AI와 실시간 원격 측정을 통해 분산 클라우드 엣지에서 사이버 보안 재정의


ASH BHALGAT, NVIDIA
변화하는 애플리케이션 환경은 새로운 공격 표면과 새로운 보안 위험을 초래합니다.
디지털 혁신과 클라우드 기술의 도입이 빠른 속도로 진행되고 있습니다. 디지털 혁신으로 인해 애플리케이션이 기업의 생명선이 되었습니다. 기업이 우리 모두에게 영향을 미치는 거시적 추세에 적응하고 애플리케이션 현대화 여정을 채택함에 따라, 애플리케이션 아키텍처는 API 중심, 마이크로서비스 기반으로 변화하고 있으며 자동화와 오케스트레이션에 크게 의존하고 있습니다.
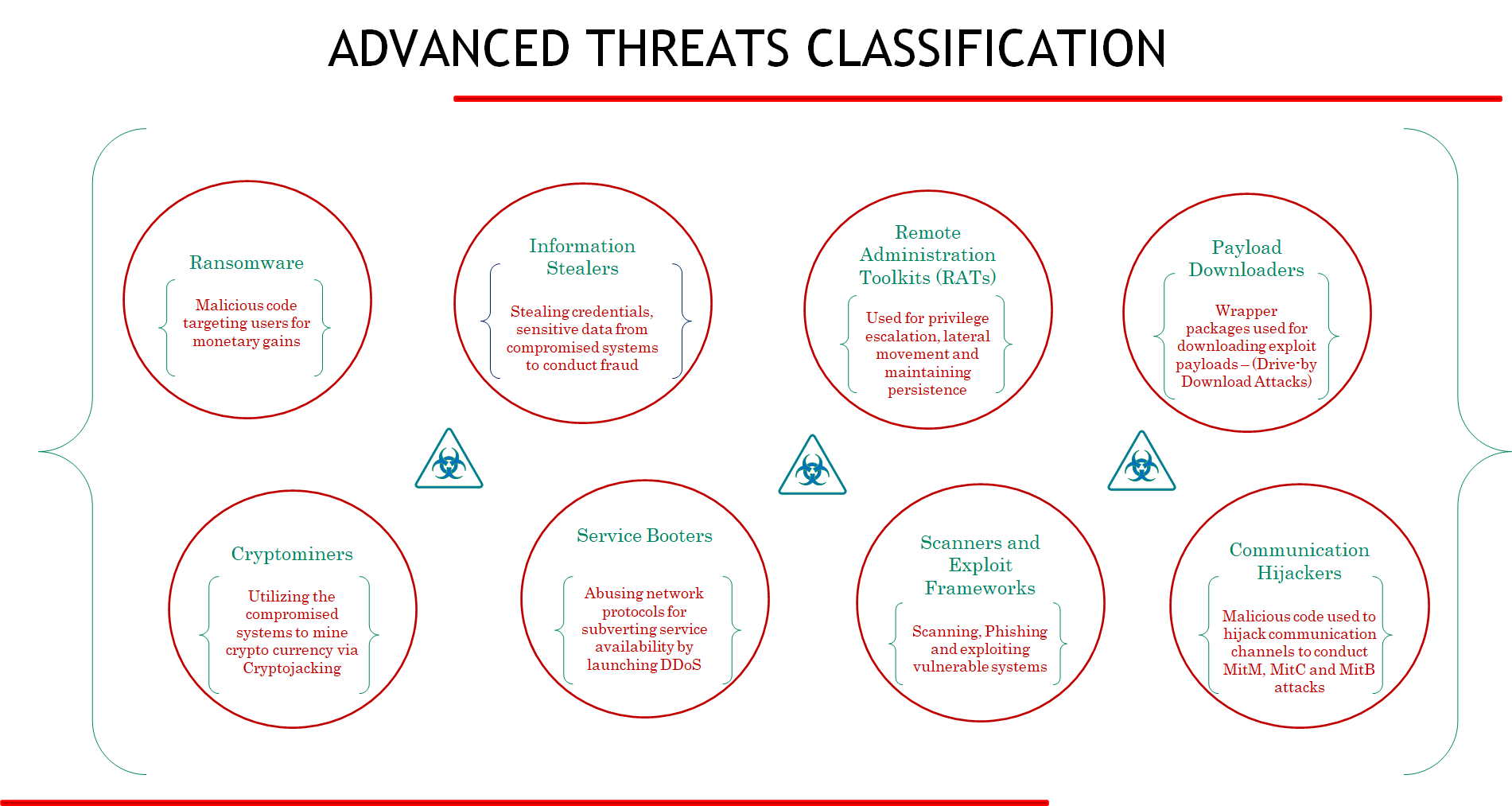
공격자는 빠르게 변화하는 애플리케이션 환경을 악용하여 도입된 공격 표면을 악용하기 위해 새로운 공격 방법을 사용하고 있습니다. 기업 고객이 직면했던 이전의 보안 위협과는 달리, 이러한 새로운 유형의 공격은 매우 조직적이며 재정적 동기를 가지고 있습니다. 공격자는 특정 자산을 표적으로 삼기 위해 특정한 전략이나 의도를 사용합니다. 아래 그림은 위협 행위자의 '의도'에 따른 몇 가지 일반적인 고급 위협의 분류입니다. 우리는 최근 랜섬웨어 활동에 대해 잘 알고 있으며 클라우드 환경의 작업 부하를 손상시키려는 위협 행위자 TeamTNT의 작업과 같이 다른 널리 퍼진 위협 활동도 몇 가지 있습니다.
AI 기반 보안은 빠른 속도로 보안을 제공하겠다는 약속입니다.
이러한 유형의 공격은 일반적으로 방화벽, 웹 애플리케이션 방화벽 등과 같은 잘 확립된 보안 제어를 우회합니다. 이러한 활동을 탐지하려면 거의 실시간으로 연관시킬 수 있는 방대한 양의 상황 정보가 필요하며, 이를 통해 진행 중인 지능형 위협 활동을 확인할 수 있습니다. 간단히 말해서, 고급 위협 활동 탐지는 이제 빅데이터 문제가 되고 있습니다!
F5는 웹, 애플리케이션, 방화벽 및 사기 완화 기술에 대한 잘 확립된 보안 조치를 강화하여 이러한 고급 위협을 탐지하는 기술을 연구하고 있습니다. 이를 위해서는 대규모 원격 측정을 통해 여러 데이터 포인트에 대한 맥락적 분석과 거의 실시간 분석이 필요합니다. 머신 러닝과 인공 지능 알고리즘을 사용하여 애플리케이션과 클라우드 환경 내부 및 주변에서 비정상적인 활동을 감지하고 사전에 위험을 해결합니다. 하지만 방대한 양의 데이터와 빠른 성능에 대한 고객들의 기대치가 충돌합니다. 여기에서 NVIDIA BlueField-2 데이터 처리 장치(DPU) 기반 실시간 원격 측정 및 NVIDIA GPU 기반 Morpheus 사이버 보안 프레임워크가 활용됩니다.
사이버 보안은 AI/ML 처리에 고유한 요구 사항을 제시합니다.
- 빠른 속도의 애자일 개발과 일시적인 작업 부하로 인해 인간의 감독이나 레이블 지정이 필요한 방법보다 클러스터링이나 이상 감지와 같은 비지도 방법에 대한 중요성이 커지고 있습니다.
- 두 번째로 중요한 측면은 설명 가능성입니다. 이 중 일부는 고객이 솔루션에 대한 신뢰를 구축하도록 돕는 맥락에서 이해되어야 합니다. 거짓 긍정 또는 거짓 부정으로 인해 고객을 잃거나, 더 광범위하게는 감사 또는 규정 준수 검사가 발생할 수 있습니다. 경험적으로, 설명 가능한 90% 효과적인 솔루션은 이해할 수 없는 95% 솔루션보다 고객에게 더 매력적입니다.
- 세 번째이자 가장 중요한 측면은 '적대자 효과'입니다. 즉, 자금이 풍부하고 지능적이며 적극적인 적이 있다는 사실입니다. 예를 들어, 자율 주행차의 시각 인식과 달리 인식해야 할 도로 표지판 세트가 고정되어 있는 경우 보안에는 인간(아마도 AI 지원 인간)이 참여하여 ML 솔루션을 분석하고 지속적으로 적극적으로 속이거나 회피하려고 시도합니다.
NVIDIA Morpheus가 새로운 사이버 보안 과제를 해결합니다.
NVIDIA는 Morpheus 사이버보안 프레임워크 출시를 통해 AI 데이터 과학의 힘을 사이버보안 산업에 제공하고 있습니다. Morpheus의 고도로 최적화된 AI 파이프라인과 사전 훈련된 AI 기능을 통해 개발자는 데이터 센터 패브릭 전반의 모든 IP 트래픽을 즉시 검사할 수 있습니다.

NVIDIA BlueField-2 DPU, 실시간 원격 측정을 가속화
Morpheus는 DPU 강화 서버 에서 실시간 네트워크 데이터를 집계하고 분석하기 위한 완벽한 솔루션입니다. 한편, BlueField DPU는 임무 수행에 중요한 인프라 기능의 부하를 분산하고, 가속화하고, 격리합니다. Morpheus는 NVIDIA BlueField DPU에서 실행되는 에이전트로부터 엄청난 양의 네트워크 원격 측정 데이터를 수신하고 이 엄청난 양의 데이터에 대해 실시간 추론을 수행할 수 있습니다. 그러면 Morpheus는 DPU로 다시 라우팅되는 원시 추론 결과에서 작업을 생성할 수 있습니다. Morpheus와 DPU 간의 양방향 데이터 스트림을 통해 정책에 영향을 미치고, 규칙을 다시 작성하고, 감지 기능을 조정하는 등의 작업에 대한 지속적이고 실시간 피드백을 얻을 수 있습니다.
가속화된 추론은 사이버 위협을 빠르고 효율적으로 감지합니다.
Morpheus는 워크플로 프로세스에 GPU를 추가하여 방대한 양의 원격 측정 데이터에 대한 실시간 추론을 제공합니다. GPU는 수집, 사전 처리, 추론, 사후 처리를 거쳐 데이터를 처리하고, 파이프라인을 통해 엄청난 양의 데이터를 이동시키기 위해 병렬화를 제공합니다. Morpheus는 데이터와 작업을 관리 가능한 일괄 처리로 나누고 동시에 실행함으로써 이기종, 분산/분산 및 모바일 소스에서 흐르는 데이터를 처리합니다.
Morpheus는 게시자/구독자 모델인 Kafka를 사용하여 추론 파이프라인으로 데이터를 전송하고 추론 파이프라인에서 결과를 가져옵니다. Morpheus 프레임워크는 데이터 처리를 위한 RAPIDS, GPU 가속 오픈소스 사이버 보안 기본 요소를 위한 Cyber Log Accelerators, 추론 서버로 사용되는 Triton 및 TensorRT, 가속화된 Kafka 읽기 및 쓰기를 위한 cuStreamz, 새롭고 업데이트된 AI 모델을 로드하는 오픈소스 라이브러리인 MLFlow를 포함한 여러 가지 빌딩 블록을 사용하여 구축되었습니다. 이러한 기술은 사이버보안 워크플로의 모든 부분을 해결하기 위해 함께 작동합니다.
F5는 Morpheus 프레임워크를 통합하여 클라우드와 엣지에 분산된 애플리케이션에 대한 실시간 원격 측정 및 AI 기반 분석을 통해 모든 서버에서 웹 및 API 사이버 보안을 가속화하는 강력한 플랫폼을 제공합니다.
NVIDIA GTC에 참석하여 NVIDIA Morpheus 프레임워크와 BlueField DPU로 가속화된 F5의 Shape 사이버보안 포트폴리오에 대해 자세히 알아보세요 . 여기서 무료로 등록할 수 있습니다.