Introduction
In part one of this two-part series, we describe (for non-programmers) what APIs are and why it’s important to understand the role they play as building blocks of modern applications. In part two, we discuss the security implications of APIs and how to protect them.
Many of us have heard the term application programming interface (API) but unless we’re application developers, we might not be entirely sure what an API is. The meaning isn’t obvious or intuitive, and the abundance of murky and deep-dive explanations offered online shed little light. We could simply say, “an API provides the means for one program to access the information and capabilities of another,” but even that could benefit from some context. So, let’s start by illustrating the concept using a completely non-technical example.
API-Like Behavior in Everyday Life
Suppose you get in a car accident and need to have your car repaired. You find a reputable repair shop and work with a service representative to discuss the work that needs to be done, answer your questions, get an estimate, and schedule an appointment. It’s not up to you to hire a mechanic, order parts, provide the necessary shop tools and equipment, run diagnostics tests, and so on. If the windshield needs to be replaced, the body needs to be repainted, or the wheels need to be realigned, your service rep will also arrange for those outside services to be performed.
You can think of the service rep as the interface between you and the shop—the messenger and interpreter who handles your request for services and, at the same time, spares you from having to know about all the behind-the-scenes details and complexities involved in repairing your car (see Figure 1). The service rep works on your behalf to take your request, interpret or translate it correctly, arrange for all the services required to fulfill your request, and eventually respond to you by returning your car in working condition. The important terms and concepts to pay attention to in this scenario are the interface as messenger and interpreter/translator, the request-response process, and the notion of shielding you, the requester, from the details of how repairs are made. These concepts are all central to how APIs work.
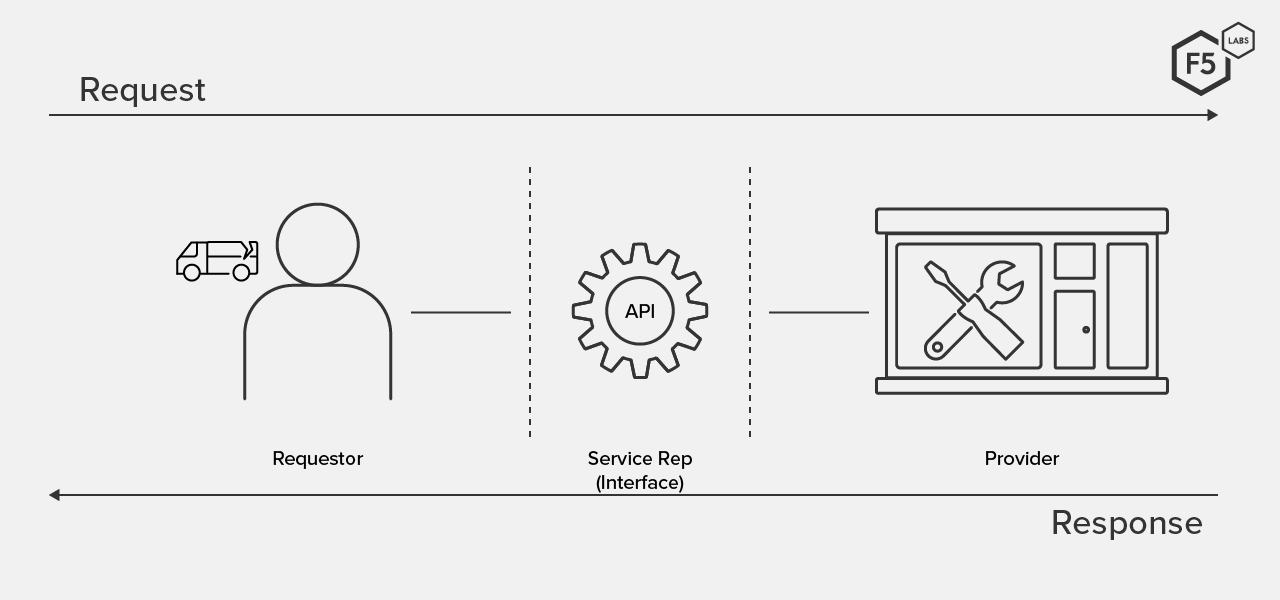
Figure 1. An interface between requestor and responder is both messenger and interpreter.
APIs in Programming
No analogy is perfect, but a similar service model can be applied to programming. Let’s apply our earlier statement—an API enables one program to access the data and services of another—to a travel app. It provides a wealth of up-to-date information about flights, hotels, cruises, ground transportation, tours, and more, but the company that makes the travel app doesn’t have this breadth of information stored in its own databases. As shown in Figure 2, the app developers request or “call” this data and functionality (services) into the app using APIs made available to them by participating vendors (hotels, airlines, cruise lines, etc.). This is similar to the way your auto repair service rep coordinates the range of services that are required to repair your car.
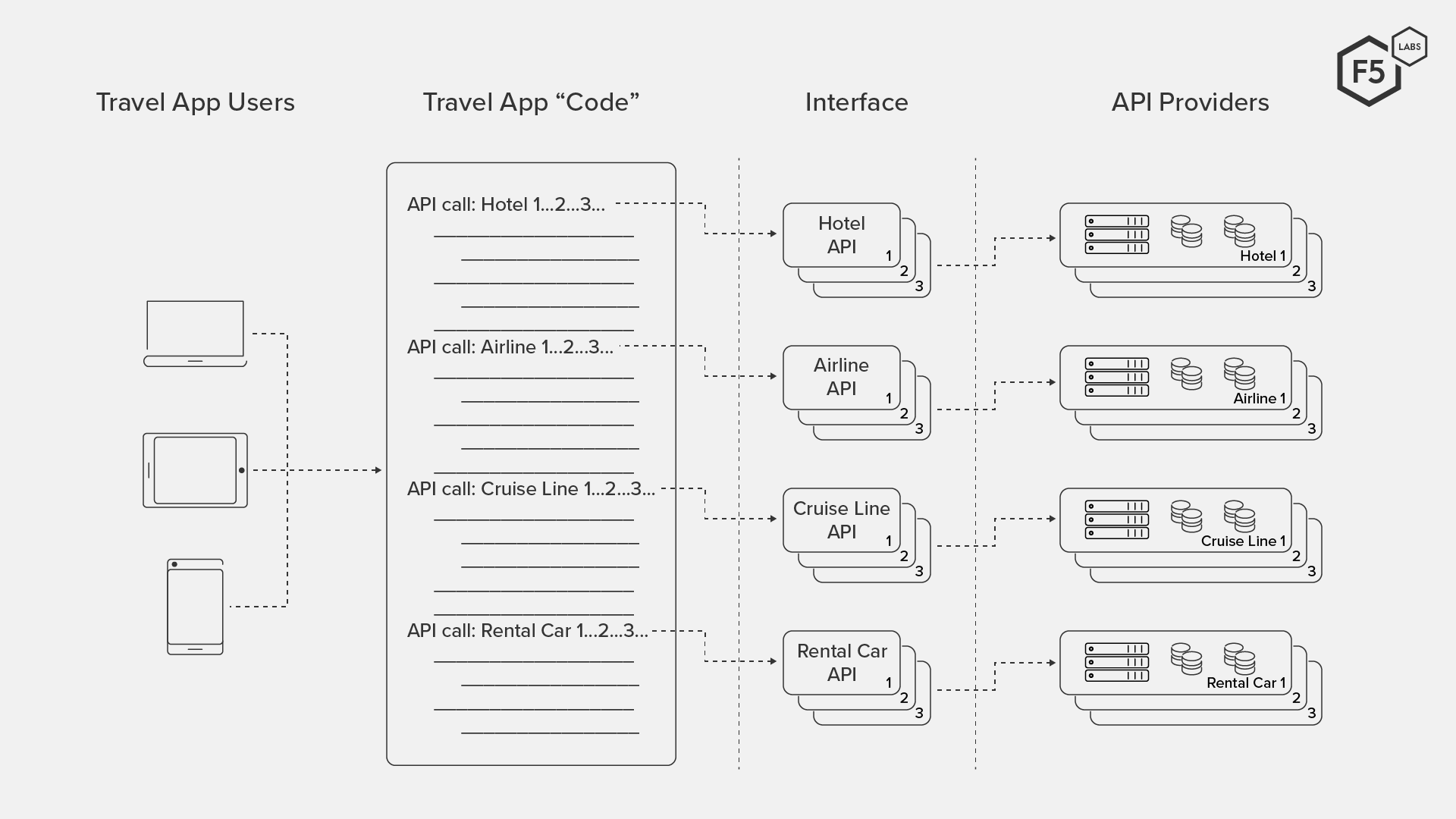
Figure 2. App developers include API calls in their app code to access third-party data and services.
Both the car repair and travel app scenarios begin with the concept of request and response. Someone or something requests a service, and fulfillment only occurs in response to a request. The facilitator of the request is the interface; it is not just a messenger but also an interpreter. Few of us speak “the language of auto repair” when we take our cars in for service, so we rely on the service rep to interpret and know how to communicate what’s needed to whomever provides the service.
The same is true in programming. APIs are the tools developers use to request data and services from outside sources, such as the hotels and airlines noted in our travel app. The API, as an interface, describes the service that’s available and defines the rules by which a service request must be made. This is what enables, for example, a program written in one language to receive and use data from an app written in different language. (Note that the API itself is not the service or data being provided; it’s the interface to it.)
Another important concept: the requester doesn’t need to understand the details of how a request is fulfilled. Instead, the developer only needs to know how to request a service in the proper way. In programming, this concept of “hiding” the complexities and technical details of the implementation is known as abstraction.
Finally, each service provided through an API stands alone and is independent of others (although they may interact with one another). This gives the API provider the flexibility to change the way a service is implemented; the rules for requesting a service stay constant, and other services remain unaffected. This is particularly significant in app development because it means that developers don’t need to continually update their programs when the “backend” implementation of an API changes; the service itself still works if the API stays constant.
Why Do APIs Exist?
As our travel app example illustrates, the benefits of APIs to the consumer are fairly obvious. But APIs aren’t primarily about consumers. APIs exist for and benefit enterprises and developers.
Why Enterprises Create APIs
APIs aren’t a new concept; they’ve been around at an operating system level since before the personal computer. Developers use private APIs within a company to share data and integrate systems internally, and enterprises share so-called partner APIs only with their strategic business partners. In 2000, Salesforce pioneered the idea of making web APIs publicly available; eBay, Amazon, and social media sites quickly followed suit. In doing so, they opened the doors to third-party integration of their data and services across a range of platforms and devices. (Note: Although there are many types of APIs, this article focuses on "web" APIs, which can be implemented in different ways, the most common being RESTREST (Representational State Transfer) APIs are commonly used in modern apps because they support HTTP and HTTPS, TLS encryption, and JSON, a file format designed for easy exchange of data., RPC and gRPCgRPC (gRPC Remote Procedure Call) APIs are gaining in popularity due to their support of multiple languages and their small data (payload) size, which leads to faster performance., and SOAPSOAP (Simple Object Access Protocol) APIs predate REST APIs, are based on international standards, and are sometimes considered more secure than other API implementations, so they're often used for apps that share sensitive data..)
Today, virtually every company, large or small, makes some APIs publicly available in order to stay relevant and competitive in today’s digital economy. The ubiquitous use of smartphones, wearables, and Internet of Things (IoT) devices is a huge driving force behind public APIs. As consumers become increasingly dependent on these devices, demand real-time services, and expect more functionality from their apps, providers make more of their data and services available to app developers through APIs. Two widely recognized APIs are Google maps, used by virtually any website that wants to provide directions to their location, and The Weather Channel, which Apple uses in its iPhone Weather app.
Let’s be candid, though: making APIs publicly available isn’t a purely benevolent gesture on the part of providers. While some organizations provide APIs free of charge, most recognize that APIs represent a new and, in some cases, astoundingly profitable revenue stream, not to mention a boost to their brand recognition. In 2015, it’s estimated that 90% of Expedia’s, 60% of eBay’s, and 50% of Salesforce’s revenues were generated by APIs.1
Why App Developers Use APIs
APIs have unquestionably changed the way developers write applications. Gone are the days of writing monolithic, million-line, so-called spaghetti-code applications that are difficult to manage and maintain. With APIs, developers can write far less code from scratch and instead, pull much of the data and services they want into their apps from outside sources. Because they don’t need to worry about the details of how a capability is implemented, they’re able to focus more on developing innovative, feature-rich apps. They can do it far more quickly and get apps to market faster. And because the apps are essentially a collection of independent components, they can also rapidly adapt apps to consumers’ ever-changing needs and desires. If a feature proves to be unpopular with users or doesn’t work quite right, developers can replace it or pull it entirely from the app without affecting other components.
The Significance of APIs to Security
Given all of these benefits, it’s easy to see how APIs have become the building blocks of modern applications. But whether you’re a consumer or creator of public APIs (or both), care must be taken. The flipside to these benefits is that, by their very nature, APIs expose data to outsiders. The “responder” behind every API is the provider’s web server and/or database. This makes an organization’s APIs extremely attractive to attackers, not just for the data the APIs provide, but as potential entry points to other backend systems within an organization’s infrastructure. If proper precautions and security controls are not in place, APIs can pose a serious risk to organizations. In part two of this article series, we’ll look at the ways APIs are most commonly compromised and what you can do to protect them.


