DDoS Attack Protection
DDoS attacks threaten application availability and can lead to lost revenue and damaged brand. F5 provides DDoS protection that makes sense for your architecture.
Under Attack? Call (866) 329-4253 or +1 (206) 272-7969
DDoS attacks threaten application availability and can lead to lost revenue and damaged brand. F5 provides DDoS protection that makes sense for your architecture.
Under Attack? Call (866) 329-4253 or +1 (206) 272-7969
All businesses risk being hit with DDoS attacks. The goal of these attacks is to disrupt application performance or availability, but the attack vectors can vary—targeting available bandwidth, application resources like CPU and memory, or critical infrastructure protocols like DNS and TLS. F5 can help.
F5 solutions mitigate multi-vector denial-of-service attacks that overwhelm critical infrastructure, target key protocols, and abuse application-layer business logic.
F5 DDoS mitigation can be deployed in the architectural and operational model your business needs, including cloud-based protection, hybrid on-premises defense with on-demand cloud-scrubbing, and native application infrastructure form factors.
The F5 Security Operations Center (SOC) is staffed with experts that monitor and protect your business from attack 24/7, 365.
See latest trends

F5 offers denial-of-service protection in the architectural and operational model that works best for your business, based on where your applications are hosted—in the cloud, on-premises, or a mix of both—and with the level of hands-on management you prefer. Plus, your solution can evolve over time as application infrastructure protection needs change.
Watch the customer story videoApps enable businesses to gain a competitive advantage, but they’re increasingly targeted for denial-of-service (DoS) attacks that lead to downtime, lost revenue, and a damaged brand. Modern apps are distributed across clouds and architectures—and integrated with development tools and CI/CD pipelines—yet traditional DDoS mitigation is centralized, static, and stateless.
F5 provides a managed DDoS protection service that detects and mitigates large-scale volumetric and targeted application attacks in real time—defending your business even from attacks that exceed hundreds of gigabits per second.
Retain control of mitigation timing and techniques on-premises, but have on-demand help for large, bandwidth-consuming attacks. The hybrid F5 solution can signal upstream to the cloud scrubbing service when necessary.
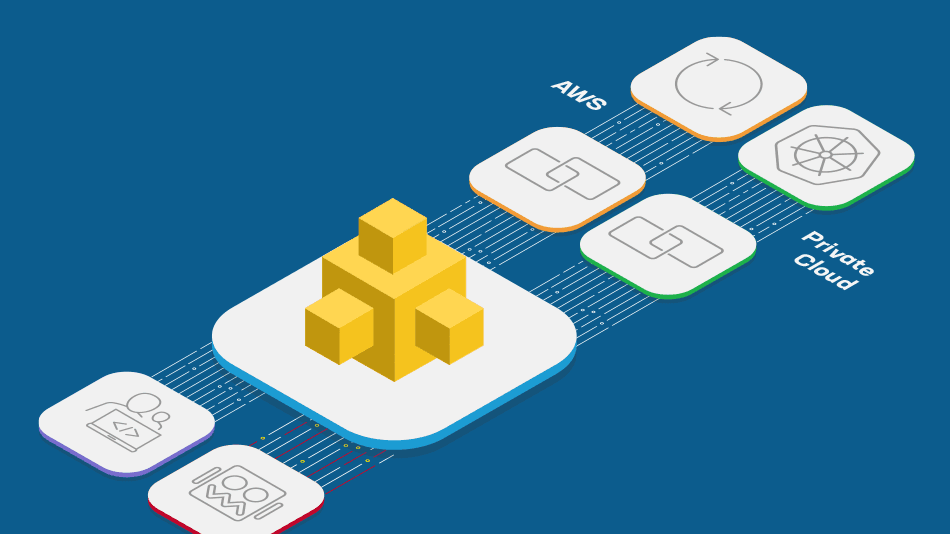
F5 Distributed Cloud DDoS Mitigation delivers DDoS and advanced security services to protect against L3-L7 attacks on enterprises and hosting and service providers.
Read the overview