F5 Labs, in conjunction with our partner Baffin Bay Networks, researched attacks by geographic region to get a better understanding of the threat landscape region to region. We sought to understand if the global attack landscape was consistent, or if it differed region to region, and to identify consistencies in attacking networks, IPs, and targeted ports. In this research series we looked at attacks over the same 90-day period in Europe, the United States, Canada, and Australia. The United States and Canada were originally slated to be combined to a “North American” view, however because Canada’s attack profile is similar to Europe and Australia, we separated the countries.
This article covers attack traffic destined for Canadian IP addresses from December 1, 2018 through March 1, 2019, and explores how it compares to the other regions.
- European countries were the primary source of attack traffic against Canadian systems
- OVH SAS from France launched 5.5 times more attacks against systems in Canada than Netherlands-based Host Palace Web Solutions, which was in second place.
- Four of the top 5 IP addresses targeting Canadian systems are from OVH SAS’s network.
- The top attacked port was SIP 5060, followed by Microsoft SMB, and then HTTP port 80. SIP was targeted 8.3 times more than Microsoft SMB.
Top Attacking Countries
Canadian systems receive attacks from systems all over the world, however 6 of the top 10 attacking countries between December 1, 2018 and March 1, 2019 were European. European systems have a similar threat profile such that they receive a high rate of attacks from European countries.
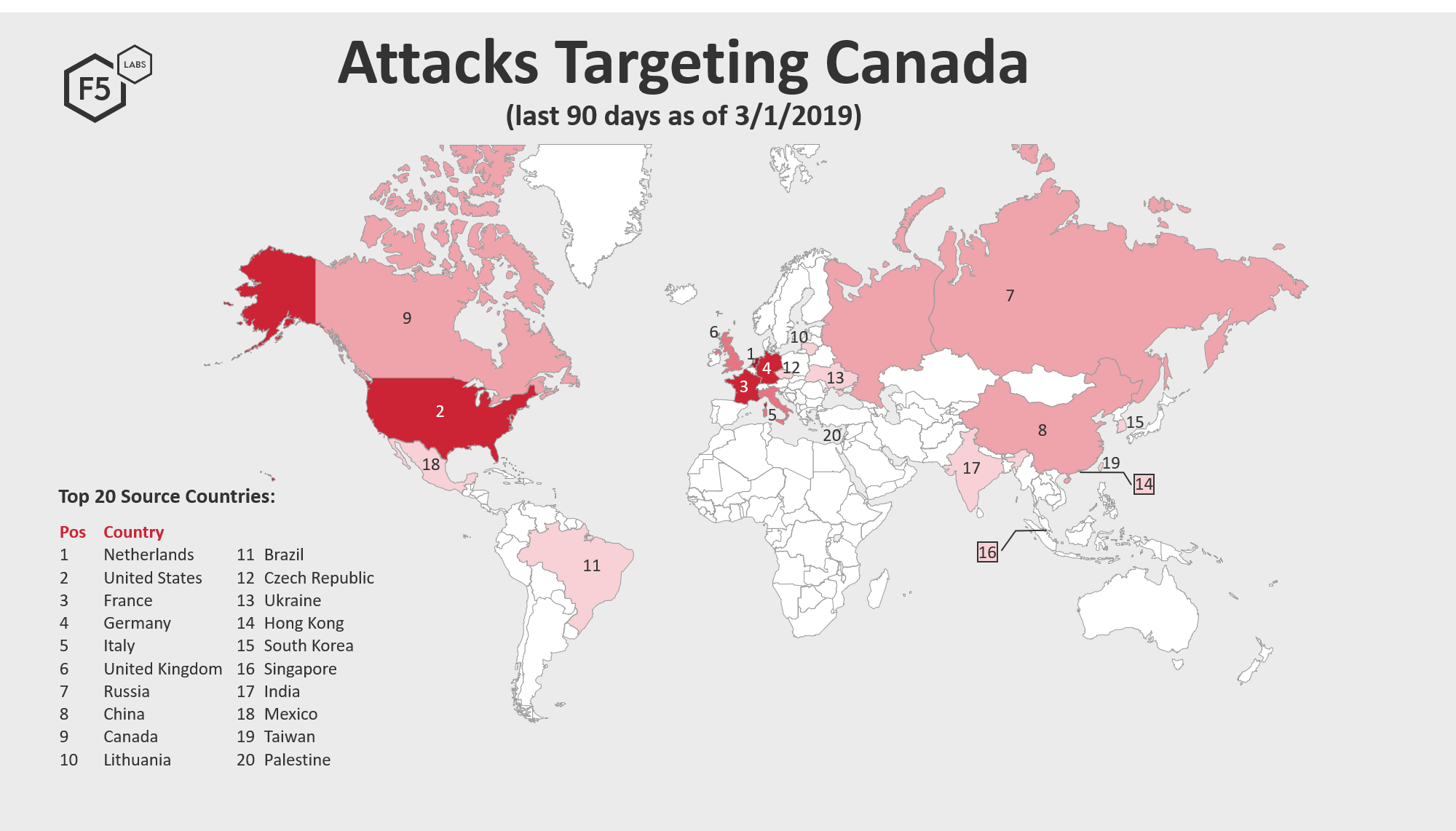
Figure 1: Source countries of attacks targeting Canada
The Netherlands was the top source traffic country launching attacks against systems in Canada from Dec 1, 2018 through March 1, 2019, followed by the United States and then France, Germany, and Italy to round out the top 5 attacking countries.
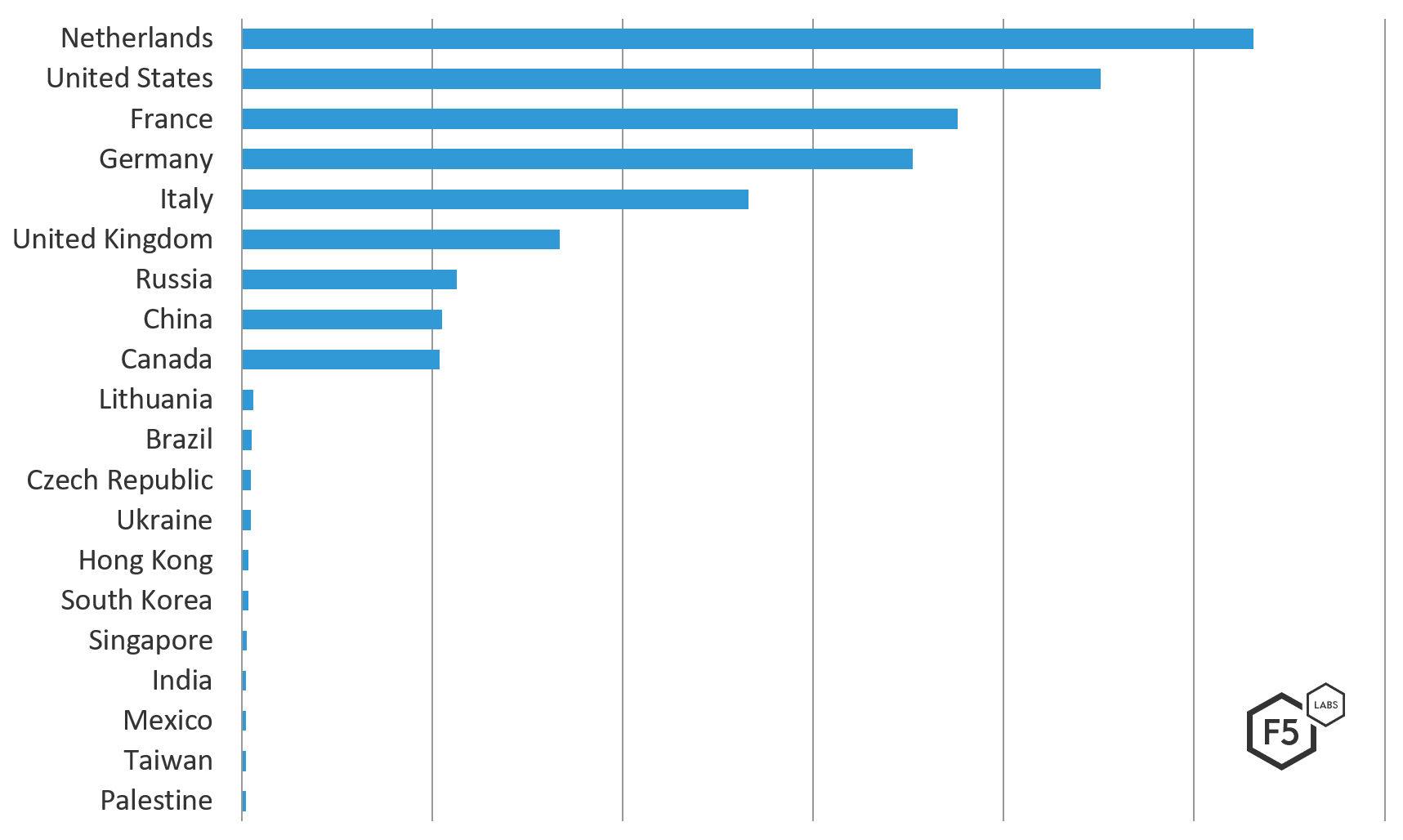
Figure 2: Top 20 countries targeting Canada (by IP location), December 1, 2018 through March 1, 2019.
Top Attacking Organizations
The top 5 networks attacking Canadian systems from December 1, 2018 to March 1, 2019 were European. The top attacking network, OVH SAS (ASN 16276), launched 5.5 times more attacks from systems in France and Germany than Host Palace Web Solutions (ASN 133229), a hosting provider from the Netherlands, which took second place. The top 4 attacking networks targeting Canadian systems in this period were the same top 4 networks attacking European systems in this period, just in a slightly different order. The fifth attacking network, Vitox Telecom from the Netherlands, was not seen attacking the other regions in this period.
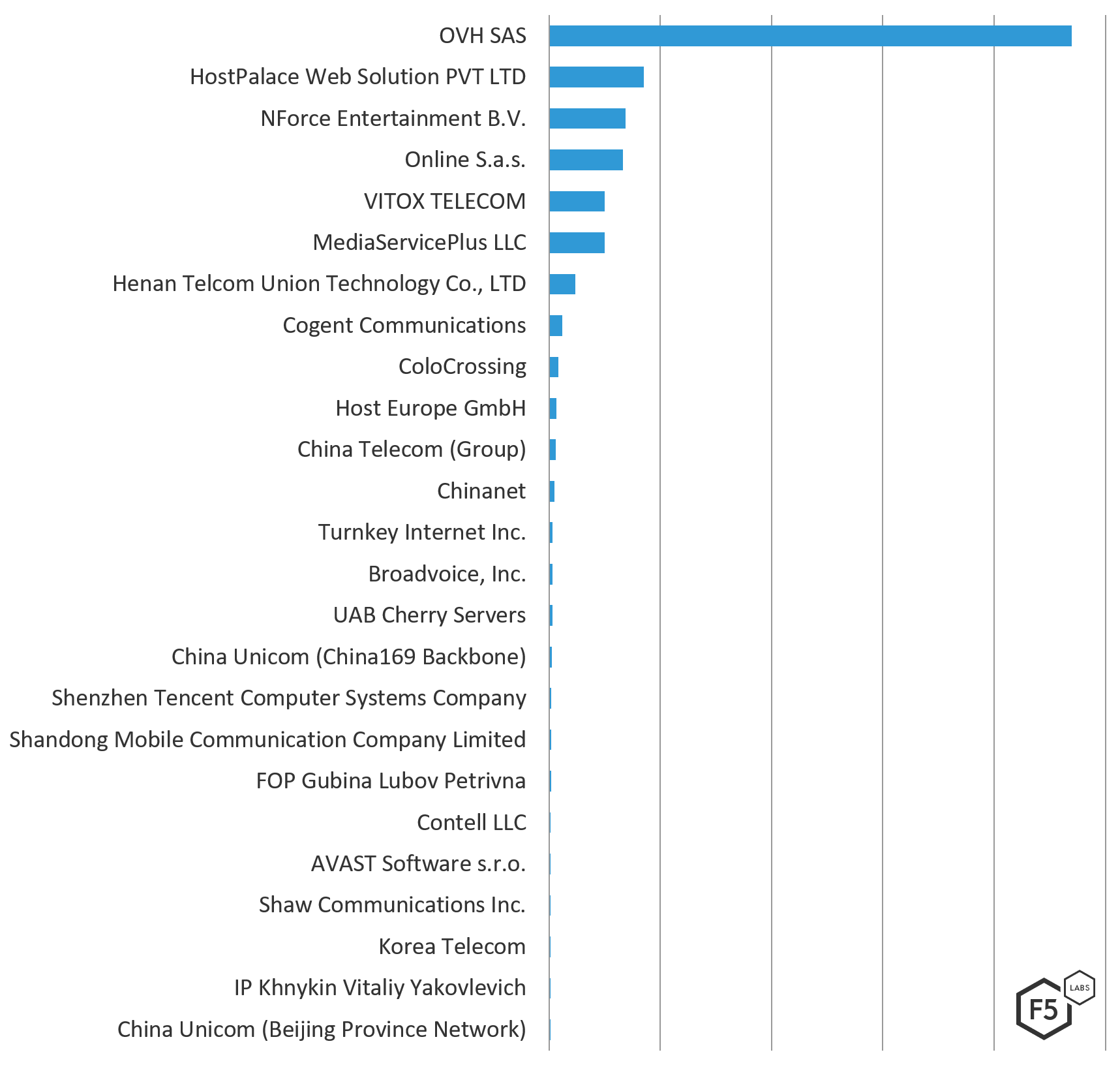
Figure 3: Top 25 attacking ASNs by attack count
The top attacking networks were primarily ISPs, followed by hosting providers and one anti-virus software provider. In comparison with Europe and Australia with similar threat profiles, ISPs accounted for 72% of attacks against European systems, and 50% of attacks against Australian systems in the same time period.
Systems residing in an ISP network are more likely to be a compromised residential or small office IoT devices. Attacks coming from a system in a hosting network are more likely to be launched by a threat actor either renting or maliciously controlling a server in the hosting environment. We believe the latter was happening, based on the count of attacks being launched per IP address in hosting environments (see Top Attacking IP Addresses section below).
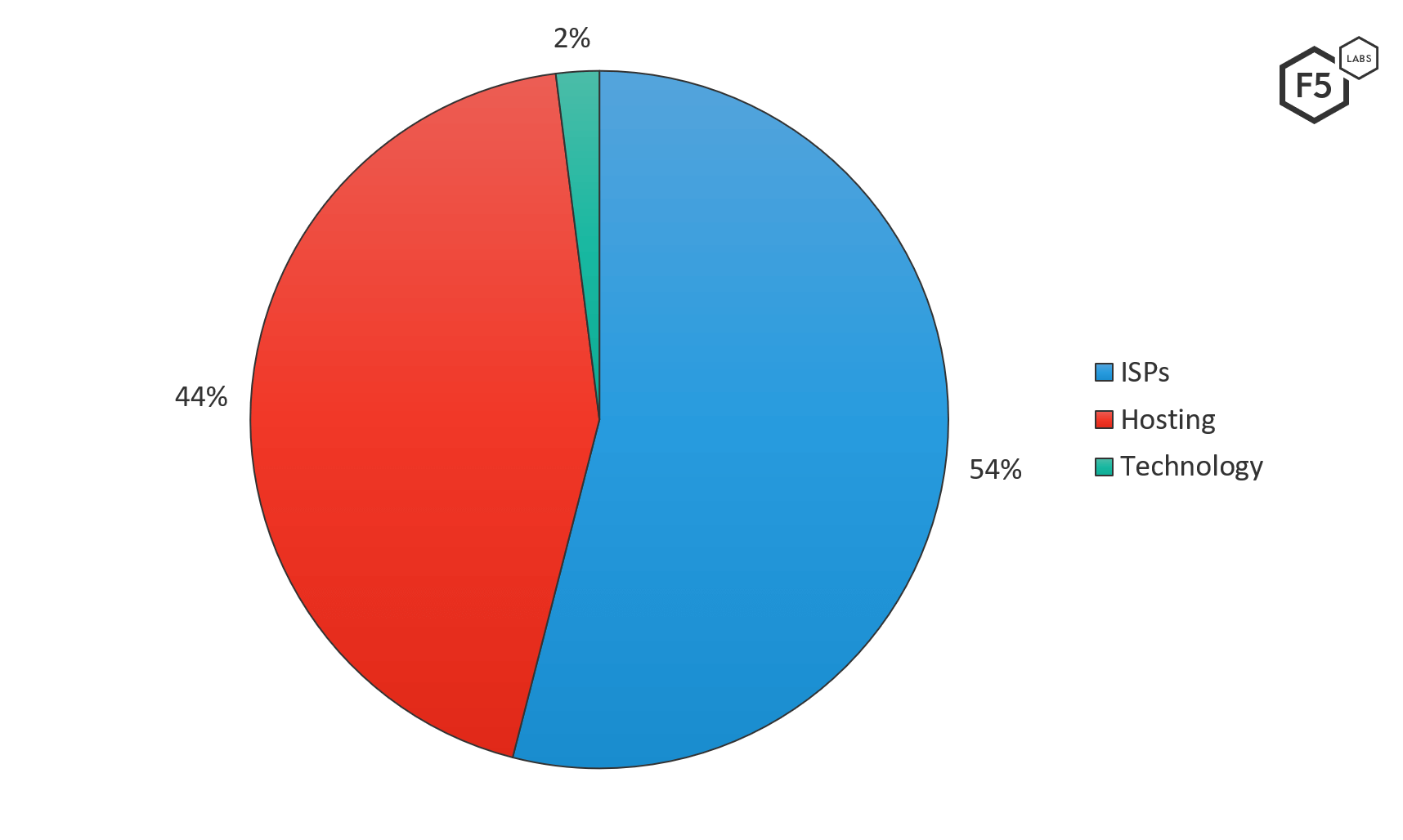
Figure 4: Top 50 ASNs attacking Canadian systems — by industry
The following table shows the top 50 ASNs attacking Canada from December 1, 2018 to March 1, 2019 in order of highest to lowest number of attacks. The majority, 54%, of the top attacking networks targeting Canada were not seen attacking systems in the US, Europe, or Australia during this time period. (The US saw similar activity in the same period where 54% of their top attacking networks were not seen attacking systems in the other regions.) One of the networks seen only targeting Canadian systems was AVAST, the anti-virus software provider.
Of the top attacking networks targeting multiple regions, almost all were seen attacking either Europe or Australia – though very few were seen attacking the US. The rows highlighted in yellow in Figure 5 indicate ASNs seen attacking other regions, and Figure 6 shows which regions those ASNs were seen attacking.
| ASN # | ASN Organization | Country | Industry |
| 16276 | OVH SAS | France | Hosting |
| 133229 | HostPalace Web Solution PVT LTD | Netherlands | Hosting |
| 43350 | NForce Entertainment B.V. | Netherlands | ISP |
| 12876 | Online SAS | France | Hosting |
| 209299 | VITOX TELECOM | Netherlands | Hosting |
| 50113 | MediaServicePlus LLC | Russia | ISP |
| 56005 | Henan Telcom Union Technology Co., LTD | China | Hosting |
| 174 | Cogent Communications | United States | ISP |
| 36352 | ColoCrossing | United States | ISP |
| 34011 | Host Europe GmbH | Germany | Hosting |
| 4835 | China Telecom (Group) | China | ISP |
| 4134 | Chinanet | China | ISP |
| 40244 | Turnkey Internet Inc. | United States | Hosting |
| 33293 | Broadvoice, Inc. | United States | ISP (VoIP) |
| 16125 | UAB Cherry Servers | Lithuania | Hosting |
| 4837 | China Unicom (China169 Backbone) | China | ISP |
| 45090 | Shenzhen Tencent Computer Systems Company | China | Hosting |
| 24444 | Shandong Mobile Communication Company Limited | China | ISP (Mobile) |
| 58271 | FOP Gubina Lubov Petrivna | Ukraine | Hosting |
| 206977 | Contell LLC | Russia | Hosting |
| 198605 | AVAST Software s.r.o. | United States | Technology |
| 6327 | Shaw Communications Inc. | Canada | ISP |
| 4766 | Korea Telecom | South Korea | ISP |
| 206792 | IP Khnykin Vitaliy Yakovlevich | Russia | ISP |
| 4808 | China Unicom (Beijing Province Network) | China | ISP |
| 9808 | Guangdong Mobile Communication Co.Ltd. | China | ISP |
| 60068 | Datacamp Limited | United Kingdom | Hosting |
| 27947 | Telconet S.A | Ecuador | ISP |
| 15975 | Hadara | Palestine | Hosting |
| 3462 | Data Communication Business Group | Taiwan | ISP |
| 19916 | OLM, LLC | United States | Hosting |
| 5413 | Daisy Communications Ltd | United Kingdom | ISP |
| 19318 | New Jersey International Internet Exchange | United States | ISP |
| 24961 | myLoc managed IT AG | Germany | Hosting |
| 8167 | Brasil Telecom S/A - Filial Distrito Federal | Brazil | ISP |
| 23033 | Wowrack.com | United States | ISP |
| 55933 | REDTone Telecommunications (HK) Limited | Malaysia | ISP |
| 60781 | LeaseWeb Netherlands B.V. | Netherlands | Hosting |
| 56389 | TSTGROUP Engineering Group EOOD | Bulgaria | ISP |
| 23724 | China Telecommunications Corporation, IDC | China | ISP |
| 31034 | Aruba S.p.A. | Italy | Hosting |
| 50613 | Thor Data Center ehf | Iceland | Hosting |
| 23650 | Chinanet (Jiangsu Province Backbone) | China | ISP |
| 26496 | GoDaddy.com, LLC | United States | Hosting |
| 29073 | Quasi Networks LTD. | Netherlands | Hosting |
| 38283 | Chinanet (SiChuan Telecom Data Center) | China | ISP |
| 44050 | Petersburg Internet Network ltd. | Russia | ISP |
| 63949 | Linode, LLC | United States | Hosting |
| 17622 | China Unicom Guangzhou network | China | ISP |
| 14061 | Digital Ocean, Inc. | United States | Hosting |
Figure 5: Top 50 attacking ASNs
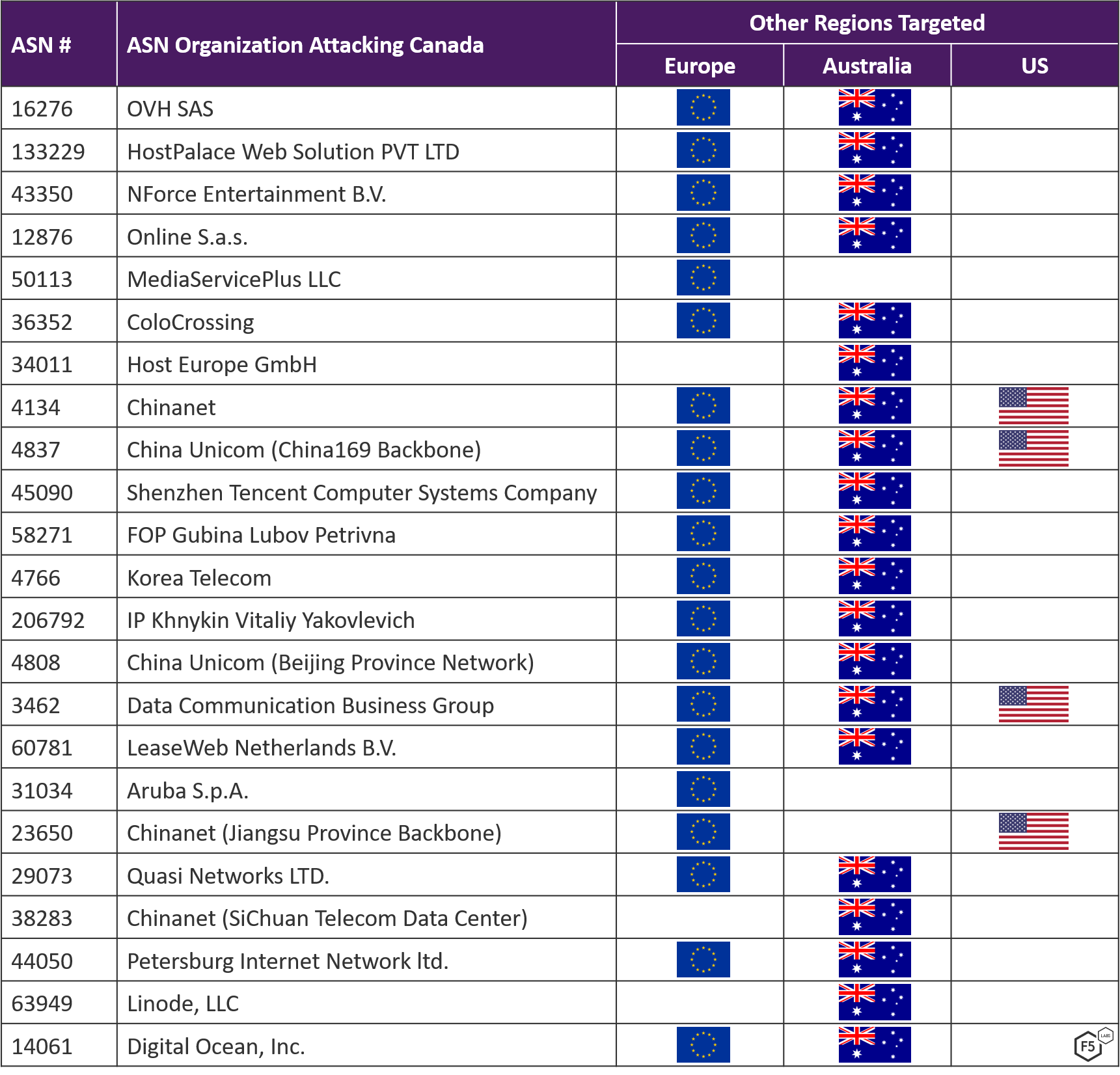
Figure 6: Commonality between target regions of ASNs attacking Canada
Top Attacking IP Addresses
Unlike the consistency seen between networks attacking Canada, European, and Australian systems, there was no consistency in the IP addresses used in those networks to attack. Forty-eight of the top 50 IP addresses (96%) attacking Canadian systems during this period were not seen attacking the other regions. Attackers are using different IP addresses in the same networks to launch attacks.
Four of the top five attacking IP addresses were from OVH SAS from systems located in Germany, Italy, and France, and collectively launched 84% of total attacks OVH SAS launched against Canada in that period. It is reasonable to think that systems in OVH SAS were compromised and used to launch these attacks, given such a high number of attacks per IP address (a threat actor trying not to get caught wouldn’t launch so many attacks per IP address).
The chart in Figure 7 below shows the top 25 IP addresses that were attacking destinations in Canada from December 1, 2018 through March 1, 2019 by count.
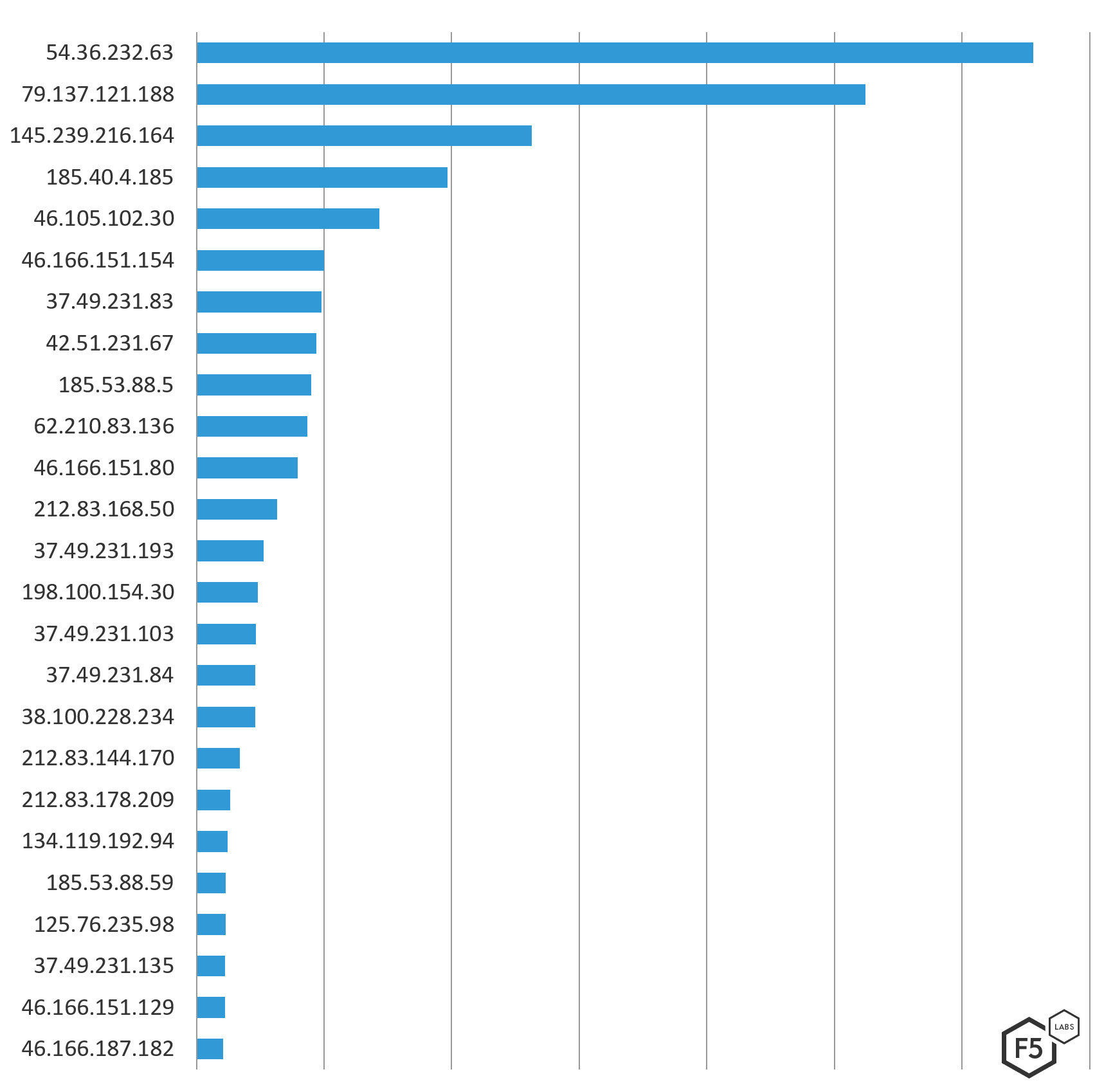
Figure 7: Top 25 attacking IP addresses by count of attacks
Figure 8 below shows the top 50 attacking IPs that launched 1.6 million attacks against Canadian destinations from Dec 1, 2018 through March 1, 2019 by ASN and Country origin. The Online SAS IP (highlighted in yellow) and NForce Entertainment IP (highlighted in orange) were also seen attacking systems in Europe in the same time period.
| Source IP | ASN Organization | Country |
| 54.36.232.63 | OVH SAS | Germany |
| 79.137.121.188 | OVH SAS | Italy |
| 145.239.216.164 | OVH SAS | France |
| 185.40.4.185 | MediaServicePlus LLC | Russia |
| 46.105.102.30 | OVH SAS | France |
| 46.166.151.154 | NForce Entertainment B.V. | Netherlands |
| 37.49.231.83 | HostPalace Web Solution PVT LTD | Netherlands |
| 42.51.231.67 | Henan Telcom Union Technology Co., LTD | China |
| 185.53.88.5 | VITOX TELECOM | Netherlands |
| 62.210.83.136 | Online SAS | France |
| 46.166.151.80 | NForce Entertainment B.V. | Netherlands |
| 212.83.168.50 | Online SAS | France |
| 37.49.231.193 | HostPalace Web Solution PVT LTD | Netherlands |
| 198.100.154.30 | OVH SAS | Canada |
| 37.49.231.103 | HostPalace Web Solution PVT LTD | Netherlands |
| 37.49.231.84 | HostPalace Web Solution PVT LTD | Netherlands |
| 38.100.228.234 | Cogent Communications | United States |
| 212.83.144.170 | Online SAS | France |
| 212.83.178.209 | Online SAS | France |
| 134.119.192.94 | Host Europe GmbH | Germany |
| 185.53.88.59 | VITOX TELECOM | Netherlands |
| 125.76.235.98 | China Telecom (Group) | China |
| 37.49.231.135 | HostPalace Web Solution PVT LTD | Netherlands |
| 46.166.151.129 | NForce Entertainment B.V. | Netherlands |
| 46.166.187.182 | NForce Entertainment B.V. | Netherlands |
| 158.69.240.193 | OVH SAS | Canada |
| 178.32.145.190 | OVH SAS | France |
| 185.53.88.55 | VITOX TELECOM | Netherlands |
| 185.53.88.16 | VITOX TELECOM | Netherlands |
| 192.3.183.186 | ColoCrossing | United States |
| 185.53.88.38 | VITOX TELECOM | Netherlands |
| 207.180.242.186 | Contabo GmbH | Germany |
| 37.49.231.107 | HostPalace Web Solution PVT LTD | Netherlands |
| 37.49.231.195 | HostPalace Web Solution PVT LTD | Netherlands |
| 185.53.88.53 | VITOX TELECOM | Netherlands |
| 102.165.33.32 | VolumeDrive | US |
| 173.198.252.203 | Turnkey Internet Inc. | United States |
| 147.135.9.218 | Broadvoice, Inc. | United States |
| 5.62.63.222 | AVAST Software s.r.o. | United States |
| 37.49.231.194 | HostPalace Web Solution PVT LTD | Netherlands |
| 212.83.163.224 | Online SAS | France |
| 185.107.94.36 | NForce Entertainment B.V. | Netherlands |
| 192.227.153.226 | ColoCrossing | United States |
| 158.69.40.251 | OVH SAS | Canada |
| 46.166.151.117 | NForce Entertainment B.V. | Netherlands |
| 46.166.151.137 | NForce Entertainment B.V. | Netherlands |
| 178.32.97.170 | OVH SAS | France |
| 185.53.88.17 | VITOX TELECOM | Netherlands |
| 185.53.88.51 | VITOX TELECOM | Netherlands |
| 93.115.28.168 | UAB Cherry Servers | Lithuania |
Figure 8: Top 50 IP addresses attacking Canadian systems December 1, 2018 through March 1, 2019
Top Targeted Ports
Looking at the destination ports of the attacks helps us understanding what types of systems attackers are after. The top three targeted ports in the Canadian attacks were SIP 5060, used by VoIP-enabled phones and video conferencing systems; Microsoft SMB, commonly referred to as Samba, which became a popular attack target after the leaked NSA/CIA exploit in 2017; and HTTP port 80, the web traffic standard. SIP 5060 was targeted eight times more than Microsoft SMB systems in the #2 position, making VoIP systems the clear target during this period.
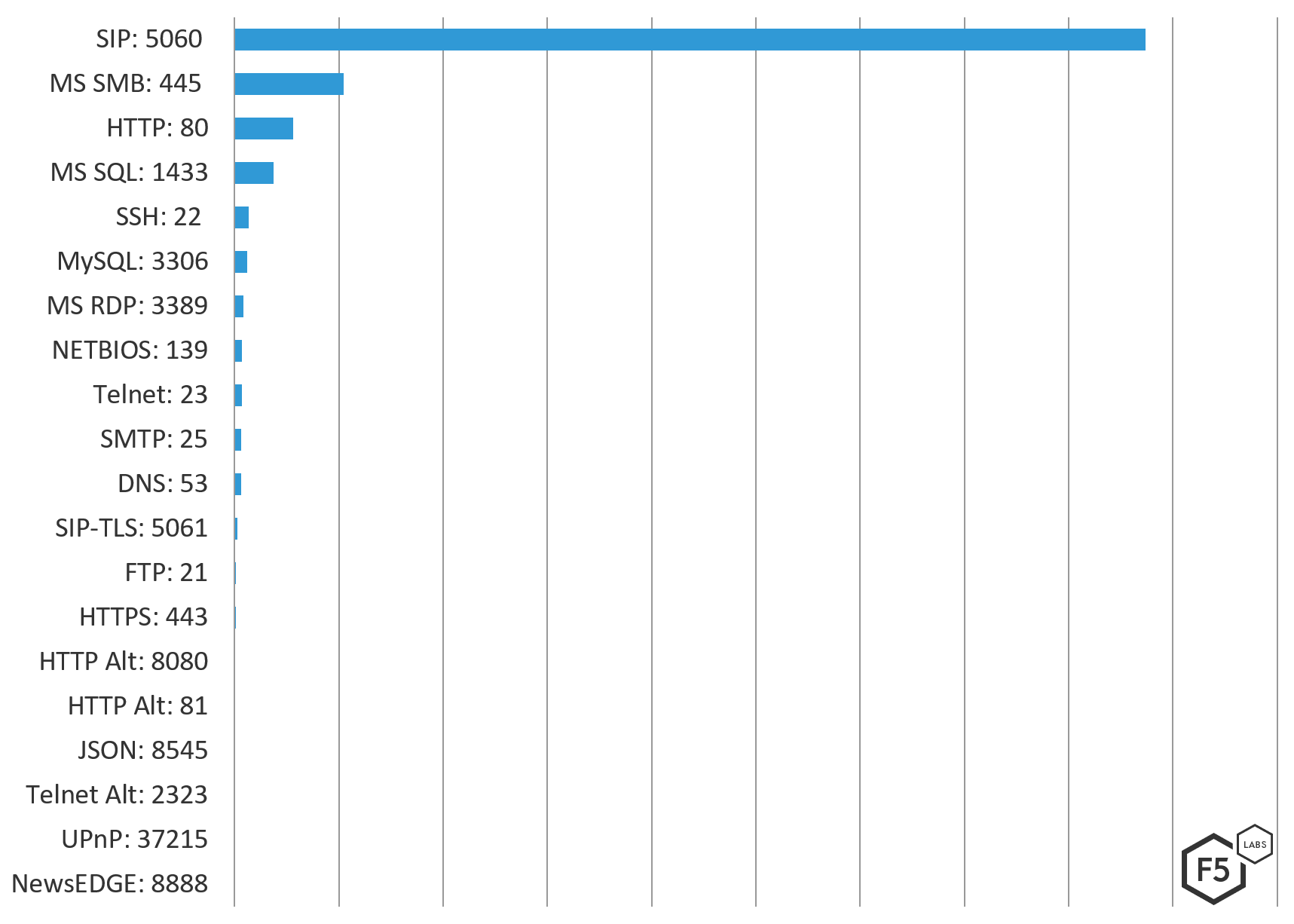
Figure 9: Top 20 ports targeted in attacks against Canadian systems Dec 1, 2018 through March 1, 2019
Comparing ports targeted in Canada versus the US, Europe, or Australia, Canada was the only region where DNS port 53 and the UPnP port 37215 were on the top 20 targeted port list. The UPnP port relates to Huawei small office home office (SOHO) routers with a Remote Code Execution (RCE) vulnerability (CVE-2017-172151 and Exploit ID 434142) that is targeted in the Kaizen, Katrina_V1, Sora, Owari, Mirai, and Hakai IoT botnets, or “thingbots.” Similarly, Microtik routers over port 8291 (CVE-2018-148473) were targeted in US, Europe, and Australia.
Conclusion
Organizations should continually run external vulnerability scans to discover what systems are exposed publicly, and on which specific ports. Systems exposed publicly with the top attacked ports open should be prioritized for firewalling off, most notably the ports from this attack traffic that should never be exposed to the big bad Internet, including: SIP port 5060, secure SIP 5061, Microsoft Samba port 445, MS SQL port 1433, MySQL port 3306, SSH port 22, Microsoft RDP port 3389 and Telnet port 23. Web applications taking traffic on ports 80, 81, 8080, and 443 should be protected with a web application firewall, be continually scanned for web application vulnerabilities, and prioritized for vulnerability management, including but not limited to bug fixes and patching.
A lot of the attacks we see on ports supporting remote access services like SSH and Telnet are brute-force attacks with known vendor default credentials. For a list of the top 100 credential pairs used in SSH brute force attacks, see the Hunt for IoT Volume 5 (/content/f5-labs-v2/en/labs/articles/threat-intelligence/the-hunt-for-iot--multi-purpose-attack-thingbots-threaten-intern.html). Remote administrative login should be restricted to a management network and have adequate brute force protections in place.
Network administrators and security engineers should review network logs for any connections from the top attacking IP addresses. If you are experiencing attacks from any of these top IP addresses, you should submit abuse complaints to the owners of the ASNs and ISPs so they hopefully shut down the attacking systems.
For those interested in IP blocking, it can be troublesome to maintain large IP blocklists and also block IP addresses within ISPs that offer Internet service to residences that might be customers. In these cases, the attacking system is likely to be an infected IoT device that the resident doesn’t know is infected, and it likely won’t get cleaned up. Blocking traffic from entire ASNs or an entire ISP can be problematic for the same reason—blocking their entire network would block all of their customers from doing business with you. Unless, of course, it’s an ISP supporting a country you don’t do business with. In that case, geolocation blocking at a country level can be effective way to reduce a large amount of attack traffic and save your systems the unnecessary processing. For this reason, it is best to drop traffic based on the attack pattern using your web application firewall.
We will continue to monitor global attacks and analyze at a regional level quarterly. Future research in this series will include the Asia-Pacific, Middle East and North Africa, and Latin American regions. If you are an implicated ASN or ISP, please reach out to us at F5LabsTeam@F5.com and we’ll be happy to share further information with you.
Recommendations
- Organizations exposing commonly attacked ports publicly to the Internet (especially systems that shouldn’t be accessible over the Internet like databases) should do their best to restrict access through their firewall.
- Any commonly attacked ports that require external access, like HTTP and HTTPS, should be prioritized for vulnerability management.
- Remote access to applications over SSH or Telnet should be restricted to management networks and protected with brute force restrictions.
- Vendor default credentials, commonly used in SSH brute force attacks, should be disabled on all systems before public deployment.
- Organizations should look to implement geo IP blocking of commonly attacking countries that the business does not have a need to communicate with.


