F5 Labs, in conjunction with our partner Baffin Bay Networks, research global attack traffic region to region to gain a deeper understanding of the cyber threat landscape. Aside from attack campaigns targeting the entire Internet (IPv4 address space), the attack landscape varies regionally in terms of sources, targets, and attack types. In addition, targeted ports expose regional differences in IT norms when it comes to the way non-standard ports are used for HTTP and SSH.
In this latest data collection, we looked at malicious traffic over the same 90-day period—August 1, 2019 through October 31, 2019—in the United States (U.S.), Canada, Latin America, Europe, Russia, Asia, Australia, and the Middle East. The attack landscape in Latin America was different from the rest of the regions in that it had the most unique in-region IP addresses sending malicious traffic.
- IP addresses assigned in-region were the number one source of attacks targeting systems in Latin America. IP addresses assigned in Brazil launched the most malicious traffic to the region, more than IP addresses assigned to the Venezuela, in second place. Latin America was also one of two regions targeted by attack traffic assigned to IP addresses in Argentina.
- Three of the top five IP addresses launching attacks against systems in Latin America were assigned to Costa Rica and Venezuela. These IP addresses conducted abusive scans, largely looking for vulnerabilities on multiple ports. These same IP addresses were not seen attacking other regions in the same period.
- Rounding out the top five IP addresses were those assigned to Moldova. These IP addresses were seen launching RFB/VNC port 5900 attacks that hit all regions of the world.
- Two of the top 25 most targeted ports were port 8291, used by Mikrotik routers, and port 7547 used by ISPs to remotely manage their SOHO router infrastructure. While these were the nineteenth and twentieth most popular targeted ports, they still saw significant attack traffic directed towards them. This activity is directly tied to the building of IoT botnets, also known as thingbots.
- The top ports targeted in Latin America followed similar patterns to the rest of the world, with SMB port 445 being the top attacked port. Other ports included VNC port 5900 (being attacked in regions all over the world), SSH port 22, and Telnet port 23.
- In addition to the most commonly attacked ports, Latin America saw a lot of attack traffic directed towards common web application ports, including port 5555, and 3389. Traffic was also directed towards MySQL port 3306 (indicating that databases were targeted), as well as web applications and IOT devices, which were a top target in Latin America.
Top Source Traffic Countries
Before we look at the top “source traffic countries,” it’s important to clarify that we’re talking about the geographical source of IP addresses in this section. The “top source traffic countries” does not mean that the country itself, individuals, or organizations based in that country were responsible for the malicious traffic. The attack traffic could be coming through a proxy server or compromised system or IoT device with IP addresses assigned in a particular country. For expediency, we refer to these as “top source traffic countries.”
IP addresses assigned to Brazil launched the most malicious traffic against systems in Latin America from August 1, 2019, through October 31, 2019. The top 10 source traffic countries during this period were:
Brazil
Venezuela
Italy
U.S.
Netherlands
Republic of Moldova
Costa Rica
China
Russia
South Korea
All of the top 10, with the exception of Venezuela and Costa Rica, were also the top malicious source traffic countries globally.
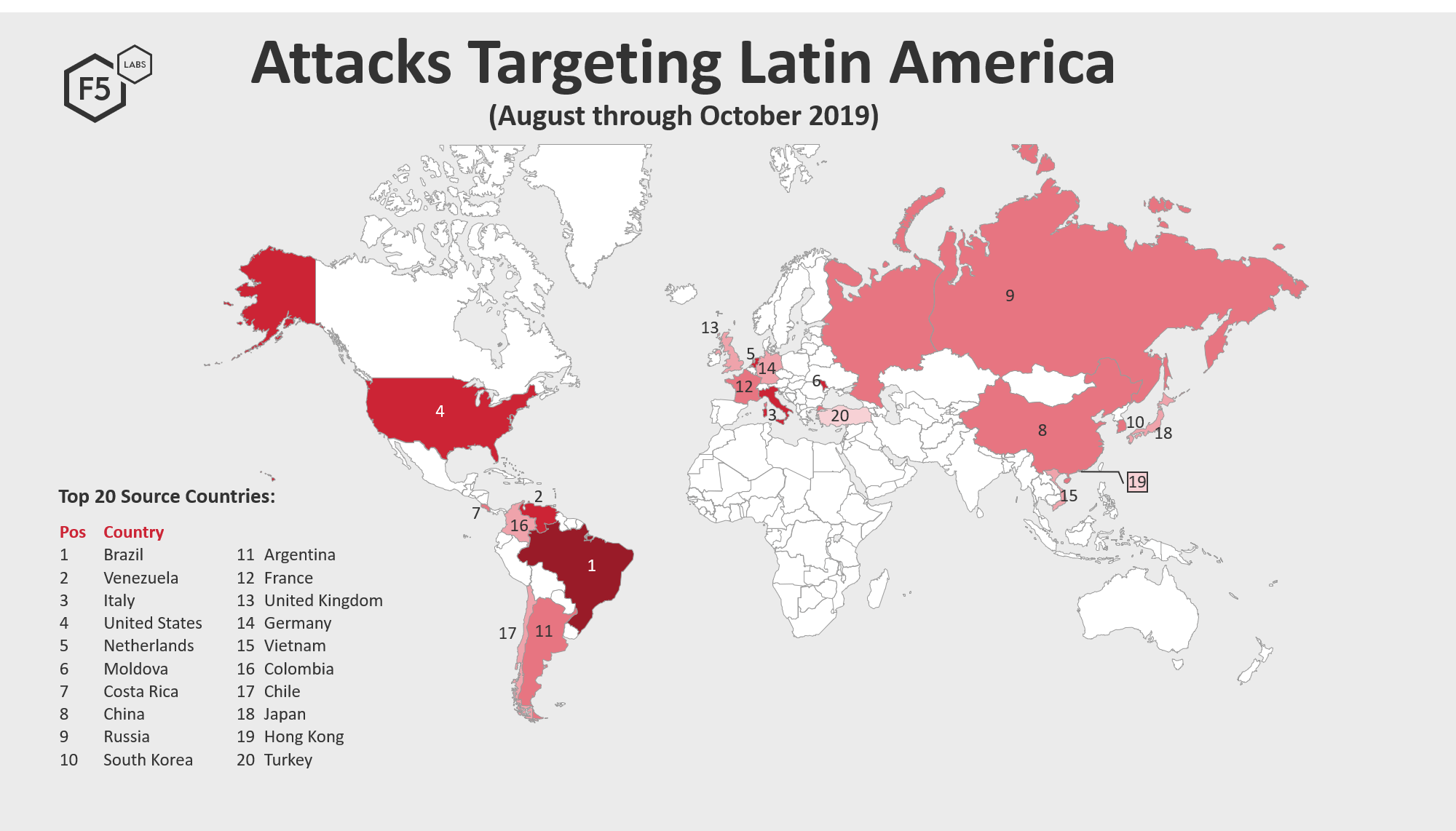
Figure 1. Top 20 source traffic countries launching attack traffic against targets in Latin America, August 1, 2019 through October 31, 2019
Similar to the European threat landscape, the Latin American threat picture experienced a lot of in-region attacks. Thirty percent of the countries in the top attacking source countries list came from Latin America, and combined they accounted for 37% of malicious traffic. The two top source traffic countries were Brazil and Venezuela, both in-region countries. While malicious traffic from Brazil was seen all over the world, malicious traffic coming from IP addresses in Venezuela exclusively targeted systems in Latin America. This kind of traffic can be more difficult for enterprises to filter since typically businesses want to remain accessible to customers in their region.
Latin America also received a considerable amount of traffic from IP addresses assigned in Argentina (position 11). Latin America was one of two regions to receive malicious traffic from Argentina, the other being Russia. Other than one IP address assigned in Argentina that together launched a normalized 120,000 attacks, accounting for about one sixth of total traffic attributed to IP addresses assigned in Argentina, no other IP addresses in Argentina show up in the top attacking IP address list, discussed later. This indicates that attacks coming from IP addresses in Argentina were more distributed; that is, they were launched from many IP addresses but had a low number of attacks per address. This type of activity is deliberate and takes more resources (systems and manpower) to pull off, and therefore is typically attributed to more sophisticated threat actors.
Note: The “normalized” attack count is not the total attack count collected, it is a calculated number considering the number of attack collection sensors region to region. We use normalized attack data in these reports in order to accurately compare attack data between regions and ensure that no single region is overrepresented in the total data analysis.
Latin American was the only region to receive malicious traffic attributed to source IP addresses assigned in Venezuela, Costa Rice, Colombia, and Chile. Traffic from IP addresses in these countries account for 19% of malicious traffic seen during the August through October timeframe. It is notable that these are in-region countries, which may indicate threat actors were attempting to disguise their traffic to blend in with other benign in-region traffic.
The threat landscape in Latin America was a bit of an outlier when it comes to some of the more popular top source traffic countries. IP addresses assigned in Russia launched the least amount of traffic against systems in Latin America. In addition, many of the top source traffic countries in other regions of the world appeared lower in the rankings for Latin America. IP addresses assigned in Russia, which was in first or second position for four regions, was in position 9 in Latin America. Along with Russia, France, which was similarly in first position for 3 regions, was noticeably further down the list (at position 12) for Latin America.
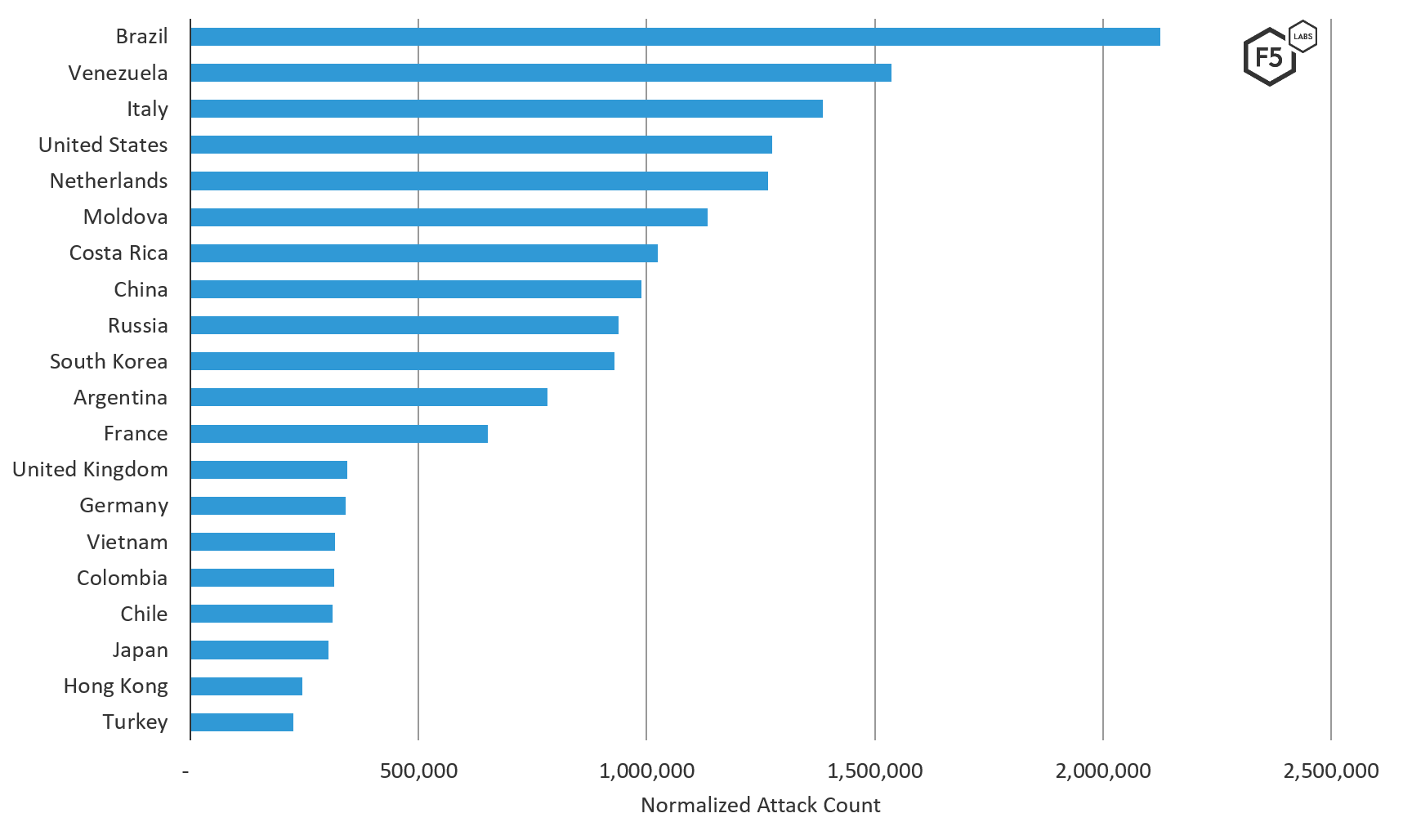
Figure 2. Top 20 source traffic countries (on a normalized scale) of attacks targeting systems in Latin America, August through October 2019.
Top Attacking Organizations (ASNs)
DigitalOcean, the AS Organization that hosts IP addresses in both the U.S. and the Netherlands, launched the most attack traffic towards systems in Latin America. It was quickly followed by RM Engineering from Moldova. Both of these ASNs had multiple IP addresses in the top attacking IP list that participated in the VNC port 5900 activity seen around the world. The ASN in third position, Radiografica Costarricense from Costa Rica, has IP addresses exclusively targeting Latin America, and heads the top attacking IP addresses list. Looking at the Latin American threat landscape, 16 ASNs (out of 50) exclusively targeted Latin America.
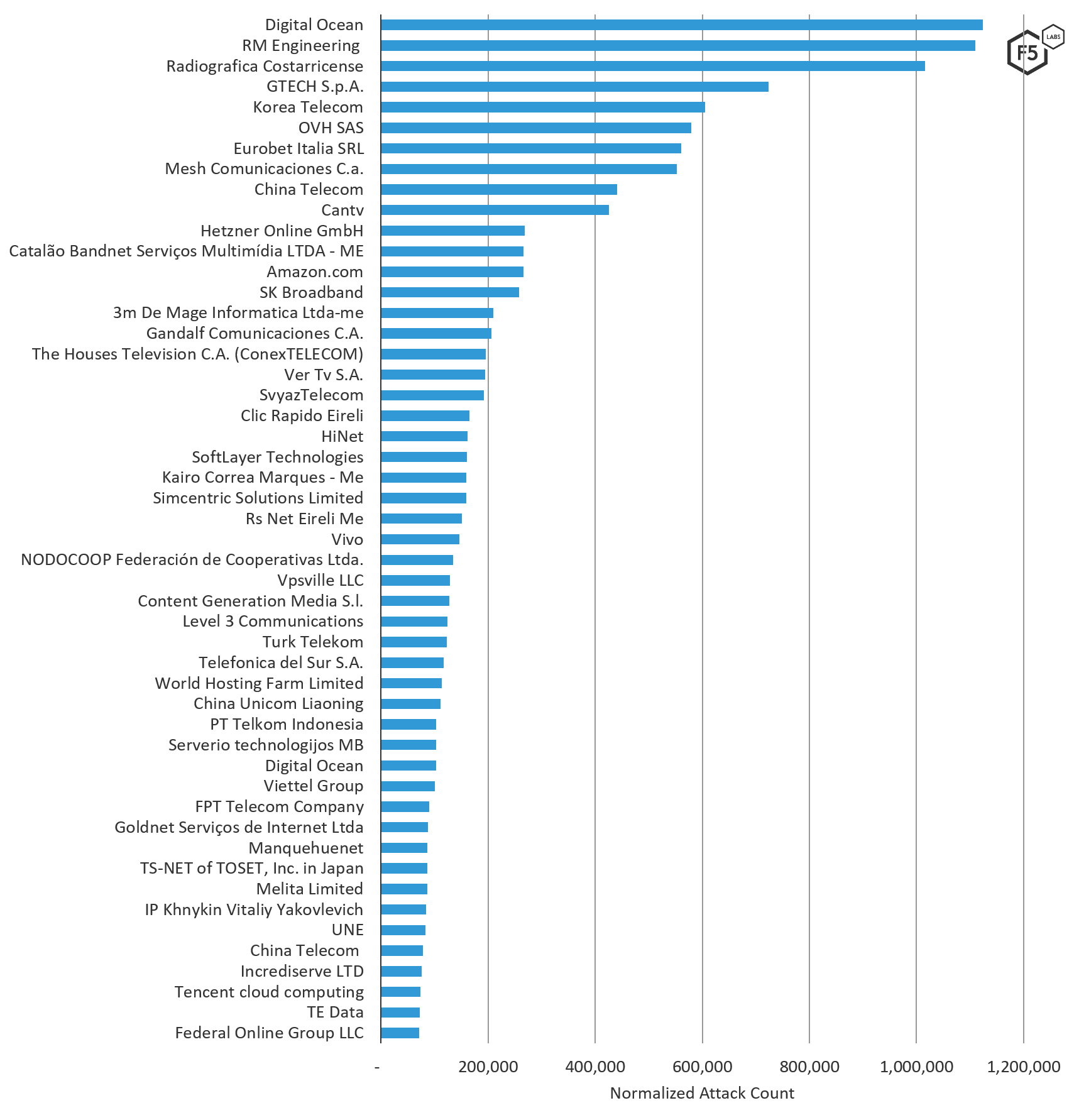
Figure 3. Source ASNs of attacks targeting systems in Latin America, August through October 2019
The following table lists ASNs and their associated organizations (note that some have multiple ASNs).
| AS Organization | ASN | Normalized Count |
| Digital Ocean, LLC | 14061 | 1,241,245.30 |
| RM Engineering LLC | 49877 | 1,110,079.20 |
| Radiografica Costarricense | 3790 | 1,023,199.10 |
| GTech S.p.A. | 35574 | 723,252.30 |
| OVH SAS | 16276 | 631,604.00 |
| Korea Telecom | 4766 | 605,698.40 |
| Eurobet Italia SRL | 200944 | 560,472.40 |
| Mesh Comunicaciones C.A. | 264660 | 552,637.60 |
| China Telecom | 4134 | 486,830.10 |
| CANTV Servicios, Venezuela | 8048 | 427,754.10 |
| Hostkey B.v. | 57043 | 334,163.00 |
| Amazon.com, Inc. | 16509 | 170,178.70 |
| Hetzner Online GmbH | 24940 | 268,935.90 |
| Catalão Bandnet Serviços Multimídia LTDA - ME | 264353 | 266,063.10 |
| SK Broadband Co Ltd | 9318 | 257,503.70 |
| Level 3 Parent, LLC | 3549 | 169,025.30 |
| Serverius Holding B.V. | 50673 | 231,860.50 |
| 3M De Mage Informatica LTDA-ME | 263852 | 209,568.80 |
| The Houses Television C.A. (ConexTELECOM) | 264628 | 195,805.40 |
| Ver Tv S.A. | 27984 | 194,638.90 |
| SoftLayer Technologies Inc. | 36351 | 179,077.30 |
| Clic Rapido Eireli | 263864 | 169,241.50 |
| NETSEC | 45753 | 162,837.40 |
| Data Communication Business Group | 3462 | 161,186.40 |
| Kairo Correa Marques - ME | 263860 | 159,003.00 |
| Sprint S.A. | 197226 | 156,964.60 |
| RS NET EIRELI ME | 263858 | 151,357.20 |
| NODOCOOP Federación de Cooperativas Ltda. | 27987 | 134,461.80 |
| China Unicom | 4837 | 132,818.00 |
| Telefonica Brasil S.A | 18881 | 77,055.50 |
| IP CHistyakov Mihail Viktorovich | 35582 | 127,644.10 |
| Turk Telekom | 47331 | 99,464.30 |
| PT Telekomunikasi Indonesia | 7713 | 109,629.30 |
| Telefonica del Sur S.A. | 14117 | 116,577.60 |
| Viettel Group | 7552 | 94,050.50 |
| The Corporation for Financing & Promoting Tech... | 18403 | 93,301.40 |
| TS-NET of TOSET, Inc. in Japan | 55902 | 89,984.90 |
| Goldnet Serviços de Internet Ltda | 52614 | 87,428.20 |
| Gtd Internet S.A. | 14259 | 86,992.30 |
| Melita Limited | 200805 | 86,665.80 |
| SS-Net | 204428 | 84,474.90 |
| EPM Telecomunicaciones S.A. E.S.P. | 13489 | 82,602.30 |
| Shenzhen Tencent Computer Systems Company Limited | 45090 | 79,418.60 |
| TE-AS | 8452 | 75,381.00 |
| IP Volume Inc. | 202425 | 74,512.10 |
| CNSERVERS LLC | 40065 | 72,532.10 |
| VNPT Corp | 45899 | 71,997.70 |
| Continent 8 LLC | 14537 | 71,515.70 |
| Servers.com, Inc. | 7979 | 67,906.30 |
| NSS S.A. | 16814 | 64,879.50 |
Table 1. ASNs and their associated organizations (some have multiple ASNs)
ASNs Attacking Latin America Compared to Other Regions
We looked at the count of attacks by ASN towards systems in Latin America and compared that to other regions of the world. The key difference between attack traffic launched from networks targeting Latin America versus the rest of the world was the volume of attack traffic launched from the 16 ASNs exclusively targeting systems in Latin America (see ASNs denoted with *** in Figure 4). These include ASNs located in region in both Venezuela (Mesh Communicaiones) and Costa Rica (Radiografica Costarricense). In contrast, top attacking networks in other regions like OVH SAS (France) and RM Engineering (Moldova), sent much less traffic towards systems in Latin America.
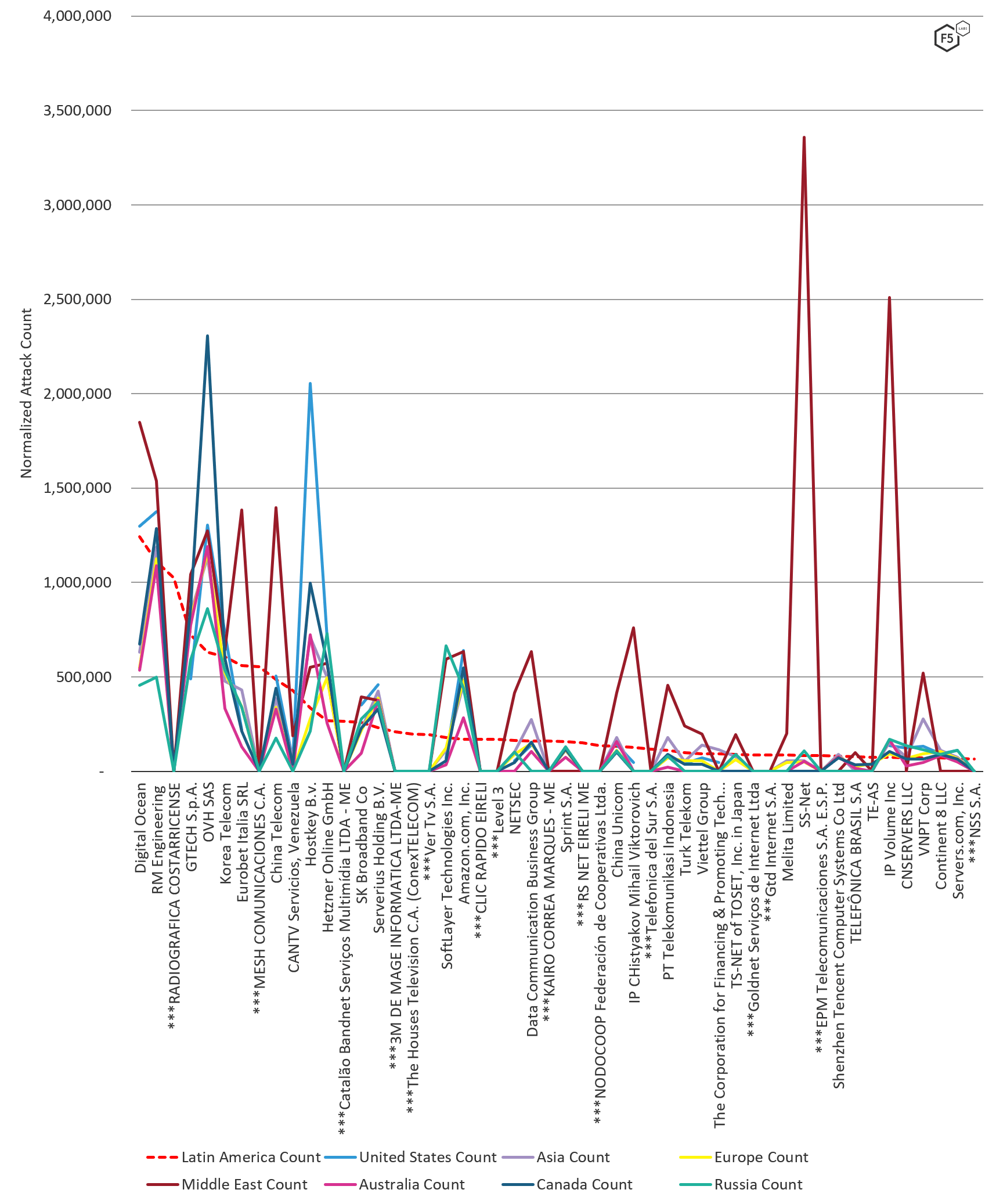
Figure 4: Normalized attack count by ASN by region, August through October 2019
Top Attacking IP Addresses
The Top five attacking IP addresses targeting systems in Latin America from August 1, 2019 through October 31, 2019 were either assigned to Latin American IP addresses or were assigned in Moldova, and were either engaged in credential stuffing or multi-port scanning, activities that are typically attributed to looking for vulnerabilities. Sixty-nine percent of the IP addresses on the top 50 attacking IP addresses list were engaging in the same multi-port scanning behavior, many of these IP addresses also specifically targeted VNC port 5900 and engaged in credential stuffing activity.1 For a complete list of attacks by IP address, see section Attacks Types of Top Attacking IP Addresses below.
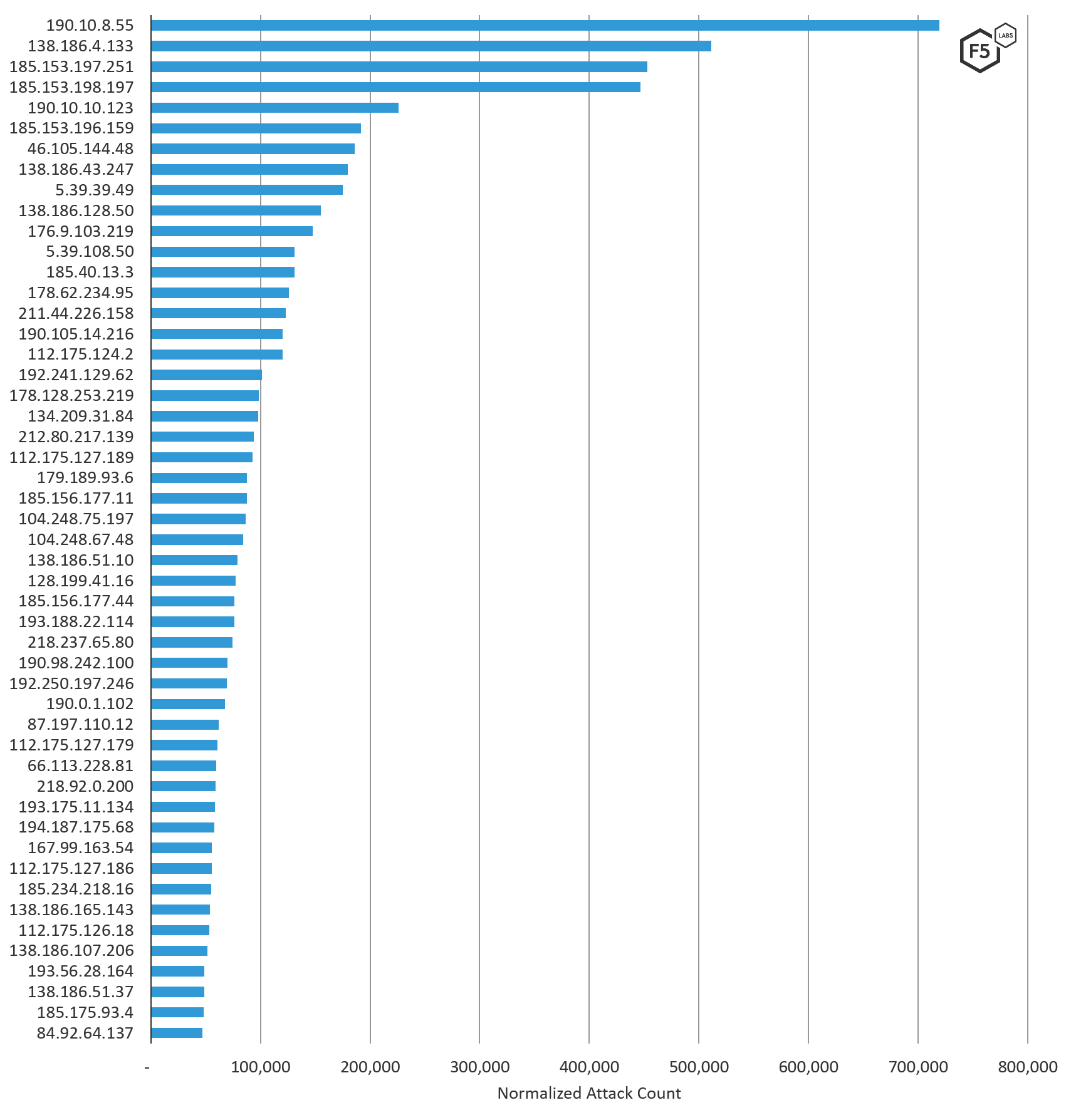
Figure 5. Top 50 IP addresses attacking Latin American targets, August through October 2019.
IP Addresses Attacking Latin America Compared to Other Regions
We compared the volume of attack traffic systems in Latin America received per IP address to other regions of the world. Attack traffic destined for these systems had some overlap with the rest of the world. There were a handful of IP addresses launching global attacks against RFB/VNC port 5900 (see the next section), which accounted for 16% of the top attacking IP addresses. 54% of the top attacking IP addresses sending malicious traffic to Latin America were exclusively targeting the Latin American region (see IP addresses denoted with *** in Figure 6). Latin America, Russia, and the Middle East saw the most unique IP addresses attacking their systems. In Latin America the top attacking IP addresses were very geographically spread out, with 8 IP addresses being the only one from their country. As mentioned in the top source traffic countries section, this indicates that there were many IP addresses used in lower volume, which takes additional time and resources.
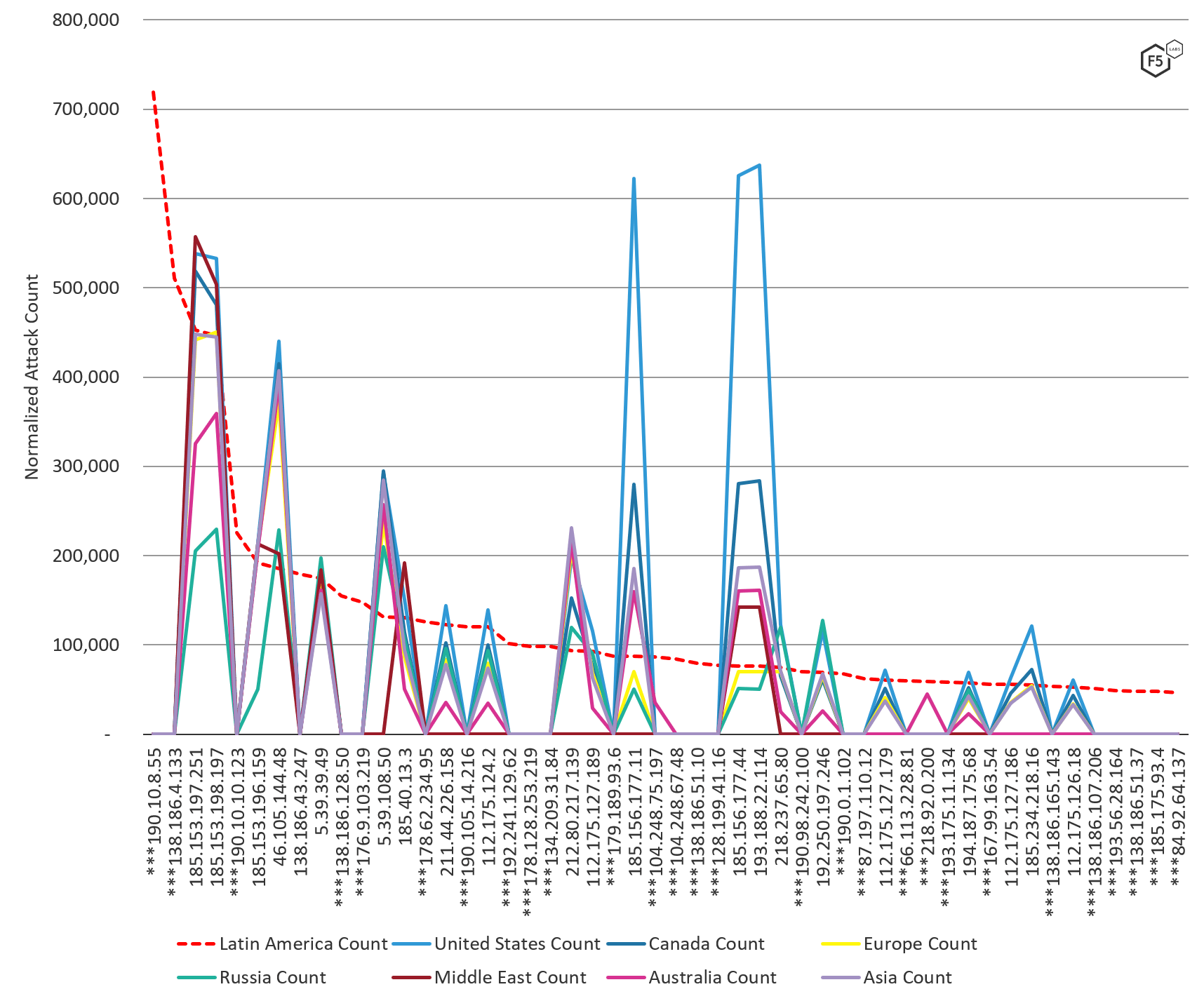
Figure 6: Normalized attack count by IP by region, August through October 2019
Attacks Types of Top Attacking IP Addresses
Unlike some of the other regions in the world, of the top 50 IP addresses attacking systems in Latin America, there was not one source country that stood out. Both Brazil and South Korea had seven IP addresses in the top 50, and beyond that geographically there was no clear pattern. Eight countries had a single IP in the top 50 IP attacking IP addresses list. Out of the top attacking IP addresses, most were conducting multi-port scanning (69%), and targeting Remote Frame Buffer (RFB)/VNC port 5900 with brute force and credential stuffing attacks (24%). The remaining 7% of IP addresses were targeting port 80 and 8080 with HTTP attacks. Many of these IP addresses were engaged in multiple types of malicious behavior, often combining multi-port scanning and credential stuffing attacks.
The IP addresses in Moldova assigned to RM Engineering, as well as OVH SAS in France, were launching brute force and credential stuffing attacks against Remote Frame Buffer (RFB)/VNC port 5900, globally. All regions of the world are being hit with these same attacks from these IP addresses:
- 185.153.197.251
- 185.153.198.197
- 46.105.144.48
- 193.188.22.114
- 185.156.177.44
- 185.153.196.159
- 5.39.39.49
- 185.40.13.3
These port 5900 attacks were new activity we noticed earlier in the summer and continued through October 31, 2019. We have opened up a public threat hunting investigation on Twitter to uncover what is going on with these attacks and will be looking to share our findings and ask questions soon. Join the conversation on Twitter.
Fifty-four percent of the IP addresses seen sending malicious traffic to Latin America exclusively targeted this region. The following table is in descending order starting with top attacking IP addresses and includes the attack types each IP address launched, as well as what we know from Shodan about the attacking host.
| Source IP | ASN Organization | Country | Normalized Attack Count | Attack Type | Tor? | Attacking Host Info (Shodan) |
| 190.10.8.55 | Radiografica Costarricense | Costa Rica | 719,170.3 | Port scanning (ports 445) | No Tor | Ubuntu box with OpenSSH, Port 22 open |
| 138.186.4.133 | Mesh Comunicaciones C.A. | Venezuela | 511,107.1 | Port scanning (ports 445, 139, 1433) | No Tor | Port 53 DNS opened |
| 185.153.197.251 | RM Engineering LLC | Moldova | 452,706.7 | Credential stuffing, multi-port scanning | No Tor | Windows Server, Ports 445 (MS SMB), 5985 (WinRM), 137 (Netbios) open |
| 185.153.198.197 | RM Engineering LLC | Moldova | 446,503.3 | Credential stuffing, multi-port scanning | No Tor | Ports 3389 (MS RDP), 5985 (WinRM), 445 (SMB) open |
| 190.10.10.123 | Radiografica Costarricense | Costa Rica | 225,981.7 | Port scanning (ports 445) | No Tor | FileZilla FTP server, Ports 5901 21 open |
| 185.153.196.159 | RM Engineering LLC | Moldova | 191,854.8 | Credential stuffing, multi-port scanning | No Tor | Windows Server, Ports 445 (MS SMB), 137 (Netbios), 5985 (WinRM), 3389 (MS RDP) open |
| 46.105.144.48 | OVH SAS | France | 185,998.2 | Credential stuffing, multi-port scanning | No Info | No Info |
| 138.186.43.247 | 3M De Mage Informatica LTDA-ME | Brazil | 179,500.6 | Port scanning (ports 1433, 445) | No Tor | MikroTik bandwidth-test server |
| 5.39.39.49 | OVH SAS | France | 175,009.3 | Credential stuffing, multi-port scanning | No Tor | Apache, Debian, OpenSSH Ports 80, 123, 22 open |
| 138.186.128.50 | Kairo Correa Marques - ME | Brazil | 155,186.6 | Port scanning (ports 445, 1433) | No Tor | MikroTik bandwidth-test server |
| 176.9.103.219 | Hetzner Online GmbH | Germany | 147,697.1 | Port scanning (ports 3389) | No Tor | Ports 5985 & 18016 open |
| 5.39.108.50 | OVH SAS | France | 131,255.8 | Credential stuffing, multi-port scanning | No Tor | OpenSSH, Port 22 open |
| 185.40.13.3 | GTECH S.p.A. | Italy | 130,853.3 | Port scanning (51 unique ports) | No Tor | Ports 443 & 80 open |
| 178.62.234.95 | Digital Ocean, LLC | Netherlands | 126,126.6 | Port scanning (ports 5900) | No Tor | Debian system with OpenSSH, Ports 123 (NTP) & 22 (SSH) open |
| 211.44.226.158 | SK Broadband Co Ltd | South Korea | 122,820.6 | Port scanning (48 unique ports) | No Tor | MS IIS, Port 80 (HTTP) open |
| 190.105.14.216 | Ver Tv S.A. | Argentina | 120,282.5 | Port scanning (ports 445, 1433) | No Info | No Info |
| 112.175.124.2 | Korea Telecom | South Korea | 120,238.2 | Port scanning (61 unique ports) | No Info | No Info |
| 192.241.129.62 | Digital Ocean, LLC | U.S. | 101,538.8 | Port scanning (ports 5900) | No Tor | Ubuntu box with OpenSSH, Port 22 open |
| 178.128.253.219 | Digital Ocean, LLC | Netherlands | 98,686.8 | Port scanning (ports 5900) | No Tor | Debian system with OpenSSH, Ports 123 (NTP) & 22 (SSH) open |
| 134.209.31.84 | Digital Ocean, LLC | United Kingdom | 98,114.6 | Port scanning (ports 5900) | No Tor | OpenSSH, Port 22 open |
| 212.80.217.139 | Serverius Holding B.V. | Netherlands | 93,982.0 | Credential stuffing, multi-port scanning | No Tor | Ports 3389 (MS RDP), 5985 (WinRM), 445 (SMB) open |
| 112.175.127.189 | Korea Telecom | South Korea | 92,589.3 | Port scanning (48 unique ports) | No Info | No Info |
| 179.189.93.6 | Goldnet Serviços de Internet Ltda | Brazil | 87,427.9 | HTTP attacks, multi-port scanning | No Info | No Info |
| 185.156.177.11 | HOSTKEY B.v. | Russia | 87,360.7 | Credential stuffing, multi-port scanning | No Tor | Ports 3389 (MS RDP), 5985 (WinRM), 445 (SMB) open |
| 104.248.75.197 | Digital Ocean, LLC | U.S. | 86,356.8 | Port scanning (ports 5900) | No Tor | Debian system with OpenSSH, Ports 123 (NTP) & 22 (SSH) open |
| 104.248.67.48 | Digital Ocean, LLC | U.S. | 84,168.8 | Port scanning (ports 5900) | No Tor | OpenSSH, Port 22 (SSH) open |
| 138.186.51.10 | RS NET EIRELI ME | Brazil | 79,218.1 | Credential stuffing, multi-port scanning | No Tor | Dropbear SSH server, Ports 80, 22 open |
| 128.199.41.16 | Digital Ocean, LLC | Netherlands | 77,360.5 | Port scanning (ports 5900) | No Tor | Debian system with OpenSSH, Ports 123 (NTP) & 22 (SSH) open |
| 185.156.177.44 | HOSTKEY B.v. | Russia | 76,381.8 | Credential stuffing, multi-port scanning | No Tor | Ports 5985 (WinRM) & 445 (SMB) open |
| 193.188.22.114 | Hostkey B.v. | Russia | 76,181.2 | Credential stuffing, multi-port scanning | No Tor | Ports 3389 (MS RDP), 5985 (WinRM), 445 (SMB) open |
| 218.237.65.80 | SK Broadband Co Ltd | South Korea | 74,701.3 | Port scanning (ports 443, 53, 22, 80) | No Info | No Info |
| 190.98.242.100 | Gtd Internet S.A. | Chile | 70,082.6 | HTTP attacks, multi-port scanning | No Tor | Port 10443 open |
| 192.250.197.246 | CNSERVERS LLC | U.S. | 69,088.7 | Credential stuffing, multi-port scanning | No Tor | Werkzeug (WSGI for Python), nginx, php, MySQL, Ports 21 (FTP), 8888 (Alt-HTTPD), 80 (HTTP), 3306 (MySQL) open |
| 190.0.1.102 | EPM Telecomunicaciones S.A. E.S.P. | Colombia | 67,861.6 | HTTP attacks, multi-port scanning | No Tor | Ports 137 (netbios) & 1723 (PPTP) open |
| 87.197.110.12 | Slovak Telecom, a. s. | Slovakia | 62,035.5 | Port scanning (ports 25) | No Tor | PPTP Port 1723 open |
| 112.175.127.179 | Korea Telecom | South Korea | 60,944.2 | Port scanning (48 unique ports) | No Info | No Info |
| 66.113.228.81 | Hostway Corporation | U.S. | 59,736.2 | Port scanning (ports 445, 1433) | No Tor | MS ESMTP, Windows, Ports 80, 21 and 25 open |
| 218.92.0.200 | China Telecom | China | 58,908.4 | Credential stuffing, multi-port scanning | No Info | No Info |
| 193.175.11.134 | Verein zur Foerderung eines Deutschen Forschun... | Germany | 58,639.3 | Credential stuffing, multi-port scanning | No Tor | Postfix, Ports 1194, 443, 5001, 25 open |
| 194.187.175.68 | GTECH S.p.A. | Italy | 57,930.7 | Port scanning (45 unique ports) | No Tor | Ports 443 & 80 open |
| 167.99.163.54 | Digital Ocean, LLC | U.S. | 55,731.6 | Port scanning (ports 5900) | No Tor | Debian system with OpenSSH, Ports 123 (NTP) & 22 (SSH) open |
| 112.175.127.186 | Korea Telecom | South Korea | 55,644.2 | Port scanning (46 unique ports) | No Info | No Info |
| 185.234.218.16 | Sprint S.A. | Ireland | 54,835.6 | Credential stuffing, multi-port scanning | No Tor | Ports 3389, 445, 5985, 137 open |
| 138.186.165.143 | Clic Rapido Eireli | Brazil | 53,797.4 | Port scanning (ports 445, 1433) | No Tor | MikroTik bandwidth-test server |
| 112.175.126.18 | Korea Telecom | South Korea | 53,251.4 | Port scanning (42 unique ports) | No Info | No Info |
| 138.186.107.206 | Catalão Bandnet Serviços Multimídia LTDA - ME | Brazil | 51,376.6 | Credential stuffing, multi-port scanning, HTTP attacks | No Tor | MikroTik bandwidth-test server |
| 193.56.28.164 | Sprint S.A. | United Kingdom | 48,627.8 | Port scanning (ports 25) | No Tor | MS IIS, Ports 445 (MS SMB), 137 (Netbios), 443 (HTTPS), 80 (HTTP), 5985 (WinRM) open |
| 138.186.51.37 | RS NET EIRELI ME | Brazil | 48,507.3 | Credential stuffing, multi-port scanning, HTTP attacks | No Tor | Dahua DVR, MikroTik router, bandwidth test server, Ports 37777, 1723, 2000, 80, 22, 23, 21 open |
| 185.175.93.4 | IP CHistyakov Mihail Viktorovich | Spain | 48,058.3 | No Info | No Info | No Info |
| 84.92.64.137 | British Telecommunications PLC | United Kingdom | 46,833.3 | Port scanning (SMTP port 25) | No Tor | MS IIS, Ports 1723 (PPTP), 443 (HTTPS), 8080 (Alt-HTTP) open |
Table 2. Top attacking IP addresses in descending order
Top Targeted Ports
SMB port 445 was the number one attacked port in Latin America by a large margin. In a distant second was port, VNC 5900, which was being attacked all over the world during this time period. This activity is not typical, hence the investigative threat hunting we are doing on Twitter mentioned previously. SSH port 22 and Telnet port 23 followed this activity. Both of these ports (along with port 445) are commonly targeted as exploiting a vulnerability on either port can give a malicious actor access to the entire system.
There are no unique ports targeted in Latin America during this time period, what stood out the most was the focus on web applications and web databases. In addition to some of the most commonly targeted ports, the number of non-standard HTTP port (81, 8443, 8088, and 8080) targeting, and other application ports like Microsoft SMB port 445, and Microsoft CRM port 5555 makes it clear that attackers were targeting applications in the Latin America.
Also noteworthy was the apparent attempt to compromise IoT systems in Latin America by targeting ports 7547 and 8291, both of which are only used by SOHO routers and are commonly attacked by IoT botnets (thingbots). We called out these ports in our 2017 report, The Hunt for IoT: The Rise of Thingbots. Latin America and the Middle East were the only regions seen where these services were targeted.
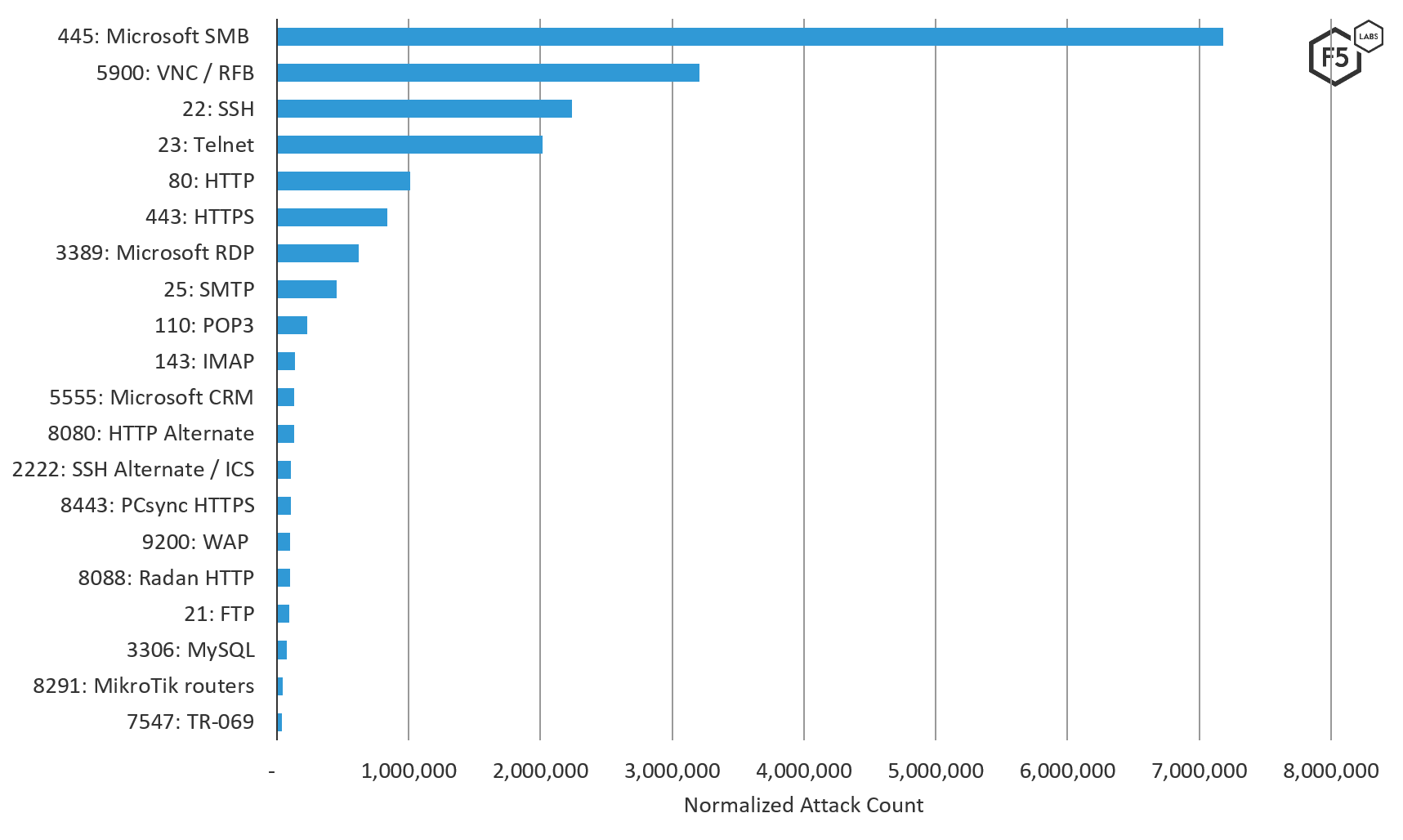
Figure 7. Top 20 ports attacked in Latin America, August through October 2019
Conclusion
In general, the best approach a security team can take as defenders in this modern threat landscape is one of “assume breach.” This is not a FUD (fear, uncertainty, and doubt) position, this is a realistic position backed up by the volume of attack traffic all systems touching the Internet receive, the likelihood of vulnerabilities existing, and the amount of compromised credentials available to attackers. When you take an “assume breach” defensive position, you are collecting attack traffic and monitoring your logs. You can use this high-level attack data to compare against the attack traffic directly hitting our own network. This will help you rule out run-of-the-mill attack traffic, or help you determine whether or not you are being targeted, in which case, investigating the attack sources and patterns is a worthwhile activity.
Additionally, locking down any of the top targeted ports that do not absolutely require unfettered Internet access should be completed as soon as possible. And because default vendor credentials are commonly left in place, and the volume of breached credentials in 2017 was enough to determine that many usernames and passwords are now considered “public,” all organizations should have credential stuffing protection in place. Particularly for any system with remote authentication, and especially administrative remote access. See F5 Labs report Lessons Learned from a Decade of Data Breachesfor more data on these breached passwords.
Security Controls
To mitigate the types of attacks discussed here, we recommend the following security controls (/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls.html) be put in place:
Recommendations
- Use firewalls to restrict all unnecessary access to commonly attacked ports that must be exposed publicly.
- Never expose internal databases publicly, and restrict access to internal data on a need-to-know basis.
- Prioritize risk mitigation for commonly attacked ports that require external access (like HTTP and SSH) for vulnerability management.
- Protect applications accessible over SSH using brute force restrictions.
- Disable all vendor default credentials (commonly used in SSH brute force attacks) on all systems before deploying them publicly.
- Implement geo IP address blocking of commonly attacking countries that your organization does not need to communicate with.


