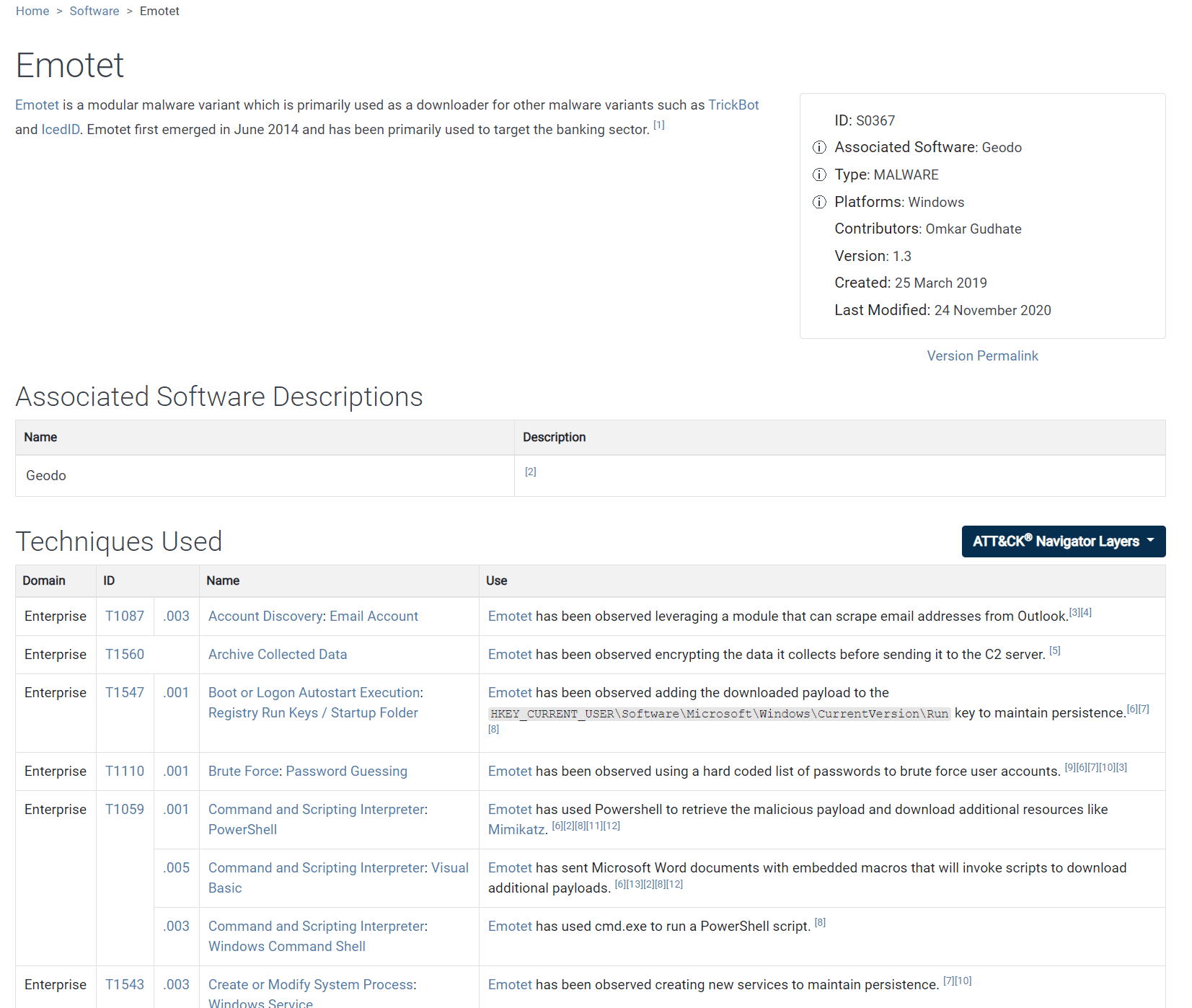
Figure 16. A partial view of the Emotet malware detail page shows five of the 24 techniques in which Emotet has been used.
Using ATT&CK Navigator for Analysis
ATT&CK Navigator is a tool that takes the headache out of using a spreadsheet or other tool to analyze threats, evaluate your defenses, plan attack simulations, compare various elements that ATT&CK tracks, and more. In Figure 17, the techniques used by Dridex and ZeusPanda banking trojans are tracked on individual tabs. The tab that’s selected combines the two for comparison. Dridex techniques are shown in yellow, ZeusPanda techniques are in red, and techniques shared by both are shown in green. This is just one simple example of the many ways ATT&CK Navigator7 can be used for analysis, planning, attack simulations, and more.
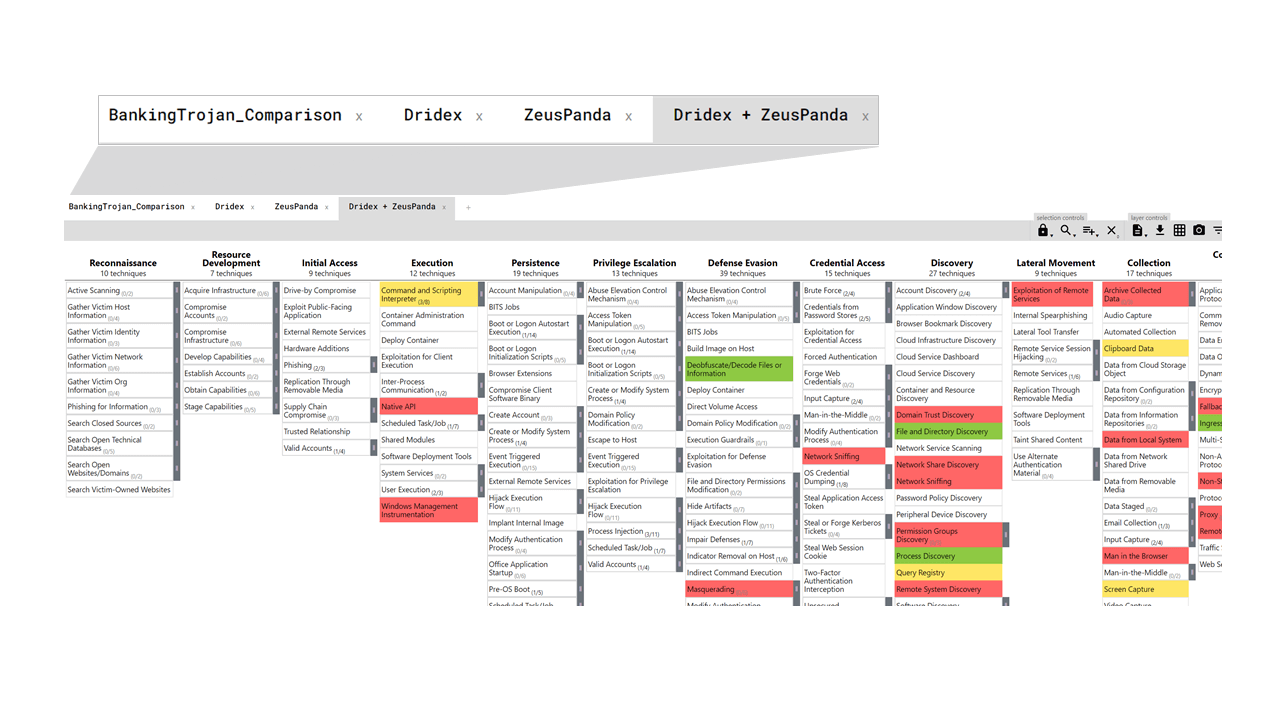
Figure 17. ATT&CK Navigator tool comparing Dridex and ZeusPanda banking trojan techniques.
Conclusion
MITRE ATT&CK is a highly detailed and cross-referenced repository of information about real-world adversary groups and their known behavior; the tactics, techniques, and procedures they use; specific instances of their activities; and the software and tools they employ (both legitimate and malicious) to aid in their attacks. Designed from an attacker’s point of view, MTRE ATT&CK stands apart from other defender-focused and risk-based threat modeling and cyberattack lifecycle models. This makes it a uniquely valuable tool for helping organizations gain insight into attacker behavior so they can improve their own defenses accordingly.
The wealth of information ATT&CK provides is difficult to grasp by description alone. You can best understand the depth of its value by setting aside an hour or two to explore it on your own. You won’t be sorry you did.


