
Welcome to the Summary of the 2019 F5 Labs TLS Telemetry Report.
This year, we expanded the scope of our research to bring you deeper insights into how encryption on the web is constantly evolving. We look into which ciphers and SSL/TLS versions are being used to secure the Internet’s top websites and, for the first time, examine the use of digital certificates on the web and look at supporting protocols (such as DNS) and application layer headers.
A lot has happened in the world of encryption since we published the 2017 TLS Telemetry Report. Over the past two years, standards have been updated, browsers have evolved and a number of new protocols have been released that aim to secure all the remaining cleartext protocols still in wide use today.
Meanwhile, the global debate between technology providers and governments (also known as Crypto Wars 2.0) continues to rumble on. Governments are increasingly trying to control how encryption is used, and we frequently see poorly written (or purposefully vague) legislation introduced.
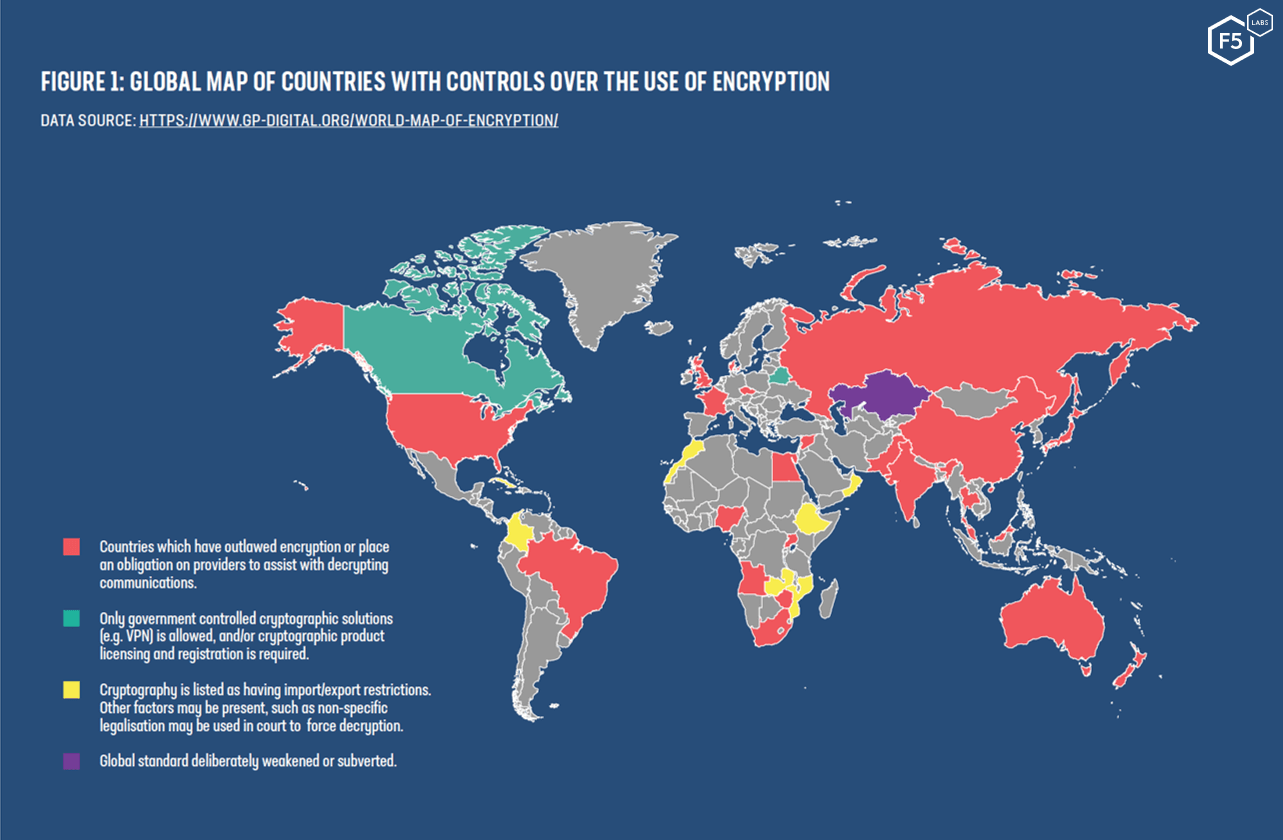
HTTPS Everywhere?
Chrome, the most widely used web browser, now fetches over 86% of web pages over secure HTTPS connections. That figure approaches 100% for Chrome OS-based devices when accessing Google properties like Gmail. For Firefox, HTTPS page loads are slightly lower but still at an impressive 80.5% average. Of the Alexa top 1 million sites, almost a third now accept TLS 1.3 connections.
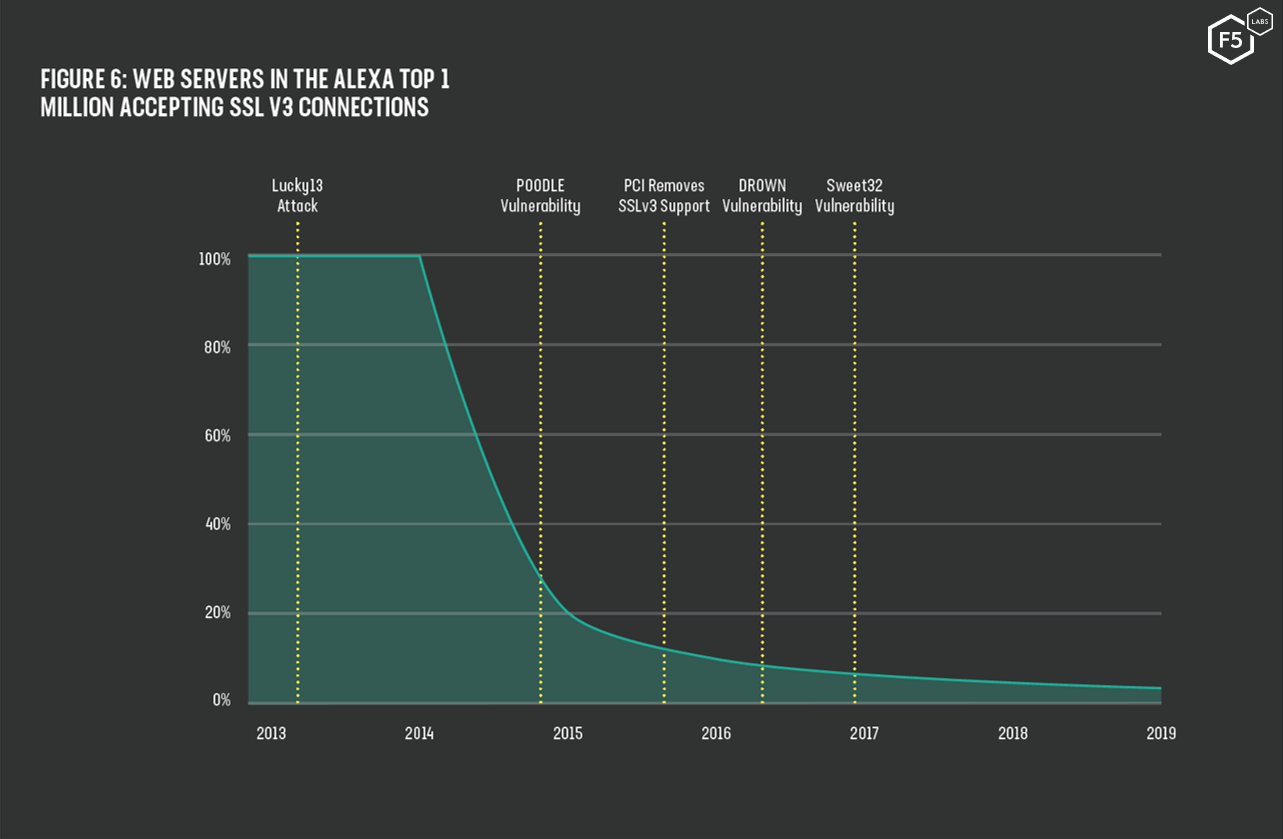
In 2014, 98% of the web servers accepting HTTPS connections still allowed the use of SSL v3. This changed rapidly in October 2014 when the POODLE vulnerability was announced.
At the end of 2019 F5 Labs joined the GitHub Security Lab coalition and as part of our new TLS Telemetry report. As part of the Security Lab coalition, we asked GitHub to help us investigate the use of OpenSSL in open-source applications. They used their LGTM code analysis tool to examine the use of the world’s most popular TLS library in 9,435 open source projects. They found that less than 1% of analyzed projects were using OpenSSL recommended methods to validate hostnames.
We also compared the malicious use of encryption to the wider web and found that domains that serve malware used a combination of legitimate public web services (such as blogging platforms and redirectors), valid certificates on malicious domains, and subtle tricks to conceal the true identity of the website. Phishing sites, used to lure victims into giving away their credentials, were even worse. The majority used HTTPS to hide traffic and appear genuine, and many sites attempted to imitate common financial institutions or e-commerce retailers.

Encryption standards are constantly evolving, so it’s crucial to stay up to date with current best practices. We hope you find this summary of the 2019 F5 Labs TLS Telemetry Report helpful and illuminating.


