If you follow tech news, it often seems like “another day, another security breach”. Increasingly, though, breaches are taking the form of attacks on APIs. You’re not safe even when taking a break to exercise – a security researcher recently found that an API from stationary bike vendor Peloton delivered private user account data in response to unauthenticated requests!
In F5’s The State of Application Strategy in 2021 report, 58% of respondents said they are building a layer of APIs to modernize applications. With the rise of DevOps, cloud, and microservices, applications and the APIs that underpin them need to be supported across a distributed environment that includes, but isn’t limited to:
- On premises, cloud, and hybrid environments
- Development, testing, staging, sandbox, and production environments
- Internal APIs that foster collaboration among developers and unlock data silos
- External APIs that are exposed to your customers, partners and third‑party developers
API gateways mediate API traffic by routing requests, authenticating and authorizing API clients, and applying rate limits to protect API‑based services from overload. Many NGINX customers have successfully deployed API gateways across the kinds of distributed environments mentioned above, but at the same time have seen APIs emerge as a new attack vector. According to F5’s 2021 Application Protection Report, nearly two‑thirds of API incidents occurred because APIs were totally exposed – they didn’t have any authentication or authorization mechanisms.
The NGINX Controller API Management Module provides a variety of mechanisms to protect your APIs, including:
- Rate limiting – Rate‑limiting policies protect your APIs from being overwhelmed and mitigate DDoS attacks by setting a limit on the number of requests the API gateway accepts from each API client in a given period of time. This helps address the Lack of Resources and Rate Limiting (API4) vulnerability in the OWASP API Security Top 10 2019.
- Authentication and authorization – Authentication and authorization mechanisms ensure that only clients with the right access privileges can consume your APIs. One such mechanism is claims in JSON Web Tokens (JWTs). This helps address three vulnerabilities in the OWASP API Security Top 10 2019: Broken Object Level Authorization (API1), Broken User Authentication (API2), and Broken Function Level Authorization (API5).
Introducing the NGINX Controller App Security Add‑On for API Management
Now you can boost your API security even further with the NGINX Controller App Security add‑on for the NGINX Controller API Management Module.
Distributed API Security in Any Environment
With Controller App Security, you now can now deploy a web application firewall (WAF) to protect your APIs across a multi‑cloud, distributed environment. The add‑on enables seamless integration of strong security with NGINX API gateways deployed anywhere – the public cloud, private cloud, bare‑metal, VMs, or containers.

True to NGINX’s “core values”, Controller App Security is lightweight, platform agnostic, and high performance. How do we achieve high performance? The WAF is colocated with the NGINX API gateway, so there’s one less hop for API traffic, reducing both latency and complexity. That’s in stark contrast with typical API management solutions, which don’t integrate with a WAF. You have to deploy the WAF separately, and once it’s set up API traffic has to traverse the WAF and API gateway separately. Controller App Security’s tight integration means high performance without compromising security.
Built on F5’s proven security expertise, Controller App Security provides out-of-the-box protection against OWASP API Security Top 10 vulnerabilities, as well as common vulnerabilities like SQL injection and remote command execution (RCE). The add‑on checks for malformed cookies, JSON, and XML, and also validates allowed file types and response status codes. It ensures compliance with HTTP RFCs and detects evasion techniques used to mask attacks.
Enhanced Visibility and Analytics
Controller App Security provides a variety of metrics and insights about different attack types attacks. These include top WAF threats and targeted APIs, top signatures for false positive investigations, WAF outcome statistics, and WAF violation events. This level of visibility helps address the Insufficient Logging & Monitoring vulnerability (API10) in the OWASP API Security Top 10 2019.
The following screenshots illustrate just some of the metrics you can track:
- The number of particular violation types during the past three hours, compared to the same time period on the previous day.

- The enforcement modes applied to API traffic during the past three hours.

- The top attack types during the past six hours.

- Log of security events during the past 30 minutes.

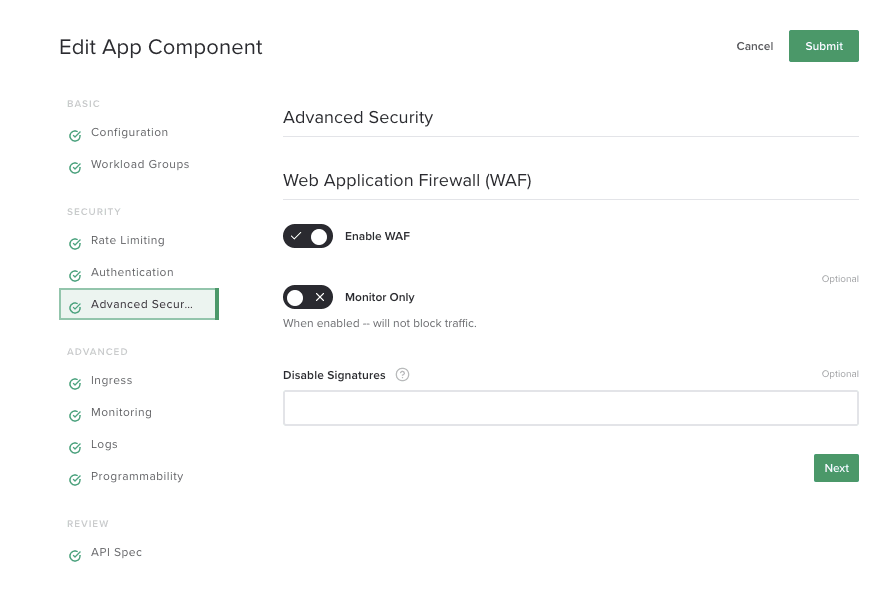
Flexible and Fine-Tuned Policies
Controller App Security gives you flexible, fine‑tuned control over security policies. As shown in this screenshot, you can set both blocking and monitoring‑only enforcement modes – in the second mode, malicious traffic is logged but still forwarded to the API server. You can also disable default signatures to reduce false positives.
This screenshot shows a list of the signatures that are blocking the most API calls, information you can use to prioritize which signatures you need to tune to reduce false positives.

DevOps-Friendly API Security
Controller App Security lets you empower DevOps by enabling self‑service and removing operational bottlenecks between security and DevOps teams, as well as supporting automation and integrating the WAF natively into CI/CD pipelines. These capabilities advance the shift‑left movement, in which developers and DevOps teams apply security earlier in the software development cycle (especially during the test phase) by integrating it into the CI/CD pipeline. API security is not treated as an afterthought – it’s an integral part of the API development process, which results in fewer issues in production.
Want to give NGINX Controller App Security for API Management a try? Download a 30-day free trial or contact us to discuss your API security needs.
About the Author

Related Blog Posts

Secure Your API Gateway with NGINX App Protect WAF
As monoliths move to microservices, applications are developed faster than ever. Speed is necessary to stay competitive and APIs sit at the front of these rapid modernization efforts. But the popularity of APIs for application modernization has significant implications for app security.
How Do I Choose? API Gateway vs. Ingress Controller vs. Service Mesh
When you need an API gateway in Kubernetes, how do you choose among API gateway vs. Ingress controller vs. service mesh? We guide you through the decision, with sample scenarios for north-south and east-west API traffic, plus use cases where an API gateway is the right tool.
Deploying NGINX as an API Gateway, Part 2: Protecting Backend Services
In the second post in our API gateway series, Liam shows you how to batten down the hatches on your API services. You can use rate limiting, access restrictions, request size limits, and request body validation to frustrate illegitimate or overly burdensome requests.
New Joomla Exploit CVE-2015-8562
Read about the new zero day exploit in Joomla and see the NGINX configuration for how to apply a fix in NGINX or NGINX Plus.
Why Do I See “Welcome to nginx!” on My Favorite Website?
The ‘Welcome to NGINX!’ page is presented when NGINX web server software is installed on a computer but has not finished configuring
