For more than 20 years, F5 has worked with customers to defend their applications against distributed denial-of-service (DDoS) attacks. Over time F5 has developed core product capabilities to help applications and services maintain resiliency against DDoS attacks. Many high-profile attacks since 2018 have prompted service providers and managed service providers (MSPs), financial organizations, and enterprises to redesign their networks to include DDoS protection. Working with these customers, F5 has developed a DDoS Protection reference architecture that includes both cloud and on-premises components.
The reference architecture includes multiple tiers of on-premises defenses to protect layers 3 through 7. The network defense tier protects DNS and layers 3 and 4. Freed from the noise of network attacks, the application defense tier can use its CPU resources to protect the high-layer applications. This design enables organizations to defend against all types of DDoS attacks and provides benefits across the organization’s data centers. Finally, the cloud component of the DDoS Protection solution works as a failsafe for volumetric attack mitigation.
While the DDoS threat landscape is constantly evolving, F5 has found that attacks continue to fall within four attack types with the following characteristics:
Defensive mechanisms have evolved to deal with these different categories, and high-profile organizations have learned to deploy them in specific arrangements to maximize their security posture. By working with these companies and fine-tuning their components, F5 has developed a recommended DDoS mitigation architecture that can accommodate specific data center scale and industry requirements.
The following DDoS Protection reference architecture is built around well-known industry components. Some may be provided by other vendors and suppliers, but some are specific F5 components.
Figure 1 maps DDoS architecture components to the four DDoS attack categories they mitigate.
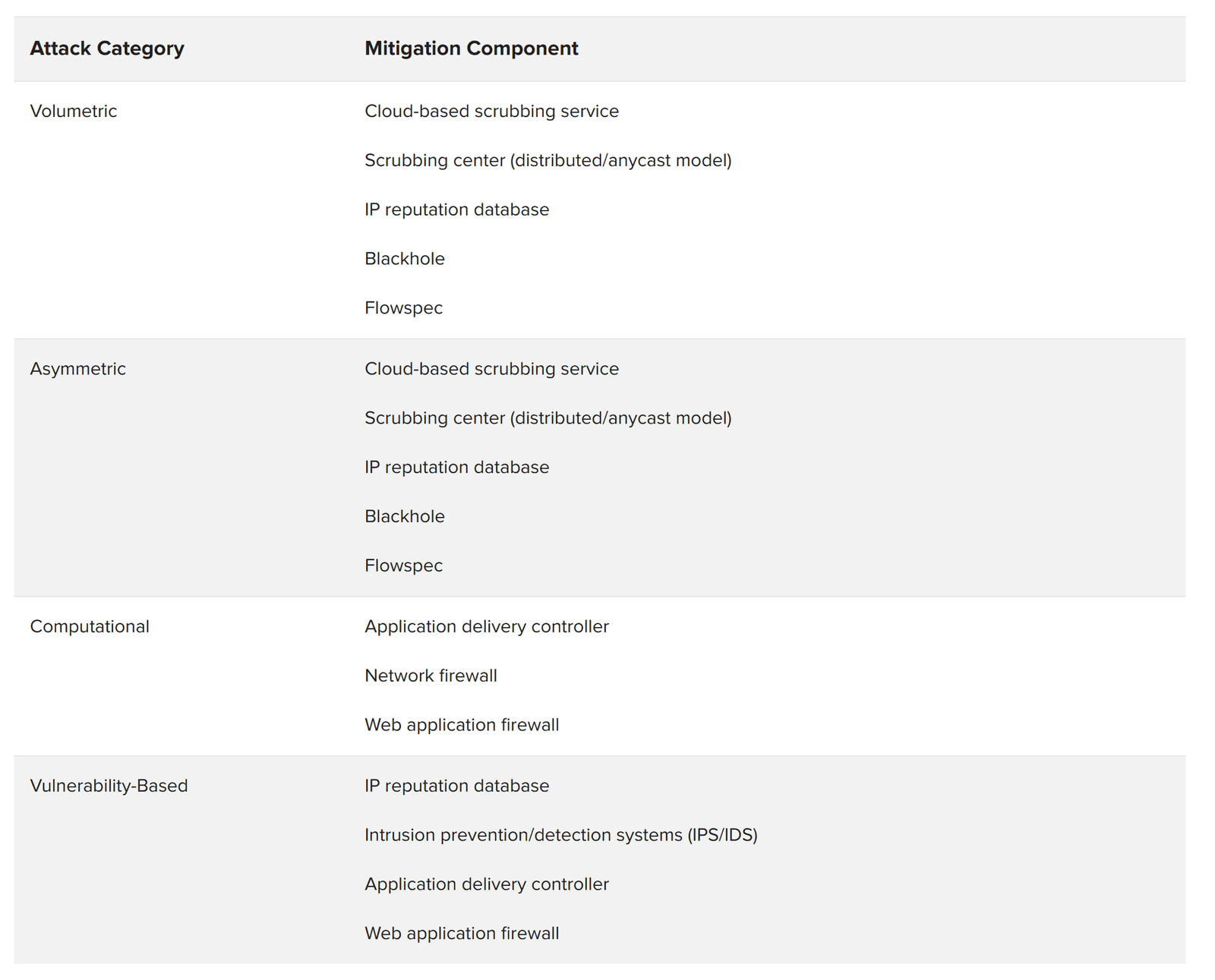
A cloud-based DDoS scrubbing service is a critical component of any DDoS mitigation architecture. When an attacker is sending 50 Gbps of data at an organization’s 1 Gbps ingress point, no amount of on-premises equipment is going to solve that problem. The cloud service, hosted either from a true public cloud or within the organization’s bandwidth service provider, solves the problem by sorting out the obvious bad from the likely good.
The network firewall has been the keystone of perimeter security for a long time. However, many network firewalls are not resistant to DDoS attacks at all. In fact, many of the best-selling firewalls can be disabled with the simplest layer 4 attacks. Sheer throughput is not the answer if the firewall does not recognize and mitigate the attack.
For a layer 3- and 4-based security control device, F5 recommends that architects choose a high-capacity, DDoS-aware network firewall. Specifically, architects should be looking to support millions (not thousands) of simultaneous connections and be able to repel various attacks (e.g., SYN floods) without affecting legitimate traffic.
Application Delivery Controllers (ADCs) provide strategic points of control in the network. When chosen, provisioned, and controlled properly, they can significantly strengthen a DDoS defense. For example, the full-proxy nature of the F5 ADC reduces computational and vulnerability-based threats by validating common protocols such as HTTP and DNS. For these reasons, F5 recommends a full-proxy ADC.
The web application firewall is a higher-level component that understands and enforces the security policy of the application. This component can see and mitigate application-layer attacks whether they are volumetric HTTP floods or vulnerability-based attacks. Several vendors provide web application firewalls. For an effective DDoS architecture, however, F5 recommends only its own web application firewall module for the following reasons:
Intrusion detection and prevention systems (IDS/IPS) can play an important role in DDoS mitigation. F5 recommends that IDS/IPS functionality should not be deployed only in a single location (for example, integrated into a layer 4 firewall). Rather, IDS/IPS should be deployed in strategic instances in front of back-end components that may need specific, additional protection, such as a database or specific web server. Nor is an IPS a replacement for a web application firewall. Securing infrastructure and applications is analogous to peeling an onion. An IPS is designed to stop attacks at the top layer—protocols—while WAFs are designed to protect at lower layers (applications).
An IP reputation database helps defend against asymmetric denial-of-service attacks by preventing DDoS attackers from using known scanners to probe an application for later exploitation and penetration. An IP reputation database may be generated internally or come from an external subscription service. F5 IP reputation solutions combine intelligence from open-source intelligence (OSINT), F5 data, and third-party feeds to provide wide coverage of malicious domains.
F5 recommends a hybrid cloud/on-premises DDoS solution. Volumetric attacks will be mitigated by F5 Silverline DDoS Protection—a service delivered via the F5 Silverline cloud-based platform. Silverline DDoS Protection will analyze and remove the bulk of attack traffic.
Sometimes, a DDoS campaign may include application layer attacks that must be addressed on the premises. These asymmetric and computational attacks can be mitigated using the network defense and application defense tiers. The network defense tier is composed of L3 and L4 network firewall services and simple load balancing to the application defense tier. The application defense tier consists of more sophisticated (and more CPU-intensive) services including SSL termination and a web application firewall stack.

There are compelling benefits to separating network defense and application defense for the on-premises portion of the DDoS Protection architecture.
Figure 3 shows components needed to provide specific capabilities. The F5 components of the DDoS Protection reference architecture include:
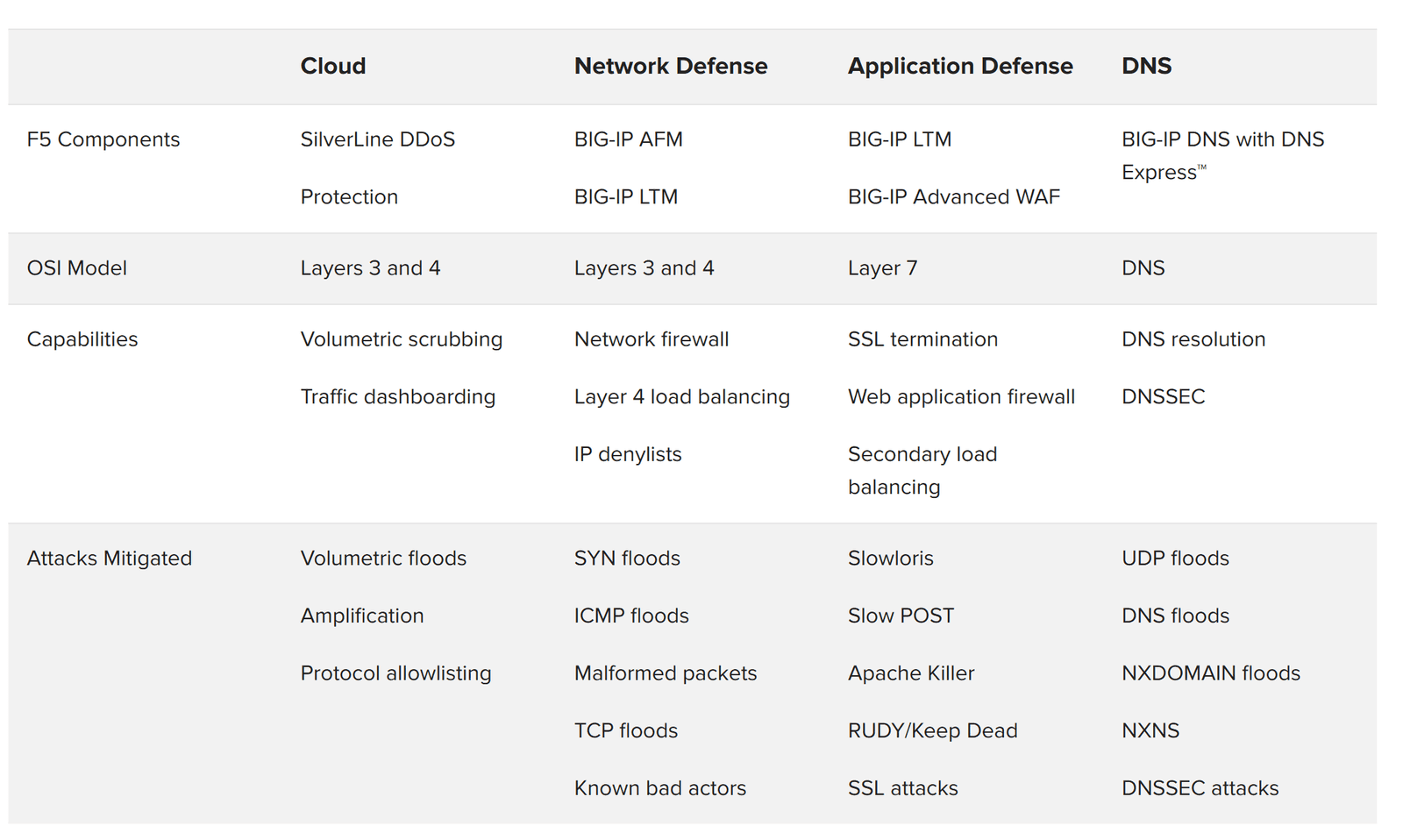
While the multi-tier architecture is preferred in high-bandwidth environments, F5 understands that for many customers, building multiple DDoS tiers may be overkill for a low-bandwidth environment. These customers are deploying a DDoS mitigation perimeter device that consolidates application delivery with network and web application firewall services.
The recommended practices here still apply. References to network and application defense tiers can simply be applied to the single, consolidated tier in the alternate architecture.
Organizations are at risk of experiencing large-scale volumetric DDoS attacks that are capable of overwhelming their Internet-facing, ingress bandwidth capacity. To defend against these attacks, they may effect a route change (with a BGP route announcement) to direct incoming traffic to high-bandwidth data centers that can scrub malicious traffic and send the clean, scrubbed traffic back to the organization’s origin data center.
Factors that may influence the choice of a cloud DDoS provider include the geographic location of scrubbing facilities, bandwidth capacity, latency, time to mitigate, and solution value. As Figure 4 indicates, DDoS attacks may reach bandwidth consumption that is measured in hundreds of Gbps, placing an infrastructure at peril of being completely overwhelmed.
In some instances, additional time may be added to incoming requests when a cloud scrubber does not have a scrubbing center in proximity to the organization’s data center. To reduce potential latency, MSPs and other global enterprises should utilize cloud scrubbers that are strategically placed within the regions where they have operations that can be impacted by attacks.
Maintaining availability against volumetric attacks depends on both global coverage—data centers in North America, Europe, and Asia—and terabits of global capacity or hundreds of gigabits per center.
Organizations will say that the true value of a cloud scrubber is realized only after the attack campaign. Questions that determine their satisfaction include:
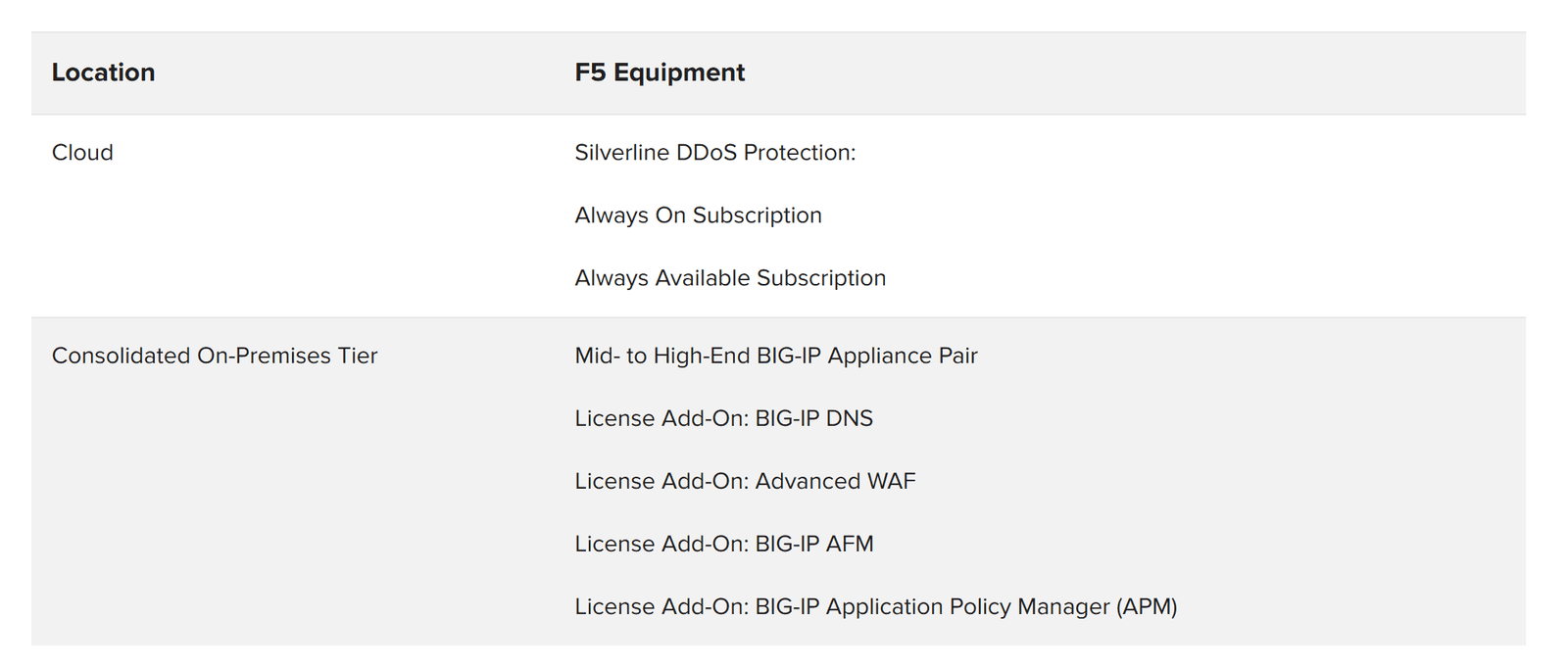
Organizations can use the Silverline DDoS Protection Always Available subscription to route traffic through F5 Silverline when a DDoS attack is detected. Alternately, the Silverline DDoS Protection Always On subscription can route traffic through F5 Silverline at all times to ensure greater availability of the organization’s networks and applications.
Silverline DDoS Protection has two main deployment models: routed mode and proxy mode.
Routed mode is for enterprises that need to protect their entire network infrastructure. Silverline DDoS Protection employs the Border Gateway Protocol (BGP) to route all the traffic to its scrubbing and protection center and utilizes a Generic Routing Encapsulation (GRE) tunnel/L2 VPN/Equinix Cloud Exchange to send the clean traffic back to the origin network. The routed mode is a scalable design for enterprises with large network deployments. It does not require any application-specific configuration and provides an easy option to turn on or off Silverline DDoS Protection.
Proxy mode is for enterprises that need to protect their applications from volumetric DDoS attacks but do not have a public Class C network. DNS is used to route all traffic to F5 Silverline scrubbing centers. Clean traffic is sent over the public Internet to the application origin servers.
Return traffic methods used by Silverline DDoS Protection include:
Figure 4 shows that in 2019–2020, the record for the world’s largest DDoS attack was broken several times. In order to reach such bandwidth consumption these attacks used a combination of flood attacks (e.g., ACK, NTP, RESET, SSDP, SYN, and UDP) along with TCP Anomaly, UDP Fragment, and CLDAP Reflection from thousands of unwitting public Internet posts to an intended victim.

The network defense tier is built around the network firewall. It is designed to mitigate computational attacks such as SYN floods and ICMP fragmentation floods. This tier also mitigates volumetric attacks up to the congestion of the ingress point (typically 80 to 90 percent of the rated pipe size). Many organizations integrate their IP reputation databases at this tier and have controls to IP addresses by source during a DDoS attack.
Some organizations pass DNS through the first tier to a DNS server in the DMZ. In this configuration, with the right layer 4 controls they can validate DNS packets before sending them on to the server.

For organizations with a virtualization-first strategy, it can be challenging to mitigate DDoS attacks that target their virtualized infrastructure without purpose-built hardware. Virtualized security solutions running on x86 COTS servers often lack the high-performance attributes of custom appliances, making effective software-centric DDoS mitigation nearly impossible in many cases.

The F5 solution to this challenge utilizes a new generation of network interface cards (NICs)— known as SmartNICs—to bolster the BIG-IP AFM virtual edition (VE) solution. By programming an embedded, high performance FPGA within these SmartNICs to detect and block DDoS attacks before they reach BIG-IP VE and applications servers, F5 is able to block attacks orders of magnitude larger—up to 300 times larger—than any comparable software-only solution to keep apps online. Offloading DDoS mitigation from BIG-IP AFM VE to a SmartNIC not only frees up VE CPU cycles for optimizing other security functionality (such as WAF or SSL) but can also reduce TCO by up to 47 percent.
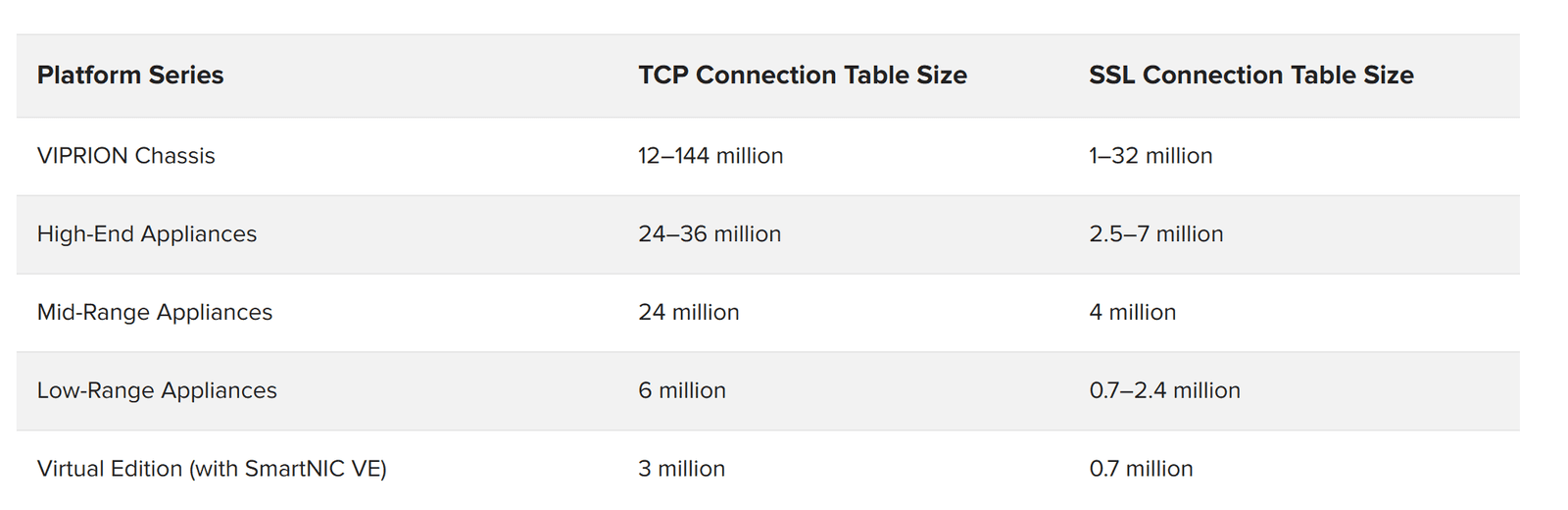
As layer 4 attacks, TCP connection floods can affect any stateful device on the network, especially firewalls that are not DDoS-resistant. The attack is designed to consume the memory of the flow connection tables in each stateful device. Often these connection floods are empty of actual content. They can be absorbed into high-capacity connection tables in the network tier or mitigated by full-proxy firewalls.
SSL connection floods are designed specifically to attack the devices that terminate encrypted traffic. Due to the cryptographic context that must be maintained, each SSL connection can consume 50,000 to 100,000 bytes of memory. This makes SSL attacks especially painful.
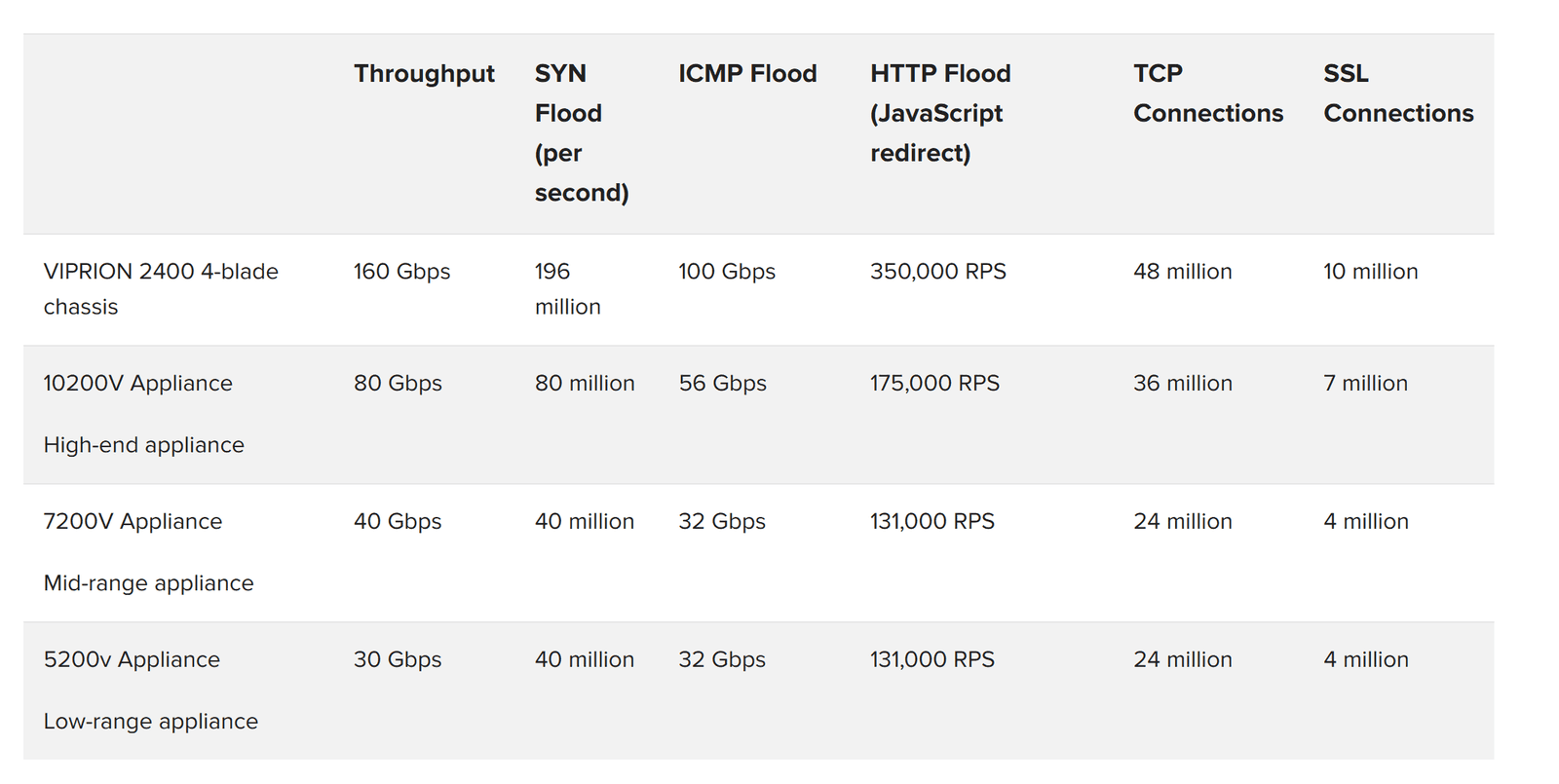
F5 recommends both capacity and the full-proxy technique for mitigating TCP and SSL connection floods. Figure 7 shows the connection capacity of F5-based network firewalls.
The application defense tier is where F5 recommends deploying application-aware, CPU-intensive defense mechanisms like login walls, web application firewall policies, and dynamic security context using F5 iRules. Often these components will share rack space with targeted IDS/IPS devices at this tier.
This is also where SSL termination typically takes place. While some organizations terminate SSL at the network defense tier, it is less common due to the sensitivity of SSL keys and policies against keeping them at the security perimeter.

Recursive GETs and POSTs are among today’s most pernicious attacks. They can be very hard to distinguish from legitimate traffic. GET floods can overwhelm databases and servers, and they can also cause a “reverse full pipe.” F5 recorded one attacker that was sending 100 Mbps of GET queries into a target and bringing out 20 Gbps of data.
Mitigation strategies for GET floods include:
The configuration and setup for these strategies can be found in the F5 DDoS Recommended Practices documentation.
DNS is the second-most targeted service after HTTP. When DNS is disrupted, all external data center services (not just a single application) are affected. This single point of total failure, along with the often under-provisioned DNS infrastructure, makes DNS a tempting target for attackers.
DNS services have been historically under-provisioned. A significant percentage of DNS deployments are under-provisioned to the point where they are unable to withstand even small-to-medium DDoS attacks.
DNS caches have become popular as they can boost the perceived performance of a DNS service and provide some resilience against standard DNS query attacks. Attackers have switched to what is called “no such domain” (or NXDOMAIN) attacks, which quickly drain the performance benefits provided by the cache.
To remedy this, F5 recommends front-ending the BIG-IP DNS Domain Name Service with the special, high-performance DNS proxy module called F5 DNS Express™. DNS Express acts as an absolute resolver in front of the existing DNS servers. It loads the zone information from the servers and resolves every single request or returns NXDOMAIN. It is not a cache and cannot be emptied via NXDOMAIN query floods.
Often the DNS service exists as its own set of devices apart from the first security perimeter. This is done to keep DNS independent of the applications it serves. For example, if part of the security perimeter goes dark, DNS can redirect requests to a secondary data center or to the cloud. Keeping DNS separate from the security and application tiers can be an effective strategy for maintaining maximum flexibility and availability.
Some large enterprises with multiple data centers serve DNS outside the main security perimeter using a combination of BIG-IP DNS with DNS Express and the BIG-IP AFM firewall module. The main benefit of this approach is that the DNS services remain available even if the network defense tier goes offline due to DDoS.
Regardless of whether DNS is served inside or outside the DMZ, either BIG-IP DNS or BIG-IP AFM can validate the DNS requests before they hit the DNS server.
Following are three uses cases for the reference architecture that map to three typical customer scenarios:
Each use case below contains a diagram of the deployment scenario, a short description of the specifics of the use case, and recommended F5 components within that scenario. Also see Figure 14 for additional sizing information.
The MSP data center use case is all about providing security for a variety of applications while maximizing the value of data center resources. Return-on-investment (ROI) is crucial for MSPs, who would often like to do everything from one device if they can and are willing to go offline during a DDoS attack.
For this use case, the MSP is putting all of its eggs in one basket. It will get the most cost-efficient solution but will also have the largest availability challenge.
On the other hand, the organization gains efficiency by focusing specialized resources with deep knowledge on a single platform. F5 provides high-availability systems, superior scale and performance, and world-class support that help further offset risk.
Certainly, financial savings is the biggest benefit of this consolidated architecture. A superior DDoS solution uses equipment that is already working to deliver revenue-generating applications every day. The consolidated environment helps save on rack space, power, and management.

The large FSI data center scenario is a mature, well-recognized use case for DDoS Protection. Typically, the FSI will have multiple service providers but may forgo those providers’ volumetric DDoS offerings in favor of another scrubbing service. Many of these may also have a backup cloud scrubber as an insurance policy against the failure of their primary cloud scrubber to mitigate volumetric DDoS attacks.
The FSI data center often has few corporate staff within it, so there is no need for a next-generation firewall.
FSIs have the most stringent security policy outside of federal military institutions. For example, nearly all FSIs must keep the payload encrypted through the entire data center. FSIs have the highest-value asset class (bank accounts) on the Internet, so they are frequent targets—not just for DDoS but also for hacking. The two-tier on-premises architecture enables FSI organizations to scale their CPU-intensive, comprehensive security policy at the application tier independently of their investment in the network tier.
This use case enables FSIs to create a DDoS-resistant solution while retaining (indeed, leveraging) the security equipment they already have. The firewalls at the network defense tier continue to do their jobs, and the BIG-IP devices at the application defense tier continue to prevent breaches.
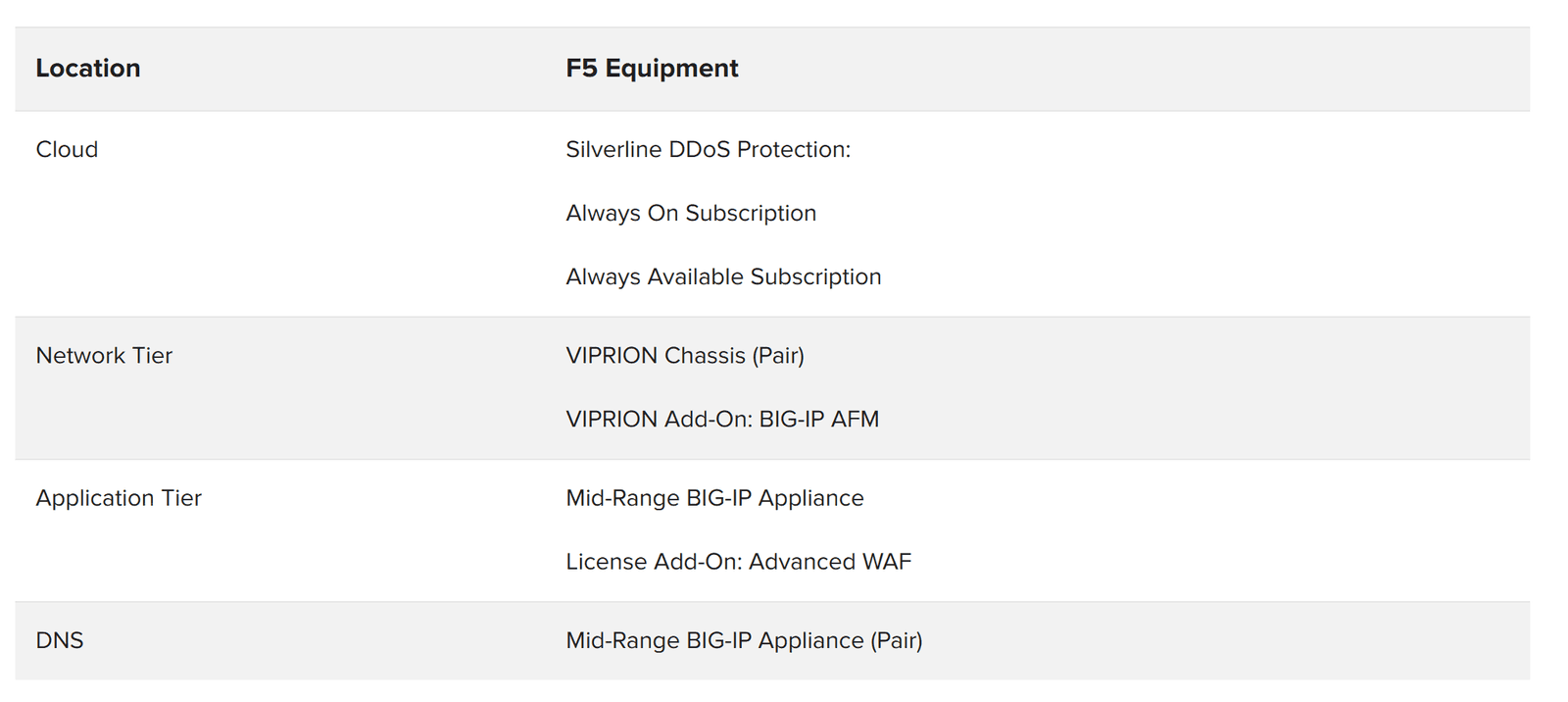

The enterprise anti-DDoS scenario is similar to the large FSI scenario. The primary difference is that enterprises do have staff inside the data center and therefore need the services of a next-generation firewall (NGFW). They may be tempted to use a single NGFW for both ingress and egress, but this makes them vulnerable to DDoS attacks, as NGFW aren’t designed to handle DDoS attacks that evolve or are multi-vector.
F5 recommends that enterprises obtain protection against volumetric DDoS attacks from a cloud scrubber like F5 Silverline. On the premises, the recommended enterprise architecture includes a smaller NGFW on a separate path from the ingress application traffic. By using a network defense tier and an application defense tier, enterprises can take advantage of asymmetric scaling—adding more F5 WAF devices if they find that CPU is at a premium.
Different verticals and companies have different requirements. By using F5 equipment at both tiers, the enterprise architecture enables customers to decide where it makes the most sense to decrypt (and optionally re-encrypt) the SSL traffic. For example, an enterprise can decrypt SSL at the network defense tier and mirror the decrypted traffic to a network tap that is monitoring for advanced threats.
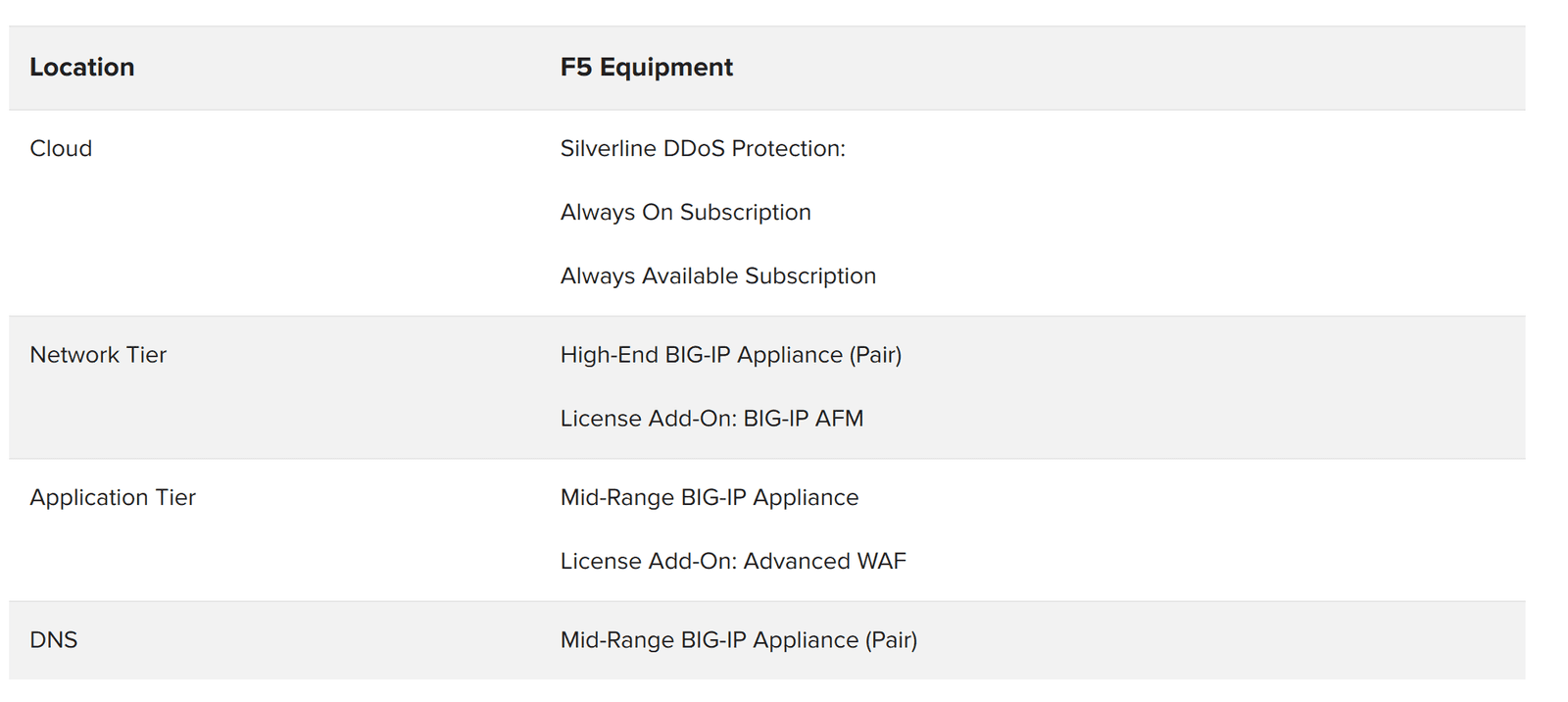
Figure 14 shows specifications for the range of F5 hardware devices that are available to meet organizations’ scaling requirements.
This recommended DDoS Protection reference architecture draws on F5’s long experience combating DDoS attacks with its customers. Service providers are finding success with a consolidated approach. Global financial services institutions are recognizing that the recommended hybrid architecture represents the ideal placement for all of their security controls. Enterprise customers are rearranging and rearchitecting their security controls around this architecture as well. For the foreseeable future, a hybrid DDoS Protection architecture should continue to provide the flexibility and manageability that architects need to combat the modern DDoS threat.
PUBLISHED OCTOBER 01, 2020