
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
Welcome to this month's installment of the Sensor Intel Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data, looking at data from January of 2025, as well as looking back at 2024 data as a whole.
2024 in Review
A quick review of 2024’s data reveals some interesting trends regarding the overall level of scanning (hint: it went way up), the prevalence of scanning for IoT vulnerabilities, and that most of the scanning we see comes from just one type of provider.
Overall Traffic Compared to 2023 Increased by 91%
When looking at the raw sensor logs we observed 5.5 million events in 2022, and 5.1 million events in 2023. This increased significantly in 2024, with 8.7 million events observed, a 71% increase. However, given that the number of sensors we have varies at least somewhat over time, this might be misleading, so we normalized these events based on the number of sensors active per month and found that the increase in scanning was even more pronounced, rising 94% from 2023.
This is a massive increase, but we were somewhat suspicious of this result. We noted back in June of 2024 that there was a huge amount of scanning for CVE-2023-1389 – is it possible that this was single-handedly accounting for the huge increase?
This is not to say that a 94% increase in total scanning activity isn’t meaningful. We’re tracking scanners, and thus, if one scanner becomes dominant, that’s just what’s going on. But we wanted to get an idea of how much increase or decrease there was in a more generalized way.
We found that while removing CVE-2023-1389 had a small effect, accounting for approximately 3.5% of the total increase in traffic, the overall level of normalized traffic still increased 91% in 2024 as compared to 2023.
By comparison, the normalized change from 2022 to 2023 was a mere 5%, and if we go back even further, the largest increase in traffic we had seen previously was from 2021 to 2022, with an increase of 22%.
We think it’s fair to say that this indicates a notable change, and everyone should expect to see more web scanning in the future, as this trend does not seem to be on track to abate any time soon, with 2025 data showing a continuing high level of activity.
Scanning for IoT and Consumer Routers Dominate CVE Traffic
Out of all the scans logged by our sensors in 2024, we were able to identify CVE exploit attempts in only 5.4% of events. A great deal of the scanning activity we see is reconnaissance or looking for exposed credentials, but it is likely that our signature based approach to CVE matching may not be catching everything. Indeed, some recent research by F5 Labs has shown this to be the case. Check back next month to see what our new techniques for identifying CVE related traffic in our dataset have revealed.
Nevertheless, we did identify and track 146 CVEs that had exploit attempts over the course of 2024. Of these, 5 CVEs accounted for 5% of total traffic, and 75% of the total CVE related traffic during the year.
Fully one third (33%) were attempts to exploit CVE-2023-1389, a command injection vulnerability in the TP-Link Archer AX21 dual-band wifi router.
A quarter (25%) were attempting to exploit CVE-2017-9841, a remote code execution flaw in PHPUnit. On this particular vulnerability, we would like to suggest you read the excellent write up on this issue, written by the author of the PHPUnit software, “PHPUnit: A Security Risk?: The long story of a security problem that shouldn’t have been one” back in 2020.
CVE-2022-24847, an RCE against the GeoServer geospatial data software, accounted for 6%, and CVE-2022-22947 and CVE-2020-11625, a code injection attack against VMWare Spring Cloud Gateway, and a username enumeration flaw in AvertX IP cameras, each accounted for 5% of the traffic observed.
An honorable mention may go to CVE-2020-8958, a command injection vulnerability in Guangzhou consumer routers, which accounted for 4% of our traffic.
All told 42% of the overall CVE traffic were targeting IoT devices and consumer routers, just for these top 6 CVEs. We have been banging this drum for quite some time. IoT devices, especially consumer grade devices, often have easy to exploit vulnerabilities, are targeted heavily, and are often ignored, or are quite difficult to patch, making them a very attractive target.
Large enterprises may not feel this constitutes much of a risk – but consider possible scenarios carefully. Are you using IP cameras for security? Are your remote workers using vulnerable routers at home? Are you sure you don’t have any exposure to IoT devices?
Scanning Infrastructure Primarily Located on Hosting Providers
When analyzing the “top talkers” we observed by AS number, we found that 75% of traffic came from just the top 20 ASNs. By far the most traffic came from AS Number 209605, a hosting provider operating out of Lithuania called “UAB Host Baltic”, with nearly 20% of all the traffic we saw coming from this single provider and 62 distinct IP addresses, the majority from the 141.98.11.0/24 netblock.
The next highest was AS51167, Contabo GmbH, a Cloud VPS and hosting provider based in Munich, Germany, with 9% of the overall traffic.
Rounding out the top three, AS14061, Digital Ocean LLC, a well-known hosting provider, sent 6% of our traffic in 2024.
Other ASNs in our top 20 list show a similar pattern with the majority being hosting providers and smaller cloud service providers.
From this we can conclude that the majority of the scanning we see is conducted not by botnets formed of consumer devices, nor even residential proxy networks which we’ve seen used in various bots and automation traffic to get around IP reputation issues. Instead, it seems most of the scanning and exploit attempt activity we see comes from simple VMs and VPS machines on hosting providers.
Over the course of 2024, we did see at least a few scanners change infrastructure, including the very active BotPoke scanner we’ve been tracking in previous months, so we can say that some hosting providers are paying attention to this. But clearly there is more work to be done.
But now, let’s turn our attention to last month’s data, where there have been some significant changes to business as usual.
January Top 10 Scanned Review
There was a rather large amount of position and placement changes in our Top 10 CVE list for from December 2024 to January 2025.
The top three remained constant, with CVE-2023-1389 continuing to be our most scanned for vulnerability. We’ve mentioned this a lot before so you’re probably already familiar with it, but just in case, it’s an RCE vulnerability in TP-Link Archer AX21 consumer routers. Overall traffic for this vulnerability was down a little from last month, continuing a trend we’ve been observing since October of 2024.
CVE-2022-24847, a remote code execution vulnerability in the GeoServer software comes in second again this month, with the level of traffic remaining very consistent compared to last month.
CVE-2022-22947, a Spring Cloud Gateway code injection vulnerability, which has also appeared consistently in our top 10 for at least 12 months is in third place, and much like CVE-2022-24847 has been very consistent in prevalence month to month.
There were a few other changes; CVE-2023-23752, previously in 8th place, jumped to 5th, and CVE-2020-11625 fell from 4th to 6th place, and CVE-2022-42457 dropped from 5th to 8th.
Additionally, the 2018 JAWS Web Server vulnerability reappeared after an absence of a few months.
Here’s where things start to get more interesting.
CVE-2024-3721, a command injection vulnerability in a couple of TBK DVR models, was announced 04/13/2024, and we first saw exploit attempts appear on the 15th of that same month. It rapidly fell off, however, and we’d seen extremely low levels since. But this month, it spiked and got to 4th place in our Top 10 by volume, surging by two orders of magnitude!
CVE-2018-10561 also appeared. There’s been a relatively low level of scanning for this authentication bypass on Dasan GPON home routers, but just recently it ticked up a bit more and made it into this list.
January Vulnerabilities by the Numbers
Figure 3 shows January traffic for the top ten CVEs that we track. Note the appearance of CVE-2024-3721, and CVE-2018-1056, as well as the continuing domination of scanning for CVE-2023-1389. See further down for an easier to understand view using a logarithmic scale in Figure 5.
Targeting Trends
Figure 4 is a bump plot showing the change in traffic volume and position over the last twelve months. We can see the slow decrease in scanning for CVE-2023-1389. If we peer quite closely, the yellow stream is CVE-2024-3721, barely visible before, but now quite significant.
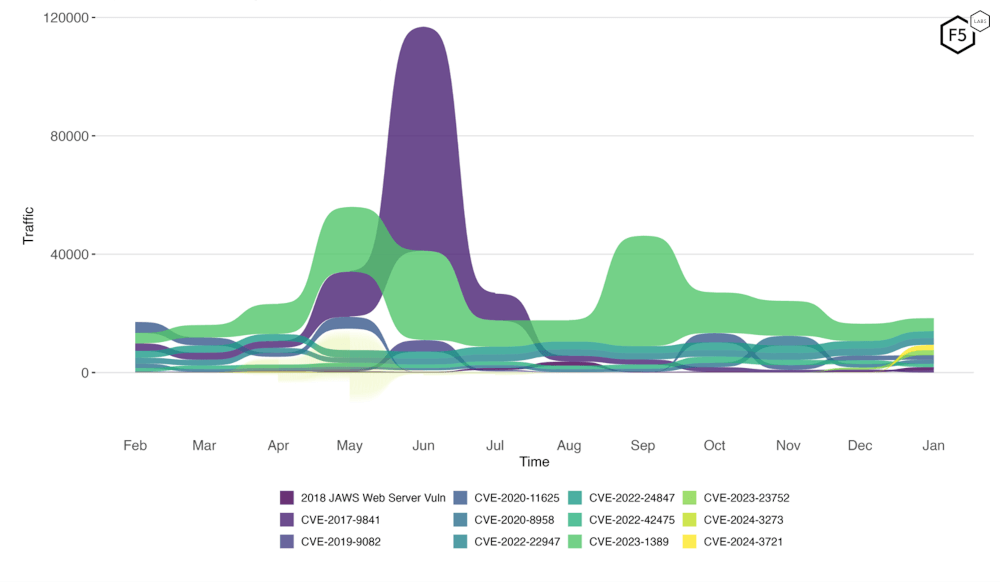
Figure 4. Evolution of vulnerability targeting in the last twelve months. Note the continued high level of scanning for CVE-2023-1389, and the appearance of CVE-2024-3721.
Long Term Trends
Figure 5 shows traffic for the top 19 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs.
The sudden re-emergence of scanning for CVE-2020-11625 continues, at the right of the top row for the fourth month. On the far righthand side of the third row, the massive increase in scanning for CVE-2023-23752 obviously continues, and in the middle of the last row, we can see CVE-2024-3721 jump. Each horizontal line on these charts represents an order of magnitude increase.
Last month we noted that CVE-2023-23752, an unauthorized access bug in Joomla! 4.0.0 to 4.2.7 has exploded, going from single digits to nearly 1000 events. It has continued at high levels, and continued to be primarily sourced from ‘66.63.187.168’, an IP currently owned by “Quadranet Enterprises, LLC”, a hosting provider based out of the USA, as we noted last month.
In the lower right corner, you can see the average of all the other 138 CVEs we currently track and note that these show a similar level of scanning since last month.
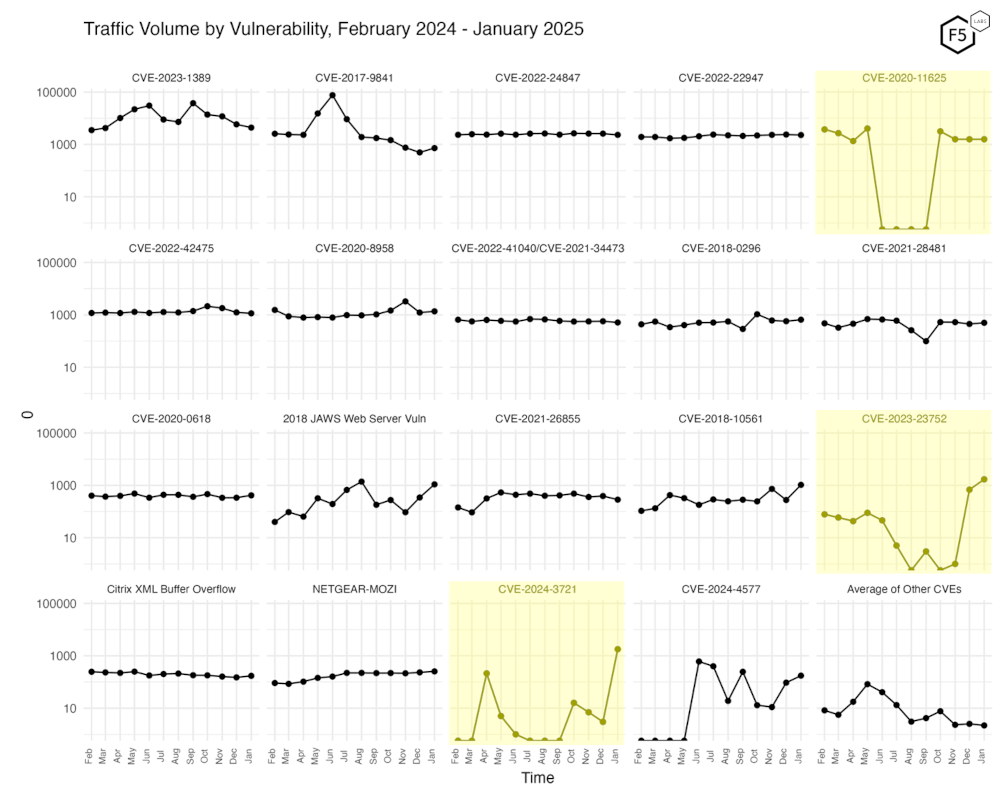
Figure 5. Traffic volume by vulnerability. This view accentuates the recent changes in CVE-2020-11625, CVE-2024-3721, and CVE-2023-23752.
Conclusions
We hope you enjoyed the high-level look at 2024 data, and hope you’ll come back soon to see what we’ve got in store. See you next month!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


