Password login attacks, especially credential stuffing attacks, are still one of the most common cyberattacks on the Internet. F5 Labs and Shape Security extensively looked at the patterns and trends associated with credential stuffing in the 2021 Credential Stuffing Report.
In part 2 of this series on credential stuffing tools and techniques, we dive deeper into how attackers actually “stuff” credentials. In part 1, we explored how cyberattackers configure credential stuffing attack tools. We used OpenBullet, a common credential attack tool, as our example. In this second part, we look at how attackers use different tools, take over a mailbox, and overcome simple defenses.
Launching a Credential Stuffing Attack
Previously we showed you how attackers configure the OpenBullet credential stuffing tool. Now, attackers can try launching the attack in the tool’s Runner section, as shown in Figure 1. This is where they can choose how many bots to run at a time. They can also run attacks against multiple sites simultaneously.
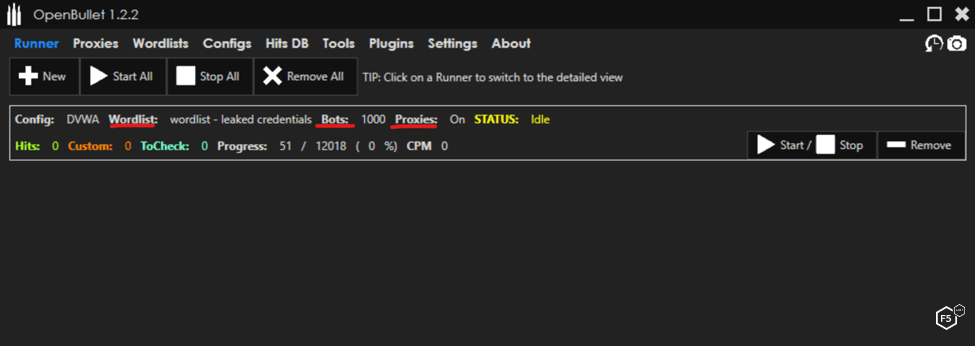
Figure 1. Launching a credential stuffing attack in OpenBullet.
Breaking Through Credential Stuffing Defenses
Many organizations put controls in place to detect and block this credential stuffing automation. F5 Labs took a closer look at the various tools credential stuffing bots use to bypass defenses. We’re going to configure OpenBullet to evade a common first line of defense: CAPTCHAs.
CAPTCHA is a contrived acronym for "Completely Automated Public Turing [test to tell] Computers and Humans Apart." It does this by forcing users to complete a challenge to prove they are not a bot. Newer versions of CAPTCHAs do this selectively—only if bot-type behavior is detected.
Many CAPTCHA bypass services are available, and they fall into two categories: optical character recognition (OCR) solutions and human-based. For more detail on this, see the F5 Labs examination of the human-based CAPTCHA market (/content/f5-labs-v2/en/labs/articles/cisotociso/turing-in-his-grave--what-human-captcha-solvers-reveal-about-con.html).
Like everything else in the tech world, there is a software as a service (SaaS) solution, specifically a CAPTCHA-solving service. These services range in price from about 40 cents to $5 for 1,000 CAPTCHA solves. This is as simple as signing up for a service (Figure 2) and entering the service name and API key in the tool’s CAPTCHA section (Figure 3).
Figure 2. Signing up for a CAPTCHA solving service.
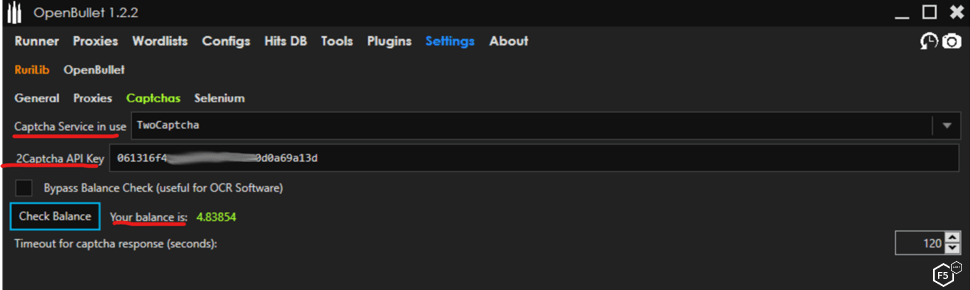
Figure 3. Entering the service name and API key in the tool’s CAPTCHA section.
Now the attacker can add a Solve CAPTCHA block to their configuration. This block requires the URL of the site containing the CAPTCHA and the Site Key, which is found in the page’s source code. The solved CAPTCHA will be stored as <SOLUTION> and can be sent in the POST, as shown in Figure 4.
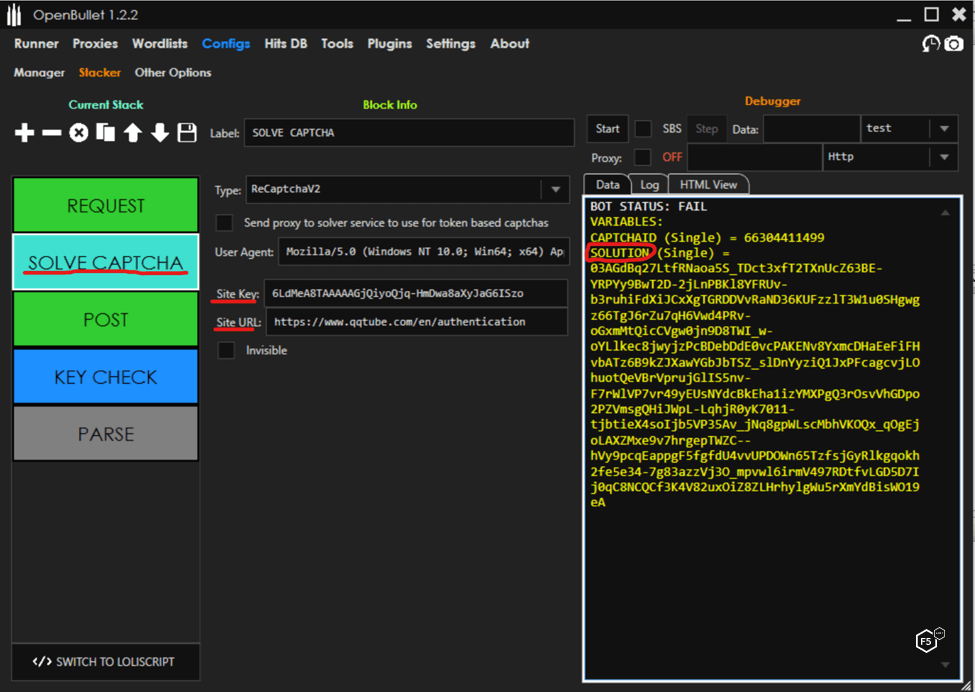
Figure 4. Telling OpenBullet to solve the CAPTCHA.
Using Credential Stuffing to Take Over an Email Account
If there is something of value behind a login, it’s a good bet automated attacks are targeting it. The sophistication of these attacks depends on the malicious automation controls in place on the target system, as attackers will invest the minimum effort necessary. They will retool with higher sophistication once their attacks are successfully mitigated. Also, there are other ways besides the direct approach to get into a high-value account using credential stuffing.
One strategy is to compromise email accounts with a credential stuffing attack. Then an attacker can use those accounts to reset passwords on the high-value logins. These compromised inboxes are easily searched to find out which accounts of interest a user can configure. Figure 5 breaks down the process.
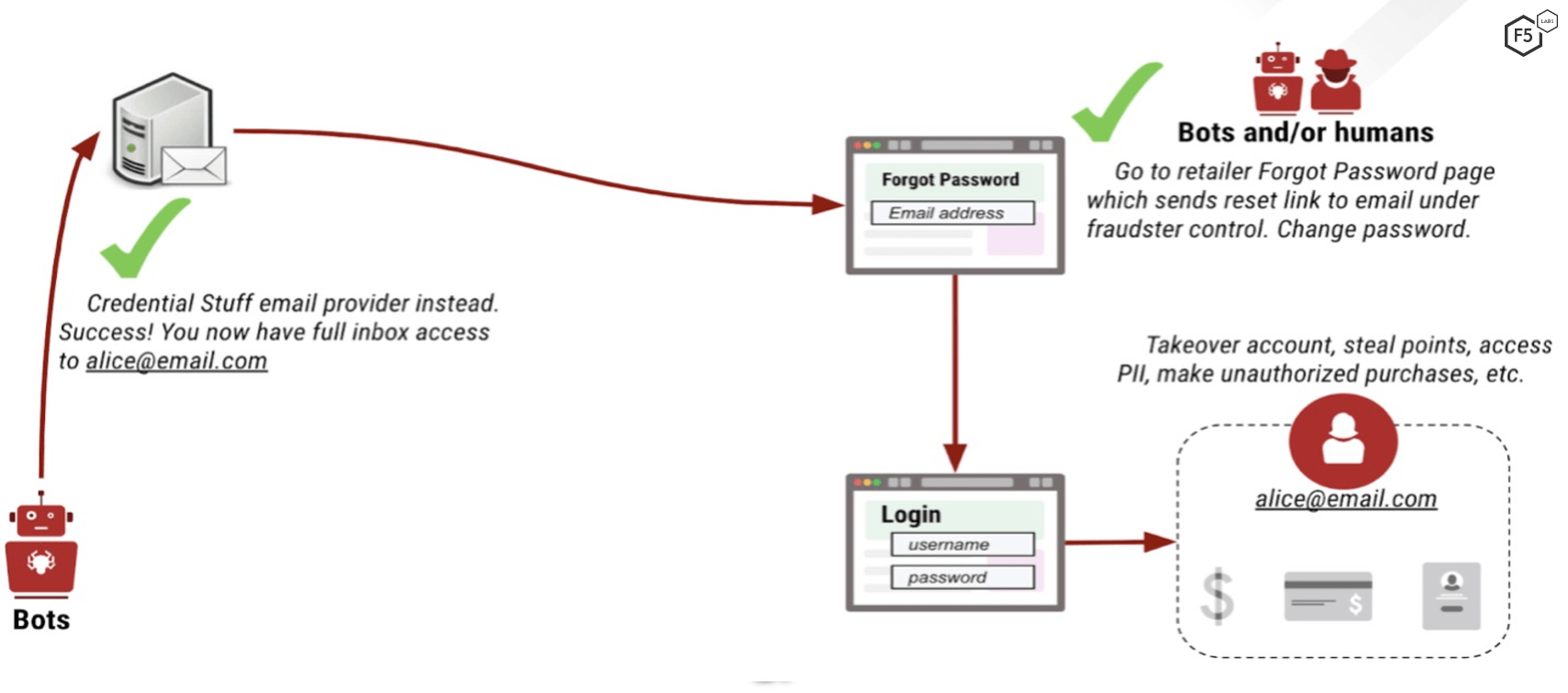
Figure 5. Credential stuffing email to gain access to other accounts.
The basic attack flow is as follows:
The attacker is unable to credential stuff a site directly because of proper bot mitigation controls.
Instead, the attacker runs credential stuffing attacks on unprotected email providers.
Once a mailbox is compromised, the attacker then searches the mail for keywords denoting accounts they are interested in.
Access to the email inbox is then used to initiate a password reset on the targeted high-value account.
The attacker now has full access to the account, and all personally identifiable information (PII), points, payment information, or anything else available to the account.
Credential Stuffing Attack Tools Geared for Mailbox Attacks
Other credential attack tools are available, some of which are designed specifically for mailbox takeover attacks. One such tool is MailRanger. Much like OpenBullet, MailRanger allows attackers to import proxies and load combolists, as shown in Figure 6.
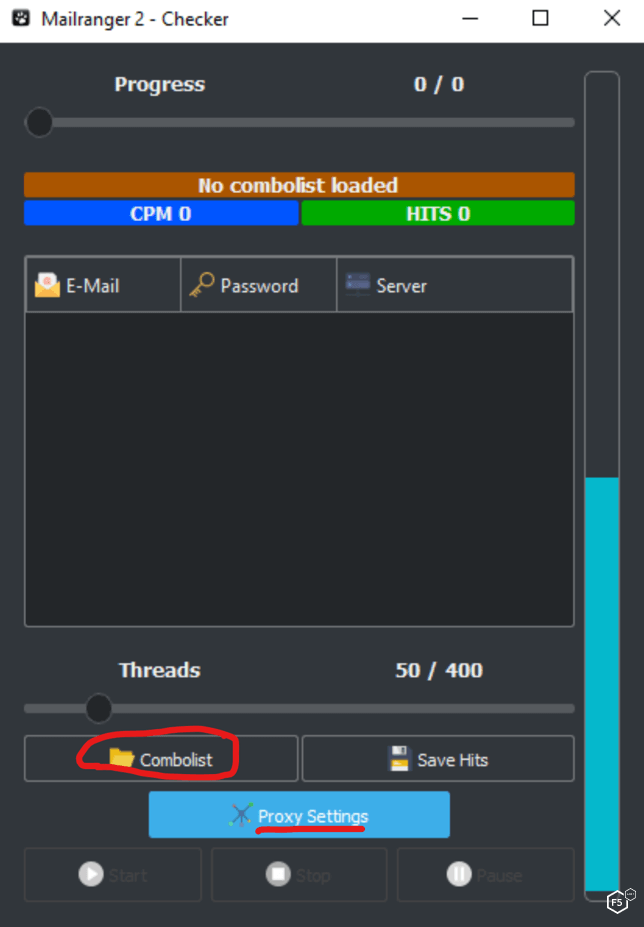
Figure 6. Loading credential combolist into MailRanger.
The difference between OpenBullet and MailRanger is that once the attacker loads the combolist containing email addresses and passwords, MailRanger does the rest. It will parse the email addresses and orchestrate the attack without further configuration. This is because MailRanger is an Internet Message Access Protocol (IMAP) client and is preconfigured with the IMAP host name for popular mail providers, including Gmail, Yahoo, and Microsoft. MailRanger will also automatically save successful mailbox takeovers.
Once the combolist is exhausted, the attacker can use the Search Phrases panel to look through the compromised email accounts for search phrases. Figure 7 shows the details of this function. This allows the attacker to hunt for target organizations the attacker is interested in.
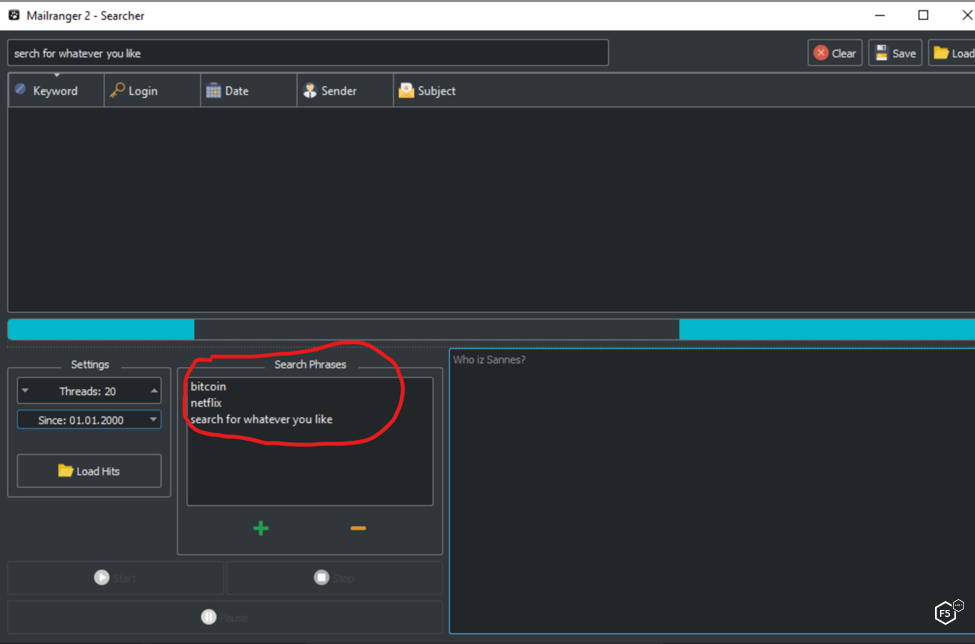
Figure 7. MailRanger’s email search phrases.
Now it is a simple process to manually go to the target site and request a password reset. The attacker can even create a mailbox rule to route emails to certain folders, ensuring the legitimate email owner does not see the password reset email.
Conclusion
We’ve looked at the ecosystem that facilitates attacks using automation or bots and how simple it is for bad actors to obtain the necessary resources and launch this type of attack.
These attacks exploit the built-in functionally of web and mobile applications. If an account has something of value, automated credential stuffing attacks are likely targeting it. Many times, malicious actors also target the password reset functionality, as this is another way to take over existing accounts.
Credential stuffing is a powerful attack technique that cybercriminals don’t hesitate to use for all kinds of fraud and mayhem. Be sure to have sufficient detection and protection systems in place.
Recommendations
- Regularly review web-facing logs to spot potential credential stuffing and brute force attacks.
- Ensure email accounts capable of account reset for critical logins are sufficiently protected against password login attacks.
- Deploy an intelligent antibot solution that uses more advanced controls beyond just IP address blocking, rate limiting, or CAPTCHA.


