F5 Labs, in conjunction with our partner Baffin Bay Networks, researched attacks by geographic region to get a better understanding of the threat landscape region to region. We sought to understand if the global attack landscape was consistent or if it differed region to region, and to identify consistencies in attacking networks, IP addresses, and targeted ports. In this research series we looked at attacks over the same 90-day period in Europe, the United States (US), Canada, and Australia. The US and Canada were originally slated to be combined in a North American regional view, however, because Canada’s attack profile was similar to Europe’s and Australia’s, we separated the countries.
This article covers attack traffic destined for US IP addresses from December 1, 2018 through March 1, 2019, and how it compares to the other regions.
- Systems with IP addresses located in Vietnam launched the most attacks against systems in the United States. Attacks from China, then Russia followed in the number 2 and number 3 positions.
- The top attacking networks were VNPT Corp (Vietnam), PT Telekomunikasi (Indonesia), and Chinanet (China).
- The majority of networks attacking US systems were not seen attacking Canadian, European, or Australian networks during the same period. The consistency in attacks across all regions came from state-sponsored networks in China.
- 76% of the top 50 attacking IP addresses are Chinese, helping put China in the number two attacking position. Comparatively, there was only one Vietnamese IP address and no Russian IP addresses in the top 50 attacking IP addresses list yet both countries were in the top 3 attacking counties list. This indicates threat actors using systems in Vietnam and Russia are launching a small amount of attacks from lots of systems in an effort to fly under the radar.
- The top targeted ports in the US were Microsoft SMB (Samba)—10 times more than SSH in the number 2 position, and 290 times more than HTTP in the number three position.
Top Attacking Countries
Systems in Vietnam were the number one source of attack traffic directed towards US systems from December 1, 2018 through March 1, 2019. China and Russia were in the number two and number three positions respectively. Vietnam is not usually the top source IP country when looking at attacks against the US; this was an anomaly in this time period. China and Russia, however, are consistently the top sources of attack traffic directed towards the US.
In comparison, the US was either the number one or number two top attacking country when looking at attacks destined for Canada, European countries, or Australia, but is not within the top 5 source countries of attacks against itself. The Netherlands and France are also top attacking countries targeting Canada, Europe, and Australia, but were not seen attacking the US in this period. Additionally, Vietnam (in the number one attacking position) and Indonesia (in the number 5 attacking position), were not in the top 25 attacking countries lists for Canada, Europe, and Australia. Because Canada’s threat landscape is similar to Europe and Australia and not the US, were reporting on Canada and the US separately.
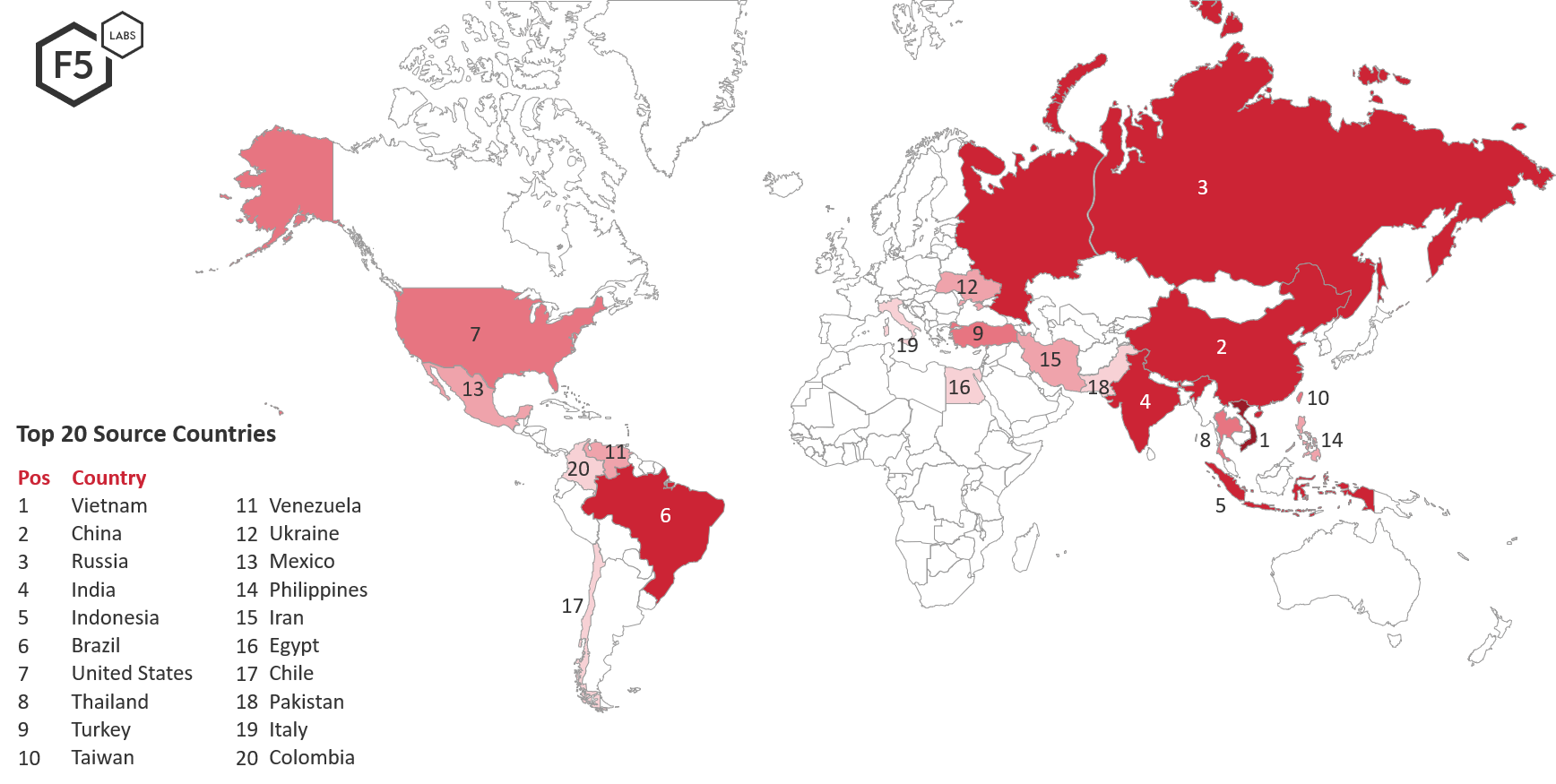
Figure 1: Source countries of attacks targeting the United States December 1, 2018 through March 1, 2019
Systems in Vietnam launched 1.4 times more attacks against systems in the US than China and Russia did from Dec 1, 2018 through March 1, 2019.
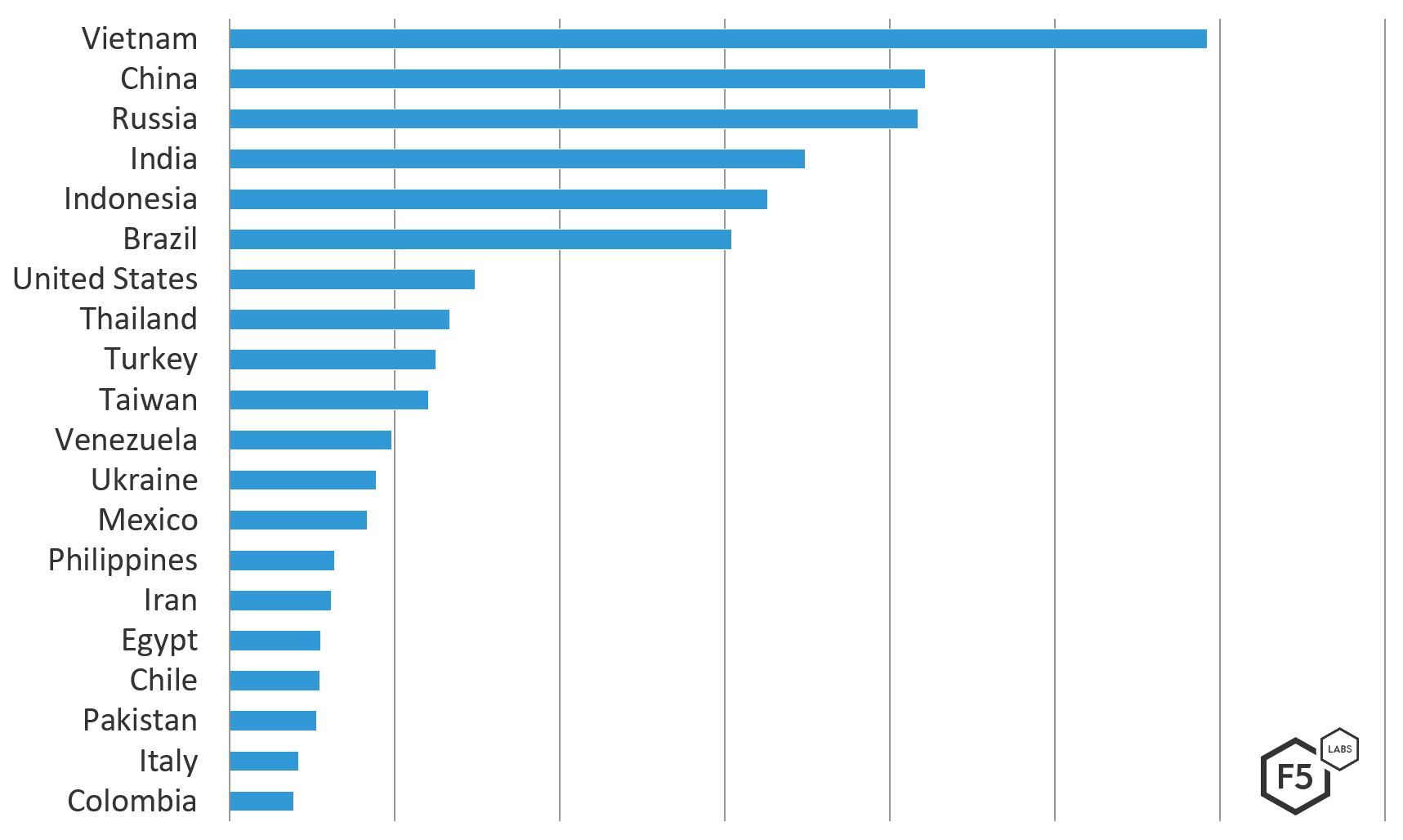
Figure 2: Top countries targeting US by count
Top Attacking Organizations (ASNs)
The Vietnamize-based hosting network VNPT Corp. (ASN 45899) launched the largest number of attacks destined for US IP addresses, followed by the Indonesian ISP PT Telekomunikasi (ASN 17974), and Chinanet (ASN 4134), a state sponsored ISP routinely on top of ASN attacker lists. Chinanet was also seen attacking IP addresses in Canada (eleventh position) and Europe (sixth position) and Australia (second position) in the same time period.
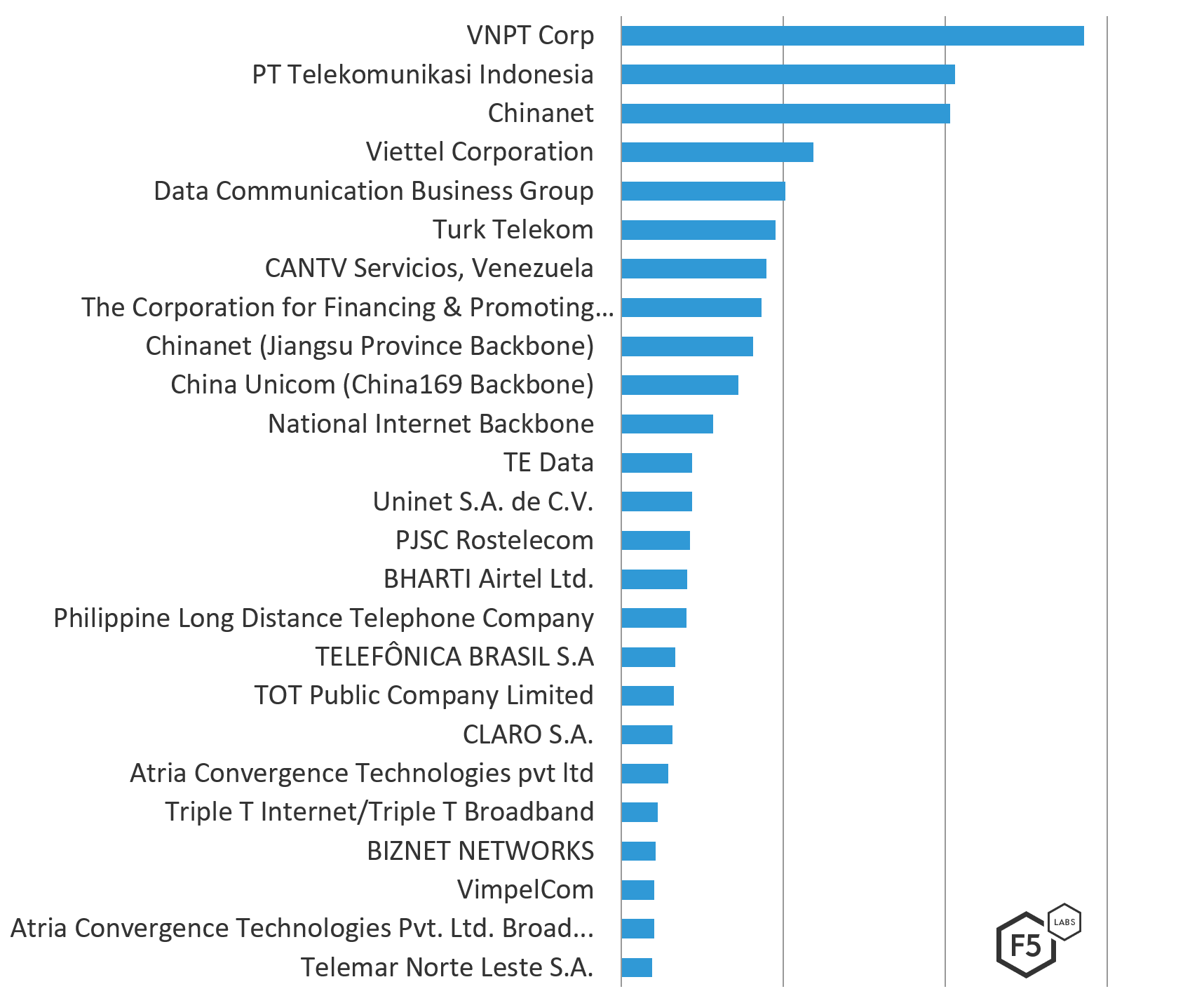
Figure 3: Top 25 Attacking ASNs by attack count
The table in Figure 4 shows the top 50 ASNs attacking US systems from Dec 1, 2018 to March 1, 2019 in order of highest to lowest number of attacks, the majority of which were ISPs. Interestingly, there are more ASNs on this list from India then any other country, followed by Russia. Three of the seven Russian ASNs are mobile phone service providers.
| ASN | ASN Organization | Country | Industry |
| 45899 | VNPT Corp | Vietnam | Hosting |
| 17974 | PT Telekomunikasi Indonesia | Indonesia | ISP |
| 4134 | Chinanet | China | ISP |
| 7552 | Viettel Corporation | Vietnam | ISP |
| 3462 | Data Communication Business Group | Taiwan | ISP |
| 9121 | Turk Telekom | Turkey | ISP |
| 8048 | CANTV Servicios, Venezuela | Venezuela | ISP |
| 18403 | The Corporation for Financing & Promoting Tech... | Vietnam | ISP |
| 23650 | Chinanet (Jiangsu Province Backbone) | China | ISP |
| 4837 | China Unicom (China169 Backbone) | China | ISP |
| 9829 | National Internet Backbone | India | ISP |
| 8452 | TE Data | Norway | ISP |
| 8151 | Uninet S.A. de C.V. | Mexico | ISP |
| 12389 | PJSC Rostelecom | Russia | ISP |
| 9498 | BHARTI Airtel Ltd. | India | Hosting |
| 9299 | Philippine Long Distance Telephone Company | Philippines | ISP |
| 18881 | TELEFÔNICA BRASIL S.A | Brazil | ISP |
| 23969 | TOT Public Company Limited | Thailand | ISP |
| 4230 | CLARO S.A. | Brazil | ISP |
| 55577 | Atria Convergence Technologies pvt ltd | India | ISP |
| 45758 | Triple T Internet/Triple T Broadband | Thailand | ISP |
| 17451 | BIZNET NETWORKS | Indonesia | Hosting |
| 8402 | VimpelCom | Netherlands | ISP |
| 24309 | Atria Convergence Technologies Pvt. Ltd. Broad... | India | ISP |
| 7738 | Telemar Norte Leste S.A. | Brazil | ISP |
| 45820 | Tata Teleservices ISP AS | India | ISP |
| 4755 | TATA Communications formerly VSNL is Leading ISP | India | ISP |
| 9198 | JSC Kazakhtelecom | Kazakhstan | ISP |
| 25019 | Saudi Telecom Company JSC | Saudi Arabia | ISP |
| 24757 | Ethiopian Telecommunication Corporation | Ethiopia | ISP |
| 24560 | Bharti Airtel Ltd., Telemedia Services | India | Hosting |
| 131090 | CAT TELECOM Public Company Ltd | Thailand | ISP |
| 12880 | Information Technology Company (ITC) | Iran | ISP |
| 4812 | China Telecom (Group) | China | ISP |
| 3269 | Telecom Italia | Italy | ISP |
| 5384 | Emirates Telecommunications Corporation | UAE | ISP |
| 45458 | SBN-ISP/AWN-ISP and SBN-NIX/AWN-NIX | Thailand | ISP (Mobile) |
| 6429 | Telmex Chile Internet S.A. | Chile | ISP |
| 3216 | PVimpelCom | Netherlands | ISP |
| 8732 | OJSC Comcor | Russia | ISP |
| 16735 | ALGAR TELECOM S/A | Brazil | ISP |
| 34984 | Tellcom Iletisim Hizmetleri A.s. | Turkey | ISP |
| 24955 | OJSC Ufanet | Russia | ISP |
| 25513 | OJS Moscow city telephone network | Russia | ISP (Mobile) |
| 12714 | Net By Net Holding LLC | Russia | ISP |
| 17762 | Tata Teleservices Maharashtra Ltd | India | ISP |
| 14259 | Gtd Internet S.A. | Chile | Hosting |
| 3549 | Level 3 Communications, Inc. | United States | ISP |
| 31163 | PJSC MegaFon | Russia | ISP (Mobile) |
| 8359 | MTS PJSC | Russia | ISP (Mobile) |
Figure 4: Top 50 ASNs attacking US systems
The following four Chinese and one Taiwan network were in the top 50 attacking ASNs list across all regions from December 1, 2018 to March 1, 2019.
| ASN | ASOrg | Country | Industry |
| 4812 | China Telecom (Group) | China | ISP |
| 4837 | China Unicom (China169 Backbone) | China | ISP |
| 4134 | Chinanet | China | ISP |
| 23650 | Chinanet (Jiangsu Province Backbone) | China | ISP |
| 3462 | Data Communication Business Group | Taiwan | ISP |
Figure 5: Networks consistently attacking all regions of the world December 1, 2018 to March 1, 2019
The US shared 10 top attacking ASNs with Europe, and 8 top attacking ASNs with both Europe and Australia in the same time period. The US did not share any top attacking ASNs with Canada in the same time period except for the Chinese and Taiwan networks listed in Figure 5 above that attacked all regions. The following 27 networks uniquely targeted systems in the US. A quarter of them are Russian ISPs, several of which only offer mobile services.
| ASN | ASOrg | Country | Industry |
| 16735 | ALGAR TELECOM S/A | Brazil | ISP |
| 24560 | Bharti Airtel Ltd., Telemedia Services | India | Hosting |
| 17451 | BIZNET NETWORKS | Indonesia | Hosting |
| 131090 | CAT TELECOM Public Company Ltd | Thailand | ISP |
| 5384 | Emirates Telecommunications Corporation | UAE | ISP |
| 24757 | Ethiopian Telecommunication Corporation | Ethopia | ISP |
| 14259 | Gtd Internet S.A. | Chile | Hosting |
| 9198 | JSC Kazakhtelecom | Kazakhstan | ISP |
| 3549 | Level 3 Communications, Inc. | United States | ISP |
| 8359 | MTS PJSC | Russia | ISP (Mobile) |
| 12714 | Net By Net Holding LLC | Russia | ISP |
| 25513 | OJS Moscow city telephone network | Russia | ISP (Mobile) |
| 8732 | OJSC Comcor | Russia | ISP |
| 24955 | OJSC Ufanet | Russia | ISP |
| 31163 | PJSC MegaFon | Russia | ISP (Mobile) |
| 3216 | PVimpelCom | Netherlands | ISP |
| 25019 | Saudi Telecom Company JSC | Saudia Arabia | ISP |
| 45458 | SBN-ISP/AWN-ISP and SBN-NIX/AWN-NIX | Thailand | ISP (Mobile) |
| 4755 | TATA Communications formerly VSNL is Leading ISP | India | ISP |
| 45820 | Tata Teleservices ISP AS | India | ISP |
| 17762 | Tata Teleservices Maharashtra Ltd | India | ISP |
| 3269 | Telecom Italia | Italy | ISP |
| 7738 | Telemar Norte Leste S.A. | Brazil | ISP |
| 34984 | Tellcom Iletisim Hizmetleri A.s. | Turkey | ISP |
| 6429 | Telmex Chile Internet S.A. | Chile | ISP |
| 45758 | Triple T Internet/Triple T Broadband | Thailand | ISP |
| 8402 | VimpelCom | Netherlands | ISP |
Figure 6: Networks targeting US systems not seen targeting other regions
Top Attacking IP Addresses
Unlike the consistency seen between networks attacking US, Canadian, European, and Australian systems, there is not consistency in the IP addresses used in those networks to attack. Only one IP address on the top 50 attacking IP addresses for the US was seen in other regional top attacking IP address lists. That address, 58.242.83.26, was seen attacking Australia in the same period and resolves to the Chinese ISP China Unicom.
Using the same networks to attack, but not the same IP addresses, can indicate that attackers are targeting specific networks they know they can successfully launch attacks from. The same Chinese networks have been consistently top attackers for decades to the point where attacks from China are accepted as the norm, and they do little to disguise them. Collectively, more attacks came from Vietnamese IP’s then any other country during this 90 day period, however there is only 1 Vietnamese IP on the top 50 list. Russia, the 3rd largest source of attacks against the US in this same time period has no IP addresses on the top 50 list. Attacks coming from Vietnam and Russia were spread out across, at a minimum, hundreds of IP addresses, launching a smaller number of attacks per address (and therefore not showing up on the top attacking IP addresses list). This is typically a deliberate effort by attackers to fly under the radar, and one that requires a considerable amount of resourcing.
The chart in Figure 7 shows the top 50 IP addresses attacking destinations in the US from December 1, 2018 through March 1, 2019 by count.
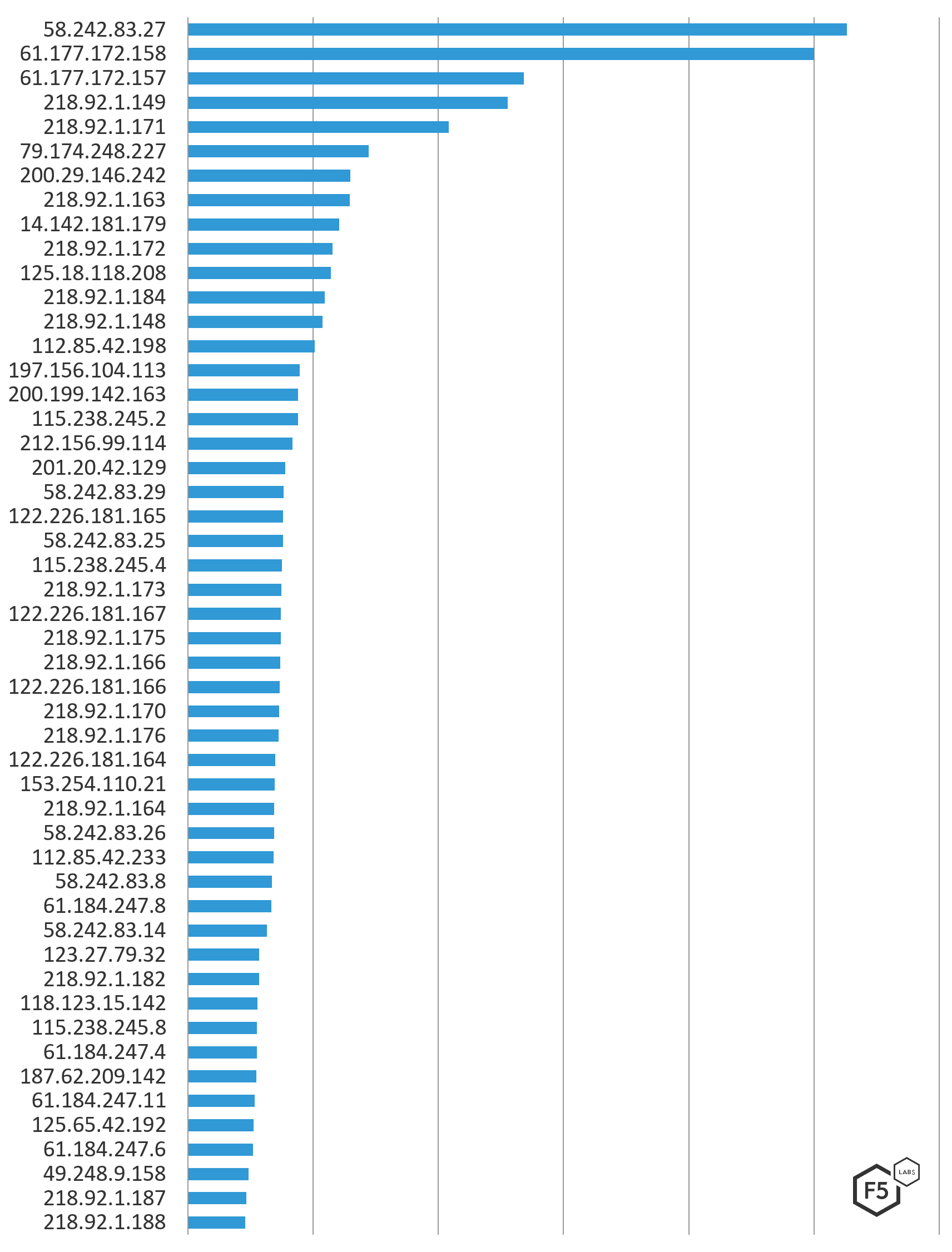
Figure 7: Top 50 IP addresses attacking US systems December 1, 2018 through March 1, 2019 by count
Figure 8 shows the top 50 IP addresses attacking systems in the US from December 1, 2018 through March 1, 2019 by ASN and country of origin.
| SourceIP | ASOrg | ISP | Country |
| 58.242.83.27 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 61.177.172.158 | Chinanet | China Telecom | China |
| 61.177.172.157 | Chinanet | China Telecom | China |
| 218.92.1.149 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 218.92.1.171 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 79.174.248.227 | Completel SAS | Completel SAS | France |
| 200.29.146.242 | Telmex Chile Internet S.A. | Telmex Servicios Empresariales S.A. | Chile |
| 218.92.1.163 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 14.142.181.179 | TATA Communications formerly VSNL is Leading ISP | Tata Communications | India |
| 218.92.1.172 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 125.18.118.208 | BHARTI Airtel Ltd. | Bharti Broadband | India |
| 218.92.1.184 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 218.92.1.148 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 112.85.42.198 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 197.156.104.113 | Ethiopian Telecommunication Corporation | Ethiopian Telecommunication Corporation | Ethiopia |
| 200.199.142.163 | Telemar Norte Leste S.A. | Oi Internet | Brazil |
| 115.238.245.2 | Chinanet | China Telecom Zhejiang | China |
| 212.156.99.114 | Turk Telekom | Turk Telekom | Turkey |
| 201.20.42.129 | EQUINIX BRASIL SP | Equinix Brazil | Brazil |
| 58.242.83.29 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 122.226.181.165 | Chinanet | China Telecom Zhejiang | China |
| 58.242.83.25 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 115.238.245.4 | Chinanet | China Telecom Zhejiang | China |
| 218.92.1.173 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 122.226.181.167 | Chinanet | China Telecom Zhejiang | China |
| 218.92.1.175 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 218.92.1.166 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 122.226.181.166 | Chinanet | China Telecom Zhejiang | China |
| 218.92.1.170 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 218.92.1.176 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 122.226.181.164 | Chinanet | China Telecom Zhejiang | China |
| 153.254.110.21 | NTT America, Inc. | NTT America | Japan |
| 218.92.1.164 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 58.242.83.26 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 112.85.42.233 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 58.242.83.8 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 61.184.247.8 | Chinanet | China Telecom | China |
| 58.242.83.14 | China Unicom (China169 Backbone) | China Unicom Liaoning | China |
| 123.27.79.32 | VNPT Corp | VDC | Vietnam |
| 218.92.1.182 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 118.123.15.142 | CHINANET SiChuan Telecom Internet Data Center | China Telecom Sichuan | China |
| 115.238.245.8 | Chinanet | China Telecom Zhejiang | China |
| 61.184.247.4 | Chinanet | China Telecom | China |
| 187.62.209.142 | Wireless Comm Services LTDA | Wireless Comm Services LTDA | Brazil |
| 61.184.247.11 | Chinanet | China Telecom | China |
| 125.65.42.192 | CHINANET SiChuan Telecom Internet Data Center | China Telecom Sichuan | China |
| 61.184.247.6 | Chinanet | China Telecom | China |
| 49.248.9.158 | Tata Teleservices Maharashtra Ltd | Tata Teleservices (Maharashtra) | India |
| 218.92.1.187 | Chinanet (Jiangsu province backbone) | China Telecom | China |
| 218.92.1.188 | Chinanet (Jiangsu province backbone) | China Telecom | China |
Figure 8: Top 50 IP addresses attacking US systems December 1, 2018 through March 1, 2019 by ASN, ISP and Location
Top Targeted Ports
Looking at the destination ports of the attacks gives us a good understanding of the types of systems the attackers are after. The top targeted port in the US attacks was Microsoft SMB 445, commonly referred to as Samba, which became popular to attack after the leaked NSA/CIA exploit in 2017. So many attacks were launched targeting Samba in the US that you can barely see the other ports targeted in Figure 9 below. The second most attacked port was SSH port 22, used for secure access to applications, followed by HTTP port 80, the web traffic standard. SSH and HTTP are typically the top attacked ports globally and indicate run-of-the-mill attacks looking for vulnerabilities in which to gain access to web applications. Such a large spike in port 445 attacks is an anomaly.
SIP port 5060 used for VoIP connectivity to phones and video conferencing systems, was a top targeted port in attacks against Canada, Europe, and Australia, but was not a top targeted port in attacks against the US in the same time period. Additionally, the Microsoft CRM port 5555 was a top attacked port in the US but not in other regions.
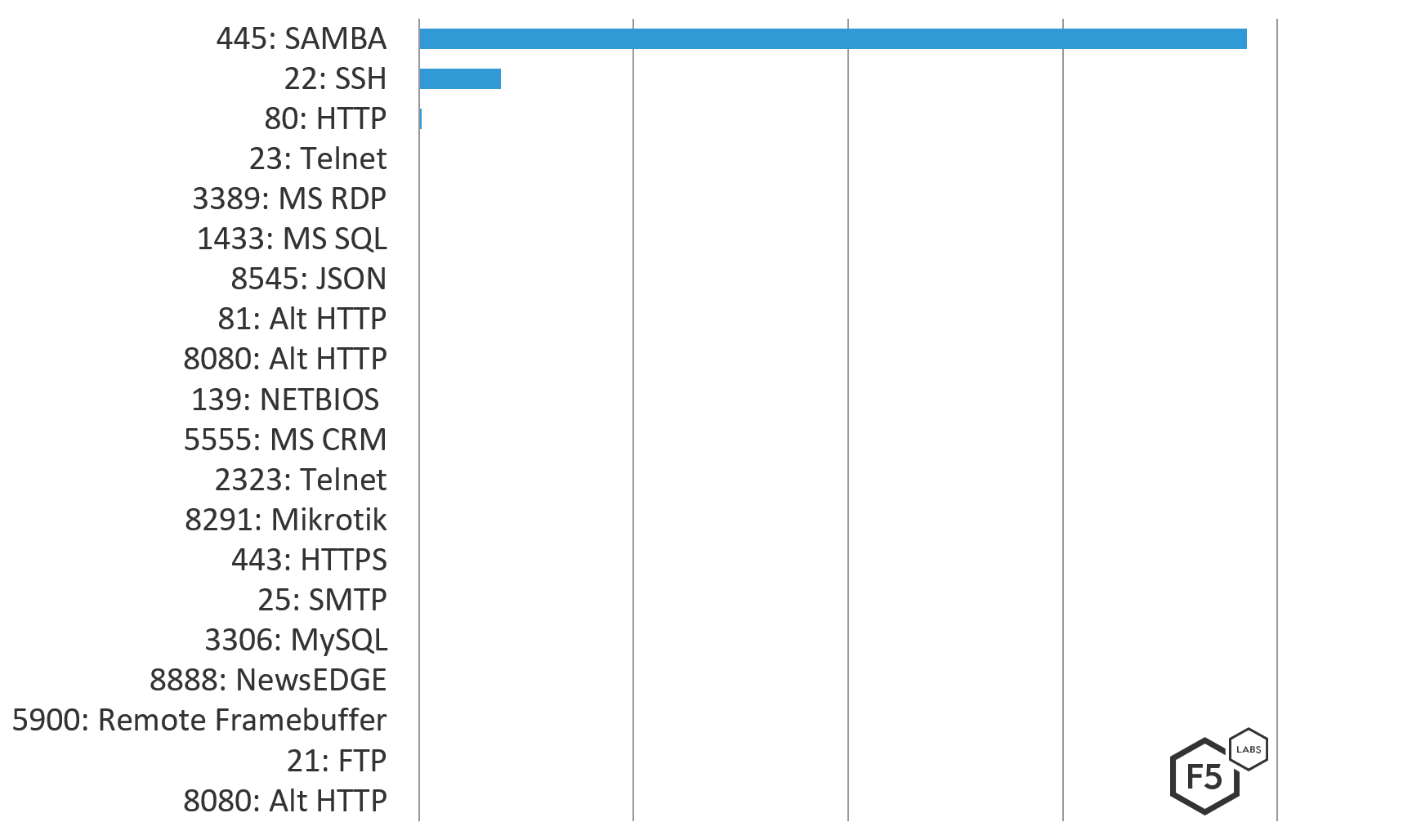
Figure 9: Top 20 targeted ports in US destination attacks December 1, 2018 through March 1, 2019
Conclusion
Organizations should continually run external vulnerability scans to discover what systems are exposed publicly, and on which specific ports. Any systems exposed publicly that have the top attacked ports open should be prioritized for either firewalling off (Microsoft Samba port 445 and SQL ports 3306 & 1433 should never be exposed publicly to the internet) or vulnerability management. Web applications taking traffic on port 80 should be protected with a web application firewall, be continually scanned for web application vulnerabilities, and prioritized for vulnerability management, including but not limited to bug fixes and patching.
A lot of the attacks we see on ports supporting access services like SSH are brute force, so any public login page should have adequate brute force protections in place. For a list of the top 100 credential pairs used in SSH brute force attacks, see the Hunt for IoT Volume 5 (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--multi-purpose-attack-thingbots-threaten-intern.html).
Network administrators and security engineers should review network logs for any connections to the top attacking IP addresses. If you are experiencing attacks from any of these top IP addresses, you should submit abuse complaints to the owners of the ASNs and ISPs so they hopefully shut down the attacking systems.
For those interested in IP blocking, it can be troublesome not only to maintain large IP blocklists, but also to block IP addresses within ISPs that offer Internet service to residences that might be customers. In these cases, the attacking system is likely to be an infected IoT device that the resident doesn’t know is infected, and it likely won’t get cleaned up. Blocking traffic from entire ASNs or an entire ISP can be problematic for the same reason—blocking their entire network would block all of their customers from doing business with you. Unless of course it’s an ISP supporting a country you don’t do business with. In that case, geolocation blocking at a country level can be effective way to reduce a large amount of attack traffic and save your systems the unnecessary processing. For this reason, it is best to drop traffic based on the attack pattern on your network and web application firewalls.
F5 Labs will continue to monitor global attacks and analyze at a regional level quarterly. Future research series will include the Asia-Pacific, the Middle East and North Africa, and Latin American regions. If you are an implicated ASN or ISP, please reach out to us at F5LabsTeam@F5.com and we’ll be happy to share further information with you.
Recommendations
- Organizations exposing commonly attacked ports publicly to the Internet, especially systems like databases that shouldn’t be accessible over the Internet, should do their best to restrict public accessibility through their firewall.
- Any commonly attacked ports that require external access, like HTTP and SSH, should be prioritized for vulnerability management.
- Access to applications over SSH should be protected with brute force restrictions.
- Vendor default credentials, commonly used in SSH brute force attacks, should be disabled on all systems before public deployment.
- Organizations should consider implementing geo IP blocking of commonly attacking countries that the business does not have a need to communicate with.


