Zero Trust is a powerful, holistic security strategy helping to drive businesses faster and more securely. Ensuring security to corporate applications is critical in preventing data breaches. Doing it well also can increase efficiencies in business processes and user productivity. A Zero Trust security model can deliver this business value, but Zero Trust is not a product. Rather, it is an approach—and a maxim—that translates into secure network and application architectures. Essentially, it is an ecosystem of solutions working together to make sure no user or device is trusted by default from inside or outside the network, and verification is required before gaining access to applications.
In recent years, Zero Trust has received a great deal of attention, although it’s not a new concept. However, it is a concept that is more relevant and important today than ever, particularly as companies around the world grapple with how to operate and respond during pandemics and other natural or manmade emergencies. As organizations worldwide accelerate digital transformation initiatives, Zero Trust is a concept that’s critical for every organization to better understand.
The established “moat and castle” approach of traditional network perimeter security – allowing only known, trusted individuals to cross the “moat” and enter the “castle walls”, allowing them access to any application or resource they are authorized access – is no longer sufficient. With the rise of applications being deployed or migrating across on-premises, multiple cloud environments, and Software-as-a-Service (SaaS) applications, along with the growing mobile and remote workforce, the network perimeter has all but disappeared.
Zero Trust eliminates the idea of a trusted network inside a defined perimeter. Today, you must assume attackers are already on your network, hiding and lurking, waiting for the right moment to launch an attack. You need to apply least-privilege user access and scrutinize users, their devices, their access, and more as much as possible and get more context and visibility from your internal and external control points.
To enable Zero Trust, you must abandon the “Trust, but Verify” approach and now adhere to these principles:
- Never trust
- Always verify
No vendor today can deliver everything needed to enable a Zero Trust environment. However, F5 does add value and delivers key components you will need in deploying a comprehensive Zero Trust approach. With our robust application security portfolio and ability to secure the new control points in a Zero Trust environment, F5 provides you with the building blocks necessary to address a “Never trust, always verify” approach to securing today’s applications, and also adds a third principle to Zero Trust, “Continuously monitor.”
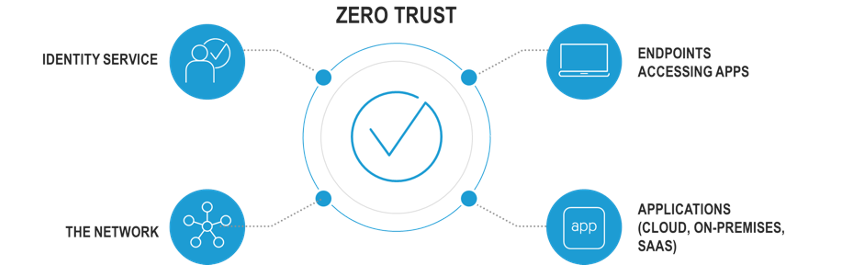
From F5’s perspective, these are the four control points that you need to secure:
- The endpoints accessing applications
- The applications (regardless if they are native cloud or SaaS apps, or classic and custom applications)
- The identity service
- The network infrastructure
So, how does F5 help to secure each control point?
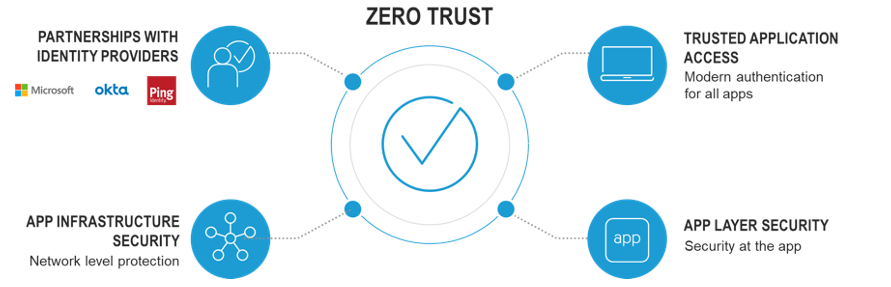
- For endpoints accessing applications, F5’s Trusted Application Access solutions provide modern authentication and centralized access to and control for all applications.
- For your network infrastructure, F5’s Application Infrastructure Security solutions help protect your network from attacks and intrusions.
- For your applications, F5 offers Application Layer Security solutions, delivering security at or near the application and protecting your application stack, from layers 4 through 7.
- For the identity service, we have deep partnerships with Microsoft, Okta, and Ping, among others. By integrating our Trusted Application Access solutions with these Identity-as-a-Service (IDaaS) providers, F5 helps you bridge the identity and authentication gap between native cloud and SaaS apps, and mission-critical classic and custom applications, enabling a unified, secure access experience for all users to any application.
F5 can specifically help you deploy a Zero Trust model leveraging our Trusted Application Access, Application Infrastructure Security, and Application Layer Security solutions.
When it comes to application access, organizations must assume that everyone accessing their site is malicious. Access-related breaches continue to rise and show no signs of abating any time soon.
F5 BIG-IP Access Policy Manager (APM) secures, simplifies, and centralizes access to apps, APIs, and data, no matter where users and their apps are located. With its Identity Aware Proxy (IAP) capabilities, BIG-IP APM deploys a Zero Trust model validation based on granular context- and identity-awareness, securing every application access request. It also continuously monitors each user’s device integrity, their location, and other application access parameters throughout their application access session.
BIG-IP APM enhances user experience via single sign-on (SSO) to any application the user is authorized access, regardless from where it is hosted or the type of authentication methods it requires, modern or classic authentication, enabling a common user experience across all apps. By employing IAP, applications and access to them is more secure, helping to enable Zero Trust application access. BIG-IP APM also delivers a common architecture for hybrid environments and enables common access policies to be created and enforced for accessing applications across multiple clouds.
With the addition of Shape Security, and the ability to determine bad actors committing fraud, F5 is now able to better identify good users and reduce the number of times a user is required to input a password. This allows users to get more access to services they are authorized for without having to create additional username / password pairs – a major source of credential theft and credential stuffing attacks, forgetting passwords, lowering your support costs, and increasing your top line.
While the network perimeter is diminished, it is not going away anytime in the foreseeable future. Your network infrastructure plays an important role in ensuring that your apps on-premises, in a data center, or in a private cloud remain secure and available in order to achieve Zero Trust. One danger that could significantly impact your network, users, and data are threats hidden in encrypted traffic.
Encryption is now the new normal. Most web page loads are now encrypted. While that’s great for privacy, it enables attackers to use the encrypted traffic to hide malware and other malicious payloads to bypass security controls. Today, you must assume your incoming encrypted traffic is harboring malware. You must also assume your outbound encrypted traffic contains sensitive data that is being exfiltrated or is communicating with malevolent command-and-control servers being readied to launch more or greater attacks.
F5 SSL Orchestrator solves the encrypted traffic dangers trying to access your network. It eliminates security blind spots by exposing malware hiding in encrypted traffic and halts exfiltration of stolen data. It’s a dedicated solution for the orchestration of inbound and outbound encrypted traffic. It enables the creation of dynamic security service chains, leveraging its context-aware policy engine and policy-based traffic steering, enabling you to do away with manually daisy-chaining the solutions in your security stack. It also ensures intelligent bypass, to keep you from running afoul of industry and government privacy compliance regulations. SSL Orchestrator monitors, load balances, and ensures the health of your existing security solutions. It also centralizes encryption control, saving your administrators time and energy.
The reality is that applications are vulnerable in any organization. Applications continue by far to be initial targets of breaches. Attackers know how important applications are for your enterprise and they actively try to compromise your apps as every one of them can be a back door (or front door) to your valuable intellectual property and data. It’s critical to continuously protect your apps as part of any Zero Trust strategy.
F5 protects your application stack in a Zero Trust architecture. Our web application firewall (WAF) solutions, such as Advanced WAF, Essential App Protect, and Silverline WAF prevent common vulnerabilities and exploits, such as the OWASP Top 10 or SQL / PHP injections. In addition, NGINX App Protect, built on F5’s leading WAF technology and running on our NGINX Plus software, is a lightweight, high performance WAF for modern application environments.
Our WAF solutions can also protect against layer 7 DoS attacks through our behavioral analytics capability, continuously monitoring the health of your applications. F5 also provides credential protection to prevent unauthorized access by attackers to your users’ accounts. Plus, with the growing use of APIs, F5 protects them and secures your applications against API attacks.
While F5 protects your application vulnerabilities with WAF and API security solutions, we also protect your business logic from fraud and abuse with Shape Security solutions.
In addition, F5 delivers our security offerings to fit your organization’s Zero Trust deployment strategy – self managed, as-a-service, or as a fully managed service via Silverline and Shape Security.