F5 Labs, in conjunction with our partner Baffin Bay Networks, set out to research the global attack landscape to get a better understanding of the threat landscape across multiple regions, identify consistencies in attackers and targeted ports, and discover what was unique in each region. In this research series we look at attacks over the same 90-day period in Europe, the United States, Canada, and Australia. This article covers attack traffic destined for European IP addresses from December 1, 2018 through March 1, 2019, and how it compares to the other regions.
- The majority of attacks against Europe came from IP addresses in the Netherlands, followed by the United States, China, Russia, and France (in that order).
- The networks of the top attacking IP addresses were used to target destinations all over the globe. However, the IP addresses used in the attacks against European destinations were not seen attacking other regions in the same period.
- The top attacked ports were 5060 for SIP, 445 for Microsoft Server Message Block (SMB), and 2222 for non-standard SSH access—very similar to what we saw in Australia and Canada.
- Europe received more attacks from within its own geographic region than any other region.
Top Attacking Countries
Systems deployed in Europe are targeted by IPs all over the world. Looking at the source countries of attacks by region on a global heatmap, the source countries of European attacks are very similar to source countries of attacks against Australia and Canada. The US receives far fewer attacks from European IPs than Europe, Canada, or Australia does.
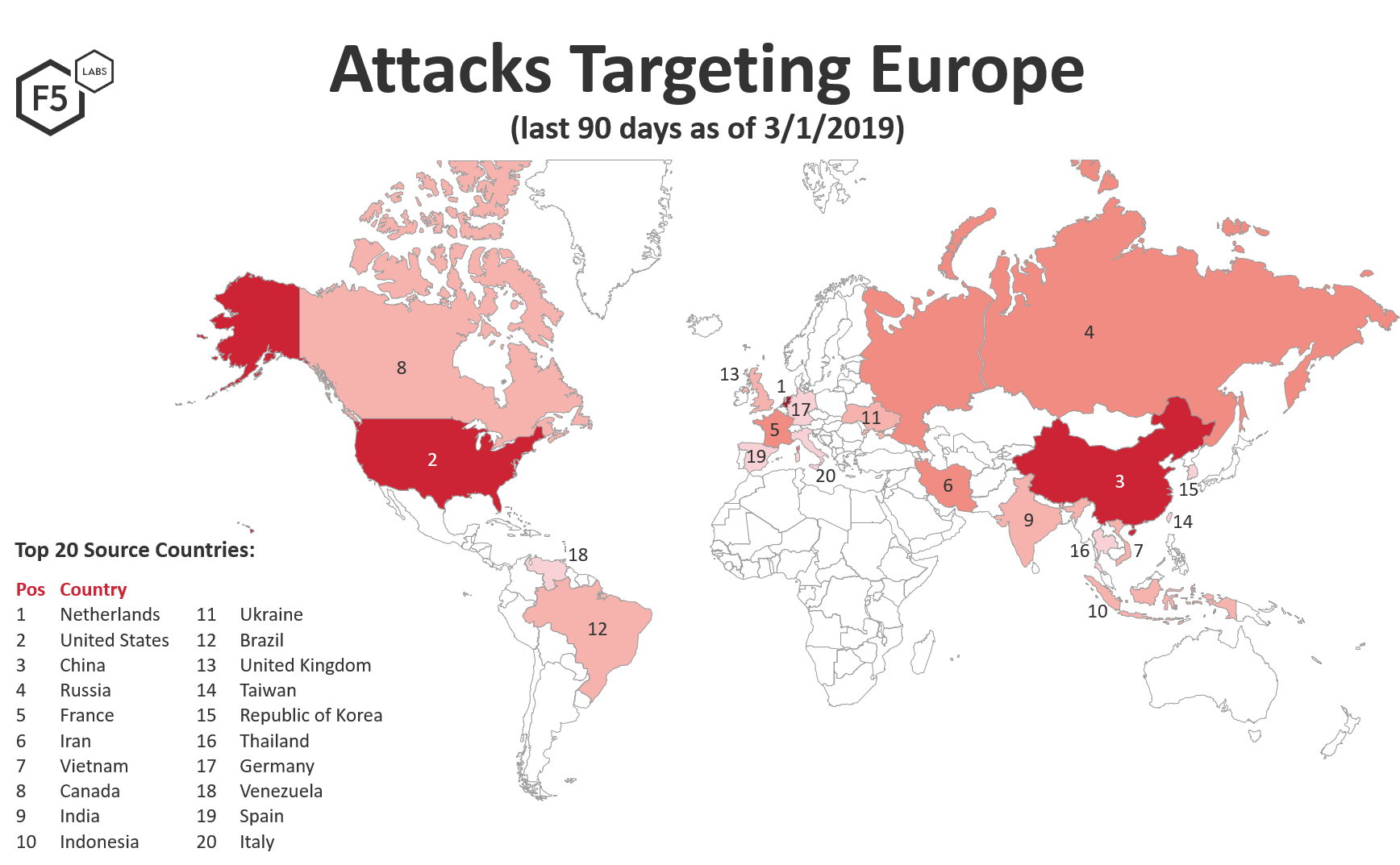
Figure 1. Source countries of attacks targeting Europe.
The Netherlands was the top source traffic country of attacks against European systems from Dec 1, 2018 through March 1, 2019. IPs in the Netherlands launched 1.5 times more attacks against European systems than IPs in the US or China, and 6 times more attacks than IPs in Indonesia in the tenth position.
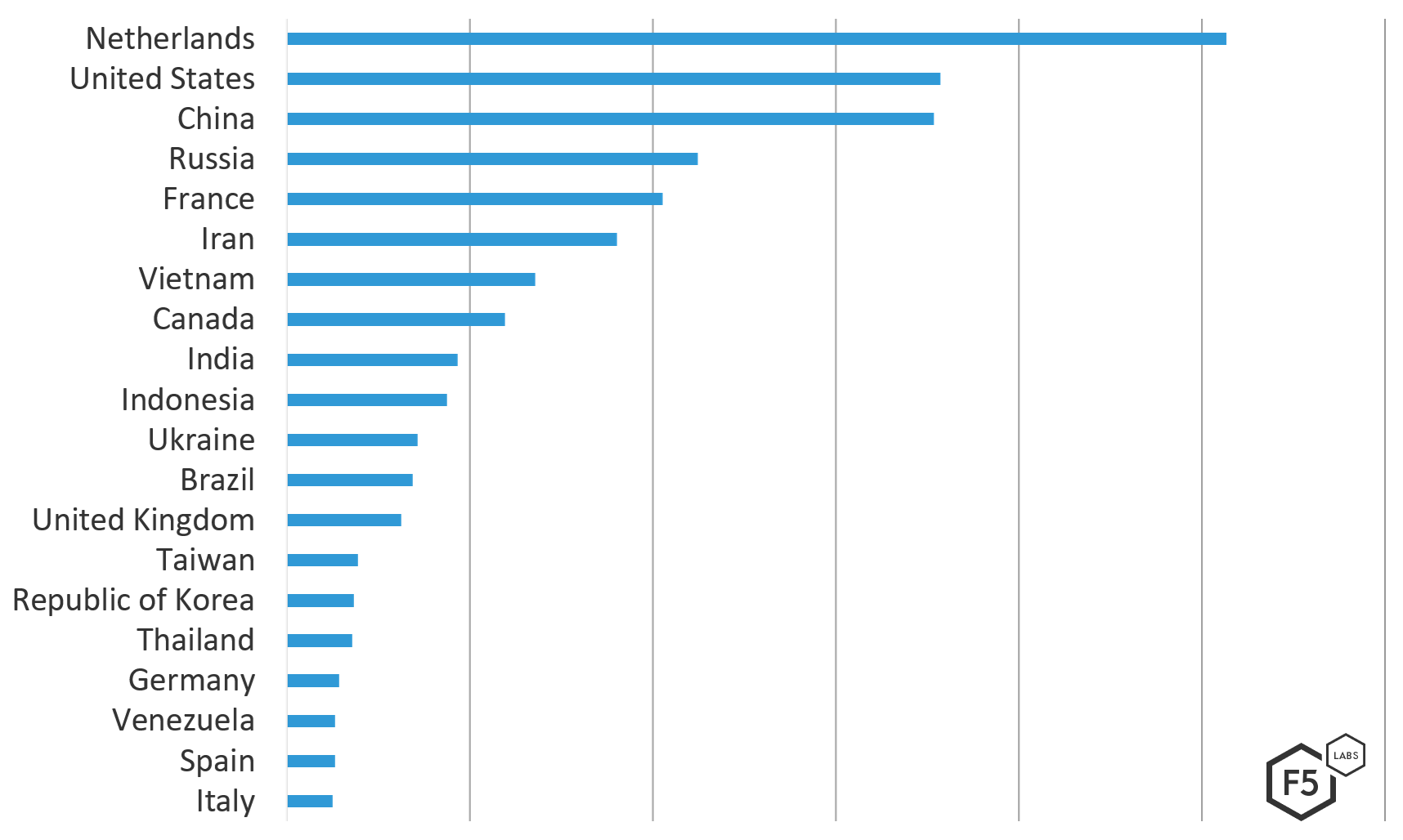
Figure 2. Top Attacking Countries by Count
Top Attacking Networks (ASNs)
The Netherlands-based network of HostPalace Web Solutions (ASN 133229) launched the largest number of attacks destined for European IP addresses, followed by France’s Online SAS (ASN 12876), and NForce Entertainment (ASN 43350), also from the Netherlands. All three of these companies are web hosting providers whose networks routinely show up in our top threat actor networks lists.
To get a sense of attack volume by ASN, Figure 2 shows the top 25 ASNs in ranking order of attack count.
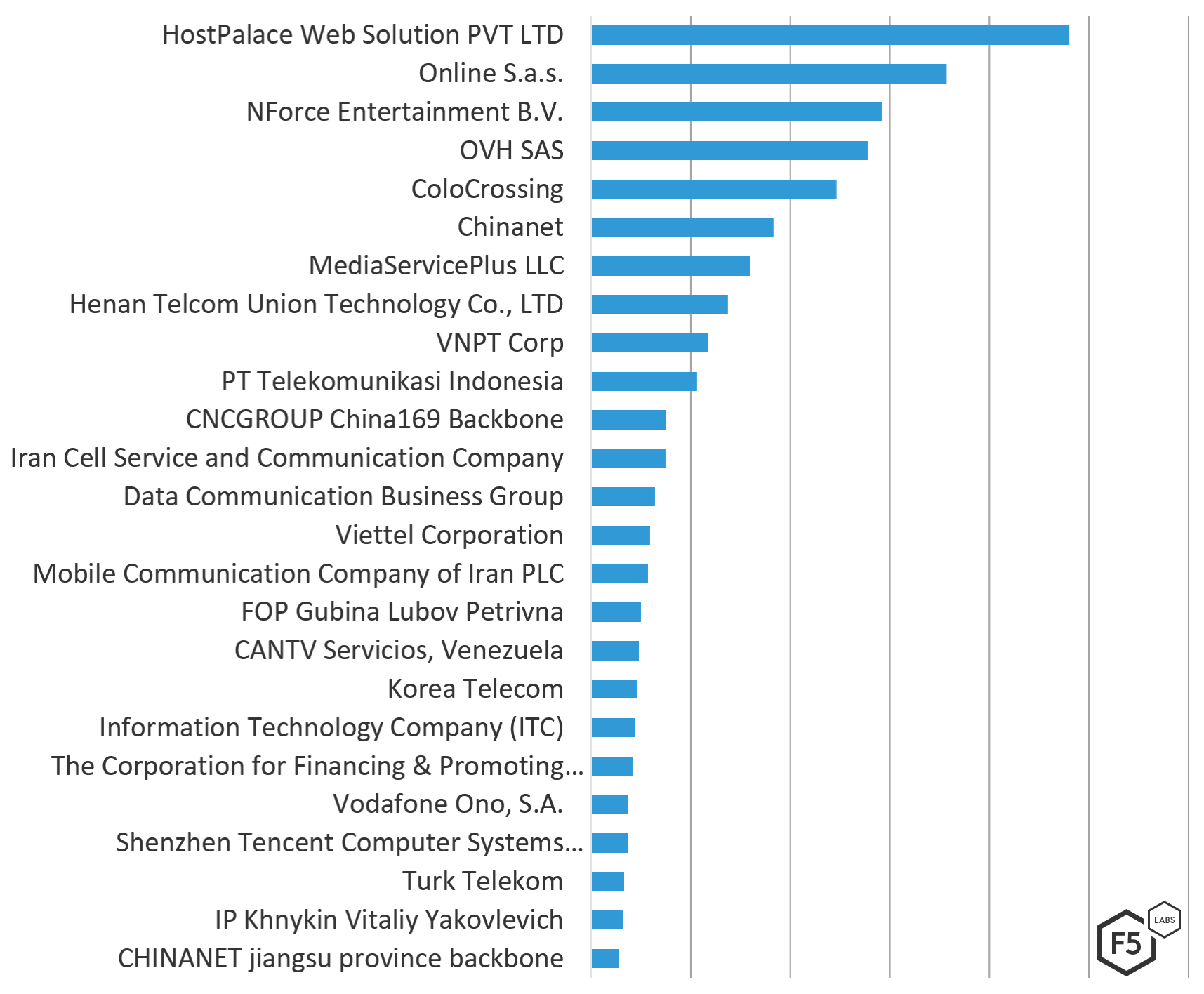
Figure 3. Top 25 Attacking ASNs by attack count
The following table shows the top 50 attacking ASNs in order of highest to lowest number of attacks. Seventy-two percent of these ASNs are Internet service providers, 28% are web hosting providers.
| ASN | ASN Organization | Country | Industry |
| 133229 | HostPalace Web Solution PVT LTD | Netherlands | Hosting |
| 2876 | Online S.a.s. | France | Hosting |
| 43350 | NForce Entertainment B.V. | Netherlands | ISP |
| 16276 | OVH SAS | France | Hosting |
| 36352 | ColoCrossing | United States | ISP |
| 4134 | Chinanet | China | ISP |
| 50113 | MediaServicePlus LLC | Russia | ISP |
| 56005 | Henan Telcom Union Technology Co., LTD | China | Hosting |
| 45899 | VNPT Corp | Vietnam | ISP |
| 17974 | PT Telekomunikasi Indonesia | Indonesia | ISP |
| 4837 | CNCGROUP China169 Backbone | China | ISP |
| 44244 | Iran Cell Service and Communication Company | Iran | ISP |
| 3462 | Data Communication Business Group | Taiwan | ISP |
| 7552 | Viettel Corporation | Vietnam | ISP |
| 197207 | Mobile Communication Company of Iran PLC | Iran | ISP |
| 58271 | FOP Gubina Lubov Petrivna | Ukraine | Hosting |
| 8048 | CANTV Servicios | Venuzuela | ISP |
| 4766 | Korea Telecom | South Korea | ISP |
| 12880 | Information Technology Company (ITC) | Iran | ISP |
| 18403 | The Corporation for Financing & Promoting Tech... | Vietnam | ISP |
| 6739 | Vodafone Ono, S.A. | Spain | ISP |
| 45090 | Shenzhen Tencent Computer Systems Company Limited | China | ISP |
| 9121 | Turk Telekom | Turkey | ISP |
| 206792 | IP Khnykin Vitaliy Yakovlevich | Russia | ISP |
| 23650 | CHINANET jiangsu province backbone | China | ISP |
| 9829 | National Internet Backbone | India | ISP |
| 31549 | Aria Shatel Company Ltd | Iran | ISP |
| 8151 | Uninet S.A. de C.V. | Mexico | ISP |
| 49877 | RM Engineering LLC | Russia | Hosting |
| 12389 | PJSC Rostelecom | Russia | ISP |
| 9299 | Philippine Long-Distance Telephone Company | Philippines | ISP |
| 4812 | China Telecom (Group) | China | ISP |
| 4808 | China Unicom Beijing Province Network | China | ISP |
| 8452 | TE Data | Norway | ISP |
| 16125 | UAB Cherry Servers | Lithuania | Hosting |
| 29073 | Quasi Networks LTD. | Netherlands | Hosting |
| 60999 | Libatech SAL | Lebanon | ISP |
| 31034 | Aruba S.p.A. | Italy | Hosting |
| 9498 | BHARTI Airtel Ltd. | India | ISP |
| 7922 | Comcast Cable Communications, LLC | United States | ISP |
| 44050 | Petersburg Internet Network ltd. | Russia | ISP |
| 60781 | LeaseWeb Netherlands B.V. | Netherlands | Hosting |
| 42590 | Telemost LLC | Ukraine | Hosting |
| 393406 | Digital Ocean, Inc. | United States | Hosting |
| 43754 | Asiatech Data Transfer Inc PLC | Iran | Hosting |
| 23969 | TOT Public Company Limited | Thailand | ISP |
| 18881 | TELEFÔNICA BRASIL S.A | Brazil | ISP |
| 16509 | Amazon.com, Inc. | United States | Hosting |
| 55577 | Atria Convergence Technologies pvt ltd | India | ISP |
| 4230 | CLARO S.A. | Brazil | ISP |
Note that Quasi Networks (ASN 29073), a known bulletproof hosting provider that did not respond to abuse complaints, has been “unassigned” as of March 24, 2019.
Top Attacking IP Addresses
Whereas we see consistency in the networks being used to launch attacks, the IP addresses used to target systems in Europe were unique, with the exception of 62.210.83.136 and 46.166.151.117. This can indicate that attackers are using specific (hosting) networks from which they know they can successfully launch attacks (and spinning up new systems or getting dynamic IPs from which to launch attacks), or they are exploiting vulnerabilities in systems resolving to ISPs, like residential or commercial IoT devices, and keep using new systems. Both scenarios result in new IPs from the same networks. The chart in Figure 4 shows the top 50 IP addresses attacking destinations in Europe from Dec 1, 2018 through March 1, 2019.
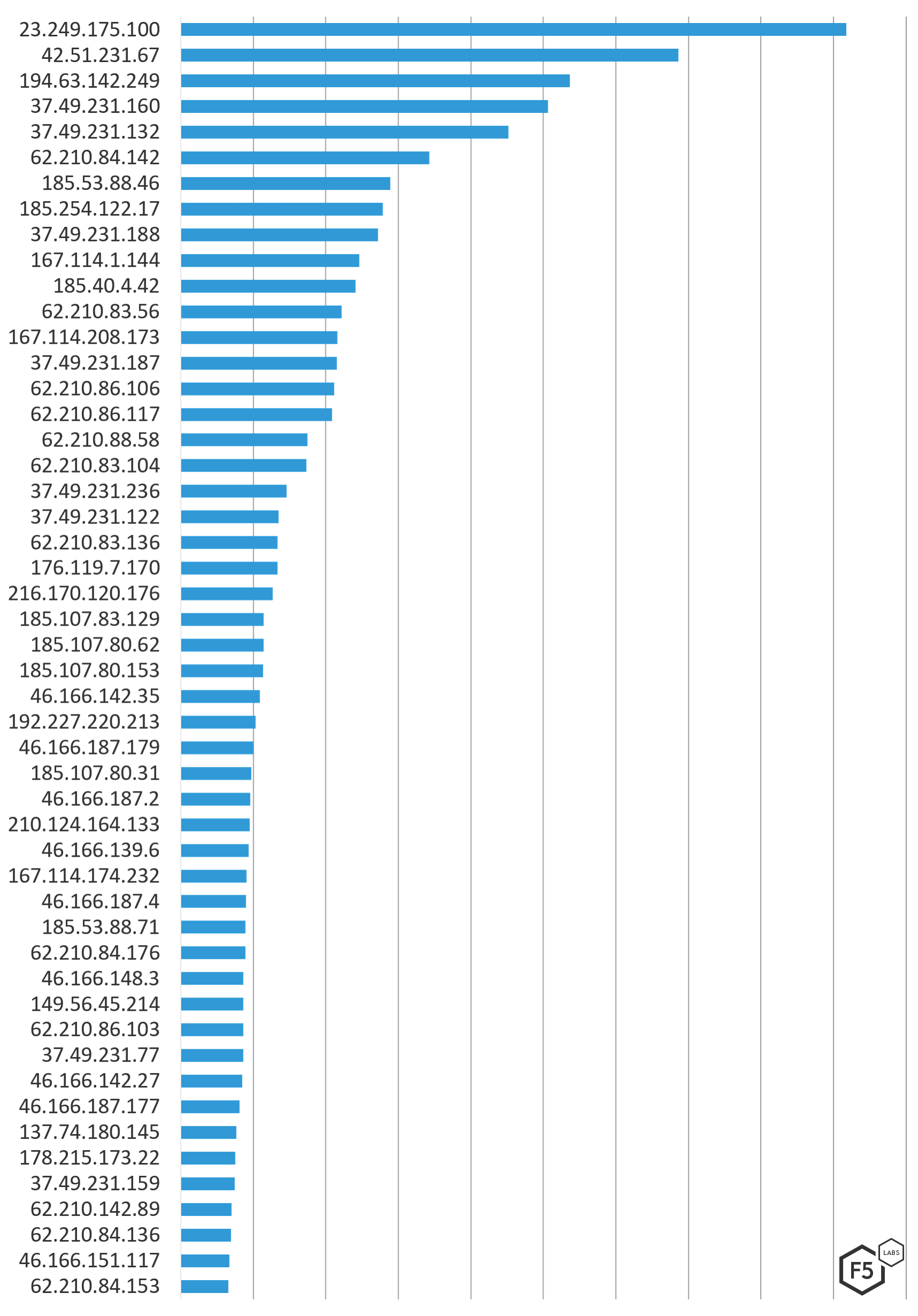
Figure 4. Top 50 attacking IPs
Organizations should check their network logs for connections from these IP addresses, and the owning networks should investigate these IP addresses for abuse.
| Source IP | ASN Organization | ASN | ISP | Country |
| 23.249.175.100 | ColoCrossing | 36352 | Net3 | United States |
| 42.51.231.67 | Henan Telcom Union Technology Co., LTD | 56005 | CNISP-Union Technology (Beijing) Co. | China |
| 194.63.142.249 | MediaServicePlus LLC | 50113 | MediaServicePlus LLC | Russia |
| 37.49.231.160 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 37.49.231.132 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 62.210.84.142 | Online S.a.s. | 12876 | Free SAS | France |
| 185.53.88.46 | Vitox Telecom | 209299 | Estonia | |
| 185.254.122.17 | UGB Hosting OU | 206485 | Russia | |
| 37.49.231.188 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 167.114.1.144 | OVH SAS | 16276 | OVH Hosting | Canada |
| 185.40.4.42 | MediaServicePlus LLC | 50113 | MediaServicePlus LLC | Russia |
| 62.210.83.56 | Online S.a.s. | 12876 | Free SAS | France |
| 167.114.208.173 | OVH SAS | 16276 | OVH Hosting | Canada |
| 37.49.231.187 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 62.210.86.106 | Online S.a.s. | 12876 | Free SAS | France |
| 62.210.86.117 | Online S.a.s. | 12876 | Free SAS | France |
| 62.210.88.58 | Online S.a.s. | 12876 | Free SAS | France |
| 62.210.83.104 | Online S.a.s. | 12876 | Free SAS | France |
| 37.49.231.236 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 37.49.231.122 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 62.210.83.136 | Online S.a.s. | 12876 | Free SAS | France |
| 176.119.7.170 | FOP Gubina Lubov Petrivna | 58271 | FOP Gubina Lubov Petrivna | Ukraine |
| 216.170.120.176 | ColoCrossing | 36352 | Net3 | United States |
| 185.107.83.129 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 185.107.80.62 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 185.107.80.153 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 46.166.142.35 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 192.227.220.213 | ColoCrossing | 36352 | ColoCrossing | United States |
| 46.166.187.179 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 185.107.80.31 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 46.166.187.2 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 210.124.164.133 | Korea Telecom | 4766 | LG DACOM Corporation | Republic of Korea |
| 46.166.139.6 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 167.114.174.232 | OVH SAS | 16276 | OVH Hosting | Canada |
| 46.166.187.4 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 185.53.88.71 | Vitox Telecom | 209299 | Estonia | |
| 62.210.84.176 | Online S.a.s. | 12876 | Free SAS | France |
| 46.166.148.3 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 149.56.45.214 | OVH SAS | 16276 | OVH Hosting | Canada |
| 62.210.86.103 | Online S.a.s. | 12876 | Free SAS | France |
| 37.49.231.77 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 46.166.142.27 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 46.166.187.177 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 137.74.180.145 | OVH SAS | 16276 | OVH SAS | France |
| 178.215.173.22 | Telemost LLC | 42590 | Telemost LLC | Ukraine |
| 37.49.231.159 | HostPalace Web Solution PVT LTD | 133229 | Estro Web Services Private Limited | Netherlands |
| 62.210.142.89 | Online S.a.s. | 12876 | Free SAS | France |
| 62.210.84.136 | Online S.a.s. | 12876 | Free SAS | France |
| 46.166.151.117 | NForce Entertainment B.V. | 43350 | NFOrce Entertainment B.V. | Netherlands |
| 62.210.84.153 | Online S.a.s. | 12876 | Free SAS | France |
Top Targeted Ports
Looking at the targeted ports gives us a sense of the types of systems the attackers are after. In Europe, the top attacked port was 5060, used by the SIP service for VoIP connectivity to phones and video conferencing systems. This is routinely a top attacked port when looking at attack traffic against a specific location during global dignitary events, such as when President Trump met with Kim Jung Un in Singapore in 2018 and with Vladimir Putin in Helsinki in 2018. The second most-attacked port in Europe is Microsoft SMB port 445, followed by port 2222, which is commonly used as a non-standard SSH port, but is also used by Industrial Control Systems.
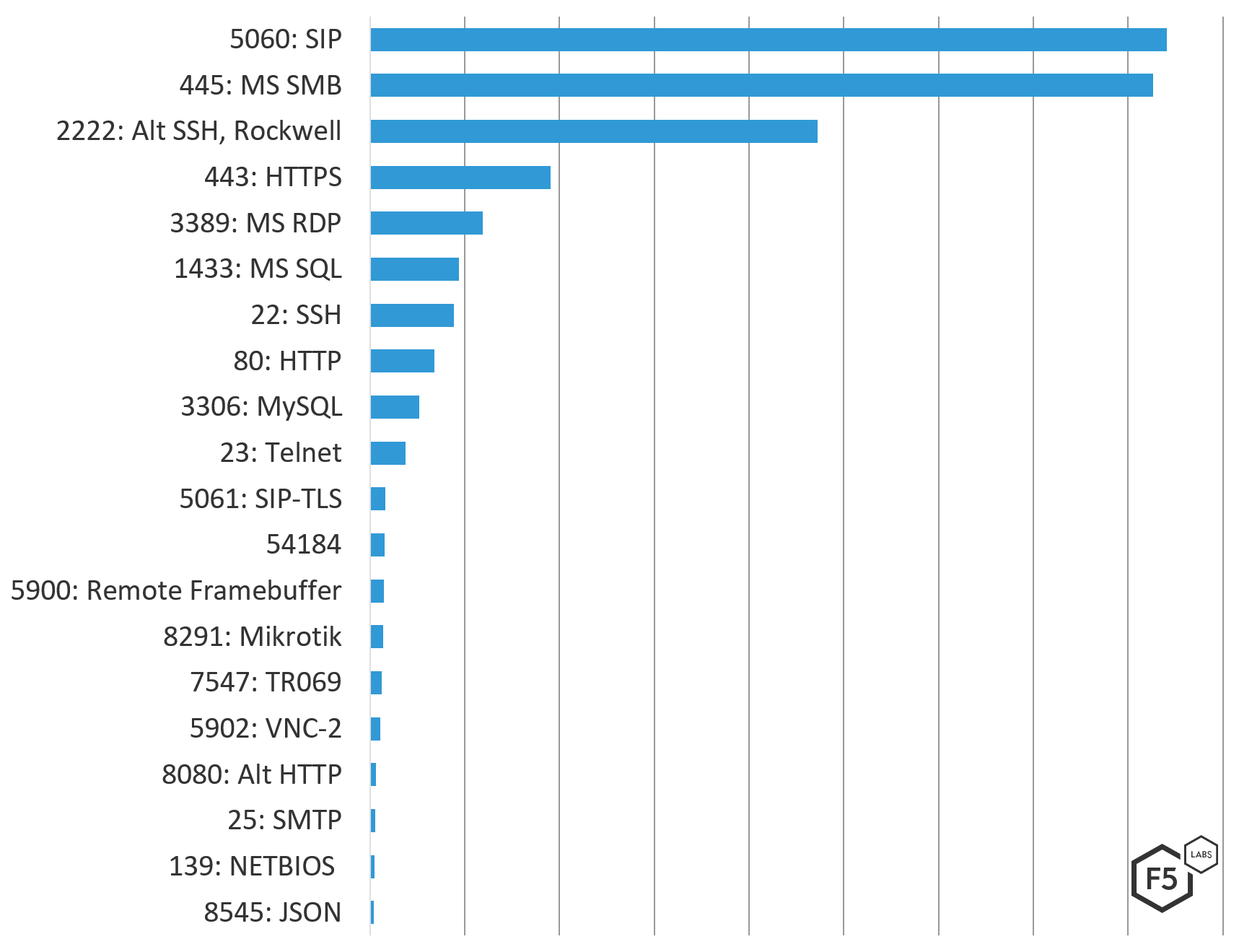
Figure 5. Top 20 attacked ports and services
Conclusion
Organizations should continually run external vulnerability scans to discover what systems are exposed publicly, and on which specific ports. Any systems exposed publicly with the top attacked ports open should be prioritized for vulnerability management. A lot of the attacks we see on ports supporting access services like SSH are brute force, so any public login page should have adequate brute force protections in place. Database ports like 1433 and 3306, which should not be exposed publicly, are top attacked ports. Organizations should do their best to protect databases and not expose them directly to the Internet. Furthermore, logs should be reviewed for any top attacking IP matches. If you are experiencing attacks from any of these top IP addresses, you should submit abuse complaints to the owners of the ASNs and ISPs so they can shut down the attacking systems.
For those interested in IP blocking, it can be troublesome not only to maintain large IP blocklists, but also to block IP addresses within ISPs that offer Internet service to residences that might be customers. In these cases, the attacking system is likely to be an infected IoT device that the resident doesn’t know is infected, and it likely won’t get cleaned up. Blocking traffic from entire ASNs or an entire ISP can be problematic for the same reason—blocking their entire network would block all of their customers from doing business with you. Unless of course it’s an ISP supporting a country you don’t do business with. In that case, geolocation blocking at a country level can be effective way to reduce a large amount of attack traffic and save your systems the unnecessary processing. For this reason, it is best to drop traffic based on the attack pattern on your network and web application firewalls.
We will continue to monitor global attacks and analyze at a regional level quarterly, and include the Asia-Pacific, Middle East and North Africa, and Latin American regions moving forward. If you are an implicated ASN or ISP, please reach out to us at F5LabsTeam@F5.com and we’ll be happy to share further information with you.
Recommendations
- Organizations exposing commonly attacked ports publicly to the internet, especially systems that shouldn’t be accessible over the internet like databases, should do their best to restrict public accessibility through their firewall.
- Any commonly attacked ports that require external access, like HTTP and SSH, should be prioritized for vulnerability management.
- Organizations should look to implement geo IP blocking of commonly attacking countries that the business does not have a need to communicate with.


