F5 security researchers analyzed the Ramnit banking trojan campaign that was active over the holiday season and discovered it’s not much of a banking trojan anymore.
- 64% of its targets were retail eCommerce sites, including Amazon.com, Best Buy, Forever 21, Gap, Zara, Carter’s, OshKosh B’gosh, Macy’s, Victoria’s Secret, H&M, Overstock.com, Toys“R”Us, Zappos, and many others.
- Although banks were a smaller portion of targets, the target list included some of the largest banks in the world, including Bank of America, CitiBank, PNC, Chase, TD Bank, and US Bank.
- The C&C framework collecting the stolen user data is shared by several banking trojans, including Ramnit, Gozi, GootKit, and Tinba.
- The Ramnit C&C server is registered to a network in Russia, JSC MediaSoft Ekspert, that shows up often in F5 Labs threat research.
- For the fraud to be accomplished, users must be tricked in several phases, pointing to the need for continued security awareness training.
Ramnit’s authors likely had high hopes for this holiday shopping season when they added major online retailers to their targets. And it makes sense if you are a threat actor trying to optimize your attack. Why not expand your fraud net to sites that have a high likelihood of activity over the holidays? Most financial organizations recognize that the holiday season is also their peak fraud season and, as such, they maintain an elevated state of security awareness. Additionally, financial institutions have been targeted by banking trojans for so long that most have adopted advance web defenses (that is, they can detect if a user is infected with a known trojan) to combat the problem. Other industries, on the other hand, traditionally haven’t been targeted and are therefore less likely to have the same defenses in place. So, instead of hunting bank account information, the Ramnit authors zeroed in on credit card theft, collecting social security numbers, mothers’ maiden names, secret question answers, and other critical personally identifiable information.
Ramnit Holiday Campaign Targets
Retailers and their eCommerce sites were clearly the biggest focus for the Ramnit authors over the holidays as they accounted for 64% of the targets. Although banks were a smaller portion of the targets, those targeted included some of the largest banks in the world. Other notable targets were travel sites, entertainment, food delivery, shipping, online auctions, dating, and porn sites. The Ramnit authors covered what people actually do over the holidays; shop, ship, eat, check their bank account, and entertain themselves.
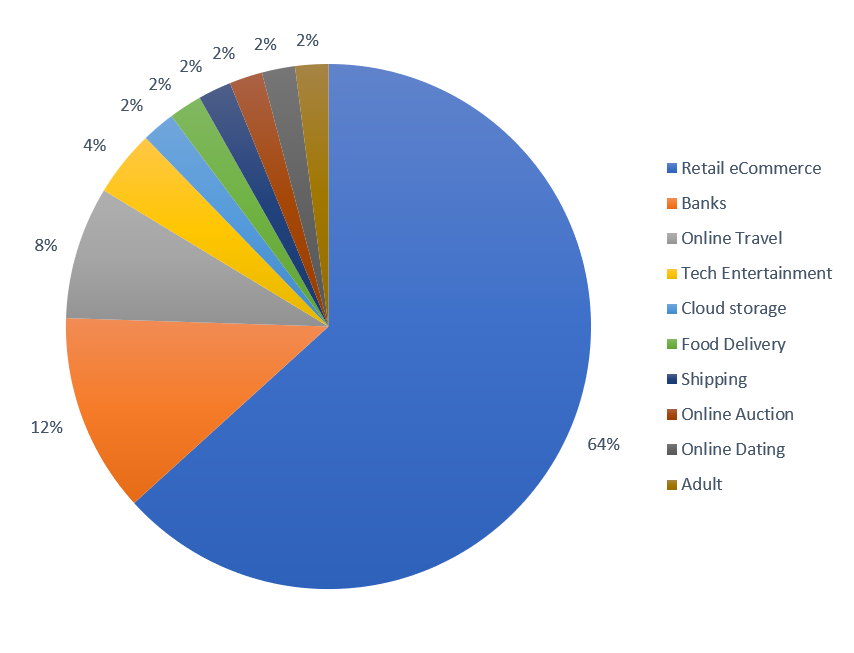
Figure 1: Ramnit 2017 Holiday Targets by Industry
Figure 1: Ramnit 2017 Holiday Targets by Industry
Retail eCommerce
- http*6pm.com*
- https*aliexpress.com*
- https*amazon.com/*
- http*asos.com*
- http*bestbuy.com*
- https*bhphotovideo.com*
- http*carters.com*
- https*etsy.com*
- http*forever21.com*
- http*gap.com*
- https*.groupon.com*
- http*hm.com*
- http*homedepot.com*
- http*ikea.com*
- https*macys.com*
- https*mrporter.com*
- https*nastygal.com*
- http*nike.com*
- http*nordstrom.com*
- http*oshkosh.com*
- https*otteny.com*
- http*overstock.com*
- http*swarovski.com*
- https*target.com*
- http*tiffany.com*
- http*timberland.com*
- http*topshop.com*
- http*toysrus.com*
- http*victoriassecret.com*
- http*zappos.com*
- https*zara.com*
Shipping
- https*usps.com*
Banks
- https://online.citi.com/*
- https://*onlinebanking.pnc.com/*
- http*pnc.com/*personal-banking.html
- https://onlinebanking.tdbank.com/*
- https://*bankofamerica.com/*
- https://*secure*chase.com/web/auth/*
- https://*chaseonline.chase.com/*.aspx
- https://onlinebanking.usbank.com/*Dashboard*
Travel
- https*airbnb.com*
- https*booking.com*
- http*.expedia.com*
- https*tripadvisor.com*
Tech Entertainment
- https*apple.com*
- https*netflix.com*
Cloud Storage
- https*sendspace.com*
Food Delivery
- https*delivery.com*
Online Auction
- http*ebay.com*
Online Dating
- https*badoo.com*
Adult
- https*pornhub.com*
Why Expansion Beyond Banks is an Easy Shift
Webinjects can perform the same way whether they are used during online banking interactions or retail purchases. When a user logs into a banking site, in some cases (say the user is accessing from a new system), the bank will ask additional validation questions before granting account access. When browsing eCommerce sites, most sites ask for login details in order to get additional information about a user. Ramnit can inject an external script with an additional request and ask the user for whatever it wants. In this case, the script asked for credit card information in addition to other personal information, including SSN.
Ramnit Infection Flow
For users to become victims, their device must first be infected with the trojan. This typically happens through some sort of social engineering attack to trick a user into clicking malicious links or opening attachments that download the trojan malware.
Upon infection, Ramnit creates sdbinst.exe in order to perform a silent installation with no visible window, status, or warning information to the user. This command then requests that iscsicli.exe run a batch file from the temp folder from any given user name. This batch file is immediately removed after infection.
This is the sdb file content in question and the inner command:
iscsicli.exeˆPatchˆMicrosoftˆ*ˆRedirectEXEˆR%temp%\..\..\LocalLow\cmd.%username%.bat

Figure 2: Ramnit sdb file content
Figure 2: Ramnit sdb file content
The batch files used in this scenario leads to two persistent infection files:
Tvysjomb.exe
KahNccgx.exe
These files can be found in the system startup actions of Windows machines: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
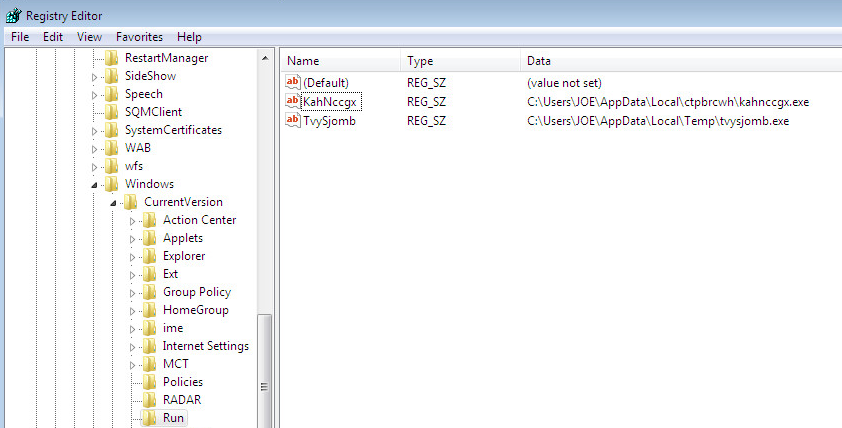
Figure 3: Where to find infection files in Windows machines
Figure 3: Where to find infection files in Windows machines
Ramnit then injects its modules into two svchost.exe processes:
Svchost.exe — Hosts rmnsoft.dll, a module that is responsible for the direct communication with the C&C server, receives modules, configurations, and commands.
Svchost.exe — Hosts modules.dll is dedicated for loading other modules and command execution.
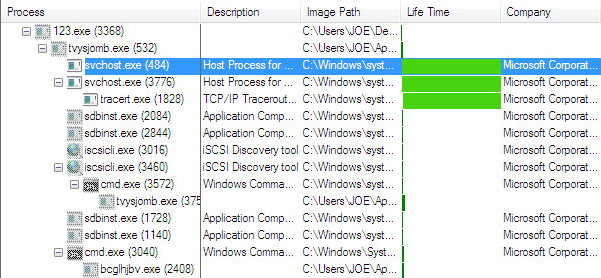
Figure 4: Processes into which Ramnit injects its modules
Figure 4: Processes into which Ramnit injects its modules
For more information on Ramnit’s infection flow, see our in-depth analysis of Ramnit from February 2017 (/content/f5-labs/en/labs/articles/threat-intelligence/ramnits-latest-twist-a-disappearing-configuration-25079.html).
Ramnit External Injections
Ramnit maintains its injection and stolen information on a Command & Control (C&C) server called Tables. Tables injects script based on the user browsing action. When the infected user accesses a targeted URL, Ramnit triggers a maintained external script to the requested page and sends back the stolen information to the Tables C&C server.
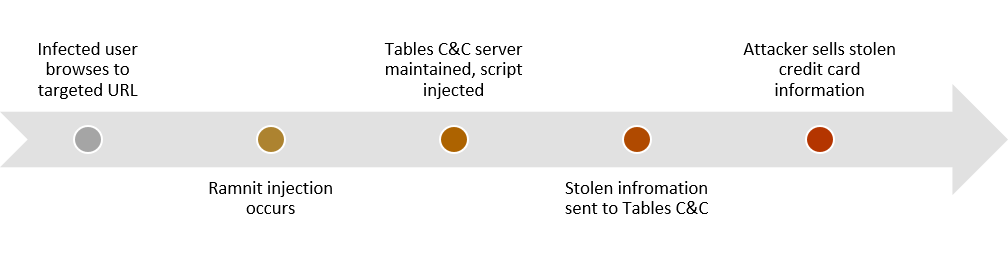
Figure 5: Ramnit attack path
Figure 5: Ramnit attack path
Banking Site Injection and Requested Information
Once Ramnit has infected the user, it still needs to create a scenario in which it can request information from that unsuspecting user. Ramnit authors rely on crafty social engineering to do this and injected content to a bank login page in three different stages:
Ramnit creates a scenario in which the user encounters a new testing ground of the banking site.
- Ramnit tells the infected user that the bank is testing an “integration of the personal email client into the banking system”
Then, Ramnit requests an email address for the new feature.
- Ramnit sends an activation link in the “confirmation email” along with activation instructions
- In this stage, Ramnit can send other, more phish-wise, related information to the infected user.
Ramnit explains to the infected user that the feature is not working due to a technical problem and that they need to supply more data. Ramnit reassures the user that this is a “one-time check” and “in the future you will be able to use your account without problems.”
The information requested at this stage includes:
- Email address
- Email password
- Debit card number
- Credit card number
- Expire date
- PIN
- CVV
- Telephone banking password
- Social insurance number
- Social security number
- Date of birth
- Mother’s date of birth
- Mother’s maiden name
- Driver’s license number
- ATM PIN
- Employer
This information is shown in the following code snippet:
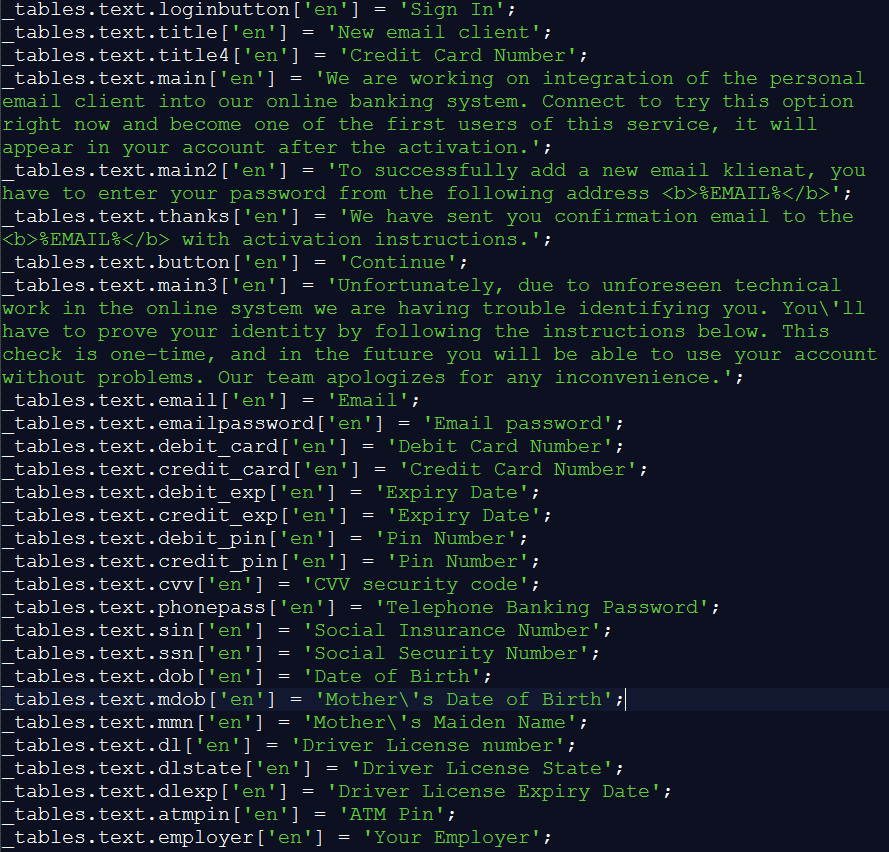
Figure 6: Ramnit’s messaging and information request to an infected user on a banking site
Figure 6: Ramnit’s messaging and information request to an infected user on a banking site
eCommerce Site Injection and Requested Information
In the eCommerce scenario, Ramnit is still reliant on social engineering to create a scenario in which the user is asked to provide additional information. At the third stage, an infected user on an eCommerce site is presented the same “technical issue” message, stating they require a “one-time check” of information that won’t be required again… but the data they request is slightly different:
- Credit or debit card
- Address details
- Name on card
- Card number
- CVV
- Street address
- City
- Phone number
- Date of birth
- Social security number
- ZIP
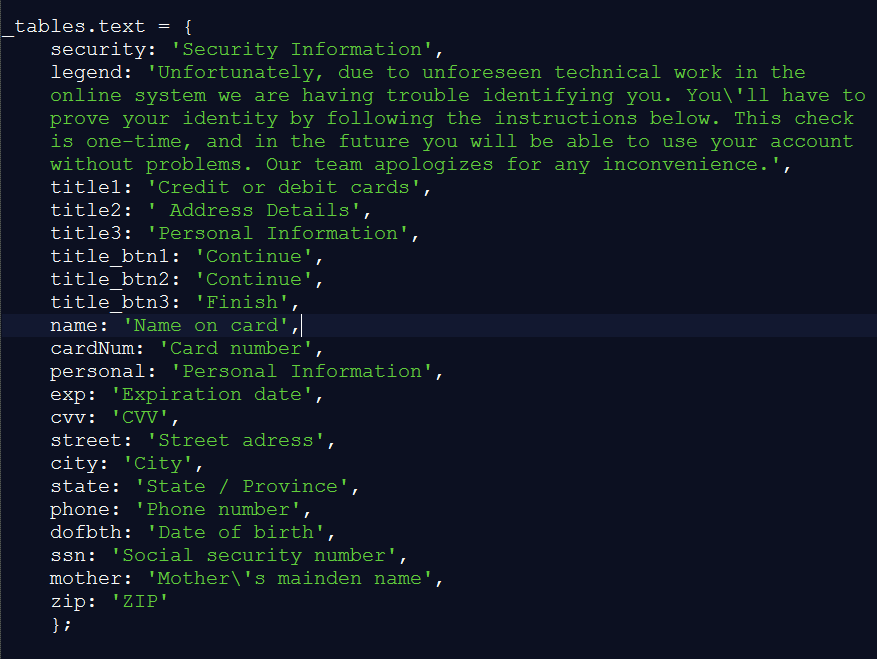
Figure 7: Ramnit’s requested information to an infected user on an eCommerce site
Figure 7: Ramnit’s requested information to an infected user on an eCommerce site
Figures 8 and 9 are examples of what the infected user sees while browsing on one of these sites. Notice the incorrect grammar, spelling and punctuation errors, as well as the non-standard characters in the fine print at the bottom of each screen:
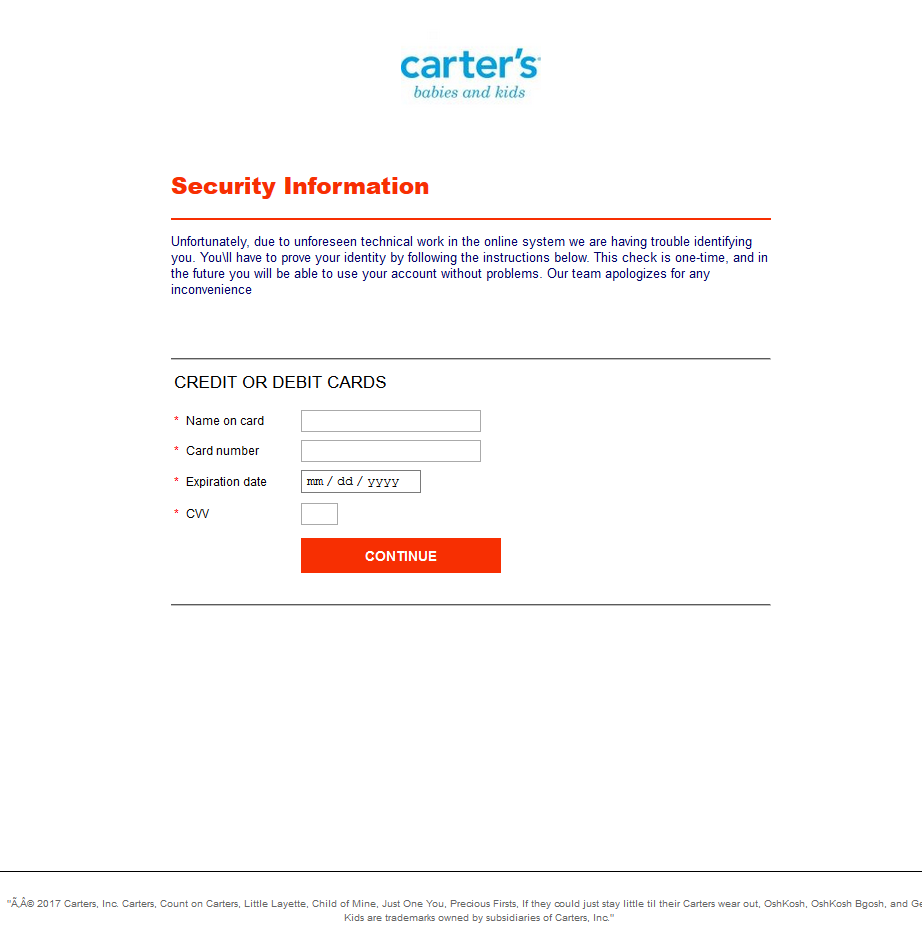
Figure 8: Infected user experience while on Carter’s
Figure 8: Infected user experience while on Carter’s
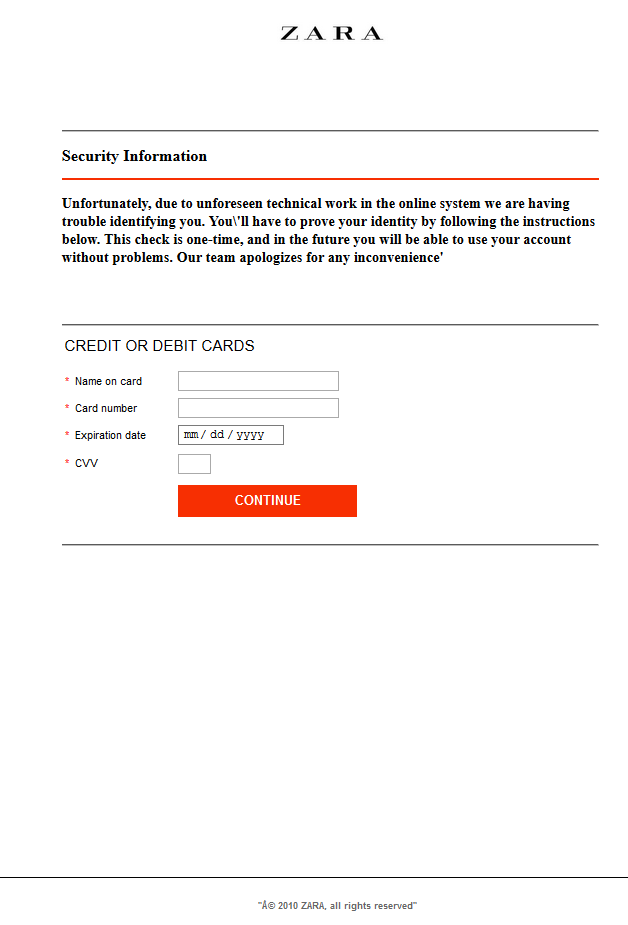
Figure 9: Infected user experience while on Zara
Figure 9: Infected user experience while on Zara
Tables Information Gathering
The Ramnit C&C server, Tables, is shared between several malwares, including Ramnit, Gozi, GootKit, and Tinba. Its IP address, 194.87.102.205, is registered to JSC MediaSoft Ekspert, a network that shows up often in F5 Labs threat research.
Tables supports a variety of operating systems:
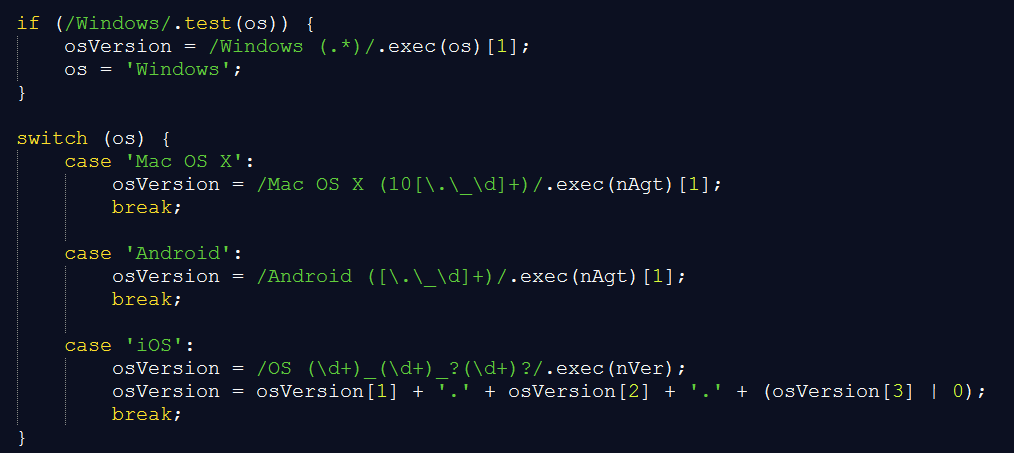
Figure 10: Tables OS support
Figure 10: Tables OS support
And it is leveled to the specific version, if needed:
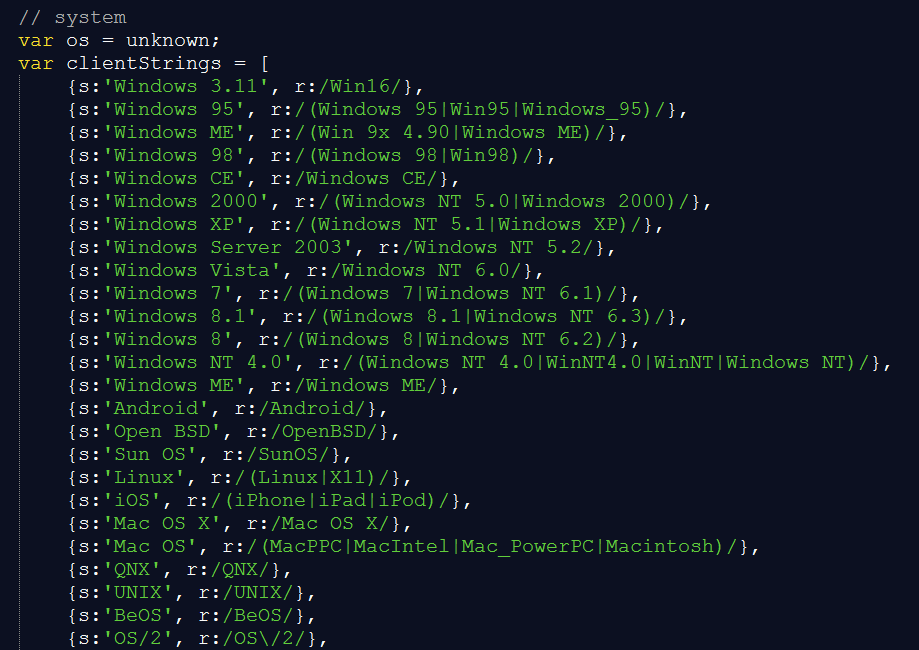
Figure 11: Tables OS versions supported
Figure 11: Tables OS versions supported
Tables identification of browsers:
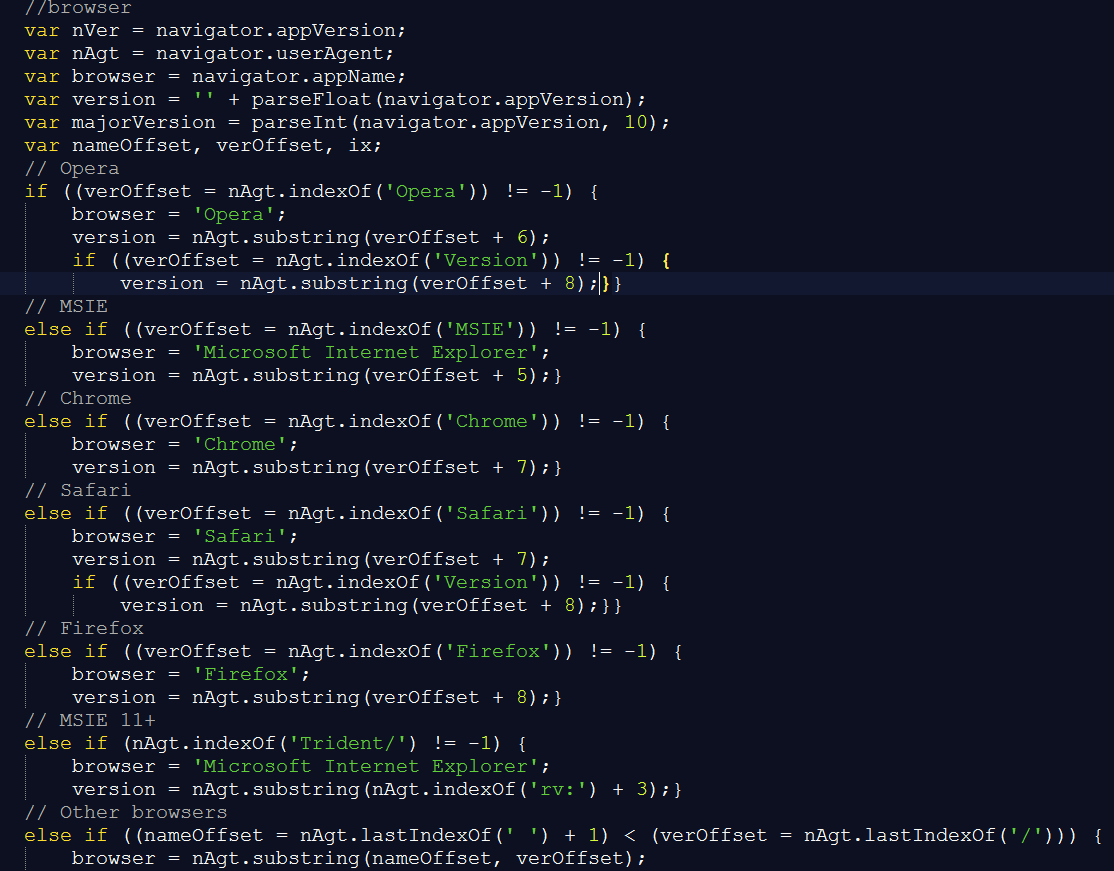
Figure 12: Tables browser support
Figure 12: Tables browser support
VNC and SOCKS functions are used in the following script to allow Ramnit authors to take control of the infected machine. In this case, Ramnit looks for elements or variables in the injected page that support VNC and SOCKS capabilities.
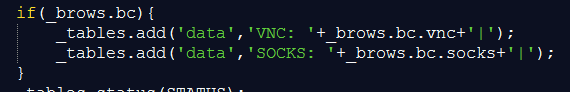
Figure 13: VNC and SOCKS functions in Ramnit
Figure 13: VNC and SOCKS functions in Ramnit
Conclusion
Ramnit’s targeting of retail eCommerce and other online industries is an unusual step. Banking trojans regularly change their activity, but it usually stays within the realm of financial targets and different geolocation targets. The authors, in this case, clearly intended to target industries and specific sites that they know are popular destinations, especially during the holiday time.
The lessons to be learned from this situation are twofold:
1. Regardless of industry, advanced web fraud protections should be widely adopted across high traffic web properties that collect personally identifiable user data to limit the amount of actual fraud that’s accomplished. What’s notable about fraud on an eCommerce site versus a financial institution is that the impact is typically felt by credit card providers and the users themselves via identity theft, not the eCommerce sites directly. The impact on a financial institution is in dollars drained out of bank accounts that must they must then deal with on behalf of the defrauded user. This process is operationally time consuming and also costs them real dollars. This gives financial institutions the incentive to purchase additional security controls, whereas a typical eCommerce site not might feel the impacts of banking trojan fraud in the same way.
2. Even though a user has been infected by a malware, there are still a lot of steps that must be accomplished before the fraud is successful. Security awareness is critical to combat this type of attack. A lot of financial institutions have created “security” pages where they give security awareness advice and tips for identifying fraud. This practice should be more widely adopted and include basic red flags like:
- A list of data your customer service department would never ask for over the phone or through your website, such as a user’s full social security number or credit card CVV.
- A warning to users to be suspicious of fraud and pay attention for unusual looking web pages with broken English, incorrect grammar, spelling errors, and strange or misplaced characters.
Appendix A
Ramnit’s domain generation algorithm (DGA) list:
- tcp://blrrebac.com:443
- tcp://dsjpyhwrcykkymgcmtk.com:443
- tcp://ojrpdqrynxjxcxep.com:443
- tcp://evkvqksebsmnuyluvm.com:443
- tcp://fbducoxhluqrpulk.com:443
- tcp://ljewfxhym.com:443
- tcp://bibcxgoilxejw.com:443
- tcp://itglxtgq.com:443
- tcp://gpvuowahrsxwnytibuk.com:443
- tcp://scessqgj.com:443
- tcp://hyfhjonbmfxdy.com:443
- tcp://gbvihdgfxccxlui.com:443
- tcp://hvyidchwstgqpjynk.com:443
- tcp://qhufdntlwo.com:443
- tcp://qyokmgngruansexcha.com:443
- tcp://jyfllqilh.com:443
- tcp://cfvvhpilqri.com:443
- tcp://mhkchwobtbl.com:443
- tcp://xkpegnrn.com:443
- tcp://silrvrscpsa.com:443
- tcp://kyfnccxlmofqce.com:443
- tcp://yntwugycoqqchtuf.com:443
- tcp://tpefhdehxevwc.com:443
- tcp://tbaieqlxhwdlxp.com:443
- tcp://gaqegnbcxb.com:443
- tcp://swalrhucdexbhwm.com:443
- tcp://kkfpihwavbp.com:443
- tcp://fcbtorovpkvovc.com:443
- tcp://uiriemhmawpawkhw.com:443
- tcp://ckkxyupijvcfaauukvo.com:443
MD5 TESTED:
- 3f4b1c4f7ce699382d5f126a512c6bbf
- 6e2cb88bf16f18b22f58603ddca81750
- 074d39af2df879c713406b00c04ca79e
- b760f973a9b78490766a5fe3c92bc5d0


