
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
Welcome to this month's installment of the Sensor Intel Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data, looking at data from November of 2024.
CVE-2023-1389, an RCE vulnerability in TP-Link Archer AX21 consumer routers, which has been consistently towards the top of our ranking, continues for a fourth month to be the most scanned for CVE that we track, albeit continuing its trend of slowly falling off in terms of volume. CVE-2020-8958, a command injection vulnerability in Guanzhou home networking equipment, comes in second, with a moderately large increase in scanning compared with last month.
BotPoke Scanner Switches IP Addresses, Yet Again
We’ve continued to track a pattern of scanning associated with the BotPoke scanner that first appeared in August. We also noted that in October, the IP address associated with the scanning had changed, from one in Lithuania to one from Hong Kong.
We find it has changed again, to 154.213.184.3, an IP hosted out of the Netherlands. Interestingly, this IP has, unlike the previously noted addresses, a terrible IP Reputation, being listed on both the Spamhaus Exploits Blocklist, and the more generic Spamhaus Blocklist.
The pattern of scanning remains the same, looking for a vast collection of filenames associated with malware.
Unlike previous months, however, this single IP is not our top talker, either singly or in aggregate!
New Top Talkers
Displacing BotPoke from the top spot in terms of volume of scanning, we instead now see the top two places taken by 75.119.158.141 and 109.205.183.151. Digging into their traffic a bit more, we can see that they are part of a cluster of IPs that are scanning for similar URIs, mostly related to php and credential related information exposures.
In fact, when we zoom out we find that seven out of our top ten talkers exhibit this scanning pattern and account for 45.9% of our total traffic. The one remaining (after we remove the BotPoke IP) is 194.28.84.86, an IP in Kiev, Ukraine, which is scanning exclusively for “/”, and exclusively against one sensor we have in that country. This may seem odd, or even exciting, but further investigation shows the User-Agent is consistently “Accept=['*/*'] connection=['close'] user_agent=['check_http/v2.4.5 (nagios-plugins 2.4.5)']” which would indicate that this is a misconfigured instance of the Nagios monitoring tool, which has been set to check the health of our sensor IP. 194.28.84.86 is an IP owned by “hostpro.com.ua”. We don’t have much more to say about it, other than to recommend they upgrade their version of the Nagios plugins, the current version being 2.4.9.
November Vulnerabilities by the Numbers
Figure 1 shows November traffic for the top ten CVEs that we track. CVE-2023-1389 is dominating this visualization, with much more traffic than any of the other top 10. The massive amount of scanning for this vulnerability throws off the proportionality of this view, however. See further down for an easier to understand view using a logarithmic scale in Figure 3.
Targeting Trends
Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. We can see quite clearly the still heavy scanning for CVE-2023-1389, albeit slowly decreasing. We can also observe the fall off in scanning for CVE-2020-11625, and the increase in scanning for CVE-2020-8958.
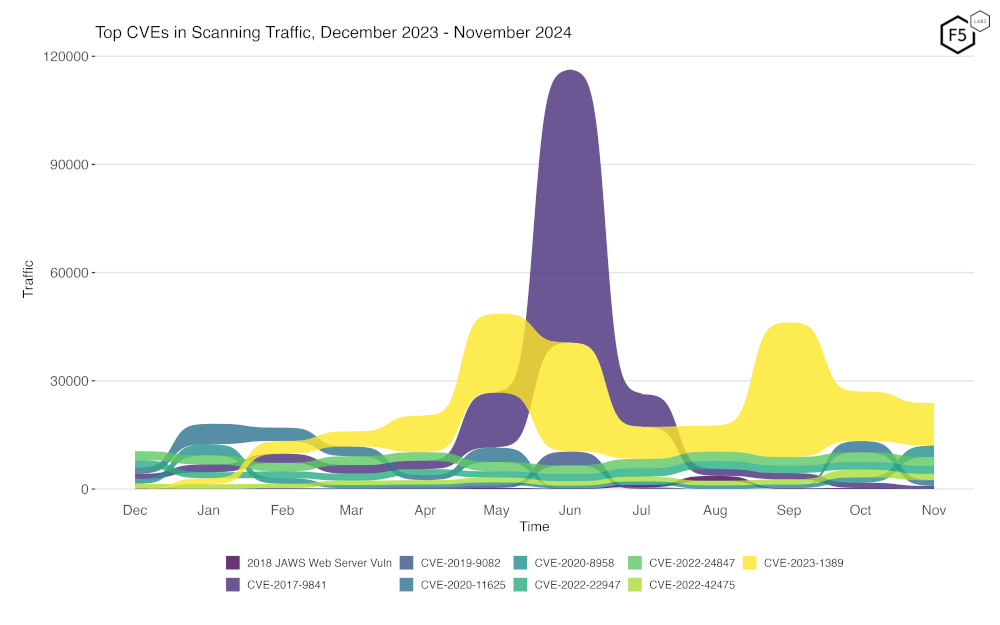
Figure 2: Evolution of vulnerability targeting in the last twelve months. Note the continued high level of scanning for CVE-2023-1389, and the emergence in scanning for CVE-2020-8958.
Long Term Trends
Figure 3 shows traffic for the top 20 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs.
Quite obvious now that a month has passed is the sudden re-emergence of scanning for CVE-2020-11625. On the leftmost cell of the second row, we can see the uptick in scanning for CVE-2020-8958 quite clearly as well. Perhaps of note is the small increase of scanning for CVE-2018-10561, which has increased approximately ten-fold in the last 12 months. We’ll be keeping an eye on that going forward.
In the lower right corner, you can see the average of all the other 110 CVEs we currently track and note that these show an overall reduction in scanning since last month. This would seem to imply many of the previously observed CVEs we track hitting the end of their long tail and finding their way to zero.
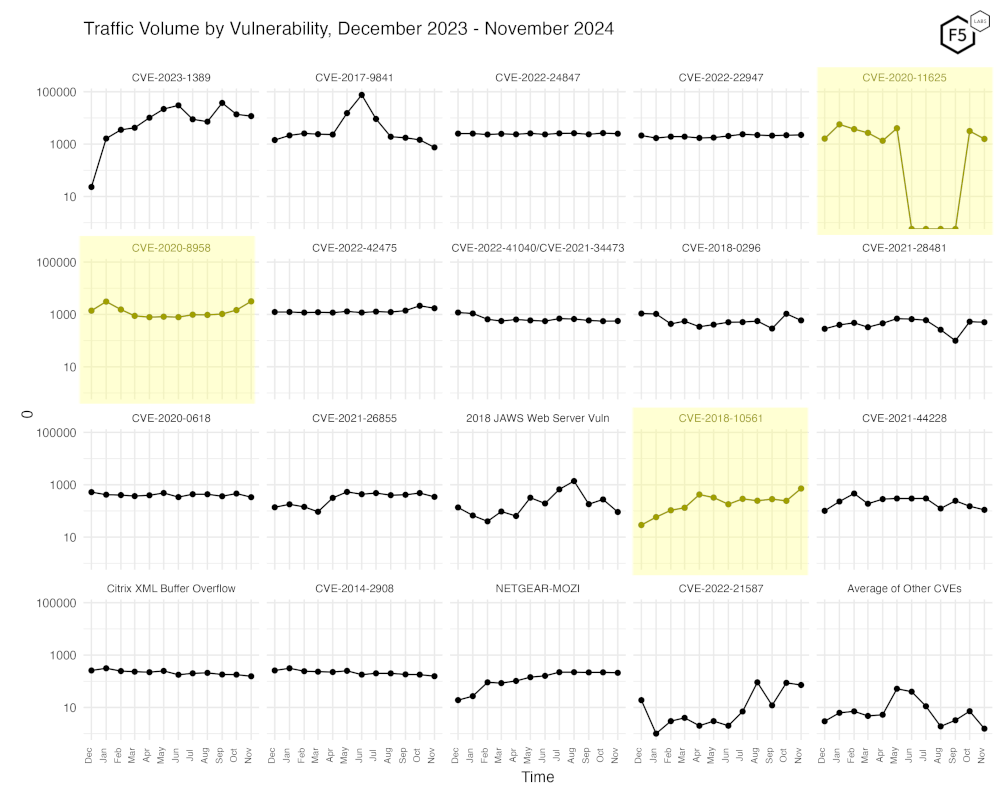
Figure 3. Traffic volume by vulnerability. This view accentuates the recent changes in CVE-2020-11625 and CVE-2020-8958.
Conclusions
While our tracking of BotPoke scanning has been interesting, it is no longer dominating our data and we’ve been able to expand our analysis into grouping different scanning IPs that share similar scanning characteristics. That only 8 of our top 10 IPs account for nearly half our traffic is perhaps not surprising, but that those IPs are all scanning for the same set of URLs, with the implication perhaps that they are being operated by the same actor, deserves more attention.
See you next month, for a year end round up!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


