Office 365의 ID 보안
Microsoft Office 365는 이메일 및 기타 생산성 도구와 같은 상용 애플리케이션을 실행하는 데 드는 관리 및 인프라 비용을 아웃소싱하려고 할 때 인기 있는 선택입니다. Office 365에서는 암호 해시를 포함하여 사용자 ID를 완벽하게 제어할 수 있는 페더레이션 ID 모델을 사용할 수 있습니다.
BIG-IP Access Policy Manager (APM)를 사용하면 추가적인 Active Directory Federation Services(ADFS) 서버와 프록시 서버 계층의 복잡성 없이 기존 Active Directory에서 Office 365로 안전하고 통합된 ID 관리를 제공할 수 있습니다. 지리적 제한 및 다중 요소 인증과 같은 향상된 APM 보안 기능을 사용하여 Office 365에 대한 액세스를 더욱 안전하게 보호할 수 있습니다.
사용자를 Office 365로 마이그레이션하기로 결정했다면 로그인 모델을 결정해야 합니다. 많은 대규모 조직에서는 비밀번호 해시에 대한 완전한 내부 제어를 유지할 수 있도록 연방 ID 모델을 선택합니다.
페더레이션 ID 모델에서 Office 365는 SAML(Security Access Markup Language)을 사용하여 기존 Active Directory 서비스(ID 공급자 또는 IdP)를 통해 사용자를 인증합니다. 페더레이션 로그인을 선택하려면 Office 365에서 Active Directory 서버에 액세스하고 SAML 인증 요청을 변환할 수 있도록 허용해야 합니다.
이를 달성하는 한 가지 방법은 Microsoft Active Directory Federation Services(ADFS) 서버와 ADFS 프록시 서버를 사용하여 보안 액세스를 관리하고 SAML IdP 역할을 하는 것입니다.
하지만 더 쉬운 방법이 있습니다.
BIG-IP LTM(Local Traffic Manager)과 APM(Access Policy Manager)을 사용하면 ADFS 프록시 서버만 제거하거나 ADFS 프록시 서버 와 ADFS 서버 자체를 제거할 수 있습니다. 어느 경우든 BIG-IP가 제공하는 고급 보안 보호 정책(방화벽 기능, 지리적 제한, 평판 제한, 사전 인증 등)을 사용하여 주요 디렉토리 인프라를 보호할 수 있습니다.
ADFS 프록시 서버를 교체하면 보안이 강화되고 방화벽이 인증된 플랫폼 을 통해 ADFS 서버에 대한 사전 인증 서비스는 물론 고가용성도 확보할 수 있습니다.
ADFS 프록시 서버와 ADFS 서버 자체를 모두 바꾸면 동일한 보안 및 사전 인증 이점이 제공되며 인프라도 간소화됩니다.
클라이언트는 2단계 인증, 클라이언트 인증서 등과 같은 고급 검사를 통해 사전 인증될 수 있습니다. 위치 및 평판과 같은 엔드포인트 검사를 배포할 수도 있습니다.
F5 ADFS iApp 템플릿을 사용하면 ADFS 서버를 보호하거나 교체하기 위해 BIG-IP를 배포하는 작업을 대폭 간소화할 수 있습니다. iApp 템플릿은 고급 구성 생성을 테스트 및 검증된 구성을 생성하는 간단한 마법사 기반 프로세스로 전환합니다.
작동하는 SAML IdP가 있으면 이러한 ID 페더레이션을 다른 많은 SAML 지원 애플리케이션과 서비스로 확장하여 다른 많은 웹 기반 SaaS 애플리케이션에서 단일 로그인을 제공할 수 있습니다.
먼저, 어떤 배포 모델을 선택할지 결정해야 합니다. 자세한 내용은 ADFS에 관한 F5 문서 시리즈 에서 확인하세요.
1. 요구 사항을 충족하는 배포 모델을 결정한 후 ADFS 배포 가이드를 읽고 iApp 템플릿을 다운로드하세요.
2. Active Directory 서버의 구성을 변경할 수 있는 자격 증명과 권한이 있는지 확인하세요.
3. BIG-IP 시스템을 배포하여 고가용성, 네트워크 연결 등을 테스트하세요.
4. iApp 템플릿을 실행하고 필요한 정보를 입력하세요. 이제 기본적인 설치가 완료되었습니다.
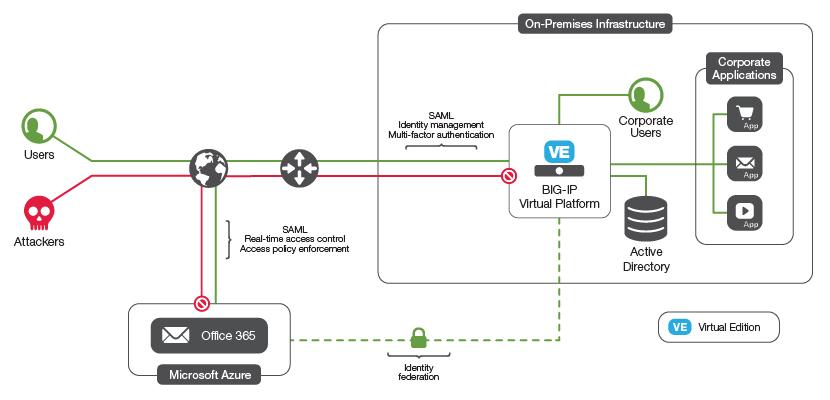
사용자가 Office 365에 보다 간편하고 안전하게 접근할 수 있도록 관리합니다.
고급 인증을 알아보려면 BIG-IP Access Policy Manager Policy Manager를 읽어보세요. 인증 및 Single Sign-On .