A new DDoS attack vector that leverages Lightweight Directory Access Protocol (LDAP) for reflection-amplification attacks was reported in October 2016 by Corero Network Security. Reflection-amplification attacks are not a new DDoS trend, but new attack vectors emerge all the time. Attackers continue to exploit decades-old protocols in an effort to achieve stronger amplification, enabling them to inflict greater damage.
How It Works
As with any reflection-amplification DDoS attack, three players are involved: the attacker, the unwitting “victim” server, and the attacker’s target. The attacker sends small requests to a publicly available “amplifying” server—in this case, an LDAP server—in order to produce large (amplified) replies, reflected to a target server. The attacker spoofs (changes) the source IP address so that the request appears to have originated from the target, thereby making the LDAP server “reply” to the target. To increase attack efficiency, the attacker usually selects the queries that will yield the largest replies in order to amplify the attack strength.
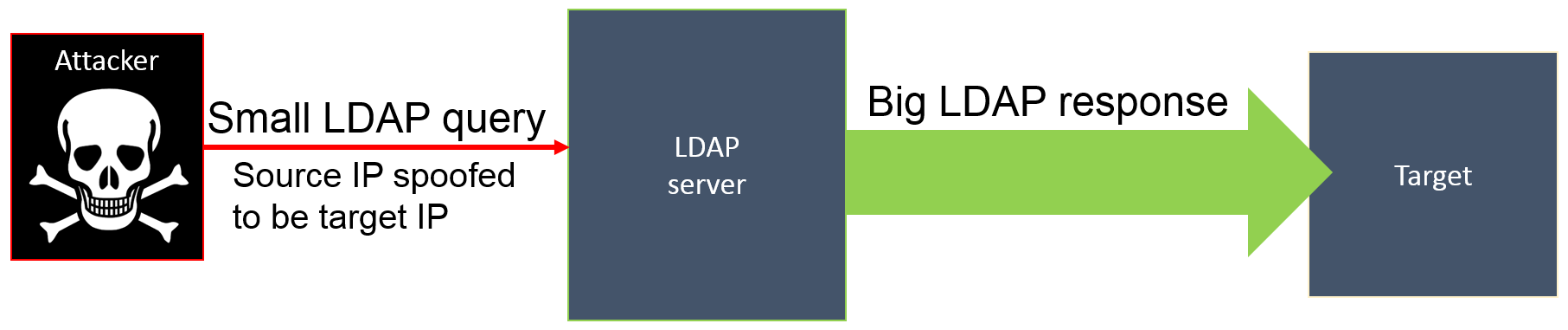
Figure 1: How an LDAP reflection-amplification attack works
Figure 1: How an LDAP reflection-amplification attack works
LDAP's Weak Spot
LDAP is used to query resources such as networks, systems, applications, and services throughout an organization network. This protocol is typically served over TCP, which requires a connection to be established before data is transferred. But, in this case, because the source IP address is spoofed and a connection cannot be established, the attacker must use a connectionless protocol like UDP in order for a reflection attack to work.
Conveniently, LDAP also supports communicating over UDP—a connectionless protocol—using port 389 by default. Thus, any publicly available LDAP server that uses UDP port 389 could be a great amplifier for serving this attack because LDAP over UDP lets some unauthenticated queries right through.
In researching this attack vector, one of our first questions was whether there were organizations that actually enabled LDAP authentication publicly. The answer was, unfortunately, yes.
Global Scope of Vulnerable LDAP Servers
Attackers typically use network scanners to look for publically open ports on selected IP addresses. These scanning tools are relatively simple to set up, even for someone with limited technical skills. A simple installation process and a few command line entries are all that’s required.
What’s more, it’s simple for just about anyone to use the Shodan search engine to find vulnerable LDAP servers. At the time of this writing, Shodan reported 1,984 vulnerable LDAP servers globally.
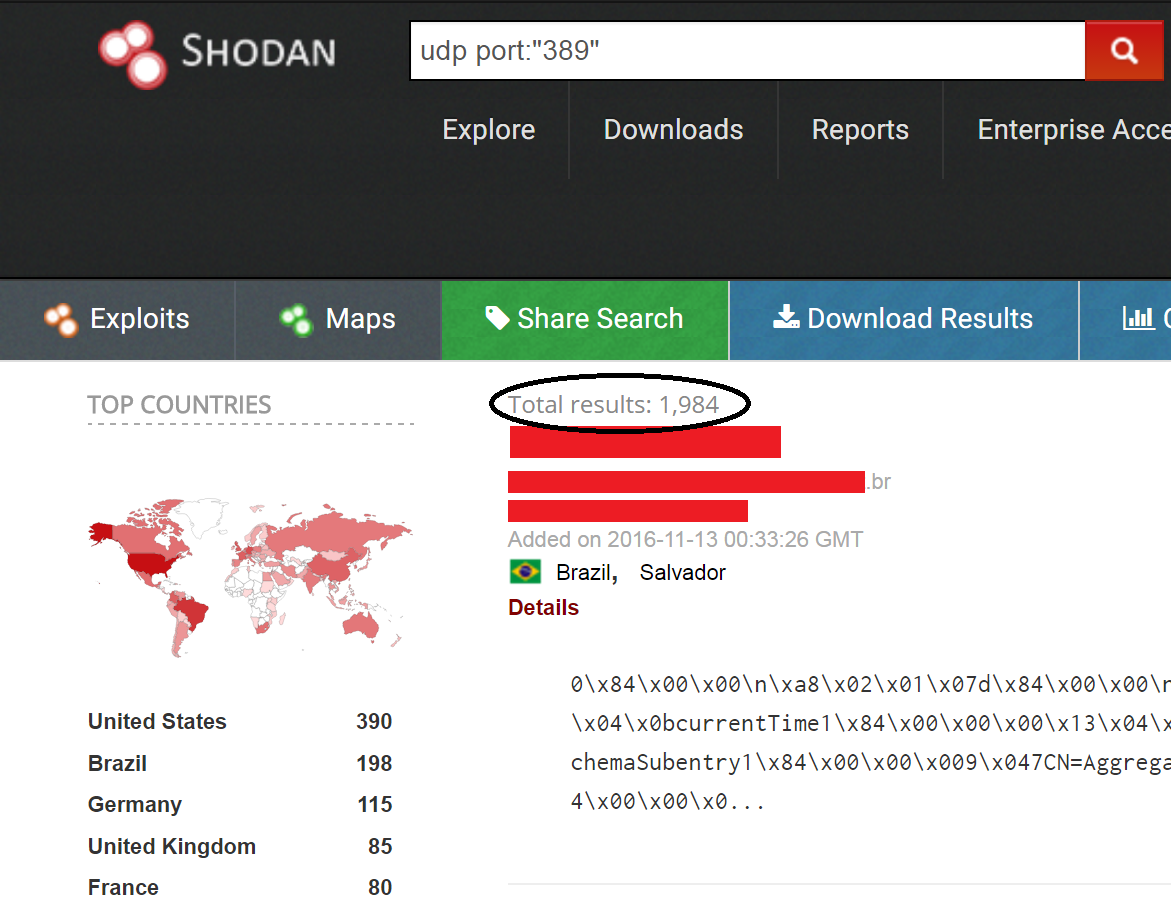
Figure 2: Search results for publically vulnerable LDAP servers
Figure 2: Search results for publically vulnerable LDAP servers
The highest percentage (20 percent) were located in the US, 10 percent in Brazil, and the remaining systems were spread across various countries throughout the globe.
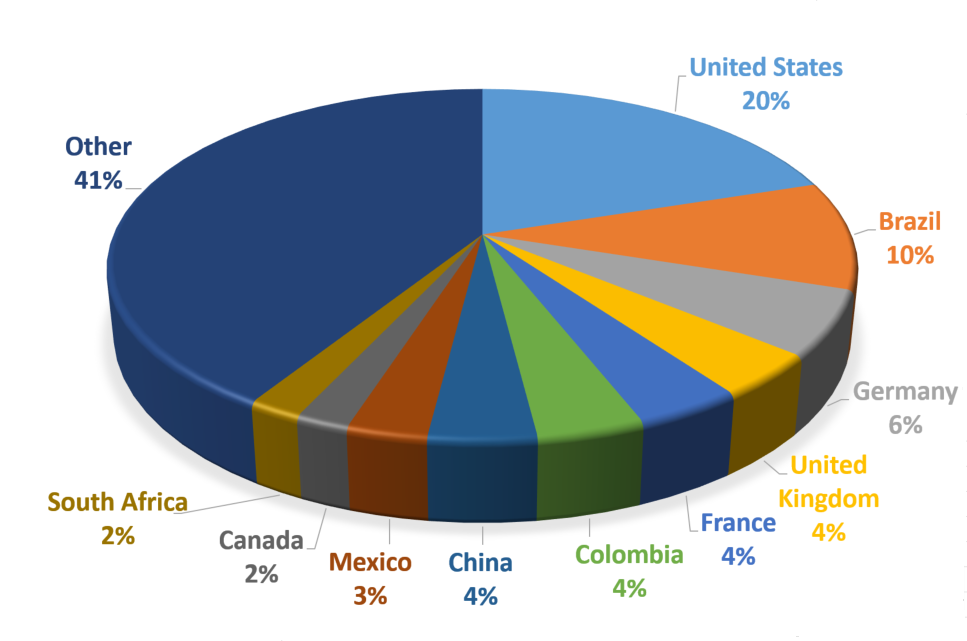
Figure 3: Vulnerable LDAP servers by country
Figure 3: Vulnerable LDAP servers by country
Getting the Amplification Factor
The “amplification factor” refers to how efficient the attack is at enlarging the amount of data that’s sent to the target. It is calculated by dividing the length of the response from the LDAP server by the length of the attacker request.
Using the list of vulnerable servers provided by Shodan, we tested a randomly selected server to determine the amplification factor.
Figure 4: Tunisian server tested
Figure 4: Tunisian server tested
Using Sysinternals’ port scanner PortQry, we generated the LDAP query over UDP.
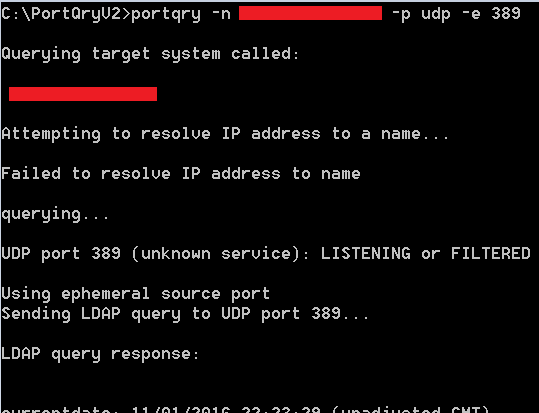
Figure 5: PortQry scanner generating the LDAP query over UDP
Figure 5: PortQry scanner generating the LDAP query over UDP
Using Wireshark, we can see the query and response length, shown in Figure 6.
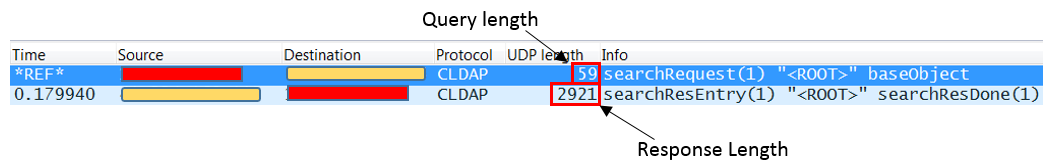
Figure 6: Wireshark displays the query and response lengths
Figure 6: Wireshark displays the query and response lengths
The response length of the Tunisian server we tested was 2,921 bytes. Based on the 59 bytes query size, the amplification factor is 49. Subsequent tests of vulnerable servers in Mexico, Kenya, and Pakistan revealed amplification factors of 51, 42, and 48 respectively. These testing figures indicate that an LDAP amplification attack could be just as strong as a DNS amplification attack.
The list in Figure 7 shows how LDAP ranks against other protocols in terms of amplification factor as reported by the US Cert.
| Rank | Protocol | Amplification Factor |
| 1 | NTP | 556.9 |
| 2 | CharGEN | 358.8 |
| 3 | QOTD | 140.3 |
| 4 | RIPv1 | 131.24 |
| 5 | Quake Network Protocol | 63.9 |
| 6 | LDAP | 46 – 55 |
| 7 | DNS | 28 – 54 |
| 8 | SSDP | 30.8 |
| 9 | Portman (RCPbind) | 7 – 28 |
| 10 | Kad | 16.3 |
| 11 | Multicast DNS (mDNS) | 2 – 10 |
| 12 | SNMPv2 | 6.3 |
| 13 | Stream Protocol | 5.5 |
| 14 | NetBIOS | 3.8 |
| 15 | BitTorrent | 3.8 |
Figure 7: US Cert Amplification Figures
The steps described above are very easy for an attacker to perform. Using a list of vulnerable LDAP servers, an attacker using raw sockets for sending the UDP requests can now spoof the request IP address and generate a reflection attack with an average amplification factor of 47.
Conclusion
LDAP has been around for more than 20 years, NTP and DNS for over 30. These protocols are all susceptible to being used as DDoS amplifiers and all discovered to be vulnerable only within the last decade. New DDoS amplification attack vectors continue to be discovered within connectionless protocols. A quick Shodan search looking for open UDP ports resulted in almost 9 million servers using the SIP protocol, over a million servers using Portmap, and more than 18,000 servers with an open UDP port 8081. The next vulnerable protocol has probably already been out there for years and is ready to serve as an enabling protocol in a DDoS amplification attack.
In general, new attack vectors have higher odds of passing through unprepared mitigation devices. We expect the LDAP DDoS attack vector to be more prominent in amplification attacks in the future.


